SSH Tunneling
From Computing and Software Wiki
| Line 1: | Line 1: | ||
| - | Tunneling is | + | Tunneling refers to a packet, that is based on one protocol, being wrapped, or encapsulated, in a second packet based on whatever differing protocol is needed in order for it to travel over an intermediary network. This process allows you to transmit otherwise insecure TCP traffic in a secure fashion. An SSH tunnel is an encrypted network tunnel created using an SSH connection. This type of tunnel is more commonly known as a VPN. |
== Components of a tunnel == | == Components of a tunnel == | ||
| Line 5: | Line 5: | ||
[[Image:wiki img.jpg|right|thumb|Tunneling Components]] | [[Image:wiki img.jpg|right|thumb|Tunneling Components]] | ||
| - | + | '''The Tunnel -''' The series of networks that the packet must travel to go from the starting network to the destination network. This is simply the Internet. | |
| + | |||
| + | '''Tunnel Interfaces -''' These are the points where the starting and destination networks comes into contact with the tunnel. | ||
| + | |||
| + | |||
== The Tunneling Process == | == The Tunneling Process == | ||
Revision as of 11:54, 9 April 2008
Tunneling refers to a packet, that is based on one protocol, being wrapped, or encapsulated, in a second packet based on whatever differing protocol is needed in order for it to travel over an intermediary network. This process allows you to transmit otherwise insecure TCP traffic in a secure fashion. An SSH tunnel is an encrypted network tunnel created using an SSH connection. This type of tunnel is more commonly known as a VPN.
Contents |
Components of a tunnel
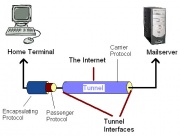
The Tunnel - The series of networks that the packet must travel to go from the starting network to the destination network. This is simply the Internet.
Tunnel Interfaces - These are the points where the starting and destination networks comes into contact with the tunnel.
The Tunneling Process
In tunneling, a packet based on one protocol is wrapped, or encapsulated, in a second packet based on whatever differing protocol is needed in order for it to travel over an intermediary network. In effect, the second wrapper "insulates" the original packet and creates the illusion of a tunnel through which the wrapped packet travels across the intermediary network. In real-life terms, tunneling is comparable to "encapsulating" a present (the original packet) in a box (the secondary wrapper) for delivery through the postal system.
Applications
Implications???
Refrences
See Also
External links
--Partsea 07:16, 9 April 2008 (EDT)