Steganography and Digital Watermarking
From Computing and Software Wiki
| (127 intermediate revisions not shown) | |||
| Line 10: | Line 10: | ||
== What is Steganography? == | == What is Steganography? == | ||
| - | |||
| - | |||
| + | [[Image:steg2.png|right|250px|Theoretical: Secret information is hidden within the image file]] | ||
| + | |||
| + | Steganography is the method of concealing a message, and its | ||
| + | very existence is a secret and only known to the person(s) who placed it. Historical steganography involved disappearing inks and masking letters to hide the information. While modern steganography, information hiding involves hiding data in digital media where by slightly altering the media causes a message to be embedded without anyone noticing any loss to the actual media file. Since steganography is a form of "[http://en.wikipedia.org/wiki/Security_through_obscurity security through obscurity]", where it protects the messages and the known parties through secrecy, it is often combined with cryptography so that even if the message is found, it still cannot be read. <sup>[9]</sup> | ||
| + | |||
| + | <br><br><br><br><br><br><br> | ||
== What is Digital Watermarking? == | == What is Digital Watermarking? == | ||
| + | [[Image:cov2watermark.png|right|250px|File displaying both visible and invisible watermarks]] | ||
| + | Digital watermarking is the process of embedding a symbol of some sort into the media file to distinguish the file from others. The embedded watermark is meant to be permanent and follows a process in which there is alterations to the media file. Digital watermarking can be hidden or seen in plain sight by other parties. Deciding on whether to use visible/invisible watermarking depends on the function of the media file, but with either technique, when the media file is copied the digital watermark gets copied as well. Digital watermarks are designed in such a way that they do not restrict the media file or change the media file in such a way it detracts the quality. Its main purpose is to detect misuse and act as a form of signature from the owner. <sup>[5]</sup> | ||
| - | + | <br><br><br><br><br><br> | |
| Line 22: | Line 28: | ||
The word steganography was derived from the Greek words steganos, which means "covered", and | The word steganography was derived from the Greek words steganos, which means "covered", and | ||
| - | graphia, which means "writing". The first recorded entry of the use of steganography is in the story of Herodotus and his slaves. Where he shaved the heads of his slaves and tattooed secret messages on their scalps. He would than let their hair grow back to hide the message and send his slaves to deliver the messages to other leaders. Since than, many early proposed steganographic techniques have been created from hiding messages in jewelery, to modifying letter strokes and sizes, and placing a mask over text. Many of these techniques are still used today and were used during World War I and II. | + | graphia, which means "writing". The first recorded entry of the use of steganography is in the story of [http://en.wikipedia.org/wiki/Herodotus Herodotus] and his slaves. Where he shaved the heads of his slaves and tattooed secret messages on their scalps. He would than let their hair grow back to hide the message and send his slaves to deliver the messages to other leaders. Since than, many early proposed steganographic techniques have been created from hiding messages in jewelery, to modifying letter strokes and sizes, and placing a mask over text. Many of these techniques are still used today and were used during World War I and II. |
| - | Other techniques that were more sophisticated that were used as well during the wars were microdots, which were microscopic images that were shrunk to resemble tiny specs of dirt. These microdots were placed on a person or in a letter and were used to transmit vital information or locations. From this moment and with the emergence of the Internet, steganographic techniques began increasing. Due to the amount of computer networks and digitalized media, covert steganography became favorable to communicate between parties. There have been many uses of steganography, good and bad, in which they provide an extra layer of security for businesses but could also be used by criminals for illegal means. | + | Other techniques that were more sophisticated that were used as well during the wars were microdots, which were microscopic images that were shrunk to resemble tiny specs of dirt. These microdots were placed on a person or in a letter and were used to transmit vital information or locations. From this moment and with the emergence of the Internet, steganographic techniques began increasing. Due to the amount of computer networks and digitalized media, covert steganography became favorable to communicate between parties. There have been many uses of steganography, good and bad, in which they provide an extra layer of security for businesses but could also be used by criminals for illegal means. <sup>[11]</sup> |
| Line 31: | Line 37: | ||
than. However in the eighteenth century, paper made in Europe and America using watermarking | than. However in the eighteenth century, paper made in Europe and America using watermarking | ||
technology was to ensure trademarks, track when the paper was created, indicate size of the | technology was to ensure trademarks, track when the paper was created, indicate size of the | ||
| - | sheets, and prevent counterfeiting. | + | sheets, and prevent counterfeiting. <sup>[10]</sup> |
| - | + | ||
| - | + | ||
| - | + | ||
| + | Counterfeiting especially, caused watermarking technology to rapidly increase as there were those attempting to stop counterfeiters and those attempting to remove or copy the watermarks. From the basic imprints on paper, watermarks moved onto color where dyed ink was inserted into the paper during the molding process. The next advancement was to create a raise in the paper causing a slight bump on the surface, which is commonly seen on paper currency today. Finally, the idea of digital watermarking appeared between in 1979, where Szepanski discussed a machine that could be used on documents which would place a pattern for anti-counterfeiting purposes. In 1988, Holt described a way of embedding an identification code in an audio signal and the term digital watermark first appeared. It was only until 1995 that the world became vastly interested in the idea of digital watermarks. From then on, many papers were released discussing ways of implementing digital watermarks and companies ranging from the music industry to business software began using this technique for security and protection. <sup>[8]</sup> <br><br> | ||
