Rootkits
From Computing and Software Wiki
(Difference between revisions)
| Line 1: | Line 1: | ||
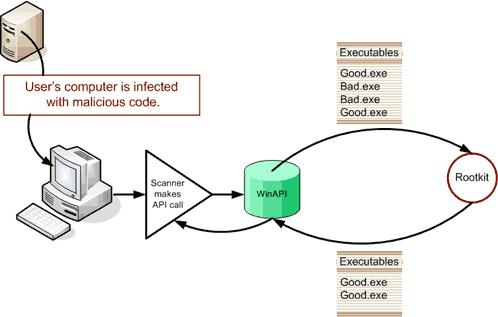
| - | Rootkits are software which provide remote access to resources without the owner's knowledge. Rootkits are available for many different operating systems including Windows, Linux, Mac OS and others. Rootkits can have both malicious and legitimate uses. Law enforcement and child protection programs use various forms of rootkits to monitor the use of a system. Rootkits have become most known for their application with malicious intent. Hackers can use rootkits to take control of a users computer and use it for any intents they wish. | + | [[Image:rootkit.gif|thumb|500px|<center>How a rootkit avoids detections</center>]] |
| + | |||
| + | '''Rootkits''' are software which provide remote access to resources without the owner's knowledge. Rootkits are available for many different operating systems including Windows, Linux, Mac OS and others. Rootkits can have both malicious and legitimate uses. Law enforcement and child protection programs use various forms of rootkits to monitor the use of a system. Rootkits have become most known for their application with malicious intent. Hackers can use rootkits to take control of a users computer and use it for any intents they wish. | ||
== Types of Rootkits == | == Types of Rootkits == | ||
Revision as of 19:22, 9 April 2009
Rootkits are software which provide remote access to resources without the owner's knowledge. Rootkits are available for many different operating systems including Windows, Linux, Mac OS and others. Rootkits can have both malicious and legitimate uses. Law enforcement and child protection programs use various forms of rootkits to monitor the use of a system. Rootkits have become most known for their application with malicious intent. Hackers can use rootkits to take control of a users computer and use it for any intents they wish.
Contents |
Types of Rootkits
User-Mode
Kernal-Mode
User/Kernal Hybrid
Firmware Level
Virtual Level
Detection
Removal
References
See Also
External Links
--Elesc 14:02, 9 April 2009 (EDT)