Secure Electronic Transaction (SET) Protocol
From Computing and Software Wiki
| (2 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
| - | The Secure Eletronic Transaction (SET) Protocol was created by the the credit cards companies VISA and MasterCard. It`s main objective is to secure transactions with credit cards over insecure networks. The SET protocol relies on cryptography and [ | + | The Secure Eletronic Transaction (SET) Protocol was created by the the credit cards companies VISA and MasterCard (involving other companies such as GTE, IBM, Microsoft, Netscape, RSA and VeriSign) starting in 1996. It`s main objective is to secure transactions with credit cards over insecure networks. The SET protocol relies on [http://en.wikipedia.org/wiki/Cryptography cryptography] and [http://en.wikipedia.org/wiki/Digital_certificate digital certificate] to ensure the authenticity of the users, confidentially of information and the payment`s integrity. |
| - | + | ||
== Overview == | == Overview == | ||
| - | All users of SET must first be registered with the Certificate Authority before a transaction is allowed to take place. Digital Certificate is used to ensure confidentially of any transactions. If a transaction is needed, both parties will then exchange their certificate. | + | All users of SET must first be registered with the Certificate Authority before a transaction is allowed to take place. Digital Certificate is used to ensure confidentially of any transactions. If a transaction is needed, both parties will then exchange their certificate. The sender will use the randomly generated session key to encrypt all the messages and use the recipient's public key to encrypt the session key. This is known as "digital envelop" of the message. The recipient will then decrypt the digital envelop using his private key and uses the symmetric key to obtain the original message. SET uses both the secret key (impractical as each customer need a distinct key) and [http://en.wikipedia.org/wiki/Public_key public key cryptography] (merchant would only need to publish his public key and the customer would be able to send a secure message to him.) |
| - | + | ||
| - | The sender will use the randomly generated session key to encrypt all the messages and use the recipient's public key to encrypt the session key. This is known as "digital envelop" of the message. | + | |
| - | + | ||
| - | The recipient will then decrypt the digital envelop using his private key and uses the symmetric key to obtain the original message. | + | |
| - | + | ||
| - | SET uses both the secret key (impractical as each customer need a distinct key) and public key cryptography (merchant would only need to publish his public key and the customer would be able to send a secure message to him.) | + | |
== Dual Signature == | == Dual Signature == | ||
| - | |||
| - | + | The data of a payment on a trasaction made by a customer includes information that concearn only to the merchant (Order Information) and only to the bank (Payment Information), that means, two messages for two different destinations. The Dual Signature permits that those information to be sent in single transaction protected by [[Digital Signatures]]. By doing this, the information will be delivered only to right destination, providing to the customers more privacy. This "linked" information also permits disputes between the involved parts(like miss calculations, erroneous charges or to determine if a payment that belongs to a specifc order) to be solved more easily. | |
| - | + | === Operation === | |
| + | This dual Signature works by encrypting the order information with the merchant`s public key an the information that refers to the payment is encrypted with the bank`s public key. The informations from the payment(PI) and from the order(OI) are hashed and the result is concatenated. Then the concatenated result is again hashed then encrypted with the customer`s key(CPKE), generating the dual signature. | ||
| - | |||
| - | + | Dual Signature = CPKE { H [ H(PI) || H(OI) ] } | |
| - | |||
| - | + | === Verification of the Dual Signature === | |
| - | + | According to the [http://www.comp.nus.edu.sg/~jervis/cs3235/set.html Data Security for e-Transaction] website the verification of the dual signature is done the following way: | |
| - | + | *Verification of the Dual Signature by the merchant | |