== Applications == | == Applications == | ||
Since the emergence of the Internet, digital distribution of media and documents has vastly increased and is constantly increasing every year. On this note, the distribution of copyright material has always been a concern for people trying to protect their work and this is where digital watermarking can become useful. Those who are worried of people eavesdropping on their conversations by email, important documents being read, or video chat being seen by others can use steganographic techniques to protect themselves. In order to know what applications these techniques can be used for, it is best to know the different ways of implementing the techniques. Steganography and digital watermarking can be broken down into four different subcategories in which the existence of the technique is either known or unknown to the public along with the original file. | Since the emergence of the Internet, digital distribution of media and documents has vastly increased and is constantly increasing every year. On this note, the distribution of copyright material has always been a concern for people trying to protect their work and this is where digital watermarking can become useful. Those who are worried of people eavesdropping on their conversations by email, important documents being read, or video chat being seen by others can use steganographic techniques to protect themselves. In order to know what applications these techniques can be used for, it is best to know the different ways of implementing the techniques. Steganography and digital watermarking can be broken down into four different subcategories in which the existence of the technique is either known or unknown to the public along with the original file. | ||
| - | <center>[[Image:sandwtable.png]]</center> | + | <center>[[Image:sandwtable.png|Subcategories of Steganography and Watermarking]]</center> |
| - | Covert watermarking is embedding a watermark related to the recipient of each copy of the file, but unaware that the watermark exists. Thus, if the file is leaked to third parties, the recipient who leaked the file can be traced. Covert steganography is embedding data unrelated to the original work. An overt watermark is when the presence of the watermark is known to others besides the creators, whether visually or told of the watermark. Overt steganography is similar to covert steganography in terms of the hidden information is unrelated to the signal in which it is embedded in. However with overt steganography, the information is only hidden to certain parties but visible to others, example timestamps. | + | Covert watermarking is embedding a watermark related to the recipient of each copy of the file, but unaware that the watermark exists. Thus, if the file is leaked to third parties, the recipient who leaked the file can be traced. Covert steganography is embedding data unrelated to the original work. An overt watermark is when the presence of the watermark is known to others besides the creators, whether visually or told of the watermark. Overt steganography is similar to covert steganography in terms of the hidden information is unrelated to the signal in which it is embedded in. However with overt steganography, the information is only hidden to certain parties but visible to others, example timestamps. <sup>[7]</sup> |
Knowing the subcategories allows for the following possible applications for both steganography and digital watermarking. Some applications may use both techniques depending on the function required. | Knowing the subcategories allows for the following possible applications for both steganography and digital watermarking. Some applications may use both techniques depending on the function required. | ||
| + | |||
===Steganography=== | ===Steganography=== | ||
| - | Some applications of steganography are: | + | Some applications of steganography are <sup>[7]</sup>: |
| - | * Protection of Data Alteration - "Digital Certificates" act as a way of protecting data by embedding the information. | + | * Protection of Data Alteration - "[http://en.wikipedia.org/wiki/Digital_certificate Digital Certificates]" as an example, act as a way of protecting data by embedding the information. |
* Confidential Communication - Where steganographic techniques could provide a way of communicating between two parties without others knowing. | * Confidential Communication - Where steganographic techniques could provide a way of communicating between two parties without others knowing. | ||
* Media Database Systems - Use of embedded messages in files to quickly identify them. | * Media Database Systems - Use of embedded messages in files to quickly identify them. | ||
| - | * Access Control - Using access keys to extract content from a steganographic file. | + | * Access Control - Using access keys to extract content from a steganographic file.<br><br> |
| - | + | ||
| - | + | ||
===Digital Watermarking=== | ===Digital Watermarking=== | ||
| - | Some applications that use digital watermarking are: | + | Some applications that use digital watermarking are <sup>[5,6]</sup>: |
* Broadcast Monitoring - Identifying where and when the media files are being broadcast by looking at the embedded watermarks. | * Broadcast Monitoring - Identifying where and when the media files are being broadcast by looking at the embedded watermarks. | ||
| Line 63: | Line 66: | ||
* Transaction Tracking - Track media files that were illegally distributed or to determine the route the file took. | * Transaction Tracking - Track media files that were illegally distributed or to determine the route the file took. | ||
* Content Authentication - The embedded watermarks can add as signatures where the information can be used to authenticate the originality of the file. | * Content Authentication - The embedded watermarks can add as signatures where the information can be used to authenticate the originality of the file. | ||
