Proxy Server
From Computing and Software Wiki
| Line 2: | Line 2: | ||
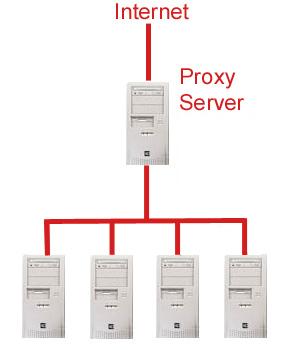
A '''proxy server''' is a server that acts as a liaison between a client seeking resources and a server that can provide that resource. The client makes a request to the proxy, which then evaulates the request according to its pre-set filtering rules. If the request is validated, the proxy makes the request of the target server on behalf of the client and provides the resource to the client. Sometimes the proxy server may modify the client's request or the server's response based on the filtering rules, and may even contact a server different than the specified one in order to provide the requested resource. Proxies are used to ensure security, administrative control and caching services. | A '''proxy server''' is a server that acts as a liaison between a client seeking resources and a server that can provide that resource. The client makes a request to the proxy, which then evaulates the request according to its pre-set filtering rules. If the request is validated, the proxy makes the request of the target server on behalf of the client and provides the resource to the client. Sometimes the proxy server may modify the client's request or the server's response based on the filtering rules, and may even contact a server different than the specified one in order to provide the requested resource. Proxies are used to ensure security, administrative control and caching services. | ||
| + | |||
| + | There are three very good reasons to use a proxy server: | ||
| + | 1. Prevents the necessity of direct TCP/UDP connections | ||
| + | 2. Can relay requests across a firewall | ||
| + | 3. Fewer bad things happen! | ||
== Functionality == | == Functionality == | ||
| Line 20: | Line 25: | ||
=== Credential-based Kerberos Services === | === Credential-based Kerberos Services === | ||
A Secured Over Credential-based Kerberos Services (SOCKS) proxy server simply provides the task of transferring data from a client to a server using any number of protocols so that according to the point of view of an Internet web server, the SOCKS server appears to be a client in itself. Because a SOCKS proxy server does not add anything from itself or change the data it is transferring from the true client, anonymity of this type of proxy server is really always absolute.[2] | A Secured Over Credential-based Kerberos Services (SOCKS) proxy server simply provides the task of transferring data from a client to a server using any number of protocols so that according to the point of view of an Internet web server, the SOCKS server appears to be a client in itself. Because a SOCKS proxy server does not add anything from itself or change the data it is transferring from the true client, anonymity of this type of proxy server is really always absolute.[2] | ||
| - | |||
Revision as of 03:34, 4 April 2009
A proxy server is a server that acts as a liaison between a client seeking resources and a server that can provide that resource. The client makes a request to the proxy, which then evaulates the request according to its pre-set filtering rules. If the request is validated, the proxy makes the request of the target server on behalf of the client and provides the resource to the client. Sometimes the proxy server may modify the client's request or the server's response based on the filtering rules, and may even contact a server different than the specified one in order to provide the requested resource. Proxies are used to ensure security, administrative control and caching services.
There are three very good reasons to use a proxy server: 1. Prevents the necessity of direct TCP/UDP connections 2. Can relay requests across a firewall 3. Fewer bad things happen!
Contents |
Functionality
A proxy server receives a request for a service (such as a Web page request) from a client. If it passes filtering requirements, the proxy server generally looks in its local cache of previously downloaded Web pages. If the page is found for example, the proxy returns it to the client without forwarding the request to the destination server. Otherwise, the proxy server acts as a client on behalf of the user and uses one of its own IP addresses to request the page from the server out on the Internet. When the page is returned, the proxy server relates it to the original request and forwards it on to the user.
To a user the proxy server is essentially non-existent; all Internet requests and returned responses appear to be directly with the addressed server. It should be noted however that the proxy is not necessarily invisible; its IP address has to be specified within the configuration options of the protocol program.[1]
An advantage of proxy servers is that all clients can theoretically access its cache. If one or more websites are frequently requested, these are likely to remain in the cache and improve response time. In fact, there are special proxy servers called cache servers. To this end, a proxy can also do logging. In addition, a proxy server can be separate or in the same machine as a firewall server and maintain the same functionality.
There are several ways in which proxy servers can accept and send data through sets of instructions called protocols.
Hypertext Transfer Protocol
The most common type of proxy, the Hypertext Transfer Protocol (HTTP) proxy server provides a means to access a website without being identified. The server simply connects to the specified webpage with an anonymous IP address so that yours is not used. There are, of course, ways that websites may know you are using a proxy server, but the site administrator will have absolutely no way of knowing who you really are. This is the brilliance of such technology, that common, everyday users can bypass a secure network by using a proxy site to do their dirty work.
File Transfer Protocol
File Transfer Protocol (FTP) is used to transfer information from one computer to another computer by using a network or server. An FTP proxy server is used to gain access to a network when the machine you are using does not have an internet connection, but does have access to a machine that has internet connection. This can also be used if your machine is blocked by a firewall and can not access the web site that you wish to connect to.
Credential-based Kerberos Services
A Secured Over Credential-based Kerberos Services (SOCKS) proxy server simply provides the task of transferring data from a client to a server using any number of protocols so that according to the point of view of an Internet web server, the SOCKS server appears to be a client in itself. Because a SOCKS proxy server does not add anything from itself or change the data it is transferring from the true client, anonymity of this type of proxy server is really always absolute.[2]
Classification of Proxy Servers
There are many different types of proxy servers that provide similar functionality but differ in practice. Depending on the required purpose you can get proxy servers to route any of the common protocols mentioned above, but there are further classifications for a proxy.
