Security for Small Home Networks
From Computing and Software Wiki
Security for Small Home Networks is a procedure to detect and obviate any attempt of unauthorized access to the computer.
Home wireless network is rarely secured, and therefore it is one of the most popular targets for intruders due to the fact that they can utilize it as a remote server for their applications in many inventive ways for their own purposes.
Contents |
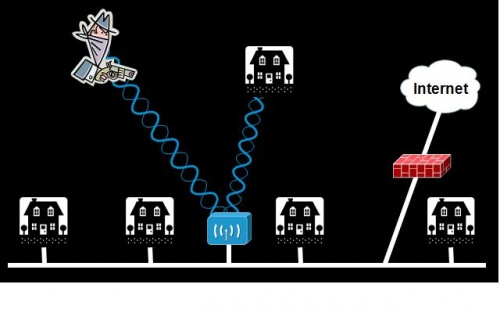
Danger of unsecure Small home network
Having unsecure home network is simply providing the intruder the chance to become a part of your local network, which in some cases would result in the usage of your broadband connection to get online without paying. However, the problems arise when an unauthorized user could abuse your connection for malicious purposes like hacking or any illegal act and since the intruder is connected to the your network, if the criminal activity is discovered and investigated, the origin of the attack will be traced back to your broadband account. More importantly, the intruder can completely take advantage of an unsecured wireless network by snooping around and steal confidential data and information from your machine or even destroying the information on it. The information damaged could be an application or the operating system resulting in a partial or complete breakdown of the machine.
Small Home network threats
Worms
Self replicating program produced without human interaction and travel across the network connections automatically. After it overtakes your computer, it searches for other listening computers to overtake, and so on. It uses system transmission capabilities to travel from machine to machine. Examples of worms can be email worm, instant messaging worms.
Virus
Is a piece of code that is written by deceitful programmer which copies itself and spread throughout your computer causing great harm to the computer`s programs. Unlike wormsm viruses need to be executed to replicate, therfore most viruses are attached to executable files and when the user get to run that executable the virus has the chance to reproduce. Sometimes the programs that got infected act as a virus themselves.
Spyware
They aren’t designed to damage your computer, spyware is a software that may run in the background and collects data about the user and monitor your internet surfing which may lead to identity theft.A spyware program is rarely alone on a computer, an affected machine usually has multiple infections. Users frequently notice some symptoms like degradation of system performance, computer starts to behave strangely and in some cases users' computer setting might change and they wont be able to change it back. A common way to become a victim of spyware is to download certain peer-to-peer file swapping products.
Trojan Horse program
It is one of the most serious threats to computer security simply because it is a software program that appears to be harmless or useful, but in fact it is harmful software that gets unauthorized control over your computer. Usually, Trojans create a "backdoor", which is used to send your personal information to another location which may lead to identity theft or sends your credit card numbers and passwords to a stranger. The most common means of infection is through email attachments
Denial of service
Attack that attempt to prevent authorized access to a system resource or delay system operations and functions, it essentially disable your computer or your network. Despite the fact that a DoS attack does not usually result in the theft of information or other security loss, it can cost the person or company a lot of money and time. Failure to access any web site anf dramatic increase in the amount of spam you receive in your account would indicate DoS attack.
Ways to secure small home network
Network Firewall
Change the default SSID
Devices come with a default system ID called the SSID (Service Set Identifier). If intruders found a default SSID, they figure that it is a poorly configured network and are much more likely to attack it. Change the default SSID immediately when configuring wireless security on your network. Use something unique, not something that can easily be guessed.
Change administrator password
Change the administrative password on your home wireless router when installing the unit so wireless snoopers can’t get into the router and mess around with its settings. The default passwords for popular models of wireless network are well-known to all intruders.
Enable encryption
Generate the WPA Encryption key, copy it and paste it into your wireless router's configuration panel. This would help securing your wireless network from traffic getting snooped or your bandwidth getting hijacked.
Web filter
Web filters monitor Web pages and controls access to certain websites to determine whether it should be displayed to the user or not. Web filters checks the origin and the content of a Web page against a set of rules provided by company or person who has installed the Web filter. Example for such web filter is K9.
Spam filter
Just like a web filter, a spam filter, but it looks at your e-mail and determines if it is a real e-mail or spam mail. Example spamAware.
Antivirus Software
They are software that aims to identify, obviate and remove malicious software. Having antivirus software running on your machine is crucial.
Install Firewall
Use Firewall because it acts as a protective barrier between your computer and the Internet and provides an extra layer of security where hackers and intruders could not break into your network. A firewall has the ability to block all traffic to and from a specific IP address, and protect it from viruses and worms etc. However, it is not sufficient to install a firewall and then ignore all other security measures.
Install Antispyware Software
Antispyware attempts to detect and eliminate spyware that has been installed on your computer and it protects your privacy by removing cookies and software that track you on the Internet. Example of antispyware that you can install is Ad-Aware.