Wi-Fi
From Computing and Software Wiki
Wi-Fi is a consortium that verifies 802.11b wireless network products interoperate, and a marketing term vendors use to sell their products.[1]
Wi-Fi is a subsection of the IEEE 802, a subcategory in the link layer of the TCP/IP Internet Protocol Suite. The Wi-Fi alliance is a trade group that owns the 'Wi-Fi' trademark, a symbol that certifies interoperability between wireless devices. Not every Internet product is Wi-Fi certified however, and there exists many devices that are able to interoperate wirelessly without the Wi-Fi logo. Some products have chosen to omit having Wi-Fi certification to avoid paying certification costs.
The use of Wi-Fi has boomed in recent years and is supported by a multitude of different devices. Laptops. game consoles, smartphones, printers and other peripherals usually have Wi-Fi certification.
Contents |
History
Wi-Fi was invented by Vic Hayes (dubbed 'the father of Wi-Fi') at the NCR Corporation/AT & T (later Lucent & Agere Systems), in 1991. Hayes had been designing IEEE standards for 802.11b, 802.11a and 802.11g and subsequent technology, initially meant for cashier systems. NCR initially released the technology under the name of 'WaveLAN' which operated in a range of 1Mbps-2 Mbps. [2] The Wi-Fi alliance was created soon after the technology.
The alliance is a consortium of separate, independent companies that promotes and develops IEEE 802.11 standards. The alliance also tests products to establish interoperability and certifies products that pass. The 'Wi-Fi' logo is allowed to be used by manufacturers who subscribe to the alliance and whose products pass testing. There exists sever unofficial "Wi-Fi" products that may work, but lack true certification.
The term "Wi-Fi" was coined by Interbrand Corporation in August 1999 when hired by the Alliance to change the name from 'IEEE 802.11b Direct Sequence.' Interbrand also created the official 'Wi-Fi' logo. It is often assumed that Wi-Fi stands for "Wireless Fidelity", however officially Wi-Fi is an abstract term and the Wi-Fi alliance is trying to downplay any association to "Hi-Fi" (High Fidelity).
Many cities globally, have announced plans for a city-wide Wi-Fi network. Many such project have since been cancelled due to unforseen difficulties however, a few (such as Sunnyvale, California) were successful. The city-wide networks were created by meshing several wireless antenna together and effectively creating a very large hotspot.
Uses
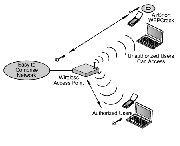
There are typically two ses for Wi-Fi: it can be used as an access technology whereby a single base station (access point) accomodates multiple clients, or it can be used in a point-to-point configuration, connecting exactly 2 access points. The latter is typically reserved for standard 802.16 (Wi-Max) and used by network providers or corporations to connect two sites.
A Wi-Fi enabled device can connect to the internet if the access point it reaches is part of a network containing the internet. A wi-Fi enabled device can essentially use the internet for any networking purpose.
There exists many wireless 'hotspots' which integrate one or more access points and the hotspots can span a range of a few meters to several kilometers( Sunnyvale, California for example, offers free city-wide Wi-Fi). Many businesses offer wireless hotspots as either free or pay services in order to attract customers.
Wi-Fi devices can operate in different modes such as peer-to-peer mode, which allows a direct connection between two people. In ad-hoc mode Wi-Fi devices are able to make client-to-client connections without a router.
Wi-Fi can enable wireless voice application (VoIP). The widespread growth of Wi-Fi now allows access to the internet outside 'traditional' setups (such as the bathroom). Wi-Fi installations can ultimately provide: a sequre computer networking gateway, firewall, DHCP server, intrusion detection system and many other services.
Advantages and Challenges
Wi-Fi uses an unlicensed radio spectrum (unlike packet radio systems) and does not require regulatory approval for individual developers, which makes Wi-Fi products widely available. Different brands are able to make products that are interoperable at a basic service level because of the technological foundations in Wi-Fi. Competition amounsts vendors has also considerably lowered prices of Wi-Fi products, and they continue to drop as technology improves.
Wi-Fi allows local area networks (LANs) to be set up without wires, which simultaneously lowers costs (of creating and exapnding) and allows much freedom in where a network can be accessed. The Wi-Fi certification aheres to a global set of standards as well so Wi-Fi products are compatible in any region.
Range
Typically a Wi-Fi router in a home setup with a 802.11b stock antenna has a range of about 32m indoors (due to barriers like walls) and about 95m with no obstructions, outdoors. The frequency block a router uses also affects the range: 2.4GHz has a greater range than 5 GHz. Wi-Fi has greater range compared to bluetooth and can provide huge outdoor range if a network incorporates a directional antenna.
Wi-Fi began with IEEE standards for short range wireless broadband technology, and appointed the standard numbers: 802.11b(Wi-Fi), 802.11a and 802.11g (can interoperate with 802.11b). Typically Wi-Fi operates between 2.5 to 4Mbps, but can go as high as 11 Mbps.
Mobility
Wi-Fi technology allows LANs to be deployed without cabling, potentially reducing the costs of network deployment and expansion. Spaces where cables cannont be run, such as outdoor areas or historical buildings can host wireless LANs. Wi-Fi technology increases the ease of setting up a network as well.
Wi-Fi networks support roaming, in which a mobile client station (like a laptop or smartphone) can move from one access point to another as the user moves. It is because Wi-Fi certified devices are able to interoperate that this is possible without complications as well.
