Rootkits
From Computing and Software Wiki
| (6 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
'''Rootkits''' are software which provide remote access to resources without the owner's knowledge. They are considered the most technically sophisticated form of malware.<sup>[1]</sup> Rootkits are available for many different operating systems including Windows, Linux, Mac OS and others. Rootkits can have both malicious and legitimate uses. Law enforcement and child protection programs use various forms of rootkits to monitor the use of a system. Rootkits have become most known for their application with malicious intent. Hackers can use rootkits to take control of a users computer and use it for any intents they wish. | '''Rootkits''' are software which provide remote access to resources without the owner's knowledge. They are considered the most technically sophisticated form of malware.<sup>[1]</sup> Rootkits are available for many different operating systems including Windows, Linux, Mac OS and others. Rootkits can have both malicious and legitimate uses. Law enforcement and child protection programs use various forms of rootkits to monitor the use of a system. Rootkits have become most known for their application with malicious intent. Hackers can use rootkits to take control of a users computer and use it for any intents they wish. | ||
== How a Rootkit works == | == How a Rootkit works == | ||
| - | [[Image:rootkit.gif|thumb|500px|<center>How a rootkit avoids detection</center>]] | + | [[Image:rootkit.gif|thumb|500px|<center>How a rootkit avoids detection |
| + | |||
| + | Source: Downloaded from http://www.zillablog.com/2008/05/21/rootkits-a-growing-threat</center>]] | ||
Rootkits work by hijacking different levels of a computer system. For example a rootkit existing on the kernel level will intercept a call to open() and execute its own code. Rookits avoid detection in a similar manner. As seen in the figure to the right a rootkit will avoid detection by intercepting system calls to list directories. A virus scanner will make an operating system call to list the files in a particular directory whose actual contents include; Good.exe, Good.exe, Bad.exe, and Bad.exe, where the Bad.exe files are the rootkit executables. The rootkit will intercept the system call and return only the Good.exe files, therefore the virus scanner will have no knowledge of the existence of the rootkits, as they were implemented in the operating system level.<sup>[2]</sup> | Rootkits work by hijacking different levels of a computer system. For example a rootkit existing on the kernel level will intercept a call to open() and execute its own code. Rookits avoid detection in a similar manner. As seen in the figure to the right a rootkit will avoid detection by intercepting system calls to list directories. A virus scanner will make an operating system call to list the files in a particular directory whose actual contents include; Good.exe, Good.exe, Bad.exe, and Bad.exe, where the Bad.exe files are the rootkit executables. The rootkit will intercept the system call and return only the Good.exe files, therefore the virus scanner will have no knowledge of the existence of the rootkits, as they were implemented in the operating system level.<sup>[2]</sup> | ||
== Types of Rootkits == | == Types of Rootkits == | ||
=== User-Mode === | === User-Mode === | ||
| - | User-Mode rootkits are given administrative privileges on the computer they run on. They are able to modify any files and resources and will start whenever the computer boots. User-Mode rootkits are the easiest to be detected by rootkit detection software. | + | User-Mode rootkits are given administrative privileges on the computer they run on. They are able to modify any files and resources and will start whenever the computer boots. User-Mode rootkits are the easiest to be detected by rootkit detection software. <sup>[3]</sup> |
=== Kernel-Mode === | === Kernel-Mode === | ||