| - | * Copy Control - Watermarks can be used in recording equipment to determine what content may | + | * Copy Control - Watermarks can be used in recording equipment to determine what content may be copied. |
* Device Control - Watermarks can be used to make devices react a certain way and display certain content. | * Device Control - Watermarks can be used to make devices react a certain way and display certain content. | ||
| - | * Legacy Enhancement - Watermarks can be used to improve functionality of existing systems. | + | * [http://en.wikipedia.org/wiki/Legacy_system Legacy] Enhancement - Watermarks can be used to improve functionality of existing systems. |
| - | + | ||
| - | + | ||
| - | + | ||
| + | Companies all over the world have been creating software programs to be used for the above applications. Commonly used programs for steganography are [http://www.steganos.com/ Steganos], [http://www.steganos.com/ Stego Suit], and [http://www.stealthencrypt.com/ Stealthencrypt]. Software used for digital watermarking are [http://www.visualwatermark.com/ Visual Watermark], [http://www.watermarker.com/watermark-protector/ Ais Watermark], and [http://www.watermarksoft.com/ WatermarkIt]. Encryption methods and watermarking schemes offer others the satisfaction of knowing that their data has an extra layer of protection from prying eyes.<br><br> | ||
== Properties == | == Properties == | ||
| - | Both methods can be illustrated by properties depending upon the application and the role each method will play. | + | Both methods can be illustrated by properties depending upon the application and the role each method will play. Properties are an important part for both methods as by weighing what properties matter to you based on the method for your application will determine the effectiveness of the system. Since for each method there are many different implementation techniques, the properties that apply to one method are different to that of another since each method list different priorities. Below are the common properties commonly associated with the two methods. |
=== Properties of Steganographic Systems === | === Properties of Steganographic Systems === | ||
| - | Some properties of steganography are: | + | Some properties of steganography are <sup>[7]</sup>: |
| - | * Security - The ability to resist attacks whether passive, active, or malicious. | + | * [http://en.wikipedia.org/wiki/Information_security Security] - The ability to resist attacks whether passive, active, or malicious. |
* Embedding Capacity - The maximum number of bits that can be hidden in a given media file. | * Embedding Capacity - The maximum number of bits that can be hidden in a given media file. | ||
* Blind or Informed Extraction - Whether the other party has a copy of the original file. | * Blind or Informed Extraction - Whether the other party has a copy of the original file. | ||
| Line 84: | Line 85: | ||
* Statistical Undetectability - The probability of detecting a steganographic technique based off assumptions. | * Statistical Undetectability - The probability of detecting a steganographic technique based off assumptions. | ||
* False Alarm Rate - The probability that an algorithm will detect and report the presence of a secret message when there is none. | * False Alarm Rate - The probability that an algorithm will detect and report the presence of a secret message when there is none. | ||
| - | * Stego Key - | + | * Stego Key - Possibility of using a publicly known algorithm to embed a secret message into the media file.<br><br> |
| - | + | ||
| - | + | ||
=== Properties of Watermarked Systems === | === Properties of Watermarked Systems === | ||
| - | Some properties of digital watermarking are: | + | Some properties of digital watermarking are <sup>[5,7]</sup>: |
| - | * Robustness - The ability of the watermark to survive processing of content. | + | * [http://en.wikipedia.org/wiki/Robustness Robustness] - The ability of the watermark to survive processing of content. |
| - | * Security - The ability of the watermark to prevent attacks or removal. | + | * [http://en.wikipedia.org/wiki/Information_security Security] - The ability of the watermark to prevent attacks or removal. |
* Embedding Effectiveness - The probability that the embedder will successfully embed the watermark in a random media file. | * Embedding Effectiveness - The probability that the embedder will successfully embed the watermark in a random media file. | ||
| - | * Fidelity - The perceptive quality of a watermarked content. | + | * [http://en.wikipedia.org/wiki/Fidelity Fidelity] - The perceptive quality of a watermarked content. |
* Data Payload - The amount of information that can be carried in the watermark. | * Data Payload - The amount of information that can be carried in the watermark. | ||
| - | * | + | * Transparency - The level of the opacity required to make the watermark visible or invisible. |
| - | * False Positive Rate - The rate in which the watermark will be falsely detected in | + | * False Positive Rate - The rate in which the watermark will be falsely detected in non-watermarked files. |
* Modification and Multiple Watermarks - The possibility of changing the watermark or embedding multiple watermarks. | * Modification and Multiple Watermarks - The possibility of changing the watermark or embedding multiple watermarks. | ||
| - | * Cost - The cost required to embed the watermark into the digital file. | + | * Cost - The cost required to embed the watermark into the digital file.<br><br> |
| + | == Model and Techniques == | ||
| + | Steganography and digital watermarking are two different techniques, however they both share similar qualities. Both techniques follows the same basic model in which two inputs (a signal and the original file) go into an embedder. The signal corresponds to the digital watermark or the secret message and the embedder function contains an algorithm that will produce a watermarked file. The output from the embedder is than transmitted or recorded. The recorded file is than sent to a third party in which the possibility of a modification, whether malicious or not, could arise. The recorded file, modified or not, is than sent as input to a detector in which the algorithm tries to determine if the signal is present. If it is, the watermark or secret message can usually be extracted depending on the properties. <sup>[10]</sup> | ||
