The Mitnick attack
From Computing and Software Wiki
| (20 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
| + | Computer security is an important factor in our information world with Internet and digitally owned materials. Over the past twenty years, network security has evolved continuously. More secure implementations are invented to replace old less secure implementations. Kevin Mitnick was able to hack into Tsutomu Shimomura's X-Terminal computer due to early implementation of [http://en.wikipedia.org/wiki/Transmission_Control_Protocol TCP] connection, which was not really secure at that time. With a huge desire of curiosity, Mitnick did something that no one has ever done before him. He exploited the trusted relationship between two computers by performing man-in-the-middle attack under a spoofed identity. His attack made him the most famous [http://en.wikipedia.org/wiki/Hacker hacker] in [http://en.wikipedia.org/wiki/United_States United States of America]. | ||
| + | [[Image:Kevin mitnick FBI.gif|thumb|right|250px|Mitnick on FBI wanted list]] | ||
== Who is Mitnick? == | == Who is Mitnick? == | ||
| - | [http://en.wikipedia.org/wiki/Mitnick Kevin Mitnick](born October 6, 1963) is known as "the most famous" hacker in | + | [[Image:kevinmitnick.jpg|thumb|right|170px|Kevin Mitnick]] |
| - | + | [[Image:Shimomura.jpg|thumb|right|170px|Tsutomu Shimomura]] | |
| - | + | [http://en.wikipedia.org/wiki/Mitnick Kevin Mitnick](born October 6, 1963) is known as "the most famous" hacker in United States of America. He is an expert in [[social engineering]], which helped him to obtain many classified information used for his hacking hobby. In his early age, he was on the [http://en.wikipedia.org/wiki/Fbi FBI] most wanted cyber criminal list. He was captured by the FBI with the aid of [http://en.wikipedia.org/wiki/Tsutomu Tsutomu] and sentenced 5 years in prison. Now he is a security consultant in his own firm [http://www.mitnicksecurity.com/index.php Mitnick Security Consulting]. | |
| - | == | + | ==Three-way handshake== |
| - | + | If there is a trusted relationship between two computers (e.g. server and client), a connection can be established by a [http://www.pccitizen.com/threewayhandshake.htm three-way handshake]. In the Mitnick attack, the three-way handshake used TCP sequence number and IP address as proof for identity and signature. Three-way handshake has three steps: | |
| - | + | ====Step 1: SYN request==== | |
| - | + | Computer A sends a SYN request under its IP address with a random TCP sequence number xA to computer B. | |
| - | ==== Step 1: SYN | + | ====Step 2: SYN/ACK response==== |
| - | + | Computer B sends an ACK response with number (xA+1) and its own random TCP sequence number xB back to computer A. | |
| - | + | ====Step 3: ACK or RESET response==== | |
| - | ==== Step | + | If computer A wants to establish the connection, it sends an ACK response with number (xB+1) back to computer B. Otherwise, it sends a RESET response to drop the connection request. |
| - | Mitnick | + | ==The attack== |
| - | + | [[Image:Mitnickattack.JPG|thumb|right|500px|The Mitnick attack]] | |
| - | + | The Mitnick attack has five general steps: | |
| - | + | ====Step 1: Information gathering==== | |
| - | + | Before the attack, Mitnick was able to determine the TCP sequence number generator’s behavior of X-Terminal and a trusted relationship between X-Terminal and Server. | |
| - | + | ======Determine the TCP sequence number generator’s behavior====== | |
| - | + | Mitnick sent SYN request to X-Terminal and received SYN/ACK response. Then he sent RESET response to keep the X-Terminal from being filled up. He repeated this for twenty times. He found there is a pattern between two successive TCP sequence numbers. It turned out that the numbers were not random at all. The latter number was greater than the previous one by 128000. | |
| - | + | ======Determine a trusted relationship between X-Terminal and Server====== | |
| - | + | Before the attack, Mitnick hacked into Shimomura’s website. He used command finger and showmount to find if X-Terminal had trusted relationship with any other computers. | |
