VoIP (Voice Over IP) Security
From Computing and Software Wiki
| (6 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
'''VoIP''' (Voice over Internet Protocol) is a protocol used for the transmission of voice data across the Internet. IP telephony treats voice as another form of data that is compressed and optimized for network traffic and is vulnerable to attacks traditional data would be on the network. VoIP security is akin to network security; voice data traveling the network will look like any other normal data. | '''VoIP''' (Voice over Internet Protocol) is a protocol used for the transmission of voice data across the Internet. IP telephony treats voice as another form of data that is compressed and optimized for network traffic and is vulnerable to attacks traditional data would be on the network. VoIP security is akin to network security; voice data traveling the network will look like any other normal data. | ||
| - | + | [[Image:oldphone.JPG|frame|right|Has VoIP evolved enough so that the benefits outweigh the costs?]] | |
| - | Corporations generally place VoIP concerns on the voice quality, latency, and quality of service above the overall security when VoIP telephony is actually more vulnerable to certain attacks compared to the traditional phone system. The most common threats found in the VoIP environment include eavesdropping, theft of services, and denial of service attacks. | + | Corporations generally place VoIP concerns on the voice quality, latency, and quality of service above the overall security when VoIP telephony is actually more vulnerable to certain attacks compared to the traditional phone system.[1] The most common threats found in the VoIP environment include eavesdropping, theft of services, and denial of service attacks.[7] |
==Introduction== | ==Introduction== | ||
| - | |||
To greater understand VoIP security, a general overview of VoIP systems is useful. | To greater understand VoIP security, a general overview of VoIP systems is useful. | ||
===Components=== | ===Components=== | ||
| - | A typical VoIP system includes four components: | + | A typical VoIP system includes four components[6]: |
| - | {| border=" | + | |
| - | + | {| border="1" cellpadding="2" | |
| - | + | ||
|- | |- | ||
| - | | | + | |width="5%"|'''Data Network''' |
| - | '''Data Network''' | + | |width="90%"| |
| - | | | + | |
* Must be high performance to avoid choppy communication | * Must be high performance to avoid choppy communication | ||
* QoS (Quality of Service) standard to prioritize voice traffic over data traffic | * QoS (Quality of Service) standard to prioritize voice traffic over data traffic | ||
| Line 23: | Line 20: | ||
*** Layer 2 QoS mechanism | *** Layer 2 QoS mechanism | ||
|- | |- | ||
| - | | | + | |'''IP Handset''' |
| - | '''IP Handset''' | + | |
| | | | ||
* Handset has to be IP enabled so audio stream can be digitized to be transmitted on the IP network | * Handset has to be IP enabled so audio stream can be digitized to be transmitted on the IP network | ||
|- | |- | ||
| - | | | + | |'''Call Server''' |
| - | '''Call Server''' | + | | |
| - | | | + | |
* Application running on dedicated workstation | * Application running on dedicated workstation | ||
* Provides all call signaling | * Provides all call signaling | ||
| Line 36: | Line 31: | ||
* Core operating code of a PBX (Private Branch Exchange) transferred here | * Core operating code of a PBX (Private Branch Exchange) transferred here | ||
|- | |- | ||
| - | | | + | |'''Gateway''' |
| - | '''Gateway''' | + | |
| | | | ||
* Voice connectivity between IP network and public carrier network | * Voice connectivity between IP network and public carrier network | ||
| Line 43: | Line 37: | ||
|} | |} | ||
<br style="clear:both;"/> | <br style="clear:both;"/> | ||
| - | |||
===VoIP Protocols=== | ===VoIP Protocols=== | ||
| - | Voice is connection oriented, hence communication between two parties must be set up first. Two of the most common protocols used are H.323 and Session Initiation Protocol (SIP). | + | Voice is connection oriented, hence communication between two parties must be set up first. Two of the most common protocols used are H.323 and Session Initiation Protocol (SIP). Here is a very brief overview of the two protocols.[6] |