| - | Rootkits running in kernel mode run at the same level as the operating system. The rootkit is integrated into the operating system and is concealed behind operating system application programming interfaces. Kernel level rootkits disguise themselves by interrupting system calls and returning expected information concealing their presence. Kernel level rootkits often experience stability issues as they are operating at the OS level they generally bring down the entire system if they fail. | + | Rootkits running in kernel mode run at the same level as the operating system. The rootkit is integrated into the operating system and is concealed behind operating system application programming interfaces. Kernel level rootkits disguise themselves by interrupting system calls and returning expected information concealing their presence. Kernel level rootkits often experience stability issues as they are operating at the OS level they generally bring down the entire system if they fail. <sup>[4]</sup> |
=== User/Kernel Hybrid === | === User/Kernel Hybrid === | ||
| - | Hybrid rootkits attempt to combine both the stealthy aspects of kernel level and the stability of user level rootkits. This style of rootkit in one of the most common in existence currently. | + | Hybrid rootkits attempt to combine both the stealthy aspects of kernel level and the stability of user level rootkits. This style of rootkit in one of the most common in existence currently.<sup>[5]</sup> |
=== Firmware Level === | === Firmware Level === | ||
| - | Firmware level rootkits are very difficult to detect and remove. Firmware rootkits hide themselves in the firmware of the hardware components of the system. Firmware rootkits are able to reinstall themselves on booting. Certain hard disk rootkits have been found that are capable of reinstalling themselves after a complete system formatting and installation. < | + | Firmware level rootkits are very difficult to detect and remove. Firmware rootkits hide themselves in the firmware of the hardware components of the system. Firmware rootkits are able to reinstall themselves on booting. Certain hard disk rootkits have been found that are capable of reinstalling themselves after a complete system formatting and installation. <sup>[6]</sup> |
=== Virtual Level === | === Virtual Level === | ||
| - | Virtual level rootkits attempt to emulate hardware through the use of software. They operate in a manner similar to virtualization software such as VMWare. Virtual level rootkits are very complex to create and as such there have been limited known virtual level rootkits found running. <ref> | + | Virtual level rootkits attempt to emulate hardware through the use of software. They operate in a manner similar to virtualization software such as VMWare. Virtual level rootkits are very complex to create and as such there have been limited known virtual level rootkits found running.<sup>[7]</sup> <ref></ref> |
== Examples == | == Examples == | ||
=== Sony BMG === | === Sony BMG === | ||
| - | Sony made headlines in late 2005 when it was discovered that they were using a rootkit to hide their Digital Rights Management (DRM) software designed to prevent music piracy on users computers. The Sony code would hide under the Operating System level and would secretly send data back to Sony concerning activity on the users computer. The Sony rootkit left large security holes in the windows operating system, hackers could easily create patches for the sony root kit that would allow them to gain control of the users system. The incident resulted in lawsuits against sony and resulted in them having to pull CDs which contained the rootkit off the shelves. | + | Sony made headlines in late 2005 when it was discovered that they were using a rootkit to hide their Digital Rights Management (DRM) software designed to prevent music piracy on users computers. The Sony code would hide under the Operating System level and would secretly send data back to Sony concerning activity on the users computer. The Sony rootkit left large security holes in the windows operating system, hackers could easily create patches for the sony root kit that would allow them to gain control of the users system. The incident resulted in lawsuits against sony and resulted in them having to pull CDs which contained the rootkit off the shelves. <sup>[8]</sup> |
=== Other Examples === | === Other Examples === | ||