| - | + | ====Step 2: The flood==== | |
| - | + | Mitnick kept the Server muted by filling the Server up with half-open SYN requests from spoofed IP address. To create half-open SYN requests, he used routable but not active IP address. Because he had no intention to complete three-way handshake with the Server, half-open SYN request occupied the Server’s memory faster. The result is that the Server could not respond to any other requests. This is a type of Denial of Service attack. | |
| - | + | ====Step 3: Trusted relationship hijacking==== | |
| - | + | Mitnick sent a SYN request to X-Terminal with spoofed IP address as the Server. He used an arbitrary number as the Server’s TCP sequence number. X-Terminal sent a SYN/ACK response to the Server. Because the Server was muted, it did not receive the SYN/ACK response. As mentioned in the information gathering step, Mitnick was able to generate the TCP sequence number that X-Terminal created for the Server. Mitnick, again spoofed his IP as the Server’s IP, sent an ACK response to X-Terminal to finish three-way handshake. Because the returned TCP sequence number was correct, X-Terminal allowed Mitnick connect to it. The connection was established. Shimomura’s computer was considered hacked by finishing this step. | |
| - | + | ====Step 4: Remote command pump==== | |
| - | + | Mitnick wanted to create a backdoor on Shimomura computer so that he could come back later without repeating the hijack. He pumped commands from his computer to Shimomura’s computer. To be precise, they were "echo + + >> /.rhosts". The ++ allowed any computers connect to X-Terminal without being verified. | |
| - | + | ====Step 5: Clean up==== | |
| - | + | Mitnick sent RESET responses to the Server to cancel all his SYN requests. The Server was freed. | |
| - | + | ||
| - | The | + | |
| - | + | ||
| - | + | ||
| - | ==== Step | + | |
| - | + | ||
== Detection == | == Detection == | ||
| - | There | + | There are no specific mechanisms to detect the Mitnick attack directly. However, a security analyst can combine several mechanisms to detect the attack indirectly. Basically, the attack can be detected by both network-based and host-based intrusion detection systems ([http://en.wikipedia.org/wiki/Intrusion_detection_system IDS]). For network-based IDS, port scan and host scan can be used to detect a potential attack. For host-based IDS, the attack can be detected using two commonly used UNIX tool, ''TCP wrappers'' and ''tripwire''. For further details, refer to the book '''Network Intrusion Detection, an analyst's hand book''' by ''Stephen Northcutt'' (ISBN: 0-7357-0868-1) |
== Prevention== | == Prevention== | ||
| - | The Mitnick attack was | + | Nowadays, Mitnick attack is no longer practical because the security in networking field is way improved than before. However, preventing Mitnick attack is the least requirement a system must satisfy to be considered secure. It worths to mention that in the days of the attack, people (e.g. Tsutomu) used [http://en.wikipedia.org/wiki/Remote_shell remote shell (RSH)] instead of [http://en.wikipedia.org/wiki/Secure_Shell secure shell (SSH)] like today. |
| - | == | + | ==Comments== |
| - | [http://en.wikipedia.org/wiki/Transport_Control_Protocol Transport control protocol] | + | The Mitnick attack was a classic case. Mitnick took advantage of easy-to-be-known weaknesses. After his attack, computer security was taken more seriously. New tools was developed to improve security in networking over the Internet. SSH (secure shell) is used to replace RSH (remote shell) which allowed data transfered insecurely. |
| - | + | == References == | |
| - | [http://en.wikipedia.org/wiki/Ip_spoofing IP address spoofing] | + | - [http://en.wikipedia.org/wiki/Transport_Control_Protocol Transport control protocol]<BR> |
| - | + | - [http://en.wikipedia.org/wiki/Ip_spoofing IP address spoofing]<BR> | |
| - | [http://en.wikipedia.org/wiki/OSI_model Open Systems Interconnection Basic Reference Model (OSI Model)] | + | - [http://en.wikipedia.org/wiki/OSI_model Open Systems Interconnection Basic Reference Model (OSI Model)]<BR> |
