Network firewall
From Computing and Software Wiki
| (58 intermediate revisions not shown) | |||
| Line 4: | Line 4: | ||
:* It restricts people to leaving at a carefully controlled point.[1:21] | :* It restricts people to leaving at a carefully controlled point.[1:21] | ||
| - | In practice,a firewall is a collection of hosts, routers, and other hardware that designed to prevent unauthorized electronic access between two parts of a network. It is also a device or set of devices configured to permit, deny, encrypt, decrypt, or proxy all computer traffic between different security domains based upon a set of rules and other criteria.[3] | + | In practice,a firewall is a collection of hosts, routers, and other hardware that designed to prevent unauthorized electronic access between two parts of a network. It is also a device or set of devices configured to permit, deny, encrypt, decrypt, or [[Proxy Server|proxy]] all computer traffic between different security domains based upon a set of rules and other criteria.[3] |
Firewalls can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria.[3] | Firewalls can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria.[3] | ||
| Line 17: | Line 17: | ||
if you answer YES to any of above, then Network Firewall is the solution you needed. | if you answer YES to any of above, then Network Firewall is the solution you needed. | ||
===What is Firewall=== | ===What is Firewall=== | ||
| - | As | + | As Figure 1 shows, a Firewall is a box/device between two connected networks, it has the following definitions: |
:*A Firewall is an integrated collection of security measures designed to prevent unauthorized electronic access to a networked computer system.[3] | :*A Firewall is an integrated collection of security measures designed to prevent unauthorized electronic access to a networked computer system.[3] | ||
| - | :*A Firewall is a device or set of devices configured to permit, deny, encrypt, decrypt, or proxy all computer traffic between different security domains based upon a set of rules and other criteria.[3] | + | :*A Firewall is a device or set of devices configured to permit, deny, encrypt, decrypt, or [[Proxy Server|proxy]] all computer traffic between different security domains based upon a set of rules and other criteria.[3] |
:*A Firewall is a device that divide a network into parts, when some parts have distinct security needs.[1:23] | :*A Firewall is a device that divide a network into parts, when some parts have distinct security needs.[1:23] | ||
:*A Firewall is a separator, a restricter, an analyzer.[1:22] | :*A Firewall is a separator, a restricter, an analyzer.[1:22] | ||
| + | |||
===Benefits of Firewall=== | ===Benefits of Firewall=== | ||
Generally, Firewalls are configured to protect against unauthenticated interactive logins for the outside world, most of the time, it acts like a choke point. All traffic in and out must pass through this single, narrow choke point, which provided a very easy mechanism to monitor, trace, and control information flow. Hence, Firewall is an efficient network security tool to block [[Systems for Detecting Network Intrusion|Intrusion]], [[Denial Of Service Attacks|Denial of service]], and Information theft. | Generally, Firewalls are configured to protect against unauthenticated interactive logins for the outside world, most of the time, it acts like a choke point. All traffic in and out must pass through this single, narrow choke point, which provided a very easy mechanism to monitor, trace, and control information flow. Hence, Firewall is an efficient network security tool to block [[Systems for Detecting Network Intrusion|Intrusion]], [[Denial Of Service Attacks|Denial of service]], and Information theft. | ||
| Line 55: | Line 56: | ||
==Firewall Types== | ==Firewall Types== | ||
There are three types of Firewalls, as: | There are three types of Firewalls, as: | ||
| - | :* Simple packet filtering: IP or filtering firewalls -- Block all but selected network traffic | + | :* [[Network firewall#Simple packet filtering: IP packet filtering Firewall|Simple packet filtering: IP or filtering firewalls]] -- Block all but selected network traffic |
| - | :* Application-layer firewall: Proxy server -- act as intermediary to make requested network connections for the user | + | :* [[Network firewall#Application Firewalls: proxy servers|Application-layer firewall: Proxy server]] -- act as intermediary to make requested network connections for the user |
| - | :* | + | :* [[Network firewall#Multilayer-inspection Firewalls|Multilayer-inspection firewalls]] -- extract the relevant communication and application state information and analyze all packet communication layers. |
===Simple packet filtering: IP packet filtering Firewall=== | ===Simple packet filtering: IP packet filtering Firewall=== | ||
| - | An IP filtering firewall works at the simple IP packet level. It is designed to control the flow of data packets based on their header information, which can be:[[Image:IpHeader. | + | An IP filtering firewall works at the simple IP packet level. It is designed to control the flow of data packets based on their header information, which can be:[[Image:IpHeader.JPG|thumb|right|350px|Figure 2 - Typical Ipv4 Packet Header]] |
:* IP source address | :* IP source address | ||
:* IP destination address | :* IP destination address | ||
| Line 73: | Line 74: | ||
:* The interface the packet arrives on | :* The interface the packet arrives on | ||
:* The interface the packet will go out on | :* The interface the packet will go out on | ||
| + | :* [http://www.rushessay.com/custom_essay.php write my essay] | ||
And finally, a IP packet filtering firewall will keeps track of packets that it has seen knows some useful historical fact, such as: | And finally, a IP packet filtering firewall will keeps track of packets that it has seen knows some useful historical fact, such as: | ||
:* Whether this packet appears to be a response to another packet, which means its source was the destination of a recent packet and it destination is the source of that other packet. | :* Whether this packet appears to be a response to another packet, which means its source was the destination of a recent packet and it destination is the source of that other packet. | ||