Open Proxy
An open proxy is a proxy server which will accept client connections from any IP address and make connections to any Internet resource.
Transparent Proxy
This type of proxy server identifies itself as a proxy server and also makes the original IP address available through the http headers. These are generally used for their ability to cache websites and do not effectively provide any anonymity to those who use them. However, the use of a transparent proxy will get you around simple IP bans. They are transparent in the terms that your IP address is exposed, not transparent in the terms that you do not know that you are using it (your system is not specifically configured to use it.)
Anonymous Proxy
This type of proxy server indentifies itself as a proxy server, but does not make the original IP address available. This type of proxy server is detectable, but provides reasonable anonymity for most users.
High Anonymity Proxy
This type of proxy server does not identify itself as a proxy server and does not make available the original IP address.
Distorting Proxy
This type of proxy server identifies itself as a proxy server, but makes an incorrect original IP address available through the http headers.
Risks of Using a Proxy Server
Although proxy servers are perfectly legal, there are other dangers that you leave yourself vulnerable to when using a proxy.
Data Interception
Because proxy servers intercept data, there’s always the risk of the administrators of that proxy site to steal your information, such as account details to a website, personal identification like phone numbers, house address, or even your social security number (SSN) and credit card numbers. This is why it is very important for you to safeguard your information when using a proxy site by taking every possible measure to keep your identity a secret.
Be sure to check the proxy site for a Terms of Service link or a Privacy Policy so you know exactly what you’re getting yourself into. Sometimes, the proxy site will hide valuable information like that so you will just use their service without thinking about it. Even if they don’t, how many of us really read the terms of service and all that? Very few. So be sure to protect your information by looking through the site very carefully before you use it to enter any sensitive data into a form.
Also, if the website is not known and trusted or appear to have a good integrity, do not use it. This would only prove to endanger your information instead of finding a good proxy site to use. Keep this in mind before you use a proxy server next time or perhaps, your first time at all.
Proxy Transparency
Many organizations — including corporations, schools, and families — use proxy servers to enforce network use policies or provide security and caching services. Usually, the web proxy is not transparent to the client application: it must be configured to use the proxy, manually or with a configuration script. Thus, the user can evade the proxy by simply resetting the client configuration, except in the case where the proxy is used instead of a NAT router to share an internet connection or a LAN.
Open Proxy Abuse
Abuse of open proxies is currently implicated in a significant portion of e-mail spam delivery. Spammers frequently install open proxies on unwitting end users' Microsoft Windows computers by means of computer viruses designed for this purpose. Internet Relay Chat (IRC) abusers also frequently use open proxies to cloak their identities.
Because proxies could be implicated in abuse, system administrators have developed a number of ways to refuse service to open proxies. IRC networks such as the Blitzed network automatically test client systems for known types of open proxy. Likewise, an email server may be configured to automatically test e-mail senders for open proxies, using software such as Michael Tokarev's proxycheck.
Groups of IRC and electronic mail operators run DNSBLs publishing lists of the IP addresses of known open proxies, such as Blitzed OPM and CBL.
The ethics of automatically testing clients for open proxies are controversial. Some experts, such as Vernon Schryver, consider such testing to be equivalent to an attacker portscanning the client host. Others consider the client to have solicited the scan by connecting to a server whose terms of service include testing.
References
See Also
- Internet Control Message Protocol (ICMP)
- Denial Of Service Attacks
- Cryptography in Information Security
- Tools for Conducting Denial of Service Attacks
- Hypertext Transfer Protocol over Secure Socket Layer (HTTPS)
- Bluetooth
- IPv6
- Dynamic Host Configuration Protocol (DHCP)
- Social Network Services
- Network Latency
- Onion Routing
- Radio Frequency Identification
- 3G Communications
- Security in Smartphones
- Credit Card Chip Security and Technology
- Address Resolution Protocol (ARP)
- How to Connect to the Internet via an ISP
- CAPTCHAs
- Security for Small Home Networks
- Rootkits
- Network Firewalls
- Steganography and Digital Watermarking
- Malware
- High-Speed Downlink Packet Access (HSDPA)
- Network Attached Storage (NAS) Devices
- Corporate Security and IT Policies
- Ethical Hacking
- Extensible Messaging and Presence Protocol (XMPP)
- Cloud Computing
- Ethernet Routing Devices
- Public Key Authentication
- AJAX Security
- Network Topology
- WLAN Standard 802.11n
- Domain Name System (DNS)
- Web 2.0
- Local Area Networks
- Botnets
- Trivial FTP
- Simple Mail Transfer Protocol (SMTP)
- Email Security
- Data Encryption for Storage Devices
- Statistical Analysis of Internet Security Threats
- Voice over IP (VoIP)
- Deep Packet Inspection
- Fingerprint Authentication
- MD5 Rainbow Tables
- The Interplanetary Internet
External Links
- Safe Proxy Tools at How-To-Hide
- Anonymous Proxy Risks at ExperienceFestival
- Proxy Server at WhatIs.com
- Types of Proxy Sites at How-To-Hide
- Open Proxies at WhatIsMyIP
--Eversom 14:12, 12 March 2009 (EDT)