| - | + | - [http://en.wikipedia.org/wiki/Tsutomu Tsutomu Shimomura (the victim of the attack)]<BR> | |
| - | [http://en.wikipedia.org/wiki/Tsutomu Tsutomu Shimomura (the victim of the attack)] | + | - [http://en.wikipedia.org/wiki/Kevin_Mitnick Kevin Mitnick (the attacker)]<BR> |
| - | + | Amazon.com: [http://www.amazon.com/Network-Intrusion-Detection-Analysts-Handbook/dp/0735708681 '''Network intrusion detection, an analyst's handbook''' by ''Stephen Northcutt''] | |
| - | [http://en.wikipedia.org/wiki/Kevin_Mitnick Kevin Mitnick (the | + | ==See also== |
| + | Information Security Topics:<BR> | ||
| + | - [[Piggybacking]]<BR> | ||
| + | - [[Security and Storage Mediums]]<BR> | ||
| + | - [[Random Number Generators and Information Security]]<BR> | ||
| + | - [[Biometric systems regarding security design principle]]<BR> | ||
| + | - [[Phishing]]<BR> | ||
| + | - [[Biometrics in Information Security]]<BR> | ||
| + | - [[Smart Card technology to prevent fraud]]<BR> | ||
| + | - [[Electronic Voting Systems]]<BR> | ||
| + | - [[Anti-spam Systems and Techniques]]<BR> | ||
| + | - [[Payment Card Industry Data Security Standard]]<BR> | ||
| + | - [[Operating Systems Security]]<BR> | ||
| + | - [[Autocomplete]]<BR> | ||
| + | - [[Social engineering]]<BR> | ||
| + | - [[Identity Theft]]<BR> | ||
| + | - [[Information security awareness]]<BR> | ||
== External links == | == External links == | ||
| - | [http://www.youtube.com/watch?v=8_VYWefmy34 An interview with Mitnick] | + | - [http://www.youtube.com/watch?v=8_VYWefmy34 An interview with Mitnick]<BR> |
| + | - [http://hack.pl/gfx/wywiady/Kevin_Mitnick.jpg Kevin Mitnick picture]<BR> | ||
| - | + | QUANG LUONG | |
| - | + | Revised date: Dec 9 2007 | |
| - | + | ||
Current revision as of 04:15, 10 December 2007
Computer security is an important factor in our information world with Internet and digitally owned materials. Over the past twenty years, network security has evolved continuously. More secure implementations are invented to replace old less secure implementations. Kevin Mitnick was able to hack into Tsutomu Shimomura's X-Terminal computer due to early implementation of TCP connection, which was not really secure at that time. With a huge desire of curiosity, Mitnick did something that no one has ever done before him. He exploited the trusted relationship between two computers by performing man-in-the-middle attack under a spoofed identity. His attack made him the most famous hacker in United States of America.
Contents |
Who is Mitnick?
Kevin Mitnick(born October 6, 1963) is known as "the most famous" hacker in United States of America. He is an expert in social engineering, which helped him to obtain many classified information used for his hacking hobby. In his early age, he was on the FBI most wanted cyber criminal list. He was captured by the FBI with the aid of Tsutomu and sentenced 5 years in prison. Now he is a security consultant in his own firm Mitnick Security Consulting.
Three-way handshake
If there is a trusted relationship between two computers (e.g. server and client), a connection can be established by a three-way handshake. In the Mitnick attack, the three-way handshake used TCP sequence number and IP address as proof for identity and signature. Three-way handshake has three steps:
Step 1: SYN request
Computer A sends a SYN request under its IP address with a random TCP sequence number xA to computer B.
Step 2: SYN/ACK response
Computer B sends an ACK response with number (xA+1) and its own random TCP sequence number xB back to computer A.
Step 3: ACK or RESET response
If computer A wants to establish the connection, it sends an ACK response with number (xB+1) back to computer B. Otherwise, it sends a RESET response to drop the connection request.
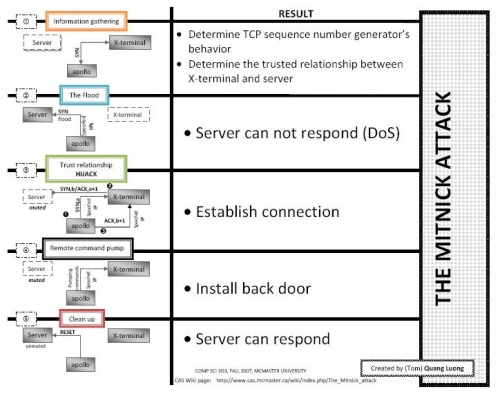
The attack
The Mitnick attack has five general steps:
Step 1: Information gathering
Before the attack, Mitnick was able to determine the TCP sequence number generator’s behavior of X-Terminal and a trusted relationship between X-Terminal and Server.