| Line 78: | Line 80: | ||
:* Whether this packet is identical to a recently seen packet | :* Whether this packet is identical to a recently seen packet | ||
:* If this packet is part of a larger packet that has been seen broken into parts (fragmented). | :* If this packet is part of a larger packet that has been seen broken into parts (fragmented). | ||
| + | |||
Base on these information, firewall filtering rules (packets routing conditions) can be applied, for example, a screened router may have rules like: | Base on these information, firewall filtering rules (packets routing conditions) can be applied, for example, a screened router may have rules like: | ||
:* Block all incoming connections from systems outside the internal network, except for incoming SMTP connections | :* Block all incoming connections from systems outside the internal network, except for incoming SMTP connections | ||
:* Block all connections to or from certain system you distrust | :* Block all connections to or from certain system you distrust | ||
| - | :* Allow mail and FTP services, but bock dangerous service like TFTP, RPC, etc.[1:106] | + | :* Allow mail and [[Secure File Transfer Protocols|FTP]] services, but bock dangerous service like TFTP, RPC, etc.[1:106] |
<small>(see [[http://linux.about.com/od/commands/l/blcmdl8_iptable.htm Linux/Unix Command: iptables]] for detail iptable example)</small> | <small>(see [[http://linux.about.com/od/commands/l/blcmdl8_iptable.htm Linux/Unix Command: iptables]] for detail iptable example)</small> | ||
| Line 100: | Line 103: | ||
:* Widely available in many hardware and software routing products. [1:108} | :* Widely available in many hardware and software routing products. [1:108} | ||
====Disadvantage of IP packet filtering firewall==== | ====Disadvantage of IP packet filtering firewall==== | ||
| - | Although IP packet filtering firewall provides many advantages, there are some | + | Although IP packet filtering firewall provides many advantages, there are some disadvantages to using packet filtering firewall as well. |
:* Current filtering tools are not perfect. | :* Current filtering tools are not perfect. | ||
:** Filtering rules are hard to configure. | :** Filtering rules are hard to configure. | ||
| Line 111: | Line 114: | ||
[[image:ProxyServer.JPG|thumb|right|350px|Figure 4 - Using proxy service with a dual-homed host]] | [[image:ProxyServer.JPG|thumb|right|350px|Figure 4 - Using proxy service with a dual-homed host]] | ||
In general, a [[Proxy Server|Proxy]] is something or someone who does something on somebody else's behalf. For instance, you may give somebody the authority to vote for you in an election.[1:110] | In general, a [[Proxy Server|Proxy]] is something or someone who does something on somebody else's behalf. For instance, you may give somebody the authority to vote for you in an election.[1:110] | ||
| - | It is called application-level firewall is because the proxies provide replacement connections and act as gateways to service. In addition, proxies are usually called connection bridges, since an virtual "air gap" is exists in the firewall between inside and outside, and proxy server is the only way to exchange information. As figure 4 shows, a "Dual-Homed Host" is act as a proxy server, proxy clients make request directly to this proxy server rather than the real service provider. It is the proxy server's duty to decide whether or not to forward the clients' service request to the real server, and it is also the proxy server's duty to decide whether or not to release the response to the service requesting clients. | + | |
| + | It is called application-level firewall is because the proxies provide replacement connections and act as gateways to service. In addition, proxies are usually called connection bridges, since an virtual "air gap" is exists in the firewall between inside and outside, and proxy server is the only way to exchange information. As figure 4 shows, a "[[Network firewall#Dual-Hoed Host|Dual-Homed Host]]" is act as a proxy server, proxy clients make request directly to this proxy server rather than the real service provider. It is the proxy server's duty to decide whether or not to forward the clients' service request to the real server, and it is also the proxy server's duty to decide whether or not to release the response to the service requesting clients. | ||
| + | |||
Most proxy systems are used to control and optimize outbound connections; they are normally controlled by a site administrator. It is also possible to use proxy servers to control and optimize inbound connections. For instance, to balance connections among multiple servers or to apply extra security. This is sometimes called reverse proxying. | Most proxy systems are used to control and optimize outbound connections; they are normally controlled by a site administrator. It is also possible to use proxy servers to control and optimize inbound connections. For instance, to balance connections among multiple servers or to apply extra security. This is sometimes called reverse proxying. | ||
====Advantage of using Proxy Server==== | ====Advantage of using Proxy Server==== | ||
| Line 127: | Line 132: | ||
:* Proxy server usually require modification to clients, applications, or procedures to suit a specific Internet service. [1:114] | :* Proxy server usually require modification to clients, applications, or procedures to suit a specific Internet service. [1:114] | ||
| - | === | + | ===Multilayer-inspection Firewalls=== |
| + | Multi-layer inspection enables a system administrator to call on packet filtering or stateful inspection for performance, yet provides additional application level security, such as traditional application proxy firewalls provide, through the use of protocol agents. [5] | ||
| + | |||