| - | + | Assuming that the merchant has the PIMD (message digest of the payment details; he does not require the payment details of the customer) and the Order details (OI) to verify the dual signature, the merchant simply need to perform the following: | |
| - | + | 1) H [ PIMD || H (OI)] | |
| - | + | 2) Decrypt the dual signature using the customer public key. | |
| + | The merchant can obtain the customer public key for the customer's certificate. The values from (1) and (2) should be equal. | ||
| + | *Verification of the Dual Signature by the Bank | ||
| - | + | Assuming that the Bank has the Payment details, and the OIMD (message digest of order details) to verify the dual signature, the bank simply needs to perform the following: | |
| - | + | 1) H [ H (PI) || OIMD] | |
| + | 2) Decrypt the dual signature using the customer public key. | ||
| + | The merchant can obtain the customer public key for the customer's certificate. The values from (1) and (2) should be equal. | ||
== General Steps == | == General Steps == | ||
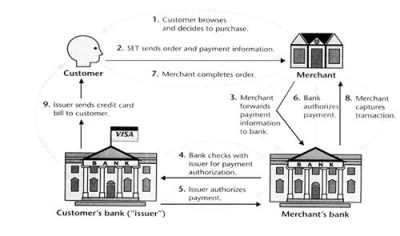
| - | + | According to the [http://www.comp.nus.edu.sg/~jervis/cs3235/set.html Data Security for e-Transaction] website the general steps for the SET are: | |
| - | + | * Customer to Merchant | |
[[Image:wikiimage1.jpeg |thumb|400px|right| '''General Steps''']] | [[Image:wikiimage1.jpeg |thumb|400px|right| '''General Steps''']] | ||
| - | Customer sends both the order and payment details to the merchant, together with his certificate. | + | # Customer sends both the order and payment details to the merchant, together with his certificate. |
| + | # The payment details will be encrypted; merchant will not be able to read the payment details. | ||
| + | # The merchant uses the customer certificate to verify the customer. | ||
| - | + | * Merchant to Customer's Bank | |
| - | + | #Merchant will send this payment details to his bank who will then forward it to the customer's bank to request authorization that the customer has sufficient available credit for the purchase. | |
| - | + | * Confirmation of Order | |
| - | + | #Once the authorization is received, the merchant will send an order confirmation to the customer. | |
| - | + | * Shipping of Goods | |
| - | + | #Upon confirmation by the customer, the merchant will deliver the goods to the customer | |
| - | + | * Request for Payment By Merchant | |
| - | + | #Lastly, the bank makes a request to the customer's credit card bank for payment. | |
| - | == | + | == See Also == |
| - | + | [[Digital Signatures]] | |
| + | [[Public Key Encryption Algorithms]] | ||
| - | + | [http://en.wikipedia.org/wiki/Digital_certificate Digital Certificate] | |
| - | + | ||
| - | + | ||
| + | [http://en.wikipedia.org/wiki/Cryptography Cryptography] | ||
== External links == | == External links == | ||
| - | [http://www.comp.nus.edu.sg/~jervis/cs3235/set.html] | + | [http://www.comp.nus.edu.sg/~jervis/cs3235/set.html Data Security for e-Transaction] |
| + | |||
| + | [http://www.samconline.com/samc/6340/Chapter-11-e-commerce/sld014.htm SET Electronic Transmission Protocol] | ||
| + | |||
| + | [http://en.wikipedia.org/wiki/Secure_electronic_transaction Secure Electronic Transaction] | ||
| + | |||
| + | [http://www.davidreilly.com/topics/electronic_commerce/essays/secure_electronic_transactions.html Secure Electronic Transactions] | ||
| + | |||
| + | [http://en.wikipedia.org/wiki/Public_key Public Key Cryptography] | ||
| + | |||
| + | == References == | ||
| + | #Data Security for e-Transaction. Retrieved on April 12th 2008, from <http://www.comp.nus.edu.sg/~jervis/cs3235/set.html> | ||
| + | #SET Electronic Transmission Protocol. Retrieved on April 12th 2008, from <http://www.samconline.com/samc/6340/Chapter-11-e-commerce/sld014.htm> | ||
| - | |||
| - | + | --[[User:Nobrem|Nobrem]] 21:30, 13 April 2008 (EDT) | |
| - | --[[User:Nobrem|Nobrem]] | + | |
Current revision as of 02:21, 14 April 2008
The Secure Eletronic Transaction (SET) Protocol was created by the the credit cards companies VISA and MasterCard (involving other companies such as GTE, IBM, Microsoft, Netscape, RSA and VeriSign) starting in 1996. It`s main objective is to secure transactions with credit cards over insecure networks. The SET protocol relies on cryptography and digital certificate to ensure the authenticity of the users, confidentially of information and the payment`s integrity.