====H.323==== | ====H.323==== | ||
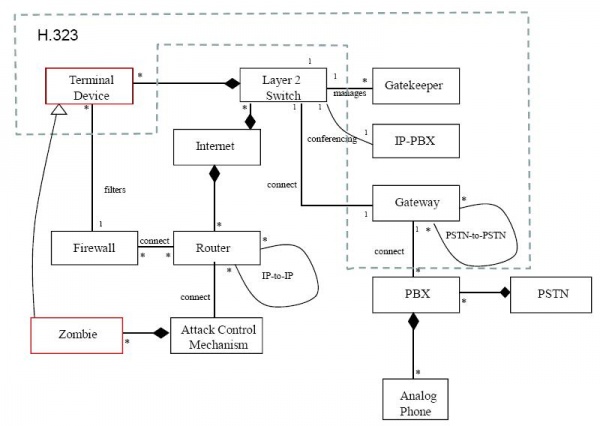
| - | H.323 is a standard to promote compatibility in video conference transmissions over IP networks. | + | H.323 is a standard to promote compatibility in video conference transmissions over IP networks.[8] |
H.323 has four main components: | H.323 has four main components: | ||
| Line 58: | Line 51: | ||
====Session Initiation Protocol==== | ====Session Initiation Protocol==== | ||
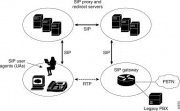
[[Image:SIP.JPG|right|thumb|Source:http://www.cisco.com/univercd/cc/td/doc/product/voice/sipsols/biggulp/bgsipov.htm]] | [[Image:SIP.JPG|right|thumb|Source:http://www.cisco.com/univercd/cc/td/doc/product/voice/sipsols/biggulp/bgsipov.htm]] | ||
| - | SIP is a peer-to-peer standard protocol for multimedia conferencing over IP. SIP exists on the application layer used to initiate, maintain, as well as terminate a call. SIP contains 3 components: | + | SIP is a peer-to-peer standard protocol for multimedia conferencing over IP. SIP exists on the application layer used to initiate, maintain, as well as terminate a call. SIP contains 3 components: [5,8] |
# User agent client or user agent server | # User agent client or user agent server | ||
# Proxy server | # Proxy server | ||
| Line 65: | Line 58: | ||
<br style="clear:both;"/> | <br style="clear:both;"/> | ||
==Attacks== | ==Attacks== | ||
| - | There are three main types of attacks that the VoIP environment are susceptible to including eavesdropping, theft of services, and denial of service attacks. | + | There are three main types of attacks that the VoIP environment are susceptible to including eavesdropping, theft of services, and denial of service attacks.[7] |
===Eavesdropping=== | ===Eavesdropping=== | ||
| - | Eavesdropping on VoIP calls involves third parties monitoring the call signal packets in which the hacker may learn of confidential information such as name, passwords, and other personal information. This is especially significant to businesses as corporate sensitive information may be revealed. | + | Eavesdropping on VoIP calls involves third parties monitoring the call signal packets in which the hacker may learn of confidential information such as name, passwords, and other personal information. This is especially significant to businesses as corporate sensitive information may be revealed.[6] |
VoIP eavesdropping is easier accomplished that eavesdropping the traditional telephone line through physical wiretap since the hacker must physically place the wiretap. Since VoIP calls send data across the network, the hacker can sniff for packets anywhere along the network. | VoIP eavesdropping is easier accomplished that eavesdropping the traditional telephone line through physical wiretap since the hacker must physically place the wiretap. Since VoIP calls send data across the network, the hacker can sniff for packets anywhere along the network. | ||
| Line 79: | Line 72: | ||
A typical eavesdropper would: | A typical eavesdropper would: | ||
# Perform a side channel attack based on the fact all IP Telephony implementations use Real Time Protocol(RTP) to transfer packets. | # Perform a side channel attack based on the fact all IP Telephony implementations use Real Time Protocol(RTP) to transfer packets. | ||
| - | # Download, install, and run Fireberd DNA-323 to capture and replay voice packets. | + | # Download, install, and run Fireberd DNA-323 to capture and replay voice packets.[6] |
# Connect to the IP network the VoIP conversation is taking place on. | # Connect to the IP network the VoIP conversation is taking place on. | ||
====Data Encryption==== | ====Data Encryption==== | ||
