Tools for conducting denial-of-service attacks
From Computing and Software Wiki
(New page: In the world of computer network security, denial-of-service attack is a sneaky and furious monster. It is calm and quite. But when it attacks you, your system will be defeated within minu...) |
|||
| Line 23: | Line 23: | ||
* SYN floods | * SYN floods | ||
==Tools for conducting DoS attacks== | ==Tools for conducting DoS attacks== | ||
| + | |||
===SSPing=== | ===SSPing=== | ||
| + | [[Image:SmurfAttack.gif|thumb|right|100px|Smurf]] | ||
| + | [[Image:SYN_flood.jpg|thumb|right|100px|SYN Flood]] | ||
SSPing, a DoS tool, is a program sends the victim's computer a series of highly fragmented, oversized ICMP data packets. While trying to put the fragments together, the computer can get into a memory overflow which causes the machine to freeze. SSPing affects Windows 95/NT and Mac OS. | SSPing, a DoS tool, is a program sends the victim's computer a series of highly fragmented, oversized ICMP data packets. While trying to put the fragments together, the computer can get into a memory overflow which causes the machine to freeze. SSPing affects Windows 95/NT and Mac OS. | ||
| Line 31: | Line 34: | ||
This trick works for Windows 95 and Windows NT. The computer which is running one of these operating systems will operate slowly and sometimes hang. | This trick works for Windows 95 and Windows NT. The computer which is running one of these operating systems will operate slowly and sometimes hang. | ||
===Smurf=== | ===Smurf=== | ||
| - | |||
| - | |||
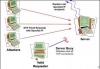
Smurf is a simple effective DoS attack involving forged ICMP packets sent to a broadcast address. Attackers spoof the source address on ICMP echo requests and sending them to an IP broadcast address. This causes every machine on the broadcast network to receive the reply and respond back to the source address that was forged by the attacker. This attack results in DoS due to high network traffic which not only hurts the victim but the broadcase network also. | Smurf is a simple effective DoS attack involving forged ICMP packets sent to a broadcast address. Attackers spoof the source address on ICMP echo requests and sending them to an IP broadcast address. This causes every machine on the broadcast network to receive the reply and respond back to the source address that was forged by the attacker. This attack results in DoS due to high network traffic which not only hurts the victim but the broadcase network also. | ||
There is a similar tool called Fraggle which uses UDP packets instead. | There is a similar tool called Fraggle which uses UDP packets instead. | ||
| Line 38: | Line 39: | ||
With a series of SYN packets, the attacker can drain the victim resources which leads to rejecting legitimate requests. | With a series of SYN packets, the attacker can drain the victim resources which leads to rejecting legitimate requests. | ||
System A sends a SYN packet to system B asking to establish a connection via three-way handshake. However the source address of the packet is spoofed thus misleads system B to switch to SYN_RECV state and send an SYN/ACK packet to the spoofed address. These connections are called half-open connections. The source address does not exist and system B can only flush the potential connection once the connection-establishment timer expires. This timer varies from system to system ranging from seconds to minutes. This type of attack is very dangerous because with little resources (e.g. bandwidth), the attacker can take down an industrial strength web server. Moreover, this is a stealth attack since everything (e.g. the packet) look so normal. Today, SYN flood is the primary capacity depletion mechanism for denial of service attacks. | System A sends a SYN packet to system B asking to establish a connection via three-way handshake. However the source address of the packet is spoofed thus misleads system B to switch to SYN_RECV state and send an SYN/ACK packet to the spoofed address. These connections are called half-open connections. The source address does not exist and system B can only flush the potential connection once the connection-establishment timer expires. This timer varies from system to system ranging from seconds to minutes. This type of attack is very dangerous because with little resources (e.g. bandwidth), the attacker can take down an industrial strength web server. Moreover, this is a stealth attack since everything (e.g. the packet) look so normal. Today, SYN flood is the primary capacity depletion mechanism for denial of service attacks. | ||
| + | ==Conclusion== | ||
| + | |||
| + | ==References== | ||
| + | |||
| + | ==See also== | ||
| + | |||
| + | ==External links== | ||
[[User:Luongqt|Luongqt]] | [[User:Luongqt|Luongqt]] | ||
Revision as of 20:19, 8 April 2009
In the world of computer network security, denial-of-service attack is a sneaky and furious monster. It is calm and quite. But when it attacks you, your system will be defeated within minutes (sometimes seconds). What is it? Where does it come from? What can it do? How can you conduct it? Conduct with what? Software or hardware?
Nowadays there are tools available on the Internet that allow any average user to conduct a denial-of-service attack to any vulnerable servers. They are created by black hat hackers for different reasons varying from personal, political reasons to nastiness. Damages from a DoS attack are usually devastating to businesses such as search engines, email providers, banks, e-commerce sites that rely heavily on availability.
On the other hand, although details of denial-of-service attacks are well-known and studied, it is quite difficult to protect any systems from it due to the very nature of the attacks. Scanning tools and other intrusion detection systems can be used to detect attacks or find vulnerable spots which can lead to an DoS attack.
Contents |
Definition
Denial-of-service (DoS) attack is an attempt to violate the availability condition of network security. Its sole purpose is to shut a computer system down or drain all its available resources, which prevents it to serve legitimate users.
As computer becomes more and more popular, DoS attack evolves to Distributed DoS (DDoS) attack which amplifies the damage from thousand to million times.
Fact
On February 6th, 2000, Yahoo portal was shut down for 3 hours. Then retailer Buy.com Inc. (BUYX) was hit the next day, hours after going public. By that evening, eBay (EBAY), Amazon.com (AMZN), and CNN (TWX) had gone dark. And in the morning, the mayhem continued with online broker E*Trade (EGRP) and others having traffic to their sites virtually choked off. (Business Week Online, 12 February 2000)
Types of attack
There are many ways to conduct a DoS attack. Some of them are
- Sending oversized packets
- fragmentation overlap
- loopback floods
- Application DoS
- UDP floods
- SYN floods
Tools for conducting DoS attacks
SSPing
SSPing, a DoS tool, is a program sends the victim's computer a series of highly fragmented, oversized ICMP data packets. While trying to put the fragments together, the computer can get into a memory overflow which causes the machine to freeze. SSPing affects Windows 95/NT and Mac OS.
Jolt is a program known for this kind of attack. It will freeze un-patched Windows 95, NT machines by sending a series of spoofed & highly fragmented ICMP packets to the target, which then tries to reassemble the received fragments.
Land Exploit
Land Exploit is a DoS attack in which a program sends a TCP SYN packet where the target and source addresses are the same and port numbers are the same. This trick works for Windows 95 and Windows NT. The computer which is running one of these operating systems will operate slowly and sometimes hang.
Smurf
Smurf is a simple effective DoS attack involving forged ICMP packets sent to a broadcast address. Attackers spoof the source address on ICMP echo requests and sending them to an IP broadcast address. This causes every machine on the broadcast network to receive the reply and respond back to the source address that was forged by the attacker. This attack results in DoS due to high network traffic which not only hurts the victim but the broadcase network also. There is a similar tool called Fraggle which uses UDP packets instead.
SYN Flood
With a series of SYN packets, the attacker can drain the victim resources which leads to rejecting legitimate requests. System A sends a SYN packet to system B asking to establish a connection via three-way handshake. However the source address of the packet is spoofed thus misleads system B to switch to SYN_RECV state and send an SYN/ACK packet to the spoofed address. These connections are called half-open connections. The source address does not exist and system B can only flush the potential connection once the connection-establishment timer expires. This timer varies from system to system ranging from seconds to minutes. This type of attack is very dangerous because with little resources (e.g. bandwidth), the attacker can take down an industrial strength web server. Moreover, this is a stealth attack since everything (e.g. the packet) look so normal. Today, SYN flood is the primary capacity depletion mechanism for denial of service attacks.