| - | + | [[Image:lifecycle.png|thumb|center|1050px|<center>Basic life-cycle model</center>]] | |
| - | + | For all the applications steganography and digital watermarking can be applied to, there have been many different techniques and variations. Below are a list of the most popular techniques currently being used today in digital media. | |
| - | + | === Steganography Techniques === | |
| - | + | Some techniques of steganography are <sup>[3]</sup>: | |
| - | === | + | ==== Least Significant Bit Insertion ==== |
| + | [http://en.wikipedia.org/wiki/Least_significant_bit Least Significant Bit] (LSB) insertion is having the rightmost bit of a binary number inserted with a different value. Which means that for every 8-bit binary number of an image, the LSB is replaced with 1-bit from the hidden message. The downside of this technique is that if the media file, say an image, is ever converted from one format to another (GIF to JPEG) the information in the message could be distorted. | ||
| - | + | <center>[[Image:lsb.png|Example of LSB insertion in a 24-bit image]]</center> | |
| - | |||
| - | + | ==== Masking and Filtering ==== | |
| + | The [http://en.wikipedia.org/wiki/Mask_(computing) masking] and filtering technique hides the secret message by integrating the message into the [http://en.wikipedia.org/wiki/Image_noise noise] level of the original file. The noise level is the redundant portion of the image and allows for the message to hide in this area. Thus, this technique will be able to protect the message from image processing and conversion. However, this technique is usually only suitable for 24-bit and gray-scaled images. | ||
| - | |||
| - | + | ==== Algorithms and Transformations ==== | |
| - | + | ||
| + | Algorithms and transformations technique uses mathematical functions in compression algorithms to hide the secret messages. This technique hides the data bits in the least significant coefficients. This technique is used on JPEG images or files using lossy compression as these files use the [http://en.wikipedia.org/wiki/Discrete_cosine_transform discrete cosine transform] (DCT) to achieve its image compression. By altering the coefficients of DCT, the secret message changes the relation of the coefficients to one another instead of the actual bits themselves.<br><br> | ||
| + | === Digital Watermarking Techniques === | ||
| + | |||
| + | Some techniques of digital watermarking are <sup>[4]</sup>: | ||
| + | |||
| + | ==== Least Significant Bit Modification ==== | ||
| + | |||
| + | Least Significant Bit (LSB) modification is the same process as that of Steganography and the watermark can be embedded multiple times if the watermark is small enough. Adding to the LSB algorithm, is to have a pseudo-random generator in which where the watermark is placed is random. Thus if the watermark undergoes an attack and one of the watermarks survive, than the process would be a success. The downside of LSB is that its not robust enough where any form of conversion would destroy the watermark. As well, if an outside party does discover the algorithm of the watermark, they would only need to change the last bit of each pixel to 1 and this would not deteriorate the overall quality of the media file. | ||
| + | |||
| + | |||
| + | ==== Correlation-Based Techniques ==== | ||
| + | |||
| + | Correlation-Based Techniques use the correlation properties of additive pseudo-random noise patterns and adding it to the media file. Thus, by multiplying a gain to the watermark and adding it to the image would result in a robust watermarked image depending on how large the gain was set to. The strength on this technique is that the image can be divided into multiple parts and the watermark can be added to each part. Additional filters can be added onto this technique to increase the chance of the watermark surviving an attack, such as pre-filtering the image to reduce the correlation of the gain to the original work or to use a [http://en.wikipedia.org/wiki/Spread_spectrum CDMA Spread-Spectrum]to scatter the bits. | ||
| + | |||
| + | |||
| + | ==== Frequency Domain Techniques ==== | ||
| + | |||
| + | Frequency Domain Techniques embeds the watermark in the Discrete Cosine Transform (DCT) where the image is broken down into different frequency bands. This makes it easy to place the watermark as the bands chosen are the middle bands with low frequencies in order to make the watermark less obvious on the image. This causes the watermark to be robust and resistant against lossy compression or image degradation. Other techniques can be merged with this one, such as the pseudo noise patterns in order to protect the watermark even further. | ||
| + | |||
| + | |||
| + | ==== Wavelet Watermarking Techniques ==== | ||
| + | |||
| + | Wavelet Watermarking techniques uses the [http://en.wikipedia.org/wiki/Discrete_Wavelet_Transform Discrete Wavelet Transform] (DWT) to separate the image into different resolutions. Once the image has been separated, the watermarked image can be embedded into these regions. The reason to use such a technique is that higher quality watermarks can be added, which in turns increases the robustness of the watermark without impacting the image quality. The CDMA spread-spectrum can again be added to this technique in order to increase the security of the watermark. It has also been said this technique would be able to survive attacks such as conversion and image altering.<br><br> | ||
| + | == Countermeasures == | ||
| + | |||
| + | Countermeasures or detection techniques against covert steganography or watermarking requires the use of the light spectrum, magnification lenses, chemical mixtures, search algorithms, and others are used to determine if a file has been embedded with either these techniques. The use of the light spectrum, and chemical mixtures can only be used for hard copy works of the media files in question. Magnification lenses can be used on both hard copies and digital copies to magnify the image to a size where the watermarked or hidden message can be found. Search algorithms can be done by hand, however it can be quite difficult and is usually done by computers and is the most likely used form of detection. As there are companies creating software to protect secret messages and embed watermarks into files, there are also companies creating software to remove and detect encoded files. <sup>[2]</sup> | ||