| - | The most effective countermeasure to eavesdropping is data encryption. As seen in class, there are many data encryption methods, some more effective than others. However, all methods introduce overhead which can greatly effect the quality of the conversation by causing large packet loss and packet jitter. Here are some common ways of implementing data encryption for VoIP: | + | The most effective countermeasure to eavesdropping is data encryption. As seen in class, there are many data encryption methods, some more effective than others. However, all methods introduce overhead which can greatly effect the quality of the conversation by causing large packet loss and packet jitter. Here are some common ways of implementing data encryption for VoIP: [2,3] |
* Using software such as [http://zfoneproject.com/ Zfone] | * Using software such as [http://zfoneproject.com/ Zfone] | ||
| Line 93: | Line 86: | ||
* Using a Virtual Private Network (VPN) | * Using a Virtual Private Network (VPN) | ||
===Theft of Services=== | ===Theft of Services=== | ||
| - | One of the great things about VoIP is the fact that you can take it anywhere in the world that has internet access and use it. Unfortunately, this also benefits the hacker so that he or she may steal access to your VoIP services and then possibly do criminal activities with them. Also known as VoIP "phreaking", the hacker can steal your VoIP services through two common ways: | + | One of the great things about VoIP is the fact that you can take it anywhere in the world that has internet access and use it. Unfortunately, this also benefits the hacker so that he or she may steal access to your VoIP services and then possibly do criminal activities with them. Also known as VoIP "phreaking", the hacker can steal your VoIP services through two common ways:[7] |
* '''Spoofing''' | * '''Spoofing''' | ||
** Accomplished through changing the header data in the voice packet so it looks like it comes from a different source | ** Accomplished through changing the header data in the voice packet so it looks like it comes from a different source | ||
| Line 101: | Line 94: | ||
====Authentication==== | ====Authentication==== | ||
| - | The most effective countermeasure to theft of VoIP services involves implementing authentication. | + | The most effective countermeasure to theft of VoIP services involves implementing authentication. Fortunately, VoIP protocols include some form of authentication. Specifically, the H.235 component of H.323 facilitates 3 types of authentication: [4] |
# Symmetric encryption | # Symmetric encryption | ||
# Subscription based | # Subscription based | ||
# IPSEC | # IPSEC | ||
Subscription based is much more CPU intensive than symmetric encryption and requires the sharing of a secret key before communication can begin. Alternatively, H.235 may allow IPSEC to handle the authentication. | Subscription based is much more CPU intensive than symmetric encryption and requires the sharing of a secret key before communication can begin. Alternatively, H.235 may allow IPSEC to handle the authentication. | ||
| - | SIP also provides 3 different types of authentication: | + | SIP also provides 3 different types of authentication:[8] |
# Basic authentication | # Basic authentication | ||
# Digest authentication | # Digest authentication | ||
| Line 118: | Line 111: | ||
===Denial of Services=== | ===Denial of Services=== | ||
| + | |||
| + | {|align="right" | ||
| + | |[[image:DoS.JPG|right|thumb|600px|Source:http://www.hillside.net/plop/2007/papers/PLoP2007_PelaezEtAl.pdf]] | ||
| + | |} | ||
| + | |||
There are two main types of denial of services attacks in the VoIP environment including: | There are two main types of denial of services attacks in the VoIP environment including: | ||