Determine the TCP sequence number generator’s behavior
Mitnick sent SYN request to X-Terminal and received SYN/ACK response. Then he sent RESET response to keep the X-Terminal from being filled up. He repeated this for twenty times. He found there is a pattern between two successive TCP sequence numbers. It turned out that the numbers were not random at all. The latter number was greater than the previous one by 128000.
Determine a trusted relationship between X-Terminal and Server
Before the attack, Mitnick hacked into Shimomura’s website. He used command finger and showmount to find if X-Terminal had trusted relationship with any other computers.
Step 2: The flood
Mitnick kept the Server muted by filling the Server up with half-open SYN requests from spoofed IP address. To create half-open SYN requests, he used routable but not active IP address. Because he had no intention to complete three-way handshake with the Server, half-open SYN request occupied the Server’s memory faster. The result is that the Server could not respond to any other requests. This is a type of Denial of Service attack.
Step 3: Trusted relationship hijacking
Mitnick sent a SYN request to X-Terminal with spoofed IP address as the Server. He used an arbitrary number as the Server’s TCP sequence number. X-Terminal sent a SYN/ACK response to the Server. Because the Server was muted, it did not receive the SYN/ACK response. As mentioned in the information gathering step, Mitnick was able to generate the TCP sequence number that X-Terminal created for the Server. Mitnick, again spoofed his IP as the Server’s IP, sent an ACK response to X-Terminal to finish three-way handshake. Because the returned TCP sequence number was correct, X-Terminal allowed Mitnick connect to it. The connection was established. Shimomura’s computer was considered hacked by finishing this step.
Step 4: Remote command pump
Mitnick wanted to create a backdoor on Shimomura computer so that he could come back later without repeating the hijack. He pumped commands from his computer to Shimomura’s computer. To be precise, they were "echo + + >> /.rhosts". The ++ allowed any computers connect to X-Terminal without being verified.
Step 5: Clean up
Mitnick sent RESET responses to the Server to cancel all his SYN requests. The Server was freed.
Detection
There are no specific mechanisms to detect the Mitnick attack directly. However, a security analyst can combine several mechanisms to detect the attack indirectly. Basically, the attack can be detected by both network-based and host-based intrusion detection systems (IDS). For network-based IDS, port scan and host scan can be used to detect a potential attack. For host-based IDS, the attack can be detected using two commonly used UNIX tool, TCP wrappers and tripwire. For further details, refer to the book Network Intrusion Detection, an analyst's hand book by Stephen Northcutt (ISBN: 0-7357-0868-1)
Prevention
Nowadays, Mitnick attack is no longer practical because the security in networking field is way improved than before. However, preventing Mitnick attack is the least requirement a system must satisfy to be considered secure. It worths to mention that in the days of the attack, people (e.g. Tsutomu) used remote shell (RSH) instead of secure shell (SSH) like today.
Comments
The Mitnick attack was a classic case. Mitnick took advantage of easy-to-be-known weaknesses. After his attack, computer security was taken more seriously. New tools was developed to improve security in networking over the Internet. SSH (secure shell) is used to replace RSH (remote shell) which allowed data transfered insecurely.
References
- Transport control protocol
- IP address spoofing
- Open Systems Interconnection Basic Reference Model (OSI Model)
- Tsutomu Shimomura (the victim of the attack)
- Kevin Mitnick (the attacker)
Amazon.com: Network intrusion detection, an analyst's handbook by Stephen Northcutt
See also
Information Security Topics:
- Piggybacking
- Security and Storage Mediums
- Random Number Generators and Information Security
- Biometric systems regarding security design principle
- Phishing
- Biometrics in Information Security
- Smart Card technology to prevent fraud
- Electronic Voting Systems
- Anti-spam Systems and Techniques
- Payment Card Industry Data Security Standard
- Operating Systems Security
- Autocomplete
- Social engineering
- Identity Theft
- Information security awareness
External links
- An interview with Mitnick
- Kevin Mitnick picture
QUANG LUONG Revised date: Dec 9 2007