| - | Other examples of rootkits with a malicious intent include; ''NTRootkit'', ''HackerDefender'', ''AFXRootkit'', ''FURootkit'', these are among the most prevalent today. Rootkits are often embedded in other forms of malware, rookits have been found to be included known malware including; ''Backdoor-CEB'', ''AdClicker-BA'', ''W32/Feebs'', ''Backdoor-CTV'', ''Qoolaid'', ''PWS-LDPinch'', ''Opanki.worm'', and ''W32/Sdbot.worm''. | + | Other examples of rootkits with a malicious intent include; ''NTRootkit'', ''HackerDefender'', ''AFXRootkit'', ''FURootkit'', these are among the most prevalent today. Rootkits are often embedded in other forms of malware, rookits have been found to be included known malware including; ''Backdoor-CEB'', ''AdClicker-BA'', ''W32/Feebs'', ''Backdoor-CTV'', ''Qoolaid'', ''PWS-LDPinch'', ''Opanki.worm'', and ''W32/Sdbot.worm''. <sup>[9]</sup> |
== Detection == | == Detection == | ||
| - | As seen from the above descriptions, rootkits can be very difficult to detect. Some naive rootkits usually at the user-level can be detected using a basic signature verification, however for rootkits at the kernel level or lower this approach is often ineffective as was discussed above. For rootkits at the kernel the best approach is generally to boot the system into a live operating system and then run some rootkit detection software. There are numerous applications designed to detect rootkits including; RootkitRevealer from Microsoft, Sophos Anti-Rootkit, and BlackLight from F-Secure. There also exists a number of rootkit detection application for linux including; chkrootkit, and rkhunter. All of these applications use different techniques to detect rootkits, they have varying degrees of success depending on the type of rootkit and the system being operated on. | + | As seen from the above descriptions, rootkits can be very difficult to detect. Some naive rootkits usually at the user-level can be detected using a basic signature verification, however for rootkits at the kernel level or lower this approach is often ineffective as was discussed above. For rootkits at the kernel the best approach is generally to boot the system into a live operating system and then run some rootkit detection software. There are numerous applications designed to detect rootkits including; RootkitRevealer from Microsoft, Sophos Anti-Rootkit, and BlackLight from F-Secure. There also exists a number of rootkit detection application for linux including; chkrootkit, and rkhunter. All of these applications use different techniques to detect rootkits, they have varying degrees of success depending on the type of rootkit and the system being operated on. <sup>[10]</sup> |
== Removal == | == Removal == | ||
Rootkits can be difficult to remove for the same reasons that they are difficult to detect. Lower level rootkits can intercept a delete call and return a false result to the user. Commercial solutions have limited success removing rootkits, however it is recommend to try them first. If existing removal applications do not work more drastic steps are required. For kernel, user, and virtual rootkits often the most effective and efficient solution is to reinstall the operating system. For firmware re-flashing or replacing hardware is often the most efficient way to remove rootkits. | Rootkits can be difficult to remove for the same reasons that they are difficult to detect. Lower level rootkits can intercept a delete call and return a false result to the user. Commercial solutions have limited success removing rootkits, however it is recommend to try them first. If existing removal applications do not work more drastic steps are required. For kernel, user, and virtual rootkits often the most effective and efficient solution is to reinstall the operating system. For firmware re-flashing or replacing hardware is often the most efficient way to remove rootkits. | ||
| Line 27: | Line 29: | ||
# What is a Rootkit? Mar 15, 2006. Available at [http://www.pcmech.com/article/what-is-a-rootkit/ http://www.pcmech.com/article/what-is-a-rootkit/] | # What is a Rootkit? Mar 15, 2006. Available at [http://www.pcmech.com/article/what-is-a-rootkit/ http://www.pcmech.com/article/what-is-a-rootkit/] | ||
# Rootkits a Growing Threat. May 21, 2008. Available at [http://www.zillablog.com/2008/05/21/rootkits-a-growing-threat/ http://www.zillablog.com/2008/05/21/rootkits-a-growing-threat/] | # Rootkits a Growing Threat. May 21, 2008. Available at [http://www.zillablog.com/2008/05/21/rootkits-a-growing-threat/ http://www.zillablog.com/2008/05/21/rootkits-a-growing-threat/] | ||
| + | # All about rootkits. October 28, 2008. Available at [http://techinfo.co.in/wordpress/?p=174 http://techinfo.co.in/wordpress/?p=174] | ||