Security
The greatest security issue with Wi-Fi (and all other wireless networks) is the easy of connectivity compared to traditional wired networks like Ethernet. Wireless communication (bluetooth especially) is designed to be simple and easily connected to. To make an attack on a wired network, the attacker must physically connect to the internal network or break through an external firewall. External access however is usually disallowed by business networks in order to protect sensitive data. It is because firewall encryption could be broken that most business networks disallow external access. Getting wireless reception is considered an attack to most business networks.[3]
The nature most wireless networks is to allow external access in order to maintain an degree of usability. If attackers gain access to a wireless network they can harm the user in a variety of ways from monitoring others' activity to fabricating a DNS spoofing attack.
Preventative Measures
WEP (Wired Equivalent Privacy) keys uses a deprecated algorithm to secure Wireless networks. First introduced in 1997, WEP keys were intended to make wireless networks have comparable security to that of wired networks. A WEP key could be interpreted as a 26 digit password allowing access to a home network. There are several security flaws in the WEP keys currently being used and there exists readily available software (such as AirSnort or AirCrack) that can obtain a WEP key in minutes. WEP keys are now considered completely broken. The security flaws of WEP keys was first counteracted in 2002 with 'Wi-Fi Protected Access' (WPA) but the attack vector are now known. Now (as of 2004), full IEEE 802.11i (WPA2) encryption standards have been release and are still considered secure as of 2009.
Another security measure in effect involves suppressing the Access Points' SSID broadcast to only allow a predefined set of MAC addresses the ability to join the network. This security measure has since proven ineffective, since if an allowed MAC address is known (or found out) by an attacker then they could potentially change their own MAC address to spoof as an allowed machine.
DNS Spoofing and Kaminsky Attack
In June 2005 Dan Kaminsky used a DNS hack in order to get free Wi-Fi at an area starbucks. He later realized the huge security issues this presented and brought attention to the Wi-Fi and DNS security flaws. Starbucks offers a Wi-Fi service but it costs a premium, the Kaminsky hack fools the domain name system and thorough Wi-Fi, exposed a glaring Internet security flaw.
The following is an excerpt from WIRED magazine:
How DNS works
1. Type anybank.com into your Web brower and the query packet is sent to your internet service provider (ISP)
2. If anybank.com's location isn't cached, your ISP's name server repeatedly searches the domain name system for it. Each search is assigned a 16-bit transaction ID for security and tracking. Responses to the searches must carry the correct transaction ID to be accepted by the name server. The packet would travel through the root name server, the .com name server then anybank.com name server.
3. Eventually, anybank.com sends an answer to your ISP; Our home page is at 60.190.216.103. This authenticated address is cached.
4. Your browser connects you.
How the Kaminsky DNS hack works
1. The attacker tries to hijack anybank.com by sending thousands of requests for fake Web pages. Malicious query packets are sent to your ISP.
2. The ISP gives each query a transaction ID (unknown to the attacker) and attempts to locates the pages.
3. At the same time, the attacker sends hundreds of responses for each malicious request. Every answer includes a randomly generated ID number.
4. Eventually one of the answers carries an ID that matches, tricking the ISP into accepting and caching the information. The now-legitimized answer contains false details about anybank.com, such as the location of its servers. Legitimate answers from anybank.com("No such page exists") will now be rejected.
5. Users looking for anybank.com get sent to the fake location already in the ISP's cache.
6. Anybank.com customers are now using a look-alike site built by the hacker.
Patch fixing Kaminsky attack
Most computers have 63, 536 ports, but DNS commonly uses only port 53 for all queries and responses. The patch works by randomly changing the port number for each DNS request. Now any response to a request must contain an accurate transaction ID number and return to the same port. The change increases the odds of beating the system from one in 65, 536 to one in 4 billion.[sup][numb][/sup]
Piggybacking
Piggybacking refers to accessing a wireless internet connection by bringing a wireless device in range of another connection and using the service without the owners knowledge or permission. Piggybacking is completely outlawed in some jurisdictions, but allowed in others. It is not considered piggybacking if a bussiness offers a Wi-Fi hotspot for free or as a pay service.
Piggybacking ofter goes unnoticed since most people only use a fraction of their upstream bandwidth. Piggybacking may also be carried out unintentionally, as most access points are configured without encryption (WPA2) and operating systems can automatically connect to wireless networks. The danger in piggybacking exists in users logging into an insecure network where illicit activity is conducted (danger for network owner) or sensitive information is broadcast (danger for user).
The Wi-Fi Scam, Home Security Scam and Bluetooth Scam
'The Real Hustle' a UK television show is premised as an educational program demonstrating how people are getting ripped-off by confidence men around the world. The hustlers demonstrate how easy it is to gain access to a Wireless network through various scams.
In the Wi-Fi Scam, the hustlers hijack a wireless network then rename their own wireless network and route people to a dummy site that looks completely legitimate.
In the Home Security Scam, the hustlers walk through a residential neighborhood and enter home wireless networks by either hacking WEP keys or finding an unlocked network. The hustlers then monitor others online activity.
In the Bluetooth Scam, the hustlers scan a shopping mall for bluetooth signals from mobile phones. Once a signal is found and a connection is made, the hustlers call their premium rate line and rack up a bill for the cell phone owner.
There exists dozens of tutorials on the Internet on how to use Wi-Fi for illicit purposes, demonstrating just how vunerable a wireless network is.
Other 802 Standards and Amendments
References
- Comer, D. E. (2006). Wi-Fi. Internetworking with TCP/IP (Fifth ed., pp. 419-441). Upper Saddle River, NJ: Pearson Prentice Hall.
- "Wi-Fi History". Retrieved on 2009-04-07
- "Pros and Cons...". Retrieved on 2009-04-07
See Also
External Links
--Hamilr3 00:51, 10 April 2009 (EDT)