Tools for conducting denial-of-service attacks
From Computing and Software Wiki
| Line 7: | Line 7: | ||
| - | ==Definition== | + | ==Definition<sup>[3]</sup>== |
[[Image:Dosgeek.jpg|thumb|right|400px|DoS in comic]] | [[Image:Dosgeek.jpg|thumb|right|400px|DoS in comic]] | ||
Denial-of-service (DoS) attack is an attempt to violate the availability condition of | Denial-of-service (DoS) attack is an attempt to violate the availability condition of | ||
| Line 38: | Line 38: | ||
* UDP floods (protocol) | * UDP floods (protocol) | ||
* [http://en.wikipedia.org/wiki/SYN_(TCP) SYN] floods (bandwidth) | * [http://en.wikipedia.org/wiki/SYN_(TCP) SYN] floods (bandwidth) | ||
| - | ==Tools for conducting DoS attacks== | + | ==Tools for conducting DoS attacks<sup>[2]</sup>== |
===SSPing=== | ===SSPing=== | ||
[[Image:SmurfAttack.gif|thumb|right|300px|Smurf]] | [[Image:SmurfAttack.gif|thumb|right|300px|Smurf]] | ||
| Line 67: | Line 67: | ||
network also. | network also. | ||
There is a similar tool called Fraggle which uses UDP packets instead. | There is a similar tool called Fraggle which uses UDP packets instead. | ||
| - | ===SYN Flood=== | + | ===SYN Flood<sup>[1]</sup>=== |
With a series of SYN packets, the attacker can drain the victim resources which leads to | With a series of SYN packets, the attacker can drain the victim resources which leads to | ||
rejecting legitimate requests. | rejecting legitimate requests. | ||
| Line 114: | Line 114: | ||
==References== | ==References== | ||
| - | * Stuart McClure, Joel Scambray and George Kurtz, Hacking Exposed—Network Security Secrets & Solutions, Fifth Edition,McGraw-Hill/Osborne, ISBN:9780072260816 | + | * [1] Stuart McClure, Joel Scambray and George Kurtz, Hacking Exposed—Network Security Secrets & Solutions, Fifth Edition,McGraw-Hill/Osborne, ISBN:9780072260816 |
| - | * International Council of Electronic Commerce Consultants, Ethical Hacking and Countermeasures [EC-Council Exam 312-50]—Student Courseware,ISBN No 0972936211 | + | * [2]International Council of Electronic Commerce Consultants, Ethical Hacking and Countermeasures [EC-Council Exam 312-50]—Student Courseware,ISBN No 0972936211 |
| - | * Jelena Mirkovic, Sven Dietrich, David Dittrich, Peter Reiher, Internet Denial of Service: Attack and Defense Mechanisms, Prentice Hall PTR, Print ISBN: 0-13-147573-8 | + | * [3] Jelena Mirkovic, Sven Dietrich, David Dittrich, Peter Reiher, Internet Denial of Service: Attack and Defense Mechanisms, Prentice Hall PTR, Print ISBN: 0-13-147573-8 |
==See also== | ==See also== | ||
| Line 183: | Line 183: | ||
* [http://en.wikipedia.org/wiki/Network_security Network security]<br> | * [http://en.wikipedia.org/wiki/Network_security Network security]<br> | ||
* [http://www.hackforums.net Hacker Forums]<BR> | * [http://www.hackforums.net Hacker Forums]<BR> | ||
| - | --[[User:Luongqt|Luongqt]] | + | * [http://lib.tkk.fi/Diss/2006/isbn9512282151/article1.pdf Mitigating denial of service attacks: A tutorial]<BR> |
| + | |||
| + | --[[User:Luongqt|Luongqt]] 23:45, 12 April 2009 (EDT) | ||
Revision as of 03:45, 13 April 2009
In the world of computer network security, denial-of-service attack is a sneaky and furious monster. It is calm and quite. But when it attacks you, your system will be defeated within minutes (sometimes seconds). What is it? Where does it come from? What can it do? How can you conduct it? Conduct with what? Software or hardware?
Nowadays there are tools available on the Internet that allow attackers to conduct denial-of-service attacks to any vulnerable servers. They are created by black hat hackers for different reasons varying from personal, political reasons to nastiness. Damages from a DoS attack are usually devastating to businesses such as search engines, email providers, banks, e-commerce sites that rely heavily on availability.
On the other hand, although details of denial-of-service attacks are well-known and studied, it is quite difficult to protect any systems from it due to the very nature of the attacks. Scanning tools and other intrusion detection systems can be used to detect attacks or find vulnerable spots which can lead to an DoS attack.
