Secure Shell Client
From Computing and Software Wiki
(→1. About Secure Shell) |
(→1. About Secure Shell) |
||
| Line 309: | Line 309: | ||
EmTec's ZOC is a terminal emulator that supports Secure Shell. It runs on OS/2 and Windows 32-bit. For more information, please see http://www.emtec.com/zoc/. | EmTec's ZOC is a terminal emulator that supports Secure Shell. It runs on OS/2 and Windows 32-bit. For more information, please see http://www.emtec.com/zoc/. | ||
---- | ---- | ||
| + | '''3. Installing Secure Shell''' | ||
| + | ---- | ||
| + | This section gives you basic information on how to install the Secure Shell distribution from SSH Communications Security. Click here for the contents of this section. | ||
| + | |||
| + | '''3.1. What is the latest version of Secure Shell?''' | ||
| + | ---- | ||
| + | The latest version of SSH1 is 1.2.27, and SSH2 is 2.2.0. If you are not using the latest version, you may run into problems. | ||
| + | |||
| + | The latest version of lsh is 0.9.14, and be aware that lsh is still in testing mode and is not ready for prime-time yet. | ||
| + | |||
| + | '''3.2. How do I install Secure Shell?''' | ||
| + | ---- | ||
| + | To install Secure Shell (either SSH1 or SSH2), download the tar files and place in a directory (either /tmp or /usr/local/src). Then do the following: | ||
| + | |||
| + | # gzip -dc ssh-2.2.0.tar.gz | tar -xvf - | ||
| + | # cd ssh-2.2.0 | ||
| + | # ./configure | ||
| + | # make | ||
| + | # make install | ||
| + | Please read the INSTALL file for more specifc instructions on SSH1, and for SSH2, please read the README. | ||
| + | |||
| + | |||
| + | If you run into any problems, check out the troubleshooting section before sending it to the Secure Shell mailing list. | ||
| + | |||
| + | Note: You may have to use specific options with configure to get Secure Shell to work the way you want (with certain ciphers, using TCP Wrappers, socks support, etc.). | ||
| + | |||
| + | '''3.3 Does it make sense to install Secure Shell as a non-root user on UNIX?''' | ||
| + | ---- | ||
| + | If you run the server, sshd or sshd2, as a user other than root then you can only login as that user. | ||
| + | |||
| + | If you install the client, ssh or ssh2, non setuid root you will still be able to connect and login to remote servers, but you will not be able to use hostbased authentication. | ||
| + | |||
| + | You can also start up sshd yourself as non-root, supplying the -p option so it binds to a non-privileged port (port number higher than 1024), and then connect from another system with ssh -p. This will only allow connections to your own account, and sshd will, as a rule, not be restarted when your machine reboots. | ||
| + | |||
| + | You will have to decide whether this is useful for you or not. | ||
| + | |||
| + | '''3.4 Where do I get pre-compiled binaries for Secure Shell?''' | ||
| + | ---- | ||
| + | Redhat RPMs: | ||
| + | ---- | ||
| + | ssh-2.2.0 - ftp://ftp.ssh.com/pub/ssh/rpms. This includes both binaries (with and without X) and source | ||
| + | ssh-2.0.11 - ftp://ftp.zedz.net/pub/cryptoI/linux/redhat/test_rpms | ||
| + | OpenSSH - ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH/portable/rpm | ||
| + | Solaris 2.6, 2.7: | ||
| + | |||
| + | ssh-1.2.27 with SDI patch - ftp://ftp.parc.xerox.com/pub/jean/solins/pkg/5.6/sshsdi.Z | ||
| + | pgp signature - ftp://ftp.parc.xerox.com/pub/jean/solins/pkg/5.6/sshsdi.Z.asc | ||
| + | SSH Communications Security and F-Secure also include binaries for several flavors of UNIX. | ||
| + | ---- | ||
References: http://www.employees.org/~satch/ssh/faq/ssh-faq.html | References: http://www.employees.org/~satch/ssh/faq/ssh-faq.html | ||
Revision as of 00:42, 4 April 2008
1. About Secure Shell
1.1. What is Secure Shell?
Secure Shell is a program to log into another computer over a network, to execute commands in a remote machine, and to move files from one machine to another. It provides strong authentication and secure communications over unsecure channels. It is intended as a replacement for telnet, rlogin, rsh, and rcp. For SSH2, there is a replacement for FTP: sftp.