| + | # Ibid. | ||
| + | # Ibid. | ||
| + | # Newfangled rootkits survive hard disk wiping by Dan Goodin. Mar 24, 2009. Available at http://www.theregister.co.uk/2009/03/24/persistent_bios_rootkits/ | ||
| + | # Implementing malware with virtual machines by Samuel T. King. et al. Available at http://www.eecs.umich.edu/virtual/papers/king06.pdf | ||
| + | # Sony CD protection sparks security concerns by John Borland. Nov 17, 2005. Available at http://news.cnet.com/2100-7355_3-5926657.html | ||
| + | # Rootkits, Part 1 of 3: The Growing Threat by McAfee. Available at http://www.mcafee.com/us/local_content/white_papers/threat_center/wp_akapoor_rootkits1_en.pdf | ||
| + | # Rootkit Information and Detection Available at http://antivirus.about.com/od/rootkits/Rootkit_Information_and_Detection.htm | ||
== See Also == | == See Also == | ||
*[[Malware]] | *[[Malware]] | ||
*[[Computer Worms]] | *[[Computer Worms]] | ||
== External Links == | == External Links == | ||
| - | [http://techinfo.co.in/wordpress/?p=174 All about rootkits] | + | *[http://techinfo.co.in/wordpress/?p=174 All about rootkits] |
| - | + | *[http://en.wikipedia.org/wiki/Rootkit Wikipedia: Rootkit] | |
| - | [http://en.wikipedia.org/wiki/Rootkit Wikipedia: Rootkit] | + | *[http://staff.washington.edu/dittrich/misc/faqs/rootkits.faq Rootkit FAQ] |
| - | + | ||
--[[User:Elesc|Elesc]] 14:02, 9 April 2009 (EDT) | --[[User:Elesc|Elesc]] 14:02, 9 April 2009 (EDT) | ||
Current revision as of 20:04, 10 April 2009
Rootkits are software which provide remote access to resources without the owner's knowledge. They are considered the most technically sophisticated form of malware.[1] Rootkits are available for many different operating systems including Windows, Linux, Mac OS and others. Rootkits can have both malicious and legitimate uses. Law enforcement and child protection programs use various forms of rootkits to monitor the use of a system. Rootkits have become most known for their application with malicious intent. Hackers can use rootkits to take control of a users computer and use it for any intents they wish.
Contents |
How a Rootkit works
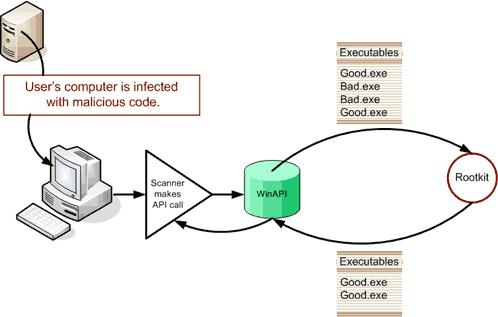
Rootkits work by hijacking different levels of a computer system. For example a rootkit existing on the kernel level will intercept a call to open() and execute its own code. Rookits avoid detection in a similar manner. As seen in the figure to the right a rootkit will avoid detection by intercepting system calls to list directories. A virus scanner will make an operating system call to list the files in a particular directory whose actual contents include; Good.exe, Good.exe, Bad.exe, and Bad.exe, where the Bad.exe files are the rootkit executables. The rootkit will intercept the system call and return only the Good.exe files, therefore the virus scanner will have no knowledge of the existence of the rootkits, as they were implemented in the operating system level.[2]
Types of Rootkits
User-Mode
User-Mode rootkits are given administrative privileges on the computer they run on. They are able to modify any files and resources and will start whenever the computer boots. User-Mode rootkits are the easiest to be detected by rootkit detection software. [3]
Kernel-Mode
Rootkits running in kernel mode run at the same level as the operating system. The rootkit is integrated into the operating system and is concealed behind operating system application programming interfaces. Kernel level rootkits disguise themselves by interrupting system calls and returning expected information concealing their presence. Kernel level rootkits often experience stability issues as they are operating at the OS level they generally bring down the entire system if they fail. [4]
User/Kernel Hybrid
Hybrid rootkits attempt to combine both the stealthy aspects of kernel level and the stability of user level rootkits. This style of rootkit in one of the most common in existence currently.[5]
Firmware Level