# Exploiting software bugs to bring down servers | # Exploiting software bugs to bring down servers | ||
# Distributed bandwidth attack | # Distributed bandwidth attack | ||
| - | Before a DoS attack can take place, the hacker must first use a sniffing program to look for vulnerable hosts. As discussed in class, a port scanner is useful to identify those hosts. In a distributed DoS (DDoS) attack, once the vulnerable host is found, a program sometimes called a bot is installed on the computer and awaits for instructions. The | + | Before a DoS attack can take place, the hacker must first use a sniffing program to look for vulnerable hosts. As discussed in class, a port scanner is useful to identify those hosts. In a distributed DoS (DDoS) attack, once the vulnerable host is found, a program sometimes called a bot is installed on the computer and awaits for instructions. The infected computers, sometimes called zombies as in the image to the right, can then be coordinated to bombard a target with traffic effectively disabling it.[7,10] |
====Packet Filtering==== | ====Packet Filtering==== | ||
| - | Denial of service attacks are hard to defend against because of the nature of the attack; The attack is hard to distinguish from normal traffic. The method to defend against DoS attacks used today is mainly packet filtering. The packet filter must look for suspicious packets and block them before reaching the target. There is still a great amount of work that can be done in this area. | + | Denial of service attacks are hard to defend against because of the nature of the attack; The attack is hard to distinguish from normal traffic. The method to defend against DoS attacks used today is mainly packet filtering and/or firewalls. The packet filter must look for suspicious packets and block them before reaching the target. There is still a great amount of work that can be done in this area. |
| + | <br style="clear:both;"/> | ||
| + | ===Summary=== | ||
| + | {| border="1" align="right" | ||
| + | | | ||
| + | {| border="5" cellspacing="5" cellpadding="2" align="right" | ||
| + | |+ '''VoIP Security Vulnerabilities''' | ||
| + | ! Threat!! Countermeasures | ||
| + | |- | ||
| + | | | ||
| + | '''Eavesdropping''' | ||
| + | | | ||
| + | Data Encryption | ||
| + | |- | ||
| + | | | ||
| + | '''Theft of services''' | ||
| + | | | ||
| + | Authentication | ||
| + | |- | ||
| + | | | ||
| + | '''Denial of Services''' | ||
| + | | | ||
| + | Packet Filtering | ||
| + | |} | ||
| + | |- | ||
| + | | align="center"|A short summary | ||
| + | |} | ||
| + | Although there is more than way one to defend against a certain kind of attack, the most common countermeasures to the attacks listed in this wiki are summarized in the table to the right. | ||
| + | <br style="clear:both;"/> | ||
==Recommendations== | ==Recommendations== | ||
| - | Although a network cannot be completely immune to attack, here are some recommendations to secure your VoIP network. | + | Although a network cannot be completely immune to attack, here are some recommendations to secure your VoIP network. [8] |
# Do not user shared media devices (ie hubs) on networks | # Do not user shared media devices (ie hubs) on networks | ||
| Line 137: | Line 163: | ||
==References== | ==References== | ||
| - | # http://www.eetimes.com/showArticle.jhtml;jsessionid=ERU1FKTFCHUJUQSNDLPCKH0CJUNN2JVN?articleID=16505939 | + | # Jaikumar Vijayan. "VOIP: Don't overlook security". Retrieved on 2008-04-08. [http://www.computerworld.com/securitytopics/security/story/0,10801,74840,00.html] |
| + | # Bruce Schneier. "VOIP Encryption". Retrieved on 2008-04-12. [http://www.schneier.com/blog/archives/2006/04/voip_encryption.html] | ||
| + | # "How to: Encrypt Your VoIP". Retrieved on 2008-04-11. [http://www.voipnow.org/2007/04/how_to_encrypt_.html] | ||
| + | # "VoIP Authentication (UNI-OSP) Feature". Retrieved on 2008-04-12. [http://www.cisco.ws/en/US/docs/ios/12_1t/12_1t2/feature/guide/uni_osp.html] | ||
| + | # "Overview of the Session Initiation Protocol". Retrieved on 2008-04-12. [http://www.cisco.com/univercd/cc/td/doc/product/voice/sipsols/biggulp/bgsipov.htm] | ||
| + | # Tom Long. "Eavesdropping an IP Telephony Call". Retrieved on 2008-04-09. [http://www.sans.org/reading_room/whitepapers/telephone/318.php] | ||
| + | # Philip Bednarz. "How VoIP is changing the network security equation". Retrieved on 2008-04-09. [http://www.eetimes.com/showArticle.jhtml;jsessionid=ERU1FKTFCHUJUQSNDLPCKH0CJUNN2JVN?articleID=16505939] | ||