Additionally, Secure Shell provides secure X connections and secure forwarding of arbitrary TCP connections. You can also use Secure Shell as a tool for things like rsync and secure network backups.
The traditional BSD 'r' - commmands (rsh, rlogin, rcp) are vulnerable to different kinds of attacks. Somebody who has root access to machines on the network, or physical access to the wire, can gain unauthorized access to systems in a variety of ways. It is also possible for such a person to log all the traffic to and from your system, including passwords (which ssh never sends in the clear).
The X Window System also has a number of severe vulnerabilities. With ssh, you can create secure remote X sessions which are transparent to the user. As a side effect, using remote X clients with ssh is more convenient for users.
There are two versions of Secure Shell available: SSH1 and SSH2. This FAQ does its best to distinguish when the situation calls for the difference between the two.
1.2 How widespread is its use?
The most current figures available are over 2 million Secure Shell users in over 60 countries. This is not an accurate amount, but an estimate. It also does not necessarily include the different implementations of Secure Shell for different operating systems.
Note that this includes both SSH1 and SSH2 implementations.
1.3 What protocols does Secure Shell use?
It should be noted that the SSH1 and SSH2 protocols are in fact different and not compatible with each other.
For the SSH1 protocol, you can find this information in an old IETF draft available here. It is also available with the latest source distribution for SSH1 at ftp.ssh.com/pub/ssh/ssh-1.2.27.tar.gz.
For the SSH2 protocol, you can find this information in the SSH2 IETF drafts:
http://www.ietf.org/ids.by.wg/secsh.html The fifth IETF draft for Secure Shell, Generic Message Exchange Authentication For Secure Shell is no longer available and expired after 6 months.
1.4 What encryption algorithms does Secure Shell use?
Secure Shell uses the following ciphers for encryption: Cipher SSH1 SSH2 DES yes no 3DES yes yes IDEA yes no Blowfish yes yes Twofish no yes Arcfour no yes Cast128-cbc no yes
Secure Shell uses the following ciphers for authentication: Cipher SSH1 SSH2 RSA yes no DSA no yes
Ciphers may be added or deleted later depending on implementations.
1.5 How does Secure Shell authenticate?
Secure Shell authenticates using one or more of the following:
Password (the /etc/passwd or /etc/shadow in UNIX) User public key (RSA or DSA, depending on the release) Kerberos (for SSH1) Hostbased (.rhosts or /etc/hosts.equiv in SSH1 or public key in SSH2) Since there is quite a big demand for it, there are some patches available for various forms of authentication. It is up to the authors to make those available. If you wish to have a particular type of authentication in Secure Shell, please submit a feature request to the SSH Secure Shell team. For OpenSSH features, please contact the OpenSSH team.
1.6 What does Secure Shell protect against?
Secure Shell protects against IP spoofing, where a remote host sends out packets which pretend to come from another, trusted host. Ssh even protects against a spoofer on the local network, who can pretend he is your router to the outside. IP source routing, where a host can pretend that an IP packet comes from another, trusted host. DNS spoofing, where an attacker forges name server records Interception of cleartext passwords and other data by intermediate hosts Manipulation of data by people in control of intermediate hosts Attacks based on listening to X authentication data and spoofed connection to the X11 server In other words, ssh never trusts the net; somebody hostile who has taken over the network can only force ssh to disconnect, but cannot decrypt or play back the traffic, or hijack the connection.
The above only holds if you actually use encryption. Secure Shell does have an option to use encryption of type "none" this is only for debugging purposes, and should not be used.
1.7 What doesn't Secure Shell protect against?
Secure Shell will not help you with anything that compromises your host's security in some other way. Once an attacker has gained root access to a machine, he can then subvert ssh, too.
If somebody malevolent has access to your home directory, then security is nonexistent. This is very much the case if your home directory is exported via NFS.