| + | Specifically, in Multilayer-inspection Firewalls, stateful inspection layer compares the first packets of connections against the defined security policies. Once a connection has been established, it is recorded in a table. This table is checked first when packets arrive at the firewall, and if a packet matches the information there, it is allowed to pass. By using this table of connection data, the overall process of matching and controlling packets is dramatically improved if complex security policies are involved. Protocol agents sit on application layer, it helps other firewall layers to determine if the received packets match the protocol standards. Like [[Secure Shell Client|SSH]] connections (as [[Secure Shell Client|SSH]] packet is encrypted), it examines the first few packets to see if they match the SSH standards, rather to check if these packets are coming from the [[Secure Shell Client|SSH]] port. In addition, Protocol agents can redirect IP packets to contents inspection system like a anti-virus program.[5] | ||
| + | |||
| + | ====Advantage of Multilayer-inspection Firewall==== | ||
| + | Unlike other firewall type, Multilayer-inspection Firewall has the following advantages: | ||
| + | :* Multilayer-inspection Firewalls contrast with traditional firewalls that limit the administrator’s ability to manage the security process, restricting administrators to set configurations, specific protocols, or expensive and proprietary hardware. Multi-layer inspection provides components of traditional technologies, plus new ideas and approaches that overcome the liabilities other firewalls have.[5] | ||
| + | :* Most efficient firewall type | ||
| + | ====Disadvantage of Multilayer-inspection Firewall==== | ||
| + | The disadvantages of Multilayer-inspection Firewall are | ||
| + | :* Expensive | ||
| + | :* Slower than other firewall types | ||
==Firewall Architectures== | ==Firewall Architectures== | ||
| + | There are many Firewall Architectures exist within different Computer Networks, but three basic ones are: | ||
| + | :* [[Network firewall#Single-Box|Single-Box]] | ||
| + | :* [[Network firewall#Screened host|Screened host]] | ||
| + | :* [[Network firewall#Screened subnet|Screened subnet]] | ||
| + | This section will expose those architectures' structure and their appropriate uses. | ||
===Single-Box=== | ===Single-Box=== | ||
| + | Single-Box firewall architecture is the simplest one as it only has a single object acts as firewall. Compare to other firewall architectures, it has the following advantages: | ||
| + | :* A single place you can concentrate on and be sure that you have correctly configured. | ||
| + | :* Cheaper | ||
| + | :* Easier to understand and explain to management | ||
| + | :* Easier to get from an external vendor | ||
| + | :* Configured once then forget about | ||
| + | In practice, Screening Router, Dual-Homed Host, and Multiple-Purpose Boxes are considered to be Single-Box Firewalls. | ||
| + | ====Screening Router==== | ||
| + | As illustrated in Figure 3, it is possible to use a screening router to do IP packet filtering and act like a firewall. | ||
| + | Screening routers are most useful for internal firewalls and for networks that are dedicated to providing services to the Internet. The appropriate uses are: | ||
| + | :* The network being protected already has a high level of host security. | ||
| + | :* The number of protocols being used is limited, and he protocols themselves is straightforward. | ||
| + | :* You require maximum performance and redundancy.[1:122] | ||
| + | |||
| + | ====Dual-Homed Host==== | ||
| + | [[image:DualHomeArc.JPG|thumb|right|350px|Figure 5 - Dual Homed host architecture]] | ||
| + | A dual-host host architecture is built around the dual-homed host computer -- a computer that has at lease two network interfaces. Such a hos could act as a router between the networks interfaces are attached to, as it shows in Figure 5. | ||
| + | |||
| + | Dual-homed hosts can provide a very high level of control, but on another hand, it is not a high-performance devices, as the number of users increased, the performance of this host is significantly reduced. It is also a single point of failure will result disconnection from Internet. | ||
| + | A dual-homed host is an appropriate firewall for a situation where: | ||
| + | :* Traffic to the Internet is small | ||
| + | :* Traffic to the Internet is '''not''' business-critical | ||
| + | :* No Service are being provided to Internet-based users. | ||
| + | :* The network being protected does not contain extremely valuable data. | ||
| + | |||
| + | ====Multiple-Purpose Boxes==== | ||
| + | Many single-box firewalls provide combination of proxying and packet filtering. The benefit is that you can allow some protocols at high speed while still having detailed control. However, it also gives you many disadvantage of both. | ||
| + | A single machine that does both proxying and packet filtering is appropriate for a situation where: | ||
| + | :* The network to be protected is small. | ||
| + | :* No services are being provided to the Internet.[1:126] | ||
| + | |||
===Screened host=== | ===Screened host=== | ||
| + | [[image:ScreenedHost.JPG|thumb|right|350px|Figure 6 - Screened Host Architecture]] | ||
| + | Figure 6 shows a simple version of screened host architecture. The [[Network firewall#Bastion Host|bastion host]] sits on the internal network. The packet filtering on the screening router is set up in such way that [[Network firewall#Bastion Host|bastion host]] is the only system on the internal network that hosts on the Internet can open connection. On another hand, any external system trying to access internal system will have to connect to this host. This allows site administrator to monitor and control the information flow between site and Internet. | ||
| + | The packet filtering router on screened host architecture is normally configured to do one of the following: | ||
| + | :* Allow other internal hosts to open connections to hosts on the Internet for certain service | ||
| + | :* Disallow all connection from internal hosts except from bastion host.[1:127] | ||
| + | Hence, this architecture is more flexible than dual-homed host, since it may allow direct connection from internal host to external host, where dual-home host architecture is not, but also introduced more risk, as if the router is compromised, the entire network is available to an attacker. | ||
