Man in the Middle Attack
From Computing and Software Wiki
(→Example Attacks) |
|||
| (34 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
[[Image:Man_in_the_Middle.jpg|frame|Man in the Middle Example]] | [[Image:Man_in_the_Middle.jpg|frame|Man in the Middle Example]] | ||
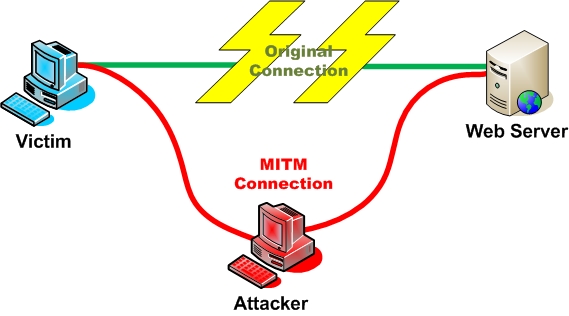
| - | Man in the Middle | + | Man in the Middle (MITM) Attacks are attacks where the attacker intercepts communication between two parties, forwarding the communication as if the attacker were not present. The name is derived from the popular game Man in the Middle. It is also referred to as a fire-brigade or bucket brigade attack based on the method for putting out a fire. Additionally it is referred to as a Janus attack in reference to the roman two-headed god of gates.<sup>[1]</sup> |
| - | It is also referred to as a fire-brigade or bucket brigade attack based on the method for putting out a fire. | + | |
| - | + | ||
| - | ==Example Attacks== | + | ==Generic Example== |
| - | Historically, several different man in the middle attacks have been described. Perhaps the earliest reference was a paper showing the possibility of IP spoofing in BSD Linux.<sup>[ | + | Alice sends a communication to Bob, which is intercepted by an attacker, and then forwarded on to Bob. Bob then replies to Alice which is also intercepted by the attacker, and then forwarded to Alice. The attacker may or may not modify the communications. |
| - | [[Image: | + | <BR> |
| + | *If tokens are used, the MITM attacker can intercept and replay the one-time password before the token times out. | ||
| + | *If challenge questions are used, the MITM attacker can simply observe the challenge question and present it to the user, replaying the response to the legitimate site. <sup>[2]</sup> | ||
| + | |||
| + | ==Specific MITM Attacks== | ||
| + | Historically, several different man in the middle attacks have been described. Perhaps the earliest reference was a paper showing the possibility of IP spoofing in BSD Linux.<sup>[3]</sup> A more recent and famous example is [[The Mitnick attack]], a man in the middle attack taking advantage of the structure of IP to establish the trusted connections. | ||
| + | <br><br> | ||
| + | Recently, there has been alot of press about MITM attacks defeating even SSL security. This is an especially distressing issue as this is the major form of security used on the web today. One researcher intercepted 200 requests for SSL encrypted pages over 20 hours, including 114 Yahoo! credentials, 50 Gmail credentials and 16 credit-card numbers.<sup>[6,7]</sup> | ||
| + | <br><br> | ||
| + | In a recent example of a successful attack combining social engineering with phishing and malware, more than 20,000 senior corporate executives were fooled into clicking a link in an e-mail that purported to be a subpoena. The resulting malware installation enabled a man-in-the-middle attack to be successfully completed without the end-users’ knowledge. <sup>[4]</sup> | ||
| + | |||
| + | ==MITM Attack Examples <sup>[4]</sup>== | ||
| + | ===LAN=== | ||
| + | *ARP Poisoining | ||
| + | *DNS Spoofing | ||
| + | *STP Mangling | ||
| + | *Port Stealing | ||
| + | ===Local to Remote=== | ||
| + | *ARP Poisoining | ||
| + | *DNS Spoofing | ||
| + | *DHCP Spoofing | ||
| + | *ICMP Redirection | ||
| + | *IRDP Spoofing | ||
| + | *Route Mangling | ||
| + | ===Remote=== | ||
| + | *DNS Poisoning | ||
| + | *Traffic | ||
| + | *Route Mangling | ||
| + | ===Wireless=== | ||
| + | *Access Point Reassociation | ||
| + | |||
| + | ==Active MITM Attacks <sup> [8] </sup> == | ||
| + | Recently a new class of MITM attacks have been occurring with two important differences; | ||
| + | *It is initiated by the attacker | ||
| + | *The target is controlled by the attacker rather than limited to the victim's communications | ||
| + | While active attacks can happen in several ways one of the simplest to imagine is through IFrame injection. The attacker would modify the requested page to include an IFrame with a source of the attacker's choice. | ||
| + | ===Attack Flow=== | ||
| + | :1. The victim browses to a page of their choice | ||
| + | [[Image:Active_MITM_Flow_1.jpg]] | ||
| + | :2. The attacker intercepts the response and injects the IFrame into it | ||
| + | [[Image:Active_MITM_Flow_2.jpg]] | ||
| + | :3. The user's browser automatically renders the IFrame sending the victim's credentials to the attacker. The attacker now has the victim's credentials and can continue with traditional hacking methods. | ||
| + | [[Image:Active_MITM_Flow_3.jpg]] | ||
| + | <br> | ||
| + | There are many different scenarios and types of active attacks that make browsing even sites traditionally thought safe dangerous. | ||
| + | |||
| + | ==Attacking Tools <sup>[9,10,11] </sup> == | ||
| + | *[http://naughty.monkey.org/~dugsong/dsniff/ Dsniff] - A collection of tools for network auditing and penetration testing | ||
| + | *[http://ettercap.sourceforge.net/ Ettercap] - A suite of tools for MITM attacks over LAN. | ||
| + | *[http://www.softpedia.com/get/Network-Tools/Network-Testing/PacketCreator.shtml PacketCreator] - A tool that uses ARP cache poisoning for network testing. | ||
| + | *[http://www.oxid.it/cain.html Cain and Abel] - A password recovery tool for Microsoft operating systems. | ||
| + | *[http://www.google.com/gwt/n?u=http://www.theta44.org/karma/ Karma] - A tool that uses 802.11 Evil Twin attacks to perform MITM attacks | ||
| + | |||
| + | ==Defences== | ||
| + | The major defense used today is to always use SSL connections for important data and never use insecure connections. This strategy is not enough for many users, as several of the attacks described are smart enough to defeat SSL when not used properly. Most browsers today do not make it simple enough for users to recognize when a MITM attack has been initiated and a secure connection is no longer being used. Additionally most web users do not check the validity of certificates they accept on a daily basis. | ||
| + | ===Multifactor Authentication <sup>[2]</sup>=== | ||
| + | *Public Key Infrastructure - external certifications for digital certificates | ||
| + | *IP Geolocation - identifies where a user’s currently assigned IP is geographically and whether it is normal or appropriate for the user | ||
| + | *Machine Fingerprinting and Tagging – stores and validates a profile of the customers system | ||
==See Also== | ==See Also== | ||
| - | + | *[[IP Spoofing]] | |
| - | + | *[[Bots & Botnets]]<BR> | |
| - | + | *[[Information security awareness]]<BR> | |
| - | + | *[[Network firewall]]<BR> | |
| - | + | *[[Network stack (dode) - attack patterns on each layer %26 how to defend it]] <BR> | |
| - | + | *[[Operating Systems Security]]<BR> | |
| - | + | *[[Personal Data Protection and Privacy]]<BR> | |
| - | + | *[[Phishing]]<BR> | |
==External Links== | ==External Links== | ||
* [http://cwe.mitre.org/data/definitions/300.html CWE-300: Channel Accessible by Non-Endpoint (aka 'Man-in-the-Middle')] | * [http://cwe.mitre.org/data/definitions/300.html CWE-300: Channel Accessible by Non-Endpoint (aka 'Man-in-the-Middle')] | ||
| - | + | * [http://www.answers.com/topic/man-in-the-middle-attack-1 Answers.Com Man in the Middle Attack] | |
| + | * [http://www.giac.org/certified_professionals/practicals/gsec/0455.php Man in the Middle Attack - A Brief] | ||
| + | * [http://www.schneier.com/blog/archives/2008/07/maninthemiddle_1.html Schneier on Security - Man in the Middle Attacks] | ||
| + | * [http://www.blackhat.com/presentations/bh-usa-03/bh-us-03-ornaghi-valleri.pdf Man in the Middle Attacks - Demos] | ||
| + | * [http://enc.slider.com/Enc/Man_in_the_middle Slider - Man in the Middle Attacks] | ||
==References== | ==References== | ||
| - | + | #http://en.wikipedia.org/wiki/Man-in-the-middle_attack | |
| - | + | #http://download.entrust.com/resources/download.cfm/22836/WP_MITM_Sept08.pdf/?start | |
| - | + | #A Weakness in the 4.2BSD Unix TCP/IP Software, Robert T. Morris, AT&T Bell Laboratories, February 1985 <BR> | |
| + | #http://www.csl.sri.com/users/ddean/papers/spoofing.pdf | ||
| + | #http://www.contentverification.com/man-in-the-middle | ||
| + | #http://www.sans.org/reading_room/whitepapers/threats/ssl_maninthemiddle_attacks_480?show=480.php&cat=threats | ||
| + | #http://www.securityfocus.com/brief/910 | ||
| + | #http://blog.watchfire.com/wfblog/2009/02/active-man-in-the-middle-attacks.html | ||
| + | #http://www.thenetworkadministrator.com/2005tophackingtools.htm | ||
| + | #http://www.owasp.org/index.php/Man-in-the-middle_attack | ||
| + | #http://wapedia.mobi/en/Man-in-the-middle_attack?t=3. | ||
---- | ---- | ||
| - | --[[User:Heifetj|Heifetj]] | + | --[[User:Heifetj|Heifetj]] 23:46, 12 April 2009 (EDT) |
Current revision as of 03:46, 13 April 2009
Man in the Middle (MITM) Attacks are attacks where the attacker intercepts communication between two parties, forwarding the communication as if the attacker were not present. The name is derived from the popular game Man in the Middle. It is also referred to as a fire-brigade or bucket brigade attack based on the method for putting out a fire. Additionally it is referred to as a Janus attack in reference to the roman two-headed god of gates.[1]
Contents |
Generic Example
Alice sends a communication to Bob, which is intercepted by an attacker, and then forwarded on to Bob. Bob then replies to Alice which is also intercepted by the attacker, and then forwarded to Alice. The attacker may or may not modify the communications.
- If tokens are used, the MITM attacker can intercept and replay the one-time password before the token times out.
- If challenge questions are used, the MITM attacker can simply observe the challenge question and present it to the user, replaying the response to the legitimate site. [2]
Specific MITM Attacks
Historically, several different man in the middle attacks have been described. Perhaps the earliest reference was a paper showing the possibility of IP spoofing in BSD Linux.[3] A more recent and famous example is The Mitnick attack, a man in the middle attack taking advantage of the structure of IP to establish the trusted connections.
Recently, there has been alot of press about MITM attacks defeating even SSL security. This is an especially distressing issue as this is the major form of security used on the web today. One researcher intercepted 200 requests for SSL encrypted pages over 20 hours, including 114 Yahoo! credentials, 50 Gmail credentials and 16 credit-card numbers.[6,7]
In a recent example of a successful attack combining social engineering with phishing and malware, more than 20,000 senior corporate executives were fooled into clicking a link in an e-mail that purported to be a subpoena. The resulting malware installation enabled a man-in-the-middle attack to be successfully completed without the end-users’ knowledge. [4]
MITM Attack Examples [4]
LAN
- ARP Poisoining
- DNS Spoofing
- STP Mangling
- Port Stealing
Local to Remote
- ARP Poisoining
- DNS Spoofing
- DHCP Spoofing
- ICMP Redirection
- IRDP Spoofing
- Route Mangling
Remote
- DNS Poisoning
- Traffic
- Route Mangling
Wireless
- Access Point Reassociation
Active MITM Attacks [8]
Recently a new class of MITM attacks have been occurring with two important differences;
- It is initiated by the attacker
- The target is controlled by the attacker rather than limited to the victim's communications
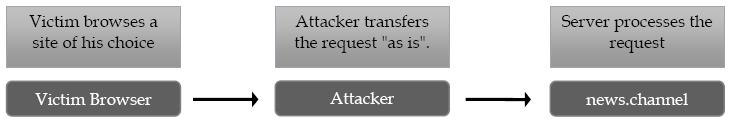
While active attacks can happen in several ways one of the simplest to imagine is through IFrame injection. The attacker would modify the requested page to include an IFrame with a source of the attacker's choice.