Contents |
Definition[3]
Denial-of-service (DoS) attack is an attempt to violate the availability condition of network security. Its sole purpose is to shut a computer system down or drain all its available resources, which prevents it to serve legitimate users. As computer becomes more and more popular, DoS attack evolves to Distributed DoS (DDoS) attack which amplifies the damage from thousand to million times. The most common technique for conducting DoS attacks is to "flood" the target with information/data. Others aim for the victim's Achilles' heel that cause it to crash.
Fact
- On February 6th, 2000, Yahoo portal was shut down for 3 hours. Then retailer Buy.com Inc. (BUYX) was hit the next day, hours after going public. By that evening, eBay (EBAY), Amazon.com (AMZN), and CNN (TWX) had gone dark. And in the morning, the mayhem continued with online broker E*Trade (EGRP) and others having traffic to their sites virtually choked off. As a result, Yahoo, which relies on advertising for much of its revenue, lost potentially an estimated $500,000 because its users were unable to access Yahoo's Web pages and the advertisements they carried. (Business Week Online, 12 February 2000)
- The FBI's Web site was taken out of service for three hours on 18 February, 2000 by a DDoS attack. (CNN)
- In October 2002, an attacker tried to performed a DDoS attack on the complete set of DNS root servers which have 13 servers of replicated DNS data in total. By a simple form of DDoS attack, he successfully took down 9 of them. The other 4 remained fully functional. The attack lasted only one hour. A longer and stronger attack might have been extremely harmful.
- During the Iraq War in 2003, a DDoS attack was launched on the Qatar-based Al-Jazeera news organization, which broadcast pictures of captured American soldiers. Al-Jazeera attempted to out-provision the attackers by purchasing more bandwidth, but they merely ratcheted up the attack. The Web site was largely unreachable for two days, following which someone hijacked their DNS name, redirecting requests to another Web site that promoted the American cause.
Types of attack
There are basically three types of DoS attack:
- Bandwidth attacks: straight forward, comsume resources.
- Protocol attacks: take advantage of expected behavior of protocols such as TCP, UDP and ICMP.
- Software vulnerability attacks: exploit vulnerabilities in network software, such as a web server, or the underlying TCP/IP stack.
There are many tools for each type such as:
- Sending oversized packets (protocol)
- fragmentation overlap (protocol)
- loopback floods (protocol)
- Application DoS (software)
- UDP floods (protocol)
- SYN floods (bandwidth)
Tools for conducting DoS attacks[2]
SSPing
SSPing, a DoS tool, is a program sends the victim's computer a series of highly fragmented, over-sized ICMP data packets. While trying to put the fragments together, the computer can get into a memory overflow which causes the machine to freeze. With a few packets, the attacker can lock the victim's computer instantaneously. The identity of the attacker is unknown since the connection is lost as the victim restarts the computer. SSPing affects Windows 95/NT and Mac OS. Jolt is a program known for this kind of attack. It will freeze unpatched Windows 95, NT machines by sending a series of spoofed & highly fragmented ICMP packets to the target, which then tries to reassemble the received fragments.
Land Exploit
Land Exploit is a DoS attack in which a program sends a TCP SYN packet where the target and source addresses are the same and port numbers are the same. Receiving such packet causes some TCP implementations to crash the target system or exhaust all CPU resources. The name of the attack comes from the first distributed source code (called "exploit") that made it possible to implement this attack: land.c. Computers running Windows 95 and NT are desired targets of this kind of attack.
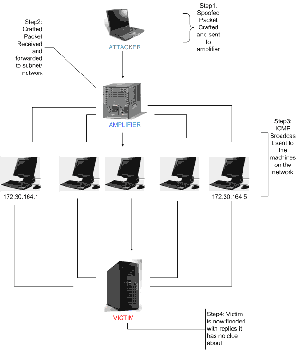
Smurf
Smurf is a simple effective DoS attack involving forged ICMP packets sent to a broadcast address. Attackers spoof the source address on ICMP echo requests and sending them to an IP broadcast address. This causes every machine on the broadcast network to receive the reply and respond back to the source address that was forged by the attacker. This attack results in DoS due to high network traffic which not only hurts the victim but the broadcast network also. There is a similar tool called Fraggle which uses UDP packets instead.
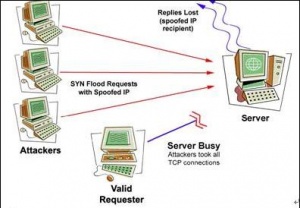
SYN Flood[1]
With a series of SYN packets, the attacker can drain the victim resources which leads to rejecting legitimate requests. System A sends a SYN packet to system B asking to establish a connection via three-way handshake. However the source address of the packet is spoofed thus misleads system B to switch to SYN_RECV state and send an SYN/ACK packet to the spoofed address. These connections are called half-open connections. The source address does not exist and system B can only flush the potential connection once the connection-establishment timer expires. This timer varies from system to system ranging from seconds to minutes. This type of attack is very dangerous because with little resources (e.g. bandwidth), the attacker can take down an industrial strength web server. Moreover, this is a stealth attack since everything (e.g. the packet) look so normal. Today, SYN flood is the primary capacity depletion mechanism for denial of service attacks.