Here is an example using SSH to connect to Birkhoff server using ssh command. I then use the rsh command to connect to the wolf machines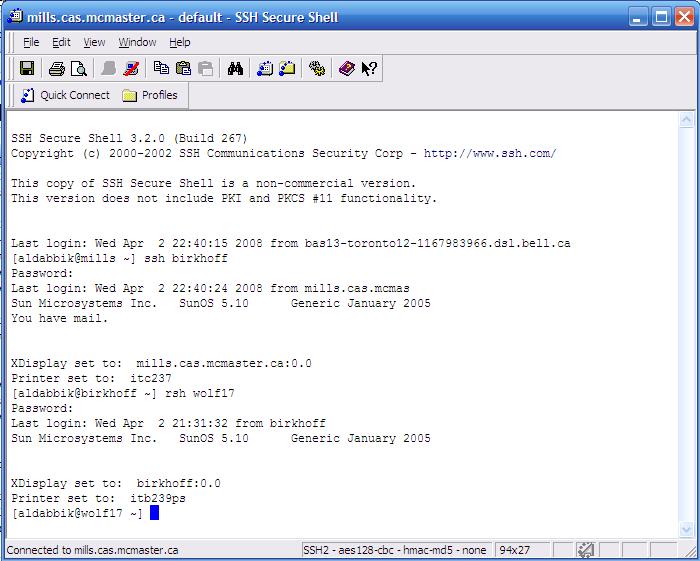
1.8 What is the difference between SSH1 and SSH2?
The difference between SSH1 and SSH2 is they are two entirely different protocols. SSH1 and SSH2 encrypt at different parts of the packets, and SSH1 uses server and host keys to authenticate systems where SSH2 only uses host keys. SSH2 is a complete rewrite of the protocol, and it does not use the same networking implementation that SSH1 does. Also, SSH2 is more secure. Because of the different protocol implementation, they are not compatible.
In a nutshell, SSH2 is a rewrite of the SSH1 protocol, with improvements to security, performance, and portability.
1.9 Who maintains Secure Shell?
SSH Communications Security, is the developer of Secure Shell (secsh) protocol and maintains the releases of SSH1 and SSH2. The IETF maintains the Secure Shell standards, which is vendor-neutral. The standards are currently in draft form; once there are two independent implementations available, then they can be submitted as an RFC.
There are currently several implementors, both freeware and commercial, of Secure Shell.
1.10 Can I run Secure Shell legally?
Most likely. It depends on your country's laws for cryptography and which version of Secure Shell that you're using. Check out the information on licensing, cryptography laws, and patents on cryptographic algorithms below.
1.10.1 Licensing
The licensing for SSH2 as of the 2.1.0 release has been completely revised. You can use Secure Shell for free if you are a university user (student, professor, staff, etc) or if you are using it for non-commercial use (playing games, checking personal email, etc.). For any commercial use, you need to have the appropriate license for Secure Shell. Click here for the current licensing information and click here for an FAQ on the licensing from SSH Communications Security.
The UNIX version of ssh 1.2.27 may be used freely for non-commercial purposes and may not be sold commercially as a separate product, as part of a bigger product or project, or otherwise used for financial gain without a separate license. The definition of "commercial use" is generally interpreted as using ssh for anything that would generate financial gain, such as logging into a customers system to do administration, or providing ssh as a secure login to your partners or vendors.
Other licensing is developer-dependent.
1.10.2 Cryptography laws
In some countries, particularly France, Russia, Iraq, and Pakistan, it may be illegal to use any encryption at all without a special permit.
If you are in the United States, you should be aware that, while ssh was written outside the United States using information publicly available everywhere, the US Government may consider it a criminal offence to export this software from the US once it has been imported, including putting it on a ftp site. Contact the Bureau of Export Administration, which is under the Department of Commerce.
There's a really good link that keeps up to date with the Wassenaar Agreement and the cryptography laws throughout the world. Check out Bert-Jaap Koops Crypto Law Survey.
1.10.3 Patents on Cryptographic algorithms
The algorithms RSA and IDEA, which are used by ssh, are claimed as patented in different countries, including the US. Linking against the RSAREF library, which is possible, may or may not make it legal to use ssh for non-commercial purposes in the US. You may need to obtain licenses for commercial use of IDEA; ssh can be configured without IDEA and works perfectly fine without it.
For information on software patents in general, see the League for Programming Freedom's homepage at http://lpf.ai.mit.edu/.
1.11 What operating systems does Secure Shell run on?
From the Secure Shell home page:
For SSH1 and the current release of SSH2 (2.2.0), check out the portability page at http://www.ssh.com/ssh/portability.html. For compatability with OpenSSH, check out http://www.openssh.com/portable.html.
There are also non-commercial ports of Secure Shell for SSH1 including PalmOS, Windows, Macintosh, OS/2, BeOS, WindowsCE, Java, and OpenVMS. See section 2 of this FAQ for information on how to get Secure Shell.