| + | # Eric Weiss. "Security Concerns with VOIP". Retrieved on 2008-04-09. [http://www.sans.org/reading_room/whitepapers/voip/323.php] | ||
| + | # Peter Thermos. "Two attacks against VoIP". Rerieved on 2008-04-09. [http://www.securityfocus.com/infocus/1862] | ||
| + | # Juan C. Pelaez, Eduardo B. Fernandez, Maria M. Larrondo-Petrie, Christian Wieser. "Attack Patterns in VoIP". Retrieved on 2008-04-12. [http://www.hillside.net/plop/2007/papers/PLoP2007_PelaezEtAl.pdf] | ||
==See Also== | ==See Also== | ||
| + | [[Two-factor Authentication]]<BR> | ||
| + | [[Public Key Encryption Algorithms]]<BR> | ||
| + | [[Peer to Peer Network Security]]<BR> | ||
| + | [[Streaming Media Technology]]<BR> | ||
| + | [[Secure Electronic Transaction (SET) Protocol]]<BR> | ||
==External Links== | ==External Links== | ||
| + | * [http://en.wikipedia.org/wiki/Session_Initiation_Protocol Session Initiation Protocol] | ||
| + | * [http://en.wikipedia.org/wiki/H.323 H.323] | ||
| + | * [http://en.wikipedia.org/wiki/VoIP VoIP] | ||
| - | --[[User:Chenc8|Chenc8]] | + | --[[User:Chenc8|Chenc8]] 23:07, 13 April 2008 (EDT) |
Current revision as of 03:07, 14 April 2008
VoIP (Voice over Internet Protocol) is a protocol used for the transmission of voice data across the Internet. IP telephony treats voice as another form of data that is compressed and optimized for network traffic and is vulnerable to attacks traditional data would be on the network. VoIP security is akin to network security; voice data traveling the network will look like any other normal data.
Corporations generally place VoIP concerns on the voice quality, latency, and quality of service above the overall security when VoIP telephony is actually more vulnerable to certain attacks compared to the traditional phone system.[1] The most common threats found in the VoIP environment include eavesdropping, theft of services, and denial of service attacks.[7]
Contents |
Introduction
To greater understand VoIP security, a general overview of VoIP systems is useful.
Components
A typical VoIP system includes four components[6]:
| Data Network |
|
| IP Handset |
|
| Call Server |
|
| Gateway |
|
VoIP Protocols
Voice is connection oriented, hence communication between two parties must be set up first. Two of the most common protocols used are H.323 and Session Initiation Protocol (SIP). Here is a very brief overview of the two protocols.[6]
H.323
H.323 is a standard to promote compatibility in video conference transmissions over IP networks.[8]
H.323 has four main components:
- Terminal
- Gateway
- Multipoint Control Unit (MCU)
- Gatekeeper
Session Initiation Protocol
SIP is a peer-to-peer standard protocol for multimedia conferencing over IP. SIP exists on the application layer used to initiate, maintain, as well as terminate a call. SIP contains 3 components: [5,8]
- User agent client or user agent server
- Proxy server
- Redirect server
Attacks
There are three main types of attacks that the VoIP environment are susceptible to including eavesdropping, theft of services, and denial of service attacks.[7]
Eavesdropping
Eavesdropping on VoIP calls involves third parties monitoring the call signal packets in which the hacker may learn of confidential information such as name, passwords, and other personal information. This is especially significant to businesses as corporate sensitive information may be revealed.[6]
VoIP eavesdropping is easier accomplished that eavesdropping the traditional telephone line through physical wiretap since the hacker must physically place the wiretap. Since VoIP calls send data across the network, the hacker can sniff for packets anywhere along the network.
To eavesdrop a call there are 3 simple steps:
- Understanding how IP Telephony works.
- Obtain tools.
- Connect the tools into the IP network.
A typical eavesdropper would:
- Perform a side channel attack based on the fact all IP Telephony implementations use Real Time Protocol(RTP) to transfer packets.
- Download, install, and run Fireberd DNA-323 to capture and replay voice packets.[6]
- Connect to the IP network the VoIP conversation is taking place on.