Contents |
Overview
All users of SET must first be registered with the Certificate Authority before a transaction is allowed to take place. Digital Certificate is used to ensure confidentially of any transactions. If a transaction is needed, both parties will then exchange their certificate. The sender will use the randomly generated session key to encrypt all the messages and use the recipient's public key to encrypt the session key. This is known as "digital envelop" of the message. The recipient will then decrypt the digital envelop using his private key and uses the symmetric key to obtain the original message. SET uses both the secret key (impractical as each customer need a distinct key) and public key cryptography (merchant would only need to publish his public key and the customer would be able to send a secure message to him.)
Dual Signature
The data of a payment on a trasaction made by a customer includes information that concearn only to the merchant (Order Information) and only to the bank (Payment Information), that means, two messages for two different destinations. The Dual Signature permits that those information to be sent in single transaction protected by Digital Signatures. By doing this, the information will be delivered only to right destination, providing to the customers more privacy. This "linked" information also permits disputes between the involved parts(like miss calculations, erroneous charges or to determine if a payment that belongs to a specifc order) to be solved more easily.
Operation
This dual Signature works by encrypting the order information with the merchant`s public key an the information that refers to the payment is encrypted with the bank`s public key. The informations from the payment(PI) and from the order(OI) are hashed and the result is concatenated. Then the concatenated result is again hashed then encrypted with the customer`s key(CPKE), generating the dual signature.
Dual Signature = CPKE { H [ H(PI) || H(OI) ] }
Verification of the Dual Signature
According to the Data Security for e-Transaction website the verification of the dual signature is done the following way:
- Verification of the Dual Signature by the merchant
Assuming that the merchant has the PIMD (message digest of the payment details; he does not require the payment details of the customer) and the Order details (OI) to verify the dual signature, the merchant simply need to perform the following:
1) H [ PIMD || H (OI)]
2) Decrypt the dual signature using the customer public key.
The merchant can obtain the customer public key for the customer's certificate. The values from (1) and (2) should be equal.
- Verification of the Dual Signature by the Bank
Assuming that the Bank has the Payment details, and the OIMD (message digest of order details) to verify the dual signature, the bank simply needs to perform the following:
1) H [ H (PI) || OIMD]
2) Decrypt the dual signature using the customer public key.
The merchant can obtain the customer public key for the customer's certificate. The values from (1) and (2) should be equal.
General Steps
According to the Data Security for e-Transaction website the general steps for the SET are:
- Customer to Merchant
- Customer sends both the order and payment details to the merchant, together with his certificate.
- The payment details will be encrypted; merchant will not be able to read the payment details.
- The merchant uses the customer certificate to verify the customer.
- Merchant to Customer's Bank
- Merchant will send this payment details to his bank who will then forward it to the customer's bank to request authorization that the customer has sufficient available credit for the purchase.
- Confirmation of Order
- Once the authorization is received, the merchant will send an order confirmation to the customer.
- Shipping of Goods
- Upon confirmation by the customer, the merchant will deliver the goods to the customer
- Request for Payment By Merchant
- Lastly, the bank makes a request to the customer's credit card bank for payment.
See Also
Public Key Encryption Algorithms
External links
Data Security for e-Transaction
SET Electronic Transmission Protocol
Secure Electronic Transactions
References
- Data Security for e-Transaction. Retrieved on April 12th 2008, from <http://www.comp.nus.edu.sg/~jervis/cs3235/set.html>
- SET Electronic Transmission Protocol. Retrieved on April 12th 2008, from <http://www.samconline.com/samc/6340/Chapter-11-e-commerce/sld014.htm>
--Nobrem 21:30, 13 April 2008 (EDT)