1.12 . Shouldn't I be using only SSH2?
Maintainer's note: Since this brought up an interesting discussion on the mailing list, it seems to be a good idea to incorporate some of the helpful information that folks brought up. Thanks! Also, if someone has a better way to organize this section, please let me know.
The SSH1 protocol is not being developed anymore, as SSH2 is being developed as the standard. Even if you are not using SSH2, many folks are establishing a path towards it. With three implementations (and growing) of SSH2 currently in the works, there is growing support (especially with the SSH2 protocol in IETF draft). However, there are arguments for and against running SSH1.
Note: If you have any additional arguments either way, I'll post them. -AC
There are structural weaknesses in SSH1 which leave it open to additional attacks SSH1 is subject to a man-in-the-middle attack SSH1 has more supported platforms SSH1 supports .rhosts authentication (it's against the draft for SSH2 SSH1 has more diverse authentication support (AFS, Kerberos, etc.) Performance for SSH2 is not equal to SSH1 Rick Moen posted this software matrix on the mailing list that shows software from diverse authors will perhaps partially explain protocol 1.5's persistence:
Highest protocol version supported in software that is:
Servers
Straight Proprietary Gratis-Usage (non-commercial) Unconditional Gratis-usage Open Source [1]
OpenVMS - - - 1.5
OS/2 - 1.5 none none
UNIX 2.0 2.0 none 2.0
Win32 - 2.0 none 2.0
Clients
Straight Proprietary Gratis-Usage (non-commercial) Unconditional Gratis-usage Open Source [1]
Amiga OS 1.5 1.5 none none
BeOS - 1.5 none none
Java - - none 1.5 [2]
Macintosh 2.0 - 1.5 none
OpenVMS - - - 1.5
OS/2 2.0 1.5 none none
PalmOS - - 1.5 none
UNIX 2.0 2.0 1.5 2.0
Win16 2.0 1.4 none none
Win32 2.0 2.0 1.5 2.0
WinCE 1.5 none - none
2.1.1 Offical site
The central site for distributing ssh is at SSH Communication Security. The application is available at ftp://ftp.ssh.com/pub/ssh/. If you wish to license SSH Secure Shell for either commercial or university distribution (remember, no cost to universities or non-profit organizations), please go to http://commerce.ssh.com
Information on how to check signatures is available at ftp.ssh.com/pub/ssh/HOWTO-CHECK-SIGNATURES.
Official releases of SSH1 are PGP-signed (RSA only), with the following key ID: Type Bits Key ID Date User ID RSA 1024 DCB9AE01 1995/04/24 Ssh distribution key <ylo@cs.hut.fi> Key fingerprint = C8 90 C8 5A 08 F0 F5 FD 61 AF E6 FF CF D4 29 D9
Official releases of SSH2 are PGP-signed (both RSA and DSA), with the following key IDs *: Type Bits Key ID Date User ID
RSA 2048 AFCA7459 1998/07/11 Ssh 2 Distribution Key <ssh2@ssh.com>
Key fingerprint = 2A 06 2C 83 F0 A6 72 52 3A 4D 4A FA 20 15 EE 74
DSA 1024 83FB127C 2000/06/13 Ssh 2 Distribution Key <ssh2@ssh.com>
Key fingerprint = A348 205D F1D8 2297 0A46 D961 ED7B 28CD 83FB 127C
Note: These keys also use the ssh2@ssh.fi address for signing.
2.1.2 Mirrors
Secure Shell is also available via anonymous ftp from the sites listed at http://www.ssh.com/ssh/download.html. Because they are updated regularly, it is too difficult to keep them up to date here.
2.2 How about getting other relatively free versions of Secure Shell?
Here is a list of other implementations Secure Shell clients and servers. The official distribution from SSH Communications Security is not included with these downloads. Please note that they should interoperate with each other; however, this is developer-dependent.
Please note that these distributions may or may not be actively maintained. The owners may not notify people if they are still maintaining the software, and it may or may not work. This information is up here for your information, and if you legally can run the software--to play with it.
If you're looking for a really complete list of Secure Shell clients, take a look at Rick Moen's list at http://linuxmafia.com/pub/linux/security/ssh-clients.
2.2.1 UNIX
Niels Möller is developing a GPL'd C implementation of the ssh version 2 protocol. Pick up the latest release (which is currently at 0.9.13) at http://www.net.lut.ac.uk/psst/download.html.
The folks from OpenBSD has also created a free Secure Shell implementation of SSH1 and SSH2. You can find it at http://www.openssh.com/. The ports are available for Linux, Solaris, FreedBSD, and many others.
OpenSSH is part of the base OS for OpenBSD, just as rsh, telnet, ksh, etc are installed. If you download the ftp://ftp.openbsd.org/pub/OpenBSD/2.6/i386/base26.tar.gz you will find that ./usr/bin/ssh is one of the files included. In other words, it is part of the base tarball that everybody on every install gets.
At the end of the install, one has the option of installing the usa based RSA implementation, the international RSA implementation, or no RSA implementation; in this last case, only protocol v2 will be used. (if installed, RSA gets retrieved via ftp to avoid patent problems).
You can also get Bjoern Groenvall's ossh (an older freeware port of SSH1) at ftp://ftp.pdc.kth.se/pub/krypto/ossh/.
2.2.2 Java
There are a couple of different Java implementations of Secure Shell.
Cédric Gourio's SSH1 java-applet - http://www.cl.cam.ac.uk/~fapp2/software/java-ssh/.
Mindterm and Mindtunnel - http://www.mindbright.se/english/technology
MindVNC, a Virtual Network Computer using SSH1 - http://www.mindbright.se/english/technology
Java Telnet Application has an Secure Shell plugin - http://www.mud.de/se/jta/doc/plugins/SSH.html
2.2.3 Windows
For some reason, a lot of people have created Secure Shell ports to Windows :-). This is the current list of Windows ports.
Robert O'Callahan's TTSSH, SSH1 extension to TeraTerm client - http://www.zip.com.au/~roca/ttssh.html
Gorden Chaffee's command line port of ssh1 and scp1 - http://bmrc.berkeley.edu/people/chaffee/winntutil.html
Sergey Okhapkin's SSH1 and SSH2 servers and clients port to 32-bit Windows - http://www.lexa.ru/sos/
Corinna Vinschen has ported OpenSSH to Cygwin- ftp://ftp.franken.de/pub/win32/develop/gnuwin32/cygwin/porters/Vinschen_Corinna/V1.1.1
PuTTY, Simon Tatham's 32-bit Windows (SSH 1 & 2) client - http://www.chiark.greenend.org.uk/~sgtatham/putty.html
FiSSH, Mass Confusion's 32-bit SSH1 client for Windows - http://mit.edu/ssh/FiSSH
Cynus Win32 port of Secure Shell 1.2.2 by Raju Mathur - http://reality.sgi.com/raju/software.html
PenguiNet Secure Shell and Telnet client - http://www.siliconcircus.com/penguinet (Shareware)
Cedomir Igaly's SSH1 Windows 16 and 32 bit clients are no longer available.
2.2.4 Macintosh
NiftyTelnet 1.1 Secure Shell is Jonas Wallden's implementation of SSH1 for Macintosh. It is available at http://www.lysator.liu.se/~jonasw/freeware.html.
MacSSH is an SSH2 implementation for Mac clients. You can find it at http://www.macssh.com.
2.2.5 OpenVMS
There is David Jones' OpenVMS SSH1 server available at http://www.er6.eng.ohio-state.edu/~jonesd/ssh/. The OpenVMS SSH1 client is done by Christer Weinigel and Richard Levitte and is available at http://www.free.lp.se/fish/.
2.2.6 Handheld devices
The ISAAC group released a version of the SSH1 client for the Palm Pilot, Top Gun ssh 1.2. It's available at http://www.isaac.cs.berkeley.edu/pilot/.
Mov Software has released a port of SSH1 to WindowsCE called sshCE. You can register for beta testing at http://www.movsoftware.com/sshce.htm. Please note that this has been in "late beta testing" for over a year now, so we're not sure if this is actively being worked on.
2.2.7 BeOS
The current BeOS R4 port of SSH1 for Intel and PowerPC platforms is available through Bebits at http://www.bebits.com/app/703. Also, check out the sshLogin client at http://www.bebits.com/app/746.
2.2.8 OS/2
The most current port of the SSH1 client to OS/2 is available at ftp://hobbes.nmsu.edu/pub/os2/apps/internet/telnet/client/ssh-1.2.27-b1.zip, which runs on OS/2 Warp 3+. There is also another Secure Shell program available at ftp://hobbes.nmsu.edu/pub/os2/apps/internet/telnet/client/sshos203.zip; however, we have no idea what it is.
2.2.9 DOS
There's now a port of SSH1 to DOS (yes, Disk Operating System) available at http://www.vein.hu/~nagyd.
2.3 How about getting commerically supported versions of Secure Shell?
There are three current commercial releases of Secure Shell. They are distributed by SSH Communication Security, F-Secure (formally Datafellows), and Van Dyke Software.
2.3.1 SSH Secure Shell
SSH Secure Shell is available from http://www.ssh.com/ssh. The product includes clients for Windows (which integrates secure file transfer in a GUI) and UNIX (which includes a server that allows two simultaneous connetions), and server available for UNIX as well. Please contact SSH Communications Security directly for more information.
2.3.2 Van Dyke Software SecureCRT
SecureCRT is available at http://www.vandyke.com/products/securecrt/. This Secure Shell client runs on Windows platforms and supports the SSH1 and SSH2 protocol. They also have SecureFX, a file transfer product that does FTP tunneling over SSH2. Please contact Van Dyke directly for more information.
2.3.3 F-Secure Tunnel and Terminal
F-Secure Tunnel and Terminal is available at http://www.f-secure.com/products/cryptography/f-sshtt.htm. It runs on UNIX, Windows, and Macintosh. It implements the SSH2 protocol, and does have a command-line scp for Windows. Please contact F-Secure directly for more information. 2.3.4 Appgate Client and Server Appgate provides a gateway for applications using a centralized database for authentication using Secure Shell. It works on Win16, Win32, UNIX, OS/2, and Macintosh. Go to http://www.appgate.com for more information.
2.3.5 EmTec ZOC
EmTec's ZOC is a terminal emulator that supports Secure Shell. It runs on OS/2 and Windows 32-bit. For more information, please see http://www.emtec.com/zoc/.
3. Installing Secure Shell
This section gives you basic information on how to install the Secure Shell distribution from SSH Communications Security. Click here for the contents of this section.
3.1. What is the latest version of Secure Shell?
The latest version of SSH1 is 1.2.27, and SSH2 is 2.2.0. If you are not using the latest version, you may run into problems.
The latest version of lsh is 0.9.14, and be aware that lsh is still in testing mode and is not ready for prime-time yet.
3.2. How do I install Secure Shell?
To install Secure Shell (either SSH1 or SSH2), download the tar files and place in a directory (either /tmp or /usr/local/src). Then do the following:
- gzip -dc ssh-2.2.0.tar.gz | tar -xvf -
- cd ssh-2.2.0
- ./configure
- make
- make install
Please read the INSTALL file for more specifc instructions on SSH1, and for SSH2, please read the README.
If you run into any problems, check out the troubleshooting section before sending it to the Secure Shell mailing list.
Note: You may have to use specific options with configure to get Secure Shell to work the way you want (with certain ciphers, using TCP Wrappers, socks support, etc.).
3.3 Does it make sense to install Secure Shell as a non-root user on UNIX?
If you run the server, sshd or sshd2, as a user other than root then you can only login as that user.
If you install the client, ssh or ssh2, non setuid root you will still be able to connect and login to remote servers, but you will not be able to use hostbased authentication.
You can also start up sshd yourself as non-root, supplying the -p option so it binds to a non-privileged port (port number higher than 1024), and then connect from another system with ssh -p. This will only allow connections to your own account, and sshd will, as a rule, not be restarted when your machine reboots.
You will have to decide whether this is useful for you or not.
3.4 Where do I get pre-compiled binaries for Secure Shell?
Redhat RPMs:
ssh-2.2.0 - ftp://ftp.ssh.com/pub/ssh/rpms. This includes both binaries (with and without X) and source ssh-2.0.11 - ftp://ftp.zedz.net/pub/cryptoI/linux/redhat/test_rpms OpenSSH - ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH/portable/rpm Solaris 2.6, 2.7:
ssh-1.2.27 with SDI patch - ftp://ftp.parc.xerox.com/pub/jean/solins/pkg/5.6/sshsdi.Z pgp signature - ftp://ftp.parc.xerox.com/pub/jean/solins/pkg/5.6/sshsdi.Z.asc SSH Communications Security and F-Secure also include binaries for several flavors of UNIX.
References: http://www.employees.org/~satch/ssh/faq/ssh-faq.html