Data Encryption
The most effective countermeasure to eavesdropping is data encryption. As seen in class, there are many data encryption methods, some more effective than others. However, all methods introduce overhead which can greatly effect the quality of the conversation by causing large packet loss and packet jitter. Here are some common ways of implementing data encryption for VoIP: [2,3]
- Using software such as Zfone
- Using VoIP clients with built in encryption such as Skype
Skype comes with its own propriety encryption method. Some other common methods include: Data Encryption Standard(DES), Triple DES (3DES), Advanced Encryption Standard (AES)
- Using a Virtual Private Network (VPN)
Theft of Services
One of the great things about VoIP is the fact that you can take it anywhere in the world that has internet access and use it. Unfortunately, this also benefits the hacker so that he or she may steal access to your VoIP services and then possibly do criminal activities with them. Also known as VoIP "phreaking", the hacker can steal your VoIP services through two common ways:[7]
- Spoofing
- Accomplished through changing the header data in the voice packet so it looks like it comes from a different source
- Hacking into SIP changing SIP registrar information
- Man in the middle attack (MITM).
- Accomplished through monitoring traffic, recording it and/or changing it
Authentication
The most effective countermeasure to theft of VoIP services involves implementing authentication. Fortunately, VoIP protocols include some form of authentication. Specifically, the H.235 component of H.323 facilitates 3 types of authentication: [4]
- Symmetric encryption
- Subscription based
- IPSEC
Subscription based is much more CPU intensive than symmetric encryption and requires the sharing of a secret key before communication can begin. Alternatively, H.235 may allow IPSEC to handle the authentication. SIP also provides 3 different types of authentication:[8]
- Basic authentication
- Digest authentication
- PGP authentication
However, all three are challenge-response based.
Other authentication methods include but not limited to:
- Public key authentication with certification
- Diffie-Hellman key exchange
- UNI-OSP from Cisco
Denial of Services
There are two main types of denial of services attacks in the VoIP environment including:
- Exploiting software bugs to bring down servers
- Distributed bandwidth attack
Before a DoS attack can take place, the hacker must first use a sniffing program to look for vulnerable hosts. As discussed in class, a port scanner is useful to identify those hosts. In a distributed DoS (DDoS) attack, once the vulnerable host is found, a program sometimes called a bot is installed on the computer and awaits for instructions. The infected computers, sometimes called zombies as in the image to the right, can then be coordinated to bombard a target with traffic effectively disabling it.[7,10]
Packet Filtering
Denial of service attacks are hard to defend against because of the nature of the attack; The attack is hard to distinguish from normal traffic. The method to defend against DoS attacks used today is mainly packet filtering and/or firewalls. The packet filter must look for suspicious packets and block them before reaching the target. There is still a great amount of work that can be done in this area.
Summary
| ||||||||
| A short summary |
Although there is more than way one to defend against a certain kind of attack, the most common countermeasures to the attacks listed in this wiki are summarized in the table to the right.
Recommendations
Although a network cannot be completely immune to attack, here are some recommendations to secure your VoIP network. [8]
- Do not user shared media devices (ie hubs) on networks
- All VoIP traffic should be encrypted
- VoIP servers with confidential information should be treated as a confidential database
- Build redundancy into VoIP network.
- Make sure firewall is VoIP aware
References
- Jaikumar Vijayan. "VOIP: Don't overlook security". Retrieved on 2008-04-08. [1]
- Bruce Schneier. "VOIP Encryption". Retrieved on 2008-04-12. [2]
- "How to: Encrypt Your VoIP". Retrieved on 2008-04-11. [3]
- "VoIP Authentication (UNI-OSP) Feature". Retrieved on 2008-04-12. [4]
- "Overview of the Session Initiation Protocol". Retrieved on 2008-04-12. [5]
- Tom Long. "Eavesdropping an IP Telephony Call". Retrieved on 2008-04-09. [6]
- Philip Bednarz. "How VoIP is changing the network security equation". Retrieved on 2008-04-09. [7]
- Eric Weiss. "Security Concerns with VOIP". Retrieved on 2008-04-09. [8]
- Peter Thermos. "Two attacks against VoIP". Rerieved on 2008-04-09. [9]
- Juan C. Pelaez, Eduardo B. Fernandez, Maria M. Larrondo-Petrie, Christian Wieser. "Attack Patterns in VoIP". Retrieved on 2008-04-12. [10]
See Also
Two-factor Authentication
Public Key Encryption Algorithms
Peer to Peer Network Security
Streaming Media Technology
Secure Electronic Transaction (SET) Protocol
External Links
--Chenc8 23:07, 13 April 2008 (EDT)