| + | |||
| + | Unlike previous architecture, screened-host can provide Internet services to other hosts on Internet through [[Network firewall#Bastion Host|bastion host]], in practice, a screened host architecture is appropriate when: | ||
| + | :* Easy [[Web Services|web services]], means few connections are coming from the Internet (in particular, it is not an appropriate architecture if the screened host is a public web server). | ||
| + | :* The network being protected has a relatively high level of host security.[1:126] | ||
| + | |||
===Screened subnet=== | ===Screened subnet=== | ||
| + | [[image:ScreenedSubnet.JPG|thumb|right|350px|Figure 6 - Screened subnet architecture (using two routers)]] | ||
| + | The screened subnet architecture adds an extra layer of security to the screened host architecture by adding a perimeter network that further isolate the internal network from the Internet. This is because, for screened host architecture, the bastion host is the primary target of Internet attacks, once the bastion host is compromised, the whole internal site is open to attack. However, for screened subnet, if someone successfully breaks into the bastion host, the internal site is still safe as the bastion host is isolated by the perimeter network. | ||
| + | |||
| + | The simplest type of screened subnet, as it shows in Figure 6, there are two screening routers, each connected to the perimeter net. One sits between the perimeter net and the internal network, and the another one sits between the perimeter net and the external network. | ||
| + | |||
| + | A screened subnet architecture is appropriate for most uses. | ||
| + | ====Perimeter Network==== | ||
| + | Perimeter Network is an additional network between the external and internal network, which offers additional protection to internal network. For instance, many internal network are Ethernet type, which is easy to monitor other hosts on the some platform, so once the bastion host sits on Ethernet has been broken in, the whole network is then become insecure, but with perimeter network, the attackers will not be able to touch the internal Ethernet network but only the perimeter network where the bastion host sits on.[1:129] | ||
| + | |||
| + | ====Bastion Host==== | ||
| + | The bastion host is an host sits on perimeter network, this is the main point for incoming connections from the outside world, for example: | ||
| + | :* For incoming email (SMTP) sessions to deliver electronic mail to the internal site | ||
| + | :* For incoming FTP connections to the site's anonymous FTP server. | ||
| + | :* For incoming Domain Name System (DNS) queries about the site. | ||
| + | and so on[1:130] | ||
| + | |||
| + | Outbound service are handled either of these ways: | ||
| + | :* Set up packet filtering on both the exterior and interior routers to allow internal clients to access the external servers directly. | ||
| + | :* Set up proxy servers to run on the bastion host.[1:130] | ||
| + | |||
| + | Much of the bastion host does is act as proxy server to connect to, and accept connection from, hosts on the Internet, and for what service, are dictated by the site's security policy. | ||
| + | |||
| + | ====Interior Router==== | ||
| + | The interior router, also called choke router, protects the internal network both from the Internet and from the perimeter net. It does most of the packet filtering for the firewall. It also reduces the number of machines connect to the bastion host. This is to reduce the risk of internal site exposure if the bastion host has been taken over by an attacker. Normally, only sophisticated Internet service like HTTP and SMTP should be allowed to go through.[1:131] | ||
| + | |||
| + | ====Exterior Router==== | ||
| + | The exterior router, which is also called access router, protects both the perimeter net and the internal net from the Internet. In practice, compares to interior router, exterior router tends to allow almost anything outbound from the perimeter net, and it generally do very little packet filtering. Frequently, exterior router is provided by Internet Service Provider (ISP), only general packet filtering rules are implemented and users may have limited access to it. However, the most important reason to have an exterior router is to block any incoming packets from the Internet that have forged source addresses. Such packets claim to have come from within the internal network but actually are coming in from the Internet, Where the interior router cannot tell if the packet that claim to be from the perimeter net are forged. Another reason to have an exterior router is to prevent IP packets containing inappropriate source addresses from leaving the internal network, since all traffic leaving the internal network should come from only one of the internal addresses.[1:132] | ||
| + | |||
==Firewall Software== | ==Firewall Software== | ||
| - | [http://www.codeproject.com/KB/IP/smfirewall.aspx Simple Packet - Filter Firewall] By sudhirmangla, The CodeProject.com | + | * [http://www.codeproject.com/KB/IP/smfirewall.aspx Simple Packet - Filter Firewall] By sudhirmangla, The CodeProject.com |
| + | * [http://sourceforge.net/projects/firewallpapi/ FirewallPAPI] Open source Firewall for Windows 2000 & up | ||
| + | * [http://www.pfsense.org/index.php?option=com_frontpage&Itemid=1 pfSence], Open source Firewall, pfsense.org | ||
| + | * [http://www.modsecurity.org/ ModSecurity], Open source Firewall, Modsecurity.org | ||
| + | * [http://firewallpapi.en.softonic.com/ FirewallPAPI], Open source Firewall, Softonic.com | ||
==References== | ==References== | ||
| Line 141: | Line 237: | ||
# [http://en.wikipedia.org/wiki/Network_firewall Firewall], Wikipedia, Accessed on April 3rd 2009 21:35. | # [http://en.wikipedia.org/wiki/Network_firewall Firewall], Wikipedia, Accessed on April 3rd 2009 21:35. | ||
# [http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/ip-packet.html IPv4 Packet Header], Engineering, University of Aberdeen, Accessed on April 10th 2009 21:10 | # [http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/ip-packet.html IPv4 Packet Header], Engineering, University of Aberdeen, Accessed on April 10th 2009 21:10 | ||
| + | # [http://www.stonesoft.com/export/download/pdf/wp_Multi-Layer_letter.pdf Multi-Layer Inspection], StoneSoft, Stonesoft.com | ||
==See also== | ==See also== | ||
| Line 152: | Line 249: | ||
* [[Public Key Authentication]] | * [[Public Key Authentication]] | ||
* [[Email Security]] | * [[Email Security]] | ||
| + | * [[Operating Systems Security]] | ||
==External links== | ==External links== | ||
| Line 157: | Line 255: | ||
# [http://www.spirit.com/Network/net0597.txt History of Firewall Technologies] A text file by Rik Farrow and Richard Power, Spirit.com | # [http://www.spirit.com/Network/net0597.txt History of Firewall Technologies] A text file by Rik Farrow and Richard Power, Spirit.com | ||
# [http://linux.about.com/od/commands/l/blcmdl8_iptable.htm Linux/Unix Command: iptables],by Juergen Haas, about.com | # [http://linux.about.com/od/commands/l/blcmdl8_iptable.htm Linux/Unix Command: iptables],by Juergen Haas, about.com | ||
| + | # [http://www.vicomsoft.com/knowledge/reference/firewalls1.html Firewall Q & A], vicomsoft, vicomsoft.com | ||
| + | # [http://www.microsoft.com/windowsxp/using/security/internet/sp2_wfintro.mspx Understanding Windows Firewall], Windows Firewall, Microsoft.com | ||
| + | # [http://www.hackerwatch.org/probe/ Firewall Test], HackerWatch.org | ||
| + | # [http://www.aboutdebian.com/firewall.htm How To Set Up A Debian Linux Firewall], aboutdebian.com | ||
==Time-stamped Signature== | ==Time-stamped Signature== | ||
| - | [[User:Fulx|Fulx]] | + | [[User:Fulx|Fulx]] 06:03, 12 April 2009 (EDT) |
Current revision as of 19:44, 9 January 2010
Network Firewall is now considered as a first line of defense in the form of a barrier against outside attacks, which is installed on computers connect to internet. In general, Firewall prevents the dangers of Internet from spreading to your internal network. It more like a moat of a medieval castle that a firewall in a modern building. It serves multiple purposes [1:21]:- It restricts people to entering at a carefully controlled point.
- It prevents attackers from getting close to your other defenses.
- It restricts people to leaving at a carefully controlled point.[1:21]
In practice,a firewall is a collection of hosts, routers, and other hardware that designed to prevent unauthorized electronic access between two parts of a network. It is also a device or set of devices configured to permit, deny, encrypt, decrypt, or proxy all computer traffic between different security domains based upon a set of rules and other criteria.[3]
Firewalls can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria.[3]
Contents |
Why Firewall
The Internet is marvelous technological advance that provides access to information, and the ability to publish information, in revolutionary ways. But it's also a major danger that provides the ability to pollute and destroy information in revolutionary ways. For this reason, no matter what kind of information you put on Internet, you may always try to protect:
- Your Data?
- Secrecy: accessibility for a certain group of people
- Integrity: no data change by others
- Availability: always able to use it by you or by a group of people who have the permit.
- Your Resources? Your computer cycle and storage space.
- Your Reputation? No one should appear on the Internet with your identity. [1:7]
- Your Data?
if you answer YES to any of above, then Network Firewall is the solution you needed.
What is Firewall
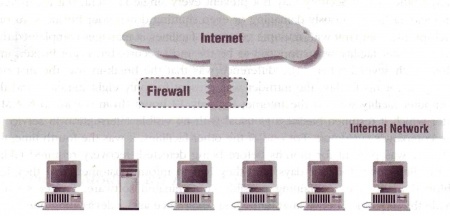
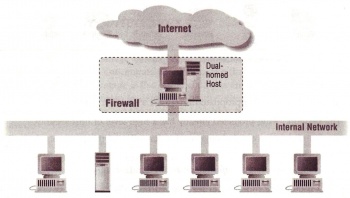
As Figure 1 shows, a Firewall is a box/device between two connected networks, it has the following definitions:
- A Firewall is an integrated collection of security measures designed to prevent unauthorized electronic access to a networked computer system.[3]
- A Firewall is a device or set of devices configured to permit, deny, encrypt, decrypt, or proxy all computer traffic between different security domains based upon a set of rules and other criteria.[3]
- A Firewall is a device that divide a network into parts, when some parts have distinct security needs.[1:23]
- A Firewall is a separator, a restricter, an analyzer.[1:22]
Benefits of Firewall
Generally, Firewalls are configured to protect against unauthenticated interactive logins for the outside world, most of the time, it acts like a choke point. All traffic in and out must pass through this single, narrow choke point, which provided a very easy mechanism to monitor, trace, and control information flow. Hence, Firewall is an efficient network security tool to block Intrusion, Denial of service, and Information theft. The following are the primary benefits of using a firewall:
- Protection from vulnerable service that are running on the server that may increase its vulnerability to attack
- Controlled access to site systems
- Concentrated Security
- Enhanced privacy
- Logging and statistics on network use, misuse
- Policy enforcement
- VPN
- DMZ
[2:12]
Limitations of Firewall
In general, a Network Firewall has the following limitations:
- Network Firewall cannot protect against attacks that don't go through the Firewall.
- example: a dial-up modem connection that allow users to dial-in to access the internal systems behind the firewall. The firewall has absolutely no way of preventing an intruder from getting in through such a modem.
- Network Firewall cannot protect against malicious insiders.
- Internal users may be blocked from sending information out by Firewall block service, but they can still download, copy the data onto disks or flash drives.
- Network Firewall cannot protect against viruses.
- Detecting a virus in a random packet of data passing through a Firewall is very difficult, as it requires:
- recognizing that the packet is part of a program
- Determine what the program should look like and its behavior.
- Determine that a change in the program is a threats to system
- Detecting a virus in a random packet of data passing through a Firewall is very difficult, as it requires:
- Network Firewall cannot protect against completely new threats.
- Firewall is designed to protect against known threats. People continuously discover new ways to attack, using previously trustworthy services, or using attacks that simply has not occurred to anyone before.
- Network Firewall cannot set itself up correctly.
- Every Firewall need some amount of configuration, as every site/private network is different, so it is impossible to use a universal firewall which will set itself up automatically. Correct configuration is absolutely essential.
- Network Firewall cannot protect against attacks that don't go through the Firewall.
[1:24]
Firewall Types
There are three types of Firewalls, as:
- Simple packet filtering: IP or filtering firewalls -- Block all but selected network traffic
- Application-layer firewall: Proxy server -- act as intermediary to make requested network connections for the user
- Multilayer-inspection firewalls -- extract the relevant communication and application state information and analyze all packet communication layers.
Simple packet filtering: IP packet filtering Firewall
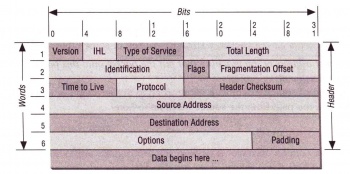
An IP filtering firewall works at the simple IP packet level. It is designed to control the flow of data packets based on their header information, which can be:- IP source address
- IP destination address
- Protocol (TCP, UDP, ICMP)
- TCP or UDP source port
- TCP or UDP destination port
- ICMP message type
- Packet size[1:105]
A traditional firewall, like a simple router, is generally make their decision based on the source, destination addresses, and port in individual IP packets. Modern simple packet-filtering firewalls have become increasingly sophisticated and maintain internal information about the state of connections passing through them, the contents of some of the data steam, and so on. For instance, modern routers can also look past the packet headers at data further on in the packet, this will allows firewall to filter packet based on more detailed information, like the name of the web page that someone is requesting and if the packet is valid (means if the packet size is the same as it claims to be and legal), which helps catch a number of denial of service attacks based on malformed packets. In addition, modern firewalls know things about the packet that are not reflected in the packet itself, such as:
- The interface the packet arrives on
- The interface the packet will go out on
- write my essay
And finally, a IP packet filtering firewall will keeps track of packets that it has seen knows some useful historical fact, such as:
- Whether this packet appears to be a response to another packet, which means its source was the destination of a recent packet and it destination is the source of that other packet.
- How many other packet have recently been seen to or from the same host.
- Whether this packet is identical to a recently seen packet
- If this packet is part of a larger packet that has been seen broken into parts (fragmented).
Base on these information, firewall filtering rules (packets routing conditions) can be applied, for example, a screened router may have rules like:
- Block all incoming connections from systems outside the internal network, except for incoming SMTP connections
- Block all connections to or from certain system you distrust
- Allow mail and FTP services, but bock dangerous service like TFTP, RPC, etc.[1:106]
(see [Linux/Unix Command: iptables] for detail iptable example)
Once the IP packet filtering firewall completed the packet audit, it may perform one of the following action:
- Send packet to its intend destination.
- Drop packet.
- Reject the packet.
- Log information about the packet.
- Notify somebody about the packet immediately. [1:107]
and more sophisticated firewalls might also be able to do one or more of these things:
- Modify the packet
- Send the packet to a different destination, for instance, re-direct the packet to a Proxy server.
- Modify the filtering rule accordingly. [1:107]
Advantages of IP packet filtering firewall
Simple IP packet filtering firewall tends to be very fast and very transparent to users. [2:51] It has a number of advantages:
- One screening router can help protect an entire network
- Simple packet filtering is extremely efficient -- only need to pay attention to a few packet headers, and contents only if needed.
- Widely available in many hardware and software routing products. [1:108}
Disadvantage of IP packet filtering firewall
Although IP packet filtering firewall provides many advantages, there are some disadvantages to using packet filtering firewall as well.
- Current filtering tools are not perfect.
- Filtering rules are hard to configure.
- Once configures, filtering rules are tend to be hard to test.
- bugs.
- Performance of the screening router is reduced.
- Some policies cannot be implemented/enforced by IP packet filtering firewall. [1:109]
- Current filtering tools are not perfect.
Application Firewalls: proxy servers
In general, a Proxy is something or someone who does something on somebody else's behalf. For instance, you may give somebody the authority to vote for you in an election.[1:110]
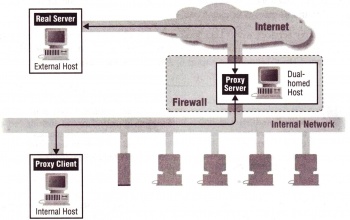
It is called application-level firewall is because the proxies provide replacement connections and act as gateways to service. In addition, proxies are usually called connection bridges, since an virtual "air gap" is exists in the firewall between inside and outside, and proxy server is the only way to exchange information. As figure 4 shows, a "Dual-Homed Host" is act as a proxy server, proxy clients make request directly to this proxy server rather than the real service provider. It is the proxy server's duty to decide whether or not to forward the clients' service request to the real server, and it is also the proxy server's duty to decide whether or not to release the response to the service requesting clients.
Most proxy systems are used to control and optimize outbound connections; they are normally controlled by a site administrator. It is also possible to use proxy servers to control and optimize inbound connections. For instance, to balance connections among multiple servers or to apply extra security. This is sometimes called reverse proxying.
Advantage of using Proxy Server
Compare to simple IP packet filtering firewall, using Proxy Server has the following advantages:
- Proxy server can be good at logging -- as proxy server understand the application protocols.
- Proxy server can provide caching -- keeping local copy of frequently requested data.
- Proxy server can do intelligent filtering -- by looking at specific connection, filtering criteria can on applies to that connection.
- Proxy server can perform user level authentication -- as it is the Proxies duty to validate the user
- Proxy server automatically provide protection for weak or fault IP implementation -- as Proxies sit between a clients and the Internet, it generates completely new IP packet for the client. [1:113]
Disadvantage of using Proxy Server
There are also some disadvantages to use a Proxy Server:
- Proxy Server lag behind Non-proxy Server -- as new Internet service does have a matched Proxy.
- Proxy services may require different proxy server for each service -- as you may need a different proxy server for each protocol due to the proxy server may need to understand the protocol in order to determine what to allow and dis-allow.
- Proxy server usually require modification to clients, applications, or procedures to suit a specific Internet service. [1:114]
Multilayer-inspection Firewalls
Multi-layer inspection enables a system administrator to call on packet filtering or stateful inspection for performance, yet provides additional application level security, such as traditional application proxy firewalls provide, through the use of protocol agents. [5]
Specifically, in Multilayer-inspection Firewalls, stateful inspection layer compares the first packets of connections against the defined security policies. Once a connection has been established, it is recorded in a table. This table is checked first when packets arrive at the firewall, and if a packet matches the information there, it is allowed to pass. By using this table of connection data, the overall process of matching and controlling packets is dramatically improved if complex security policies are involved. Protocol agents sit on application layer, it helps other firewall layers to determine if the received packets match the protocol standards. Like SSH connections (as SSH packet is encrypted), it examines the first few packets to see if they match the SSH standards, rather to check if these packets are coming from the SSH port. In addition, Protocol agents can redirect IP packets to contents inspection system like a anti-virus program.[5]
Advantage of Multilayer-inspection Firewall
Unlike other firewall type, Multilayer-inspection Firewall has the following advantages:
- Multilayer-inspection Firewalls contrast with traditional firewalls that limit the administrator’s ability to manage the security process, restricting administrators to set configurations, specific protocols, or expensive and proprietary hardware. Multi-layer inspection provides components of traditional technologies, plus new ideas and approaches that overcome the liabilities other firewalls have.[5]
- Most efficient firewall type
Disadvantage of Multilayer-inspection Firewall
The disadvantages of Multilayer-inspection Firewall are
- Expensive
- Slower than other firewall types
Firewall Architectures
There are many Firewall Architectures exist within different Computer Networks, but three basic ones are:
This section will expose those architectures' structure and their appropriate uses.
Single-Box
Single-Box firewall architecture is the simplest one as it only has a single object acts as firewall. Compare to other firewall architectures, it has the following advantages:
- A single place you can concentrate on and be sure that you have correctly configured.
- Cheaper
- Easier to understand and explain to management
- Easier to get from an external vendor
- Configured once then forget about
In practice, Screening Router, Dual-Homed Host, and Multiple-Purpose Boxes are considered to be Single-Box Firewalls.
Screening Router
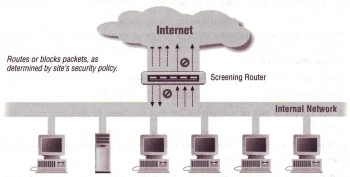
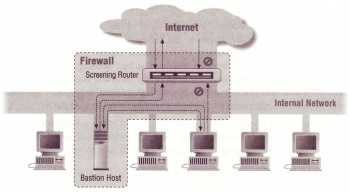
As illustrated in Figure 3, it is possible to use a screening router to do IP packet filtering and act like a firewall. Screening routers are most useful for internal firewalls and for networks that are dedicated to providing services to the Internet. The appropriate uses are:
- The network being protected already has a high level of host security.
- The number of protocols being used is limited, and he protocols themselves is straightforward.
- You require maximum performance and redundancy.[1:122]
Dual-Homed Host
A dual-host host architecture is built around the dual-homed host computer -- a computer that has at lease two network interfaces. Such a hos could act as a router between the networks interfaces are attached to, as it shows in Figure 5.
Dual-homed hosts can provide a very high level of control, but on another hand, it is not a high-performance devices, as the number of users increased, the performance of this host is significantly reduced. It is also a single point of failure will result disconnection from Internet. A dual-homed host is an appropriate firewall for a situation where:
- Traffic to the Internet is small
- Traffic to the Internet is not business-critical
- No Service are being provided to Internet-based users.
- The network being protected does not contain extremely valuable data.
Multiple-Purpose Boxes
Many single-box firewalls provide combination of proxying and packet filtering. The benefit is that you can allow some protocols at high speed while still having detailed control. However, it also gives you many disadvantage of both. A single machine that does both proxying and packet filtering is appropriate for a situation where:
- The network to be protected is small.
- No services are being provided to the Internet.[1:126]
Screened host
Figure 6 shows a simple version of screened host architecture. The bastion host sits on the internal network. The packet filtering on the screening router is set up in such way that bastion host is the only system on the internal network that hosts on the Internet can open connection. On another hand, any external system trying to access internal system will have to connect to this host. This allows site administrator to monitor and control the information flow between site and Internet. The packet filtering router on screened host architecture is normally configured to do one of the following:
- Allow other internal hosts to open connections to hosts on the Internet for certain service
- Disallow all connection from internal hosts except from bastion host.[1:127]
Hence, this architecture is more flexible than dual-homed host, since it may allow direct connection from internal host to external host, where dual-home host architecture is not, but also introduced more risk, as if the router is compromised, the entire network is available to an attacker.
