Public Key Authentication
From Computing and Software Wiki
| (14 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
| - | '''Public key authentication''' is a process | + | '''Public key authentication''', also known as '''asymmetric-key encryption''' is a cryptographic process that involves the generation of a key pair; a public key and a private key for encryption and decryption of messages, as well as the verification of a user's identity on a server. The private key is kept secret on the user's system who generated it, while the public key is distributed to any user or server with which the user wishes to communicate. |
| - | + | ||
| - | + | Messages are encrypted using the public key, and may only be decrypted by the corresponding private key. In this way, possession of the private key is required for the message to be read and third parties are prevented from intercepting the message. Similarly, the private key can generate unique signatures that could only have come from that specific private key. Using the matching public key a server can verify the signature provided and therefore the user's identity. | |
| - | + | ||
| - | + | [[Image:key.jpg|thumb|500px|right|Public Key Authentication]] | |
| - | + | ||
| - | + | ||
| - | + | ||
==Background== | ==Background== | ||
| - | + | The idea behind the use public keys is to create a secure system of authentication which prevents third parties from hacking into one of the participants' systems and gaining access to any sensitive information that is transferred. The use of complex schemes to separately generate the private and public keys go a long way in preventing this from happening. Even though the public key is freely distributed, the key pair is generated in such a way that the private key cannot be derived should the public key fall into the wrong hands. Since the private key does all of the important work regarding sensitive material (decrypting messages, generating signatures to confirm identity) the public key is useless to those seeking to use it for malicious purposes. | |
| - | + | ||
| + | This is not the case with password-based authentication, also known as symmetric key authentication in which only the one password is used for all encryption. Should an attacker obtain this password, there is no telling the damage they can do. | ||
===Identity Verification Process=== | ===Identity Verification Process=== | ||
| + | |||
| + | [[Image:signature.jpg|thumb|350px|right|Process for verifying identity in public key authentication]] | ||
* Generate a key pair on your computer | * Generate a key pair on your computer | ||
* Copy your public key to the server | * Copy your public key to the server | ||
| Line 20: | Line 20: | ||
===Message Encryption/Decryption Process=== | ===Message Encryption/Decryption Process=== | ||
| + | |||
| + | [[Image:encrypt.jpg|thumb|350px|right|Process for encrypting and decrypting message in public key authentication]] | ||
* Generate a key pair on your computer | * Generate a key pair on your computer | ||
* Send your public key to the desired user you wish to communicate with | * Send your public key to the desired user you wish to communicate with | ||
| Line 26: | Line 28: | ||
* Recipient uses their private key to decrypt the message | * Recipient uses their private key to decrypt the message | ||
| - | ===Physical World | + | ===Physical World Equivalents=== |
| - | + | ||
| + | The process of message delivery in networking resembles the postal system of the physical world. Encryption of the messages themselves is like locking the parcel with a padlock. Using a symmetric key would involve a single padlock with each user possessing an identical copy of the key used to open that padlock. | ||
| + | |||
| + | Alternatively, the use of a public (asymmetric) key system is equivalent to each user purchasing their own key/padlock set and sending the padlock to the user with whom they wish to communicate. This second user would then use this received padlock to lock up any messages they wish to send. The first user then unlocks the padlock with the matching key that they remained in possession of the entire time.<sup>[1]</sup> | ||
| + | |||
| + | ==History== | ||
| + | |||
| + | Although the first asymmetric key algorithm was published in 1976 by Whitfield Diffie and Martin Hellman, a similar such cryptography had already been invented independently by James H. Ellis, Clifford Cocks, and Malcolm Williamson in the early 1970s due to the fact that Ellis, Cocks, and Williamson work was done for Britain's Government Communications Headquarters and was kept confidential until 1997.<sup>[1]</sup> | ||
| + | |||
| + | These were soon followed by the invention of the RSA algorithm by Ron Rivest, Adi Shamir, and Leonard Adleman in 1977 as well many more schemes over the previous three decades.<sup>[1]</sup> | ||
==Benefits== | ==Benefits== | ||
| - | + | ||
| - | + | ===Hacked Server=== | |
| - | + | ||
| + | One advantage the public key authentication possesses over those that are password-based is when the server has been hacked or spoofed. In systems that use symmetric keys for authentication, the attacker can learn your password and proceