Steganography and Digital Watermarking
From Computing and Software Wiki
| Line 68: | Line 68: | ||
* False Alarm Rate | * False Alarm Rate | ||
* Stego Key | * Stego Key | ||
| + | |||
=== Properties of Watermarked Systems === | === Properties of Watermarked Systems === | ||
Revision as of 04:09, 8 April 2009
Steganography and Digital Watermarking are both forms of information hiding where the context can be viewed as keeping the information a secret or making the information subtle respectively. Both these methods have been around for a long time, at least several centuries, however they have only gained worldwide popularity in the digital world since roughly the mid 1990s. With new technologies constantly emerging, these two methods have been used to prevent theft, prevent plagiarism, track, and hide secrets among other things. There is not one standard way of implementing these techniques and each version differs from one another. Thus, with the vast amount of applications these techniques can be applied to, many companies have made software to create and detect both techniques.
Contents |
History
The word steganography was derived from the Greek words steganos, which means "covered", and graphia, which means "writing".
The word watermark is thought to have been derived from the German word wassermarke and is termed as the marks were thought to have resembled the effects of water on paper.
Applications
Steganography and digital watermarking can be broken down into four different subcategories in which the existence of the technique is either known or unknown to the public along with the original file.

Covert watermarking is embedding a watermark related to the recipient of each copy of the file, but unaware that the watermark exists. Thus, if the file is leaked to third parties, the recipient who leaked the file can be traced. Covert steganography is embedding data unrelated to the original work. An overt watermark is when the presence of the watermark is known to others besides the creators, whether visually or told of the watermark. Overt steganography is similar to covert steganography in terms of the hidden information is unrelated to the signal in which it is embedded in. However with overt steganography, the information is only hidden to certain parties but visible to others, example timestamps.
Knowing the subcategories allows for the following possible applications for both steganography and digital watermarking. Some applications may use both techniques depending on the function required.
Steganography
Some applications of steganography are:
- Protection of Data Alteration
- Confidential Communication
- Media Database Systems
- Access Control
Digital Watermarking
Some applications that use digital watermarking are:
- Broadcast Monitoring
- Owner Identification
- Proof of Ownership
- Transaction Tracking
- Content Authentication
- Copy Control
- Device Control
- Legacy Enhancement
Properties
Properties of Steganographic Systems
Some properties of steganography are:
- Robustness
- Security
- Embedding Effectiveness
- Fidelity
- Steganographic Capacity
- Blind or Informed Extraction
- Embedding Capacity
- Embedding Efficiency
- Data Payload
- Blind or Targeted Steganalysis
- Statistical Undetectability
- False Alarm Rate
- Stego Key
Properties of Watermarked Systems
Some properties of digital watermarking are:
- Robustness
- Security
- Embedding Effectiveness
- Fidelity
- Data Payload
- Cipher andWatermark Keys
- Blind or Informed Detection
- False Positive Rate
- Modification and MultipleWatermarks
- Cost
Models and Techniques
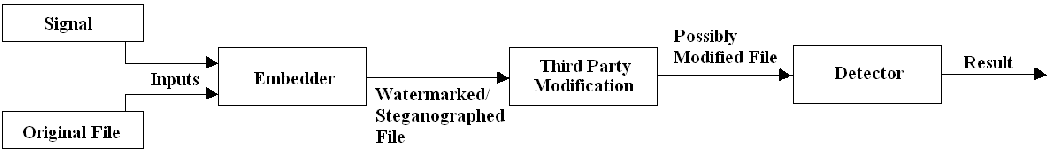
Steganography and digital watermarking are two different techniques, however they both share similar qualities. Both techniques follows the same basic model in which two inputs (a signal and the original file) go into an embedder. The signal corresponds to the digital watermark or the secret message and the embedder function contains an algorithm that will produce a watermaked file. The output from the embedder is than transmitted or recorded. The recorded file is than sent to a third party in which the possibility of a modification, whether malicous or not, could arise. The recorded file, modified or not, is than sent as input to a detector in which the algorithm tries to determine if the signal is present. If it is, the watermark or secret message can usually be extracted depending on the properties.
How Steganography Works
How Digital Watermarking Works
Countermeasures
Countermeasures or detection techniques against covert steganography or watermarking requires the use of the light spectrum, magnification lenses, chemical mixtures, cipher algorithms, and others are used to determine if a file has been embedded with either these techniques.
See Also
- Cryptography in Information Security
- Public Key Authentication
- Corporate Security and IT Policies
- CAPTCHA
- Personal Data Protection and Privacy
- MD5 Rainbow Tables
- Data Encryption for Storage Devices
- Conventional Encryption Algorithms
- Information security awareness
- Digital Signatures
- Statistics of Internet Threats
- Multicasting
External Links
References
--Ganv 20:14, 7 April 2009 (EDT)