| + | |||
| + | In steganography, the detection of steganographic messages is called steganalysis where the algorithm takes the original file and compares it to the file that is thought to have the secret message. However this only works if a known clean copy of the original is available. In digital watermarking, the technique of watermark detection, informed detection, is used to find invisible watermarks. Watermark detection can follow the same principle algorithm that steganalysis goes through by obtaining the original work and comparing it with one that is believed to have the invisible watermark. Another way of detecting invisible watermarks is by blind detection, where the detecting algorithm is provided with limited information of the original work to find the watermark. <sup>[9]</sup> Thus as you can see, although steganography and watermarking are very effective, there are ways for them to be removed or detected. For every technique, there must be a way of detection as the rightful owners need a way of checking/tracking their work and thus if those with illegal intentions discover the way of detection, they too can find and remove the methods.<br><br> | ||
| + | == References == | ||
| + | # [http://encyclopedia.jrank.org/articles/pages/6725/Digital-Watermarking.html Digital Watermarking - Common watermarking techniques, Important parameters, Applied mechanisms, Applications, Invertible watermarking, Content-fragile watermarking]. 2009. Retrieved April 7, 2009.<br> | ||
| + | # [http://enterpriseinnovator.com/index.php?articleID=14174§ionID=25 Document Fraud and Technology, a Double-Edged Sword ]. 2008. Retrieved April 8, 2009.<br> | ||
| + | # [http://www.infosyssec.com/infosyssec/Steganography/techniques.htm Steganography Techniques]. 2009. Retrieved April 2, 2009.<br> | ||
| + | # [http://www.vu.union.edu/~shoemakc/watermarking/watermarking.html Hidden Bits: A Survey of Techniques for Digital Watermarking]. 2002. Retrieved April 6, 2009.<br> | ||
| + | # [http://www.watermarkingworld.org/faq.html Watermarking FAQ]. 2005. Retrieved April 7, 2009.<br> | ||
| + | # Arnold, Michael Konrad and Schmucker, Martin. [http://books.google.ca/books?id=iVEOYEukfmUC&printsec=frontcover&dq=watermark+techniques&source=gbs_summary_r&cad=0 Techniques and Applications of Digital Watermarking and Content Protection]. Published by Artech House, 2003. <br> | ||
| + | # Cox, Ingemar J. , Miller, Matthew., Bloom, Jeffrey ., Fridrich, Jessica ., and Kalker, Ton. [http://books.google.ca/books?id=Uo-qf5GiBPgC&printsec=frontcover&dq=steganography+watermark&source=gbs_summary_r&cad=0 Digital Watermarking and Steganography]. Published by Morgan Kaufmann, 2007. <br> | ||
| + | # Cox, Ingemar J., Miller, Matthew L. and Bloom, Jeffrey A. [http://books.google.ca/books?id=nkomUUXASpcC&printsec=frontcover&dq=steganography+watermark&source=gbs_summary_r&cad=0 Digital watermarking]. Published by Morgan Kaufmann, 2002. <br> | ||
| + | # Johnson, Neil F., Duric, Zoran., and Jajodia, Sushil. [http://books.google.ca/books?id=OWhPeGK93VcC&printsec=frontcover&dq=steganography&source=gbs_summary_r&cad=0 Information Hiding]. Published by Springer, 2001. <br> | ||
| + | # Pan, Jeng-Shyang and Huang, Hsiang-Cheh. [http://books.google.ca/books?id=tatqoONPzHUC&printsec=frontcover&dq=watermark+techniques&source=gbs_summary_r&cad=0 Intelligent watermarking techniques]. Published by World Scientific, 2004.<br> | ||
| + | # Wayner, Peter. [http://books.google.ca/books?id=ymjTAqsG2hoC&dq=disappearing+cryptography Disappearing cryptography]. Published by Morgan Kaufmann, 2002.<br><br> | ||
== See Also == | == See Also == | ||
| Line 133: | Line 173: | ||
* [[CAPTCHA]] | * [[CAPTCHA]] | ||
* [[Personal Data Protection and Privacy]] | * [[Personal Data Protection and Privacy]] | ||
| - | |||
* [[Data Encryption for Storage Devices]] | * [[Data Encryption for Storage Devices]] | ||
* [[Conventional Encryption Algorithms]] | * [[Conventional Encryption Algorithms]] | ||
* [[Information security awareness]] | * [[Information security awareness]] | ||
| - | * [[Digital Signatures]] | + | * [[Digital Signatures]]<br><br> |
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
== External Links == | == External Links == | ||
| Line 154: | Line 189: | ||
---- | ---- | ||
| - | --[[User:Ganv|Ganv]] | + | --[[User:Ganv|Ganv]] 10:33, 12 April 2009 (EDT) |
Current revision as of 14:33, 12 April 2009
Steganography and Digital Watermarking are both forms of information hiding where the context can be viewed as keeping the information a secret or making the information subtle respectively. Both these methods have been around for a long time, at least several centuries, however they have only gained worldwide popularity in the digital world since roughly the mid 1990s. With new technologies constantly emerging, these two methods have been used to prevent theft, prevent plagiarism, track, and hide secrets among other things. There is not one standard way of implementing these techniques and each version differs from one another. Thus, with the vast amount of applications these techniques can be applied to, many companies have made software to create and detect both techniques.
Contents |
What is Steganography?
Steganography is the method of concealing a message, and its very existence is a secret and only known to the person(s) who placed it. Historical steganography involved disappearing inks and masking letters to hide the information. While modern steganography, information hiding involves hiding data in digital media where by slightly altering the media causes a message to be embedded without anyone noticing any loss to the actual media file. Since steganography is a form of "security through obscurity", where it protects the messages and the known parties through secrecy, it is often combined with cryptography so that even if the message is found, it still cannot be read. [9]
What is Digital Watermarking?