Attack Flow
- 1. The victim browses to a page of their choice
- 2. The attacker intercepts the response and injects the IFrame into it
- 3. The user's browser automatically renders the IFrame sending the victim's credentials to the attacker. The attacker now has the victim's credentials and can continue with traditional hacking methods.
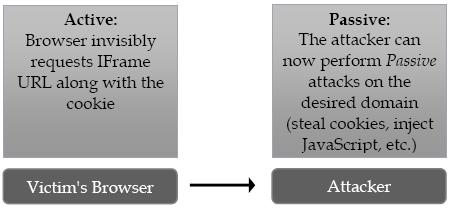
There are many different scenarios and types of active attacks that make browsing even sites traditionally thought safe dangerous.
Attacking Tools [9,10,11]
- Dsniff - A collection of tools for network auditing and penetration testing
- Ettercap - A suite of tools for MITM attacks over LAN.
- PacketCreator - A tool that uses ARP cache poisoning for network testing.
- Cain and Abel - A password recovery tool for Microsoft operating systems.
- Karma - A tool that uses 802.11 Evil Twin attacks to perform MITM attacks
Defences
The major defense used today is to always use SSL connections for important data and never use insecure connections. This strategy is not enough for many users, as several of the attacks described are smart enough to defeat SSL when not used properly. Most browsers today do not make it simple enough for users to recognize when a MITM attack has been initiated and a secure connection is no longer being used. Additionally most web users do not check the validity of certificates they accept on a daily basis.
Multifactor Authentication [2]
- Public Key Infrastructure - external certifications for digital certificates
- IP Geolocation - identifies where a user’s currently assigned IP is geographically and whether it is normal or appropriate for the user
- Machine Fingerprinting and Tagging – stores and validates a profile of the customers system
See Also
- IP Spoofing
- Bots & Botnets
- Information security awareness
- Network firewall
- Network stack (dode) - attack patterns on each layer & how to defend it
- Operating Systems Security
- Personal Data Protection and Privacy
- Phishing
External Links
- CWE-300: Channel Accessible by Non-Endpoint (aka 'Man-in-the-Middle')
- Answers.Com Man in the Middle Attack
- Man in the Middle Attack - A Brief
- Schneier on Security - Man in the Middle Attacks
- Man in the Middle Attacks - Demos
- Slider - Man in the Middle Attacks
References
- http://en.wikipedia.org/wiki/Man-in-the-middle_attack
- http://download.entrust.com/resources/download.cfm/22836/WP_MITM_Sept08.pdf/?start
- A Weakness in the 4.2BSD Unix TCP/IP Software, Robert T. Morris, AT&T Bell Laboratories, February 1985
- http://www.csl.sri.com/users/ddean/papers/spoofing.pdf
- http://www.contentverification.com/man-in-the-middle
- http://www.sans.org/reading_room/whitepapers/threats/ssl_maninthemiddle_attacks_480?show=480.php&cat=threats
- http://www.securityfocus.com/brief/910
- http://blog.watchfire.com/wfblog/2009/02/active-man-in-the-middle-attacks.html
- http://www.thenetworkadministrator.com/2005tophackingtools.htm
- http://www.owasp.org/index.php/Man-in-the-middle_attack
- http://wapedia.mobi/en/Man-in-the-middle_attack?t=3.
--Heifetj 23:46, 12 April 2009 (EDT)