SSH Tunneling
From Computing and Software Wiki
(New page: Tunneling, also known as port forwarding, is the process by which one network is able to send its data via another network's connections. This process allows you to forward otherwise insec...) |
|||
| Line 4: | Line 4: | ||
== Components of a tunnel == | == Components of a tunnel == | ||
| - | + | [[Image:wiki img.jpg]] | |
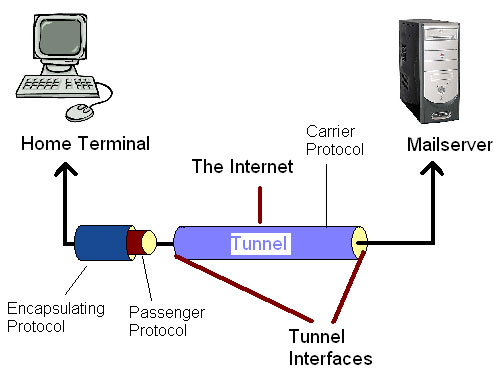
In tunneling, a packet based on one protocol is wrapped, or encapsulated, in a second packet based on whatever differing protocol is needed in order for it to travel over an intermediary network. In effect, the second wrapper "insulates" the original packet and creates the illusion of a tunnel through which the wrapped packet travels across the intermediary network. In real-life terms, tunneling is comparable to "encapsulating" a present (the original packet) in a box (the secondary wrapper) for delivery through the postal system. | In tunneling, a packet based on one protocol is wrapped, or encapsulated, in a second packet based on whatever differing protocol is needed in order for it to travel over an intermediary network. In effect, the second wrapper "insulates" the original packet and creates the illusion of a tunnel through which the wrapped packet travels across the intermediary network. In real-life terms, tunneling is comparable to "encapsulating" a present (the original packet) in a box (the secondary wrapper) for delivery through the postal system. | ||
Revision as of 10:38, 9 April 2008
Tunneling, also known as port forwarding, is the process by which one network is able to send its data via another network's connections. This process allows you to forward otherwise insecure TCP traffic through a secure shell.
Components of a tunnel
In tunneling, a packet based on one protocol is wrapped, or encapsulated, in a second packet based on whatever differing protocol is needed in order for it to travel over an intermediary network. In effect, the second wrapper "insulates" the original packet and creates the illusion of a tunnel through which the wrapped packet travels across the intermediary network. In real-life terms, tunneling is comparable to "encapsulating" a present (the original packet) in a box (the secondary wrapper) for delivery through the postal system.