Digital watermarking is the process of embedding a symbol of some sort into the media file to distinguish the file from others. The embedded watermark is meant to be permanent and follows a process in which there is alterations to the media file. Digital watermarking can be hidden or seen in plain sight by other parties. Deciding on whether to use visible/invisible watermarking depends on the function of the media file, but with either technique, when the media file is copied the digital watermark gets copied as well. Digital watermarks are designed in such a way that they do not restrict the media file or change the media file in such a way it detracts the quality. Its main purpose is to detect misuse and act as a form of signature from the owner. [5]
History
The word steganography was derived from the Greek words steganos, which means "covered", and graphia, which means "writing". The first recorded entry of the use of steganography is in the story of Herodotus and his slaves. Where he shaved the heads of his slaves and tattooed secret messages on their scalps. He would than let their hair grow back to hide the message and send his slaves to deliver the messages to other leaders. Since than, many early proposed steganographic techniques have been created from hiding messages in jewelery, to modifying letter strokes and sizes, and placing a mask over text. Many of these techniques are still used today and were used during World War I and II.
Other techniques that were more sophisticated that were used as well during the wars were microdots, which were microscopic images that were shrunk to resemble tiny specs of dirt. These microdots were placed on a person or in a letter and were used to transmit vital information or locations. From this moment and with the emergence of the Internet, steganographic techniques began increasing. Due to the amount of computer networks and digitalized media, covert steganography became favorable to communicate between parties. There have been many uses of steganography, good and bad, in which they provide an extra layer of security for businesses but could also be used by criminals for illegal means. [11]
The word watermark is thought to have been derived from the German word wassermarke and is termed as the marks were thought to have resembled the effects of water on paper. Watermarking first began in Italy in 1282 where wired patterns were created during paper production which left
designs in the paper once it molded. The purpose is unclear as to why watermarking was done back
than. However in the eighteenth century, paper made in Europe and America using watermarking
technology was to ensure trademarks, track when the paper was created, indicate size of the
sheets, and prevent counterfeiting. [10]
Counterfeiting especially, caused watermarking technology to rapidly increase as there were those attempting to stop counterfeiters and those attempting to remove or copy the watermarks. From the basic imprints on paper, watermarks moved onto color where dyed ink was inserted into the paper during the molding process. The next advancement was to create a raise in the paper causing a slight bump on the surface, which is commonly seen on paper currency today. Finally, the idea of digital watermarking appeared between in 1979, where Szepanski discussed a machine that could be used on documents which would place a pattern for anti-counterfeiting purposes. In 1988, Holt described a way of embedding an identification code in an audio signal and the term digital watermark first appeared. It was only until 1995 that the world became vastly interested in the idea of digital watermarks. From then on, many papers were released discussing ways of implementing digital watermarks and companies ranging from the music industry to business software began using this technique for security and protection. [8]
Applications
Since the emergence of the Internet, digital distribution of media and documents has vastly increased and is constantly increasing every year. On this note, the distribution of copyright material has always been a concern for people trying to protect their work and this is where digital watermarking can become useful. Those who are worried of people eavesdropping on their conversations by email, important documents being read, or video chat being seen by others can use steganographic techniques to protect themselves. In order to know what applications these techniques can be used for, it is best to know the different ways of implementing the techniques. Steganography and digital watermarking can be broken down into four different subcategories in which the existence of the technique is either known or unknown to the public along with the original file.

Covert watermarking is embedding a watermark related to the recipient of each copy of the file, but unaware that the watermark exists. Thus, if the file is leaked to third parties, the recipient who leaked the file can be traced. Covert steganography is embedding data unrelated to the original work. An overt watermark is when the presence of the watermark is known to others besides the creators, whether visually or told of the watermark. Overt steganography is similar to covert steganography in terms of the hidden information is unrelated to the signal in which it is embedded in. However with overt steganography, the information is only hidden to certain parties but visible to others, example timestamps. [7]
Knowing the subcategories allows for the following possible applications for both steganography and digital watermarking. Some applications may use both techniques depending on the function required.
Steganography
Some applications of steganography are [7]:
- Protection of Data Alteration - "Digital Certificates" as an example, act as a way of protecting data by embedding the information.
- Confidential Communication - Where steganographic techniques could provide a way of communicating between two parties without others knowing.
- Media Database Systems - Use of embedded messages in files to quickly identify them.
- Access Control - Using access keys to extract content from a steganographic file.
Digital Watermarking
Some applications that use digital watermarking are [5,6]:
- Broadcast Monitoring - Identifying where and when the media files are being broadcast by looking at the embedded watermarks.
- Owner Identification - The embedded watermark will identify the owner of the media files as a way of copyright protection.
- Transaction Tracking - Track media files that were illegally distributed or to determine the route the file took.
- Content Authentication - The embedded watermarks can add as signatures where the information can be used to authenticate the originality of the file.
- Copy Control - Watermarks can be used in recording equipment to determine what content may be copied.
- Device Control - Watermarks can be used to make devices react a certain way and display certain content.
- Legacy Enhancement - Watermarks can be used to improve functionality of existing systems.
