SSH Tunneling
From Computing and Software Wiki
Tunneling refers to a packet, which is based on one protocol, being wrapped, or encapsulated, in a second packet that is based on another protocol. The encapsulating packet's protocol will be whatever differing protocol is needed in order for it to travel over an intermediary network. An SSH tunnel is an encrypted network tunnel created using an SSH connection. This type of tunnel allows you to transmit otherwise insecure TCP traffic in a secure fashion, as well as transfer packets with incompatible protocols over an intermediary network. When a tunneling protocol uses data encryption (SSH) to transport packets that are based on insecure protocols over the Internet, they are in essence providing VPN functionality.
Contents |
Components of a tunnel
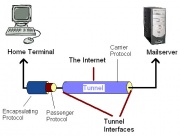
The Tunnel - The series of networks that the packet must travel to go from the starting network to the destination network.
Tunnel Interfaces - These are the points where the starting and destination networks comes into contact with the tunnel.
The Tunneling Process
In tunneling, a packet based on one protocol is wrapped, or encapsulated, in a second packet based on whatever differing protocol is needed in order for it to travel over an intermediary network. In effect, the second wrapper "insulates" the original packet and creates the illusion of a tunnel through which the wrapped packet travels across the intermediary network. In real-life terms, tunneling is comparable to "encapsulating" a present (the original packet) in a box (the secondary wrapper) for delivery through the postal system.
Application
A typical use would be to securely retrieve e-mail from work, while sitting at home, using a POP client. By connecting to the machine directly, you would be sending your login and password in the open and risk having them stolen to be subsequently used to gain access to confidential information.
To avoid this, instead of connecting directly, establish an SSH connection to the network of which the mail server is a part of. The SSH client software sets up a port forwarding mechanism, making the traffic heading to your home computer's POP be forwarded over the encrypted tunnel and end up at the mail server's POP port. You then direct your email client to your local POP port and it thinks that it is talking to the remote end, only this time, the entire session is encrypted. Anyone trying to listen in on the conversation between your home computer and work machine, will hear something resembling noise.
Implications???
History?
Refrences
See Also
External links
--Partsea 07:16, 9 April 2008 (EDT)