The X Windowing System
From Computing and Software Wiki
(→Communication Security and Tunneling Through SSH) |
|||
| (11 intermediate revisions not shown) | |||
| Line 19: | Line 19: | ||
* There is one last message which is sent between X clients and X hosts. If there is any error on the X host, there needs to be a way for the host to tell the client that the error occurred. This is taken care of by the error response message. This message is the same size as a normal event response message, but is sent to the error handling routine of the X client. | * There is one last message which is sent between X clients and X hosts. If there is any error on the X host, there needs to be a way for the host to tell the client that the error occurred. This is taken care of by the error response message. This message is the same size as a normal event response message, but is sent to the error handling routine of the X client. | ||
| - | |||
| - | |||
| - | |||
=Security= | =Security= | ||
There are several ways in which security is a major concern when using the X Windowing system. These can concerns can be broken up into two major categories: interception of communications between the X client and X host, and having a malignant client connect to your host. The communication security can be handled by tunneling the communication between the X host and X client through a more secure protocol such as ssh. The malignant client concern can be handled by using tools distributed with the X Windowing system: XAuth and XHosts. | There are several ways in which security is a major concern when using the X Windowing system. These can concerns can be broken up into two major categories: interception of communications between the X client and X host, and having a malignant client connect to your host. The communication security can be handled by tunneling the communication between the X host and X client through a more secure protocol such as ssh. The malignant client concern can be handled by using tools distributed with the X Windowing system: XAuth and XHosts. | ||
==Communication Security and Tunneling Through SSH== | ==Communication Security and Tunneling Through SSH== | ||
| - | + | Depending on how an X Client connects to an X Host, there can be some major security issues. When used by itself through a non-secure connection, the X Windowing system will send all of it's data unencrypted across the network you are using. Depending how many people have access to the network, this can be a huge security issue. Everything from passwords to possibly confidential documents are sent essentially unencrypted across the network which allows anyone to view them. | |
| - | < | + | <BR> One possible solution to this problem is to tunnel through a more secure communication medium, such as ssh. By embedding X Window messages in SSH datagrams, the X Window messages will then be encrypted within the SSH message. To see more on tunneling, please see one of the following articles: [[Applications_of_SSH#SSH_Tunneling | Applications of SSH]], [[SSH Tunneling]] |
==XAuth== | ==XAuth== | ||
| + | One utility to help with security which comes with the X Windowing system is xauth. This tool operates works with MIT Magic Cookies. The way it works is when you start up an X Windowing host, it will create a Magic Cookie which is just a hexidecimal string. This cookie is stored in the file $HOME/.Xauthority of the client machine. This file contains a list of hosts, displays and magic cookies. When the client connects to the host on a specific display, it sends the corresponding Magic Cookie. If the Magic Cookie matches the host's cookie, then the host accepts the connection. | ||
==XHosts== | ==XHosts== | ||
| + | Another utility to help with security of the X Windowing system is the xhost tool. This tool operates in two modes called plus(+) and minus (-). Plus mode will allow any X Client to connect to the X Host. Obviously this is a very insecure mode. A more secure mode is the minus mode. Using this mode, only hosts on the trusted list are allowed to connect. Hosts can be added and removed from the trusted list through xauth +/-<host name>. | ||
= References = | = References = | ||
# [http://www.javvin.com/protocolXWindow.html http://www.javvin.com/protocolXWindow.html] | # [http://www.javvin.com/protocolXWindow.html http://www.javvin.com/protocolXWindow.html] | ||
| + | # [http://www.xfree86.org/4.4.0/xauth.1.html http://www.xfree86.org/4.4.0/xauth.1.html] | ||
| + | # [http://www.xfree86.org/current/xhost.1.html http://www.xfree86.org/current/xhost.1.html] | ||
| + | # [http://ptolemy.eecs.berkeley.edu/~cxh/sapub/Xsecurity.html http://ptolemy.eecs.berkeley.edu/~cxh/sapub/Xsecurity.html] | ||
| + | # [http://www.xfree86.org/current/Xsecurity.7.html http://www.xfree86.org/current/Xsecurity.7.html] | ||
=External Links= | =External Links= | ||
| - | * | + | * [http://www.xfree86.org/ http://www.xfree86.org/] |
| + | * [http://www.x.org/wiki/ http://www.x.org/wiki/] | ||
= See Also = | = See Also = | ||
Current revision as of 02:52, 14 April 2008
The X Windowing System’s main purpose is to provide an interface between a client application (such as a desktop environment), which can take advantage of the client CPU’s power, and a host, which takes advantage of the host’s native system’s display hardware. It provides basic functionality like… in a standardized API which allows developers to relatively easily create GUI applications. In short, the X Windowing System will run all the logic behind an application on one client machine while displaying the results on and poling for input from another host machine. This leads to some major security concerns about the communications between the client and host themselves and also how to run an X Windowing host in such a way that does not open a huge security hole in your system. Today, the client machine can be, and often is, the same machine as the host machine. However, the focus of this article will be on the networking side of the X Windowing System.