Companies all over the world have been creating software programs to be used for the above applications. Commonly used programs for steganography are Steganos, Stego Suit, and Stealthencrypt. Software used for digital watermarking are Visual Watermark, Ais Watermark, and WatermarkIt. Encryption methods and watermarking schemes offer others the satisfaction of knowing that their data has an extra layer of protection from prying eyes.
Properties
Both methods can be illustrated by properties depending upon the application and the role each method will play. Properties are an important part for both methods as by weighing what properties matter to you based on the method for your application will determine the effectiveness of the system. Since for each method there are many different implementation techniques, the properties that apply to one method are different to that of another since each method list different priorities. Below are the common properties commonly associated with the two methods.
Properties of Steganographic Systems
Some properties of steganography are [7]:
- Security - The ability to resist attacks whether passive, active, or malicious.
- Embedding Capacity - The maximum number of bits that can be hidden in a given media file.
- Blind or Informed Extraction - Whether the other party has a copy of the original file.
- Embedding Efficiency - The number of secret message bits embedded/unit distortion.
- Statistical Undetectability - The probability of detecting a steganographic technique based off assumptions.
- False Alarm Rate - The probability that an algorithm will detect and report the presence of a secret message when there is none.
- Stego Key - Possibility of using a publicly known algorithm to embed a secret message into the media file.
Properties of Watermarked Systems
Some properties of digital watermarking are [5,7]:
- Robustness - The ability of the watermark to survive processing of content.
- Security - The ability of the watermark to prevent attacks or removal.
- Embedding Effectiveness - The probability that the embedder will successfully embed the watermark in a random media file.
- Fidelity - The perceptive quality of a watermarked content.
- Data Payload - The amount of information that can be carried in the watermark.
- Transparency - The level of the opacity required to make the watermark visible or invisible.
- False Positive Rate - The rate in which the watermark will be falsely detected in non-watermarked files.
- Modification and Multiple Watermarks - The possibility of changing the watermark or embedding multiple watermarks.
- Cost - The cost required to embed the watermark into the digital file.
Model and Techniques
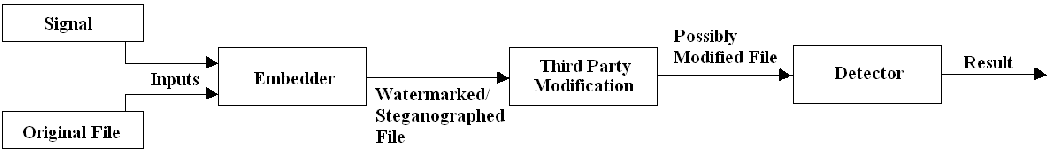
Steganography and digital watermarking are two different techniques, however they both share similar qualities. Both techniques follows the same basic model in which two inputs (a signal and the original file) go into an embedder. The signal corresponds to the digital watermark or the secret message and the embedder function contains an algorithm that will produce a watermarked file. The output from the embedder is than transmitted or recorded. The recorded file is than sent to a third party in which the possibility of a modification, whether malicious or not, could arise. The recorded file, modified or not, is than sent as input to a detector in which the algorithm tries to determine if the signal is present. If it is, the watermark or secret message can usually be extracted depending on the properties. [10]
For all the applications steganography and digital watermarking can be applied to, there have been many different techniques and variations. Below are a list of the most popular techniques currently being used today in digital media.
Steganography Techniques
Some techniques of steganography are [3]:
Least Significant Bit Insertion
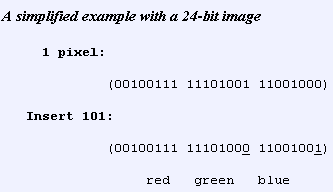
Least Significant Bit (LSB) insertion is having the rightmost bit of a binary number inserted with a different value. Which means that for every 8-bit binary number of an image, the LSB is replaced with 1-bit from the hidden message. The downside of this technique is that if the media file, say an image, is ever converted from one format to another (GIF to JPEG) the information in the message could be distorted.
Masking and Filtering
The masking and filtering technique hides the secret message by integrating the message into the noise level of the original file. The noise level is the redundant portion of the image and allows for the message to hide in this area. Thus, this technique will be able to protect the message from image processing and conversion. However, this technique is usually only suitable for 24-bit and gray-scaled images.
Algorithms and Transformations
Algorithms and transformations technique uses mathematical functions in compression algorithms to hide the secret messages. This technique hides the data bits in the least significant coefficients. This technique is used on JPEG images or files using lossy compression as these files use the discrete cosine transform (DCT) to achieve its image compression. By altering the coefficients of DCT, the secret message changes the relation of the coefficients to one another instead of the actual bits themselves.
Digital Watermarking Techniques
Some techniques of digital watermarking are [4]:
Least Significant Bit Modification
Least Significant Bit (LSB) modification is the same process as that of Steganography and the watermark can be embedded multiple times if the watermark is small enough. Adding to the LSB algorithm, is to have a pseudo-random generator in which where the watermark is placed is random. Thus if the watermark undergoes an attack and one of the watermarks survive, than the process would be a success. The downside of LSB is that its not robust enough where any form of conversion would destroy the watermark. As well, if an outside party does discover the algorithm of the watermark, they would only need to change the last bit of each pixel to 1 and this would not deteriorate the overall quality of the media file.