Firmware level rootkits are very difficult to detect and remove. Firmware rootkits hide themselves in the firmware of the hardware components of the system. Firmware rootkits are able to reinstall themselves on booting. Certain hard disk rootkits have been found that are capable of reinstalling themselves after a complete system formatting and installation. [6]
Virtual Level
Virtual level rootkits attempt to emulate hardware through the use of software. They operate in a manner similar to virtualization software such as VMWare. Virtual level rootkits are very complex to create and as such there have been limited known virtual level rootkits found running.[7] <ref></ref>
Examples
Sony BMG
Sony made headlines in late 2005 when it was discovered that they were using a rootkit to hide their Digital Rights Management (DRM) software designed to prevent music piracy on users computers. The Sony code would hide under the Operating System level and would secretly send data back to Sony concerning activity on the users computer. The Sony rootkit left large security holes in the windows operating system, hackers could easily create patches for the sony root kit that would allow them to gain control of the users system. The incident resulted in lawsuits against sony and resulted in them having to pull CDs which contained the rootkit off the shelves. [8]
Other Examples
Other examples of rootkits with a malicious intent include; NTRootkit, HackerDefender, AFXRootkit, FURootkit, these are among the most prevalent today. Rootkits are often embedded in other forms of malware, rookits have been found to be included known malware including; Backdoor-CEB, AdClicker-BA, W32/Feebs, Backdoor-CTV, Qoolaid, PWS-LDPinch, Opanki.worm, and W32/Sdbot.worm. [9]
Detection
As seen from the above descriptions, rootkits can be very difficult to detect. Some naive rootkits usually at the user-level can be detected using a basic signature verification, however for rootkits at the kernel level or lower this approach is often ineffective as was discussed above. For rootkits at the kernel the best approach is generally to boot the system into a live operating system and then run some rootkit detection software. There are numerous applications designed to detect rootkits including; RootkitRevealer from Microsoft, Sophos Anti-Rootkit, and BlackLight from F-Secure. There also exists a number of rootkit detection application for linux including; chkrootkit, and rkhunter. All of these applications use different techniques to detect rootkits, they have varying degrees of success depending on the type of rootkit and the system being operated on. [10]
Removal
Rootkits can be difficult to remove for the same reasons that they are difficult to detect. Lower level rootkits can intercept a delete call and return a false result to the user. Commercial solutions have limited success removing rootkits, however it is recommend to try them first. If existing removal applications do not work more drastic steps are required. For kernel, user, and virtual rootkits often the most effective and efficient solution is to reinstall the operating system. For firmware re-flashing or replacing hardware is often the most efficient way to remove rootkits.
References
- What is a Rootkit? Mar 15, 2006. Available at http://www.pcmech.com/article/what-is-a-rootkit/
- Rootkits a Growing Threat. May 21, 2008. Available at http://www.zillablog.com/2008/05/21/rootkits-a-growing-threat/
- All about rootkits. October 28, 2008. Available at http://techinfo.co.in/wordpress/?p=174
- Ibid.
- Ibid.
- Newfangled rootkits survive hard disk wiping by Dan Goodin. Mar 24, 2009. Available at http://www.theregister.co.uk/2009/03/24/persistent_bios_rootkits/
- Implementing malware with virtual machines by Samuel T. King. et al. Available at http://www.eecs.umich.edu/virtual/papers/king06.pdf
- Sony CD protection sparks security concerns by John Borland. Nov 17, 2005. Available at http://news.cnet.com/2100-7355_3-5926657.html
- Rootkits, Part 1 of 3: The Growing Threat by McAfee. Available at http://www.mcafee.com/us/local_content/white_papers/threat_center/wp_akapoor_rootkits1_en.pdf
- Rootkit Information and Detection Available at http://antivirus.about.com/od/rootkits/Rootkit_Information_and_Detection.htm
See Also
External Links
--Elesc 14:02, 9 April 2009 (EDT)