Unlike previous architecture, screened-host can provide Internet services to other hosts on Internet through bastion host, in practice, a screened host architecture is appropriate when:
- Easy web services, means few connections are coming from the Internet (in particular, it is not an appropriate architecture if the screened host is a public web server).
- The network being protected has a relatively high level of host security.[1:126]
Screened subnet
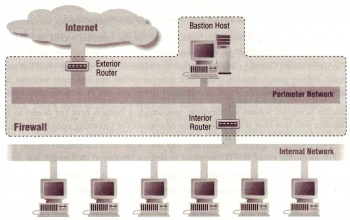
The screened subnet architecture adds an extra layer of security to the screened host architecture by adding a perimeter network that further isolate the internal network from the Internet. This is because, for screened host architecture, the bastion host is the primary target of Internet attacks, once the bastion host is compromised, the whole internal site is open to attack. However, for screened subnet, if someone successfully breaks into the bastion host, the internal site is still safe as the bastion host is isolated by the perimeter network.
The simplest type of screened subnet, as it shows in Figure 6, there are two screening routers, each connected to the perimeter net. One sits between the perimeter net and the internal network, and the another one sits between the perimeter net and the external network.
A screened subnet architecture is appropriate for most uses.
Perimeter Network
Perimeter Network is an additional network between the external and internal network, which offers additional protection to internal network. For instance, many internal network are Ethernet type, which is easy to monitor other hosts on the some platform, so once the bastion host sits on Ethernet has been broken in, the whole network is then become insecure, but with perimeter network, the attackers will not be able to touch the internal Ethernet network but only the perimeter network where the bastion host sits on.[1:129]
Bastion Host
The bastion host is an host sits on perimeter network, this is the main point for incoming connections from the outside world, for example:
- For incoming email (SMTP) sessions to deliver electronic mail to the internal site
- For incoming FTP connections to the site's anonymous FTP server.
- For incoming Domain Name System (DNS) queries about the site.
and so on[1:130]
Outbound service are handled either of these ways:
- Set up packet filtering on both the exterior and interior routers to allow internal clients to access the external servers directly.
- Set up proxy servers to run on the bastion host.[1:130]
Much of the bastion host does is act as proxy server to connect to, and accept connection from, hosts on the Internet, and for what service, are dictated by the site's security policy.
Interior Router
The interior router, also called choke router, protects the internal network both from the Internet and from the perimeter net. It does most of the packet filtering for the firewall. It also reduces the number of machines connect to the bastion host. This is to reduce the risk of internal site exposure if the bastion host has been taken over by an attacker. Normally, only sophisticated Internet service like HTTP and SMTP should be allowed to go through.[1:131]
Exterior Router
The exterior router, which is also called access router, protects both the perimeter net and the internal net from the Internet. In practice, compares to interior router, exterior router tends to allow almost anything outbound from the perimeter net, and it generally do very little packet filtering. Frequently, exterior router is provided by Internet Service Provider (ISP), only general packet filtering rules are implemented and users may have limited access to it. However, the most important reason to have an exterior router is to block any incoming packets from the Internet that have forged source addresses. Such packets claim to have come from within the internal network but actually are coming in from the Internet, Where the interior router cannot tell if the packet that claim to be from the perimeter net are forged. Another reason to have an exterior router is to prevent IP packets containing inappropriate source addresses from leaving the internal network, since all traffic leaving the internal network should come from only one of the internal addresses.[1:132]
Firewall Software
- Simple Packet - Filter Firewall By sudhirmangla, The CodeProject.com
- FirewallPAPI Open source Firewall for Windows 2000 & up
- pfSence, Open source Firewall, pfsense.org
- ModSecurity, Open source Firewall, Modsecurity.org
- FirewallPAPI, Open source Firewall, Softonic.com
References
- Elizabeth D. Zwicky, Simon Cooper, and D. Brent Chapman;Building internet Firewalls, Second Edition; Published by O'Reilly & Associates, Inc. @2000; ISBN:1-56592-871-7, McMaster Thode Library: TK 5105.59.Z85 2000
- John R. Vacca, Scott R. Ellis; Firewalls, Jumpstart for Network and Systems Administrators; Elsevier digital press @2005; ISBN: 1-55558-297-4, McMaster Thode Library: TK 5105.59.V32 2005
- Firewall, Wikipedia, Accessed on April 3rd 2009 21:35.
- IPv4 Packet Header, Engineering, University of Aberdeen, Accessed on April 10th 2009 21:10
- Multi-Layer Inspection, StoneSoft, Stonesoft.com
See also
- Web content filtering
- Deep packet inspection
- Virtual Private Network
- Tools for conducting denial-of-service attacks
- Peer To Peer Network Security
- Corporate Security and IT Policies
- Personal Data Protection and Privacy
- Public Key Authentication
- Email Security
- Operating Systems Security
External links
- Firewalls and Internet Security by Frederic Avolio, Avolio Consulting, Cisco Systems.
- History of Firewall Technologies A text file by Rik Farrow and Richard Power, Spirit.com
- Linux/Unix Command: iptables,by Juergen Haas, about.com
- Firewall Q & A, vicomsoft, vicomsoft.com
- Understanding Windows Firewall, Windows Firewall, Microsoft.com
- Firewall Test, HackerWatch.org
- How To Set Up A Debian Linux Firewall, aboutdebian.com
Time-stamped Signature
Fulx 06:03, 12 April 2009 (EDT)