Targa
Targa, written by a German hacker known as Mixter, is a free software packet available on the Internet. It can run 8 different DoS attacks using some of the tools listed above. The attacker can try individual attack or try all attacks until it is successful. The attacker must be logged in with root permissions; since most of the attacks, use IP spoofing that requires root privileges. The attack can be done from any machine on which the targa.c code compiles. Target platforms can be any operating system but the attacks do not have an impact on all operating systems.
The attacks that can be done with the Targa kit:
- Jolt by Jeff W. Roberson
- Land by m3lt
- Winnuke by _eci
- Nestea by humble and ttol
- Syndrop by PineKoan
- Teardrop by route|daemon9
- Bonk by route|daemon9 and klepto
- NewTear by route|daemon9 (a variation of Teardrop)
For further information about these tools, please refer to the references below.
Prevention
You could do the following things to minimize the DoS attack:
- Effective robust design
- Bandwidth limitations
- Keep systems patched
- Run the least amount of services
- Allow only necessary traffic
- Block IP addresses
Due to the power of DoS attacks and the way they work, there is nothing that can be done to prevent a Dos attack entirely.
Conclusion
DoS attacks can happen to anyone with devastating damage. A good network design will help mitigating DoS attacks. It is essential to have filtering capability based on packet header and content within the network or at the critical gateways in order to filter malicious traffic as a response to such attacks while waiting for a permanent solution. It is important to have the relevant referrals in the policy and legislation to address the issue of DoS and DDoS to ensure an effective cooperation between service providers and law enforcement agencies.
References
- [1] Stuart McClure, Joel Scambray and George Kurtz, Hacking Exposed—Network Security Secrets & Solutions, Fifth Edition,McGraw-Hill/Osborne, ISBN:9780072260816
- [2]International Council of Electronic Commerce Consultants, Ethical Hacking and Countermeasures [EC-Council Exam 312-50]—Student Courseware,ISBN No 0972936211
- [3] Jelena Mirkovic, Sven Dietrich, David Dittrich, Peter Reiher, Internet Denial of Service: Attack and Defense Mechanisms, Prentice Hall PTR, Print ISBN: 0-13-147573-8
See also
- Cell BE - A Network on a Chip
- Digital Enhanced Cordless Telecommunications (DECT)
- Internet Control Message Protocol
- Denial Of Service Attacks
- Wi-Fi
- Cryptography in Information Security
- Hypertext Transfer Protocol over Secure Socket Layer (HTTPS)
- Bluetooth
- The practicality of IPv6
- Dynamic Host Configuration Protocol (DHCP)
- Social Network Service
- Keystroke Logging: Are You Next
- Network Latency
- Onion Routing
- Radio Frequency Identification (RFID)
- 3G Communications
- Security in Smartphones
- Credit Card Chip Security and Technology
- Address Resolution Protocol (ARP)
- How to Connect to the Internet via an ISP
- CAPTCHA
- Security for Small Home Networks
- Rootkits
- Proxy Server
- Network Firewall
- Steganography and Digital Watermarking
- Malware
- Peer-to-Peer Network Security
- High-Speed Downlink Packet Access (HSDPA)
- Man in the Middle Attack
- Network Attached Storage
- RSA Encryption Algorithm
- Corporate Security and IT Policies
- Ethical Hacking
- Extensible Messaging and Presence Protocol (XMPP)
- Cloud Computing
- Ethernet Routing Devices
- Personal Data Protection and Privacy
- Public Key Authentication
- AJAX Security
- Network Topology
- IP Spoofing
- WLAN Standard 802.11n
- Domain Name System
- Web 2.0
- Local Area Network
- Bots & Botnets
- Trivial File Transfer Protocol
- Load Balancing for Network Servers
- Simple Mail Transfer Protocol (SMTP)
- Email Security
- Data Encryption for Storage Devices
- Statistics of Internet Threats
- VoIP
- Deep Packet Inspection
- Fingerprint Authentication
- Multicasting
- MD5 Rainbow Tables
- The Interplanetary Internet
External links
- Denial-of-service Attacks
- Network security
- Hacker Forums
- Mitigating denial of service attacks: A tutorial
--Luongqt 23:45, 12 April 2009 (EDT)