Correlation-Based Techniques
Correlation-Based Techniques use the correlation properties of additive pseudo-random noise patterns and adding it to the media file. Thus, by multiplying a gain to the watermark and adding it to the image would result in a robust watermarked image depending on how large the gain was set to. The strength on this technique is that the image can be divided into multiple parts and the watermark can be added to each part. Additional filters can be added onto this technique to increase the chance of the watermark surviving an attack, such as pre-filtering the image to reduce the correlation of the gain to the original work or to use a CDMA Spread-Spectrumto scatter the bits.
Frequency Domain Techniques
Frequency Domain Techniques embeds the watermark in the Discrete Cosine Transform (DCT) where the image is broken down into different frequency bands. This makes it easy to place the watermark as the bands chosen are the middle bands with low frequencies in order to make the watermark less obvious on the image. This causes the watermark to be robust and resistant against lossy compression or image degradation. Other techniques can be merged with this one, such as the pseudo noise patterns in order to protect the watermark even further.
Wavelet Watermarking Techniques
Wavelet Watermarking techniques uses the Discrete Wavelet Transform (DWT) to separate the image into different resolutions. Once the image has been separated, the watermarked image can be embedded into these regions. The reason to use such a technique is that higher quality watermarks can be added, which in turns increases the robustness of the watermark without impacting the image quality. The CDMA spread-spectrum can again be added to this technique in order to increase the security of the watermark. It has also been said this technique would be able to survive attacks such as conversion and image altering.
Countermeasures
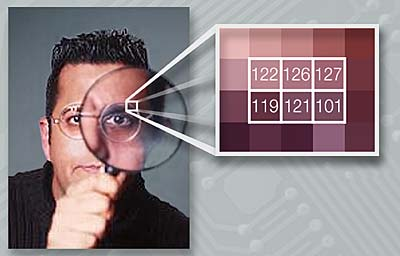
Countermeasures or detection techniques against covert steganography or watermarking requires the use of the light spectrum, magnification lenses, chemical mixtures, search algorithms, and others are used to determine if a file has been embedded with either these techniques. The use of the light spectrum, and chemical mixtures can only be used for hard copy works of the media files in question. Magnification lenses can be used on both hard copies and digital copies to magnify the image to a size where the watermarked or hidden message can be found. Search algorithms can be done by hand, however it can be quite difficult and is usually done by computers and is the most likely used form of detection. As there are companies creating software to protect secret messages and embed watermarks into files, there are also companies creating software to remove and detect encoded files. [2]
In steganography, the detection of steganographic messages is called steganalysis where the algorithm takes the original file and compares it to the file that is thought to have the secret message. However this only works if a known clean copy of the original is available. In digital watermarking, the technique of watermark detection, informed detection, is used to find invisible watermarks. Watermark detection can follow the same principle algorithm that steganalysis goes through by obtaining the original work and comparing it with one that is believed to have the invisible watermark. Another way of detecting invisible watermarks is by blind detection, where the detecting algorithm is provided with limited information of the original work to find the watermark. [9] Thus as you can see, although steganography and watermarking are very effective, there are ways for them to be removed or detected. For every technique, there must be a way of detection as the rightful owners need a way of checking/tracking their work and thus if those with illegal intentions discover the way of detection, they too can find and remove the methods.
References
- Digital Watermarking - Common watermarking techniques, Important parameters, Applied mechanisms, Applications, Invertible watermarking, Content-fragile watermarking. 2009. Retrieved April 7, 2009.
- Document Fraud and Technology, a Double-Edged Sword . 2008. Retrieved April 8, 2009.
- Steganography Techniques. 2009. Retrieved April 2, 2009.
- Hidden Bits: A Survey of Techniques for Digital Watermarking. 2002. Retrieved April 6, 2009.
- Watermarking FAQ. 2005. Retrieved April 7, 2009.
- Arnold, Michael Konrad and Schmucker, Martin. Techniques and Applications of Digital Watermarking and Content Protection. Published by Artech House, 2003.
- Cox, Ingemar J. , Miller, Matthew., Bloom, Jeffrey ., Fridrich, Jessica ., and Kalker, Ton. Digital Watermarking and Steganography. Published by Morgan Kaufmann, 2007.
- Cox, Ingemar J., Miller, Matthew L. and Bloom, Jeffrey A. Digital watermarking. Published by Morgan Kaufmann, 2002.
- Johnson, Neil F., Duric, Zoran., and Jajodia, Sushil. Information Hiding. Published by Springer, 2001.
- Pan, Jeng-Shyang and Huang, Hsiang-Cheh. Intelligent watermarking techniques. Published by World Scientific, 2004.
- Wayner, Peter. Disappearing cryptography. Published by Morgan Kaufmann, 2002.
See Also
- Cryptography in Information Security
- Public Key Authentication
- Corporate Security and IT Policies
- CAPTCHA
- Personal Data Protection and Privacy
- Data Encryption for Storage Devices
- Conventional Encryption Algorithms
- Information security awareness
- Digital Signatures
External Links
- Steganography Revealed
- Hide and Seek: An Introduction to Steganography
- Steganography Tools
- Steganography and Steganalysis
- Robustness and Security of Digital Watermarks
- On the Limitations of Digital Watermarks: A Cautionary Note
- Digital Watermarking Alliance
- Digital Watermarking World
--Ganv 10:33, 12 April 2009 (EDT)