Man in the Middle Attack
From Computing and Software Wiki
(→Specific MITM Attacks) |
|||
| Line 11: | Line 11: | ||
Another common man in the middle attack is [[IP Spoofing]], where victims have all their web traffic re-routed through the attacker.<sup>[3]</sup> <br> | Another common man in the middle attack is [[IP Spoofing]], where victims have all their web traffic re-routed through the attacker.<sup>[3]</sup> <br> | ||
[[Image:IP_Spoofing.jpg|frame|IP Spoofing Diagram <sup>[4]</sup>]] | [[Image:IP_Spoofing.jpg|frame|IP Spoofing Diagram <sup>[4]</sup>]] | ||
| - | Recently, there has been alot of press about MITM attacks defeating even SSL security. This is an especially distressing issue as this is the major form of security used on the web today. | + | Recently, there has been alot of press about MITM attacks defeating even SSL security. This is an especially distressing issue as this is the major form of security used on the web today. One researcher intercepted 200 requests for SSL encrypted pages over 20 hours, including 114 Yahoo! credentials, 50 Gmail credentials and 16 credit-card numbers.<sup>[5,6]</sup> |
==MITM Attack Examples== | ==MITM Attack Examples== | ||
| Line 33: | Line 33: | ||
*Access Point Reassociation | *Access Point Reassociation | ||
| - | ==Active MITM Attacks <sup> [ | + | ==Active MITM Attacks <sup> [7] </sup> == |
Recently a new class of MITM attacks have been occurring with two important differences; | Recently a new class of MITM attacks have been occurring with two important differences; | ||
*It is initiated by the attacker | *It is initiated by the attacker | ||
| Line 48: | Line 48: | ||
There are many different scenarios and types of active attacks that make browsing even sites traditionally thought safe dangerous. | There are many different scenarios and types of active attacks that make browsing even sites traditionally thought safe dangerous. | ||
| - | ==Attacking Tools <sup>[ | + | ==Attacking Tools <sup>[8,9] </sup> == |
| - | *[http://naughty.monkey.org/~dugsong/dsniff/ Dsniff] A collection of tools for network auditing and penetration testing | + | *[http://naughty.monkey.org/~dugsong/dsniff/ Dsniff]: A collection of tools for network auditing and penetration testing |
| - | *[http://ettercap.sourceforge.net/ Ettercap] A suite of tools for MITM attacks over LAN. | + | *[http://ettercap.sourceforge.net/ Ettercap]: A suite of tools for MITM attacks over LAN. |
| - | *[http://www.softpedia.com/get/Network-Tools/Network-Testing/PacketCreator.shtml PacketCreator] A tool that uses ARP cache poisoning for network testing. | + | *[http://www.softpedia.com/get/Network-Tools/Network-Testing/PacketCreator.shtml PacketCreator]: A tool that uses ARP cache poisoning for network testing. |
| - | *[http://www.oxid.it/cain.html Cain and Abel] A password recovery tool for Microsoft operating systems. | + | *[http://www.oxid.it/cain.html Cain and Abel]: A password recovery tool for Microsoft operating systems. |
| + | *Juggernaut: A network sniffer that can be used to hijack TCP sessions. | ||
==Defences== | ==Defences== | ||
| Line 71: | Line 72: | ||
* [http://cwe.mitre.org/data/definitions/300.html CWE-300: Channel Accessible by Non-Endpoint (aka 'Man-in-the-Middle')] | * [http://cwe.mitre.org/data/definitions/300.html CWE-300: Channel Accessible by Non-Endpoint (aka 'Man-in-the-Middle')] | ||
* [http://www.answers.com/topic/man-in-the-middle-attack-1 Answers.Com Man in the Middle Attack] | * [http://www.answers.com/topic/man-in-the-middle-attack-1 Answers.Com Man in the Middle Attack] | ||
| + | * [http://www.giac.org/certified_professionals/practicals/gsec/0455.php Man in the Middle Attack - A Brief] | ||
==References== | ==References== | ||
| - | # | + | #http://en.wikipedia.org/wiki/Man-in-the-middle_attack |
#A Weakness in the 4.2BSD Unix TCP/IP Software, Robert T. Morris, AT&T Bell Laboratories, February 1985 <BR> | #A Weakness in the 4.2BSD Unix TCP/IP Software, Robert T. Morris, AT&T Bell Laboratories, February 1985 <BR> | ||
| - | # | + | #http://www.csl.sri.com/users/ddean/papers/spoofing.pdf |
| - | # | + | #http://www.contentverification.com/man-in-the-middle |
| - | # | + | #http://www.sans.org/reading_room/whitepapers/threats/ssl_maninthemiddle_attacks_480?show=480.php&cat=threats |
| + | #http://www.securityfocus.com/brief/910 | ||
| + | #http://blog.watchfire.com/wfblog/2009/02/active-man-in-the-middle-attacks.html | ||
#http://www.thenetworkadministrator.com/2005tophackingtools.htm | #http://www.thenetworkadministrator.com/2005tophackingtools.htm | ||
#http://www.owasp.org/index.php/Man-in-the-middle_attack | #http://www.owasp.org/index.php/Man-in-the-middle_attack | ||
Revision as of 03:08, 13 April 2009
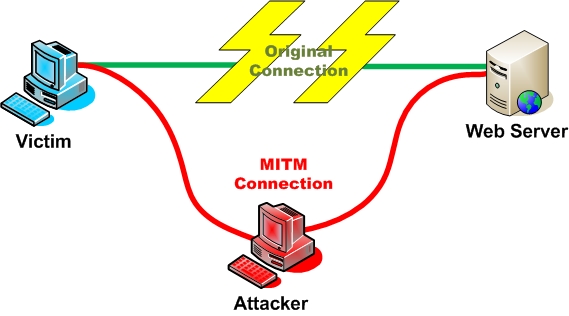
Man in the Middle Attacks (sometimes MITM) are attacks where the attacker intercepts communication between two parties, forwarding the communication as if the attacker were not present. The name is derived from the popular game Man in the Middle. It is also referred to as a fire-brigade or bucket brigade attack based on the method for putting out a fire. Lastly it is referred to as a Janus attack in reference to the roman two-headed god of gates.[1]
Contents |
Generic Example
Alice sends a communication to Bob, which is intercepted by an attacker, and then forwarded on to Bob. Bob then replies to Alice which is also intercepted by the attacker, and then forwarded to Alice.
Specific MITM Attacks
Historically, several different man in the middle attacks have been described. Perhaps the earliest reference was a paper showing the possibility of IP spoofing in BSD Linux.[2] A more recent and famous example is The Mitnick attack, a man in the middle attack taking advantage of the structure of IP to establish the trusted connections.
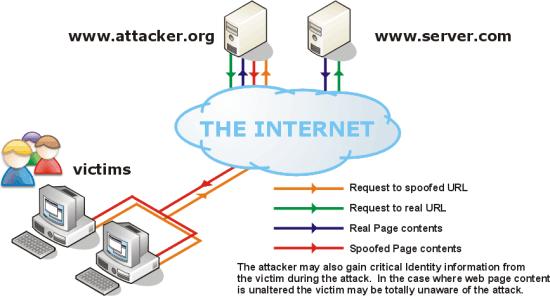
Another common man in the middle attack is IP Spoofing, where victims have all their web traffic re-routed through the attacker.[3]
Recently, there has been alot of press about MITM attacks defeating even SSL security. This is an especially distressing issue as this is the major form of security used on the web today. One researcher intercepted 200 requests for SSL encrypted pages over 20 hours, including 114 Yahoo! credentials, 50 Gmail credentials and 16 credit-card numbers.[5,6]
MITM Attack Examples
LAN
- ARP Poisoining
- DNS Spoofing
- STP Mangling
- Port Stealing
Local to Remote
- ARP Poisoining
- DNS Spoofing
- DHCP Spoofing
- ICMP Redirection
- IRDP Spoofing
- Route Mangling
Remote
- DNS Poisoning
- Traffic
- Route Mangling
Wireless
- Access Point Reassociation
Active MITM Attacks [7]
Recently a new class of MITM attacks have been occurring with two important differences;
- It is initiated by the attacker
- The target is controlled by the attacker rather than limited to the victim's communications
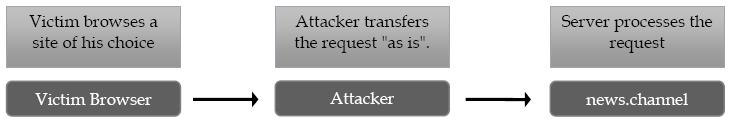
While active attacks can happen in several ways one of the simplest to imagine is through IFrame injection. The attacker would modify the requested page to include an IFrame with a source of the attacker's choice.
Attack Flow
- 1. The victim browses to a page of their choice
- 2. The attacker intercepts the response and injects the IFrame into it
- 3. The user's browser automatically renders the IFrame sending the victim's credentials to the attacker. The attacker now has the victim's credentials and can continue with traditional hacking methods.
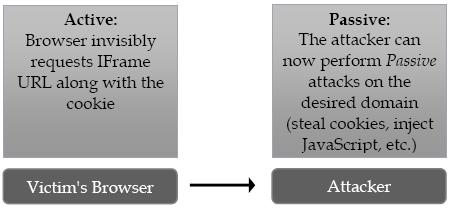
There are many different scenarios and types of active attacks that make browsing even sites traditionally thought safe dangerous.
Attacking Tools [8,9]
- Dsniff: A collection of tools for network auditing and penetration testing
- Ettercap: A suite of tools for MITM attacks over LAN.
- PacketCreator: A tool that uses ARP cache poisoning for network testing.
- Cain and Abel: A password recovery tool for Microsoft operating systems.
- Juggernaut: A network sniffer that can be used to hijack TCP sessions.
Defences
The two major issues with MITM attacks are endpoint verification, confirming you are speaking with the desired target and channel security, confirming that the medium of communication has not been infiltrated.
Beyond Computing
See Also
- Bots & Botnets
- Information security awareness
- Network firewall
- Network stack (dode) - attack patterns on each layer & how to defend it
- Operating Systems Security
- Personal Data Protection and Privacy
- Phishing
External Links
- CWE-300: Channel Accessible by Non-Endpoint (aka 'Man-in-the-Middle')
- Answers.Com Man in the Middle Attack
- Man in the Middle Attack - A Brief
References
- http://en.wikipedia.org/wiki/Man-in-the-middle_attack
- A Weakness in the 4.2BSD Unix TCP/IP Software, Robert T. Morris, AT&T Bell Laboratories, February 1985
- http://www.csl.sri.com/users/ddean/papers/spoofing.pdf
- http://www.contentverification.com/man-in-the-middle
- http://www.sans.org/reading_room/whitepapers/threats/ssl_maninthemiddle_attacks_480?show=480.php&cat=threats
- http://www.securityfocus.com/brief/910
- http://blog.watchfire.com/wfblog/2009/02/active-man-in-the-middle-attacks.html
- http://www.thenetworkadministrator.com/2005tophackingtools.htm
- http://www.owasp.org/index.php/Man-in-the-middle_attack
--Heifetj 10:24, 12 April 2009 (EDT)