Contents |
What is the X Windowing System?
The X Windowing system is a windowing system which has been around since the mid-80’s. Being designed mainly for a UNIX environment, the X Windowing System lends itself to work in a client/server environment. This means that applications themselves may reside on a foreign host machine while the display is being taken care of by a local client. When X was first developed, CPU power was expensive. It was a lot more common for people to be working at client terminals logged into a powerful host where they did their work. X allowed them to run a GUI on their local machine while still taking advantage of the processing power of the server machine. This meant that the server could “focus” on processing while their local machines would take care of the graphical part of the application.
Definitions
- Host: The machine which is displaying the X Windowing application. The host must be listening for client X Windowing application requests.
- Client: The machine which is running the logic of the X Windowing application. The client must send a request to the host in order to display an X Windowing application on it.
Client Server Relationship
Communication Protocols
The basic idea behind the communication protocols between clients running the logic of the application and hosts displaying the application is to provide a way for the client to send information about what needs to be displayed on the host to the host while the host will send any input from the user, such as mouse clicks and keyboard strokes, back to the client for the client to interpret.
Basic Protocols
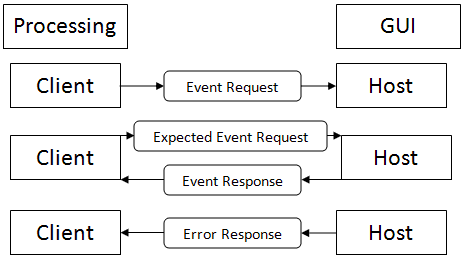
- The X client makes a request, which is 4 bytes long, for a certain event to happen on the host. This event can be anything from creating a window to changing what’s being displayed in a window to closing the window. In order to make this process more efficient, there is no response sent from the host to the client saying that the request has been successfully executed. It is left to the network layer, which can be unreliable, and is assumed to get the packets to the host. Some updates will not make it from the client to the host and hence there can be some strange screen artifacts which occur as some requests are processed and others aren’t.
- There are some requests for which the X host must respond to the client, also in multiples of 4 bytes, with information. When an expected event occurs, such as a mouse click or key stroke, the X host must send information about that event back to the client. Again, in order to keep network traffic to a minimum, the X host will only send information back to the client about expected events. However, the expected event which occurred may have been on a different part of the X Windowing hosts screen. This can lead to some major security breaches which the user of the X Windowing system could be unaware of. For example, if the user is expected to enter a password in one application that’s running on the user’s host, the keystrokes of that password could be “intercepted” by another application running on the host which would then be sent back to whatever client machine is running the other application.
- There is one last message which is sent between X clients and X hosts. If there is any error on the X host, there needs to be a way for the host to tell the client that the error occurred. This is taken care of by the error response message. This message is the same size as a normal event response message, but is sent to the error handling routine of the X client.
Security
There are several ways in which security is a major concern when using the X Windowing system. These can concerns can be broken up into two major categories: interception of communications between the X client and X host, and having a malignant client connect to your host. The communication security can be handled by tunneling the communication between the X host and X client through a more secure protocol such as ssh. The malignant client concern can be handled by using tools distributed with the X Windowing system: XAuth and XHosts.
Communication Security and Tunneling Through SSH
Depending on how an X Client connects to an X Host, there can be some major security issues. When used by itself through a non-secure connection, the X Windowing system will send all of it's data unencrypted across the network you are using. Depending how many people have access to the network, this can be a huge security issue. Everything from passwords to possibly confidential documents are sent essentially unencrypted across the network which allows anyone to view them.
One possible solution to this problem is to tunnel through a more secure communication medium, such as ssh. By embedding X Window messages in SSH datagrams, the X Window messages will then be encrypted within the SSH message. To see more on tunneling, please see one of the following articles: Applications of SSH, SSH Tunneling
XAuth
One utility to help with security which comes with the X Windowing system is xauth. This tool operates works with MIT Magic Cookies. The way it works is when you start up an X Windowing host, it will create a Magic Cookie which is just a hexidecimal string. This cookie is stored in the file $HOME/.Xauthority of the client machine. This file contains a list of hosts, displays and magic cookies. When the client connects to the host on a specific display, it sends the corresponding Magic Cookie. If the Magic Cookie matches the host's cookie, then the host accepts the connection.
XHosts
Another utility to help with security of the X Windowing system is the xhost tool. This tool operates in two modes called plus(+) and minus (-). Plus mode will allow any X Client to connect to the X Host. Obviously this is a very insecure mode. A more secure mode is the minus mode. Using this mode, only hosts on the trusted list are allowed to connect. Hosts can be added and removed from the trusted list through xauth +/-<host name>.
References
- http://www.javvin.com/protocolXWindow.html
- http://www.xfree86.org/4.4.0/xauth.1.html
- http://www.xfree86.org/current/xhost.1.html
- http://ptolemy.eecs.berkeley.edu/~cxh/sapub/Xsecurity.html
- http://www.xfree86.org/current/Xsecurity.7.html
External Links
See Also
Manselnj 18:47, 13 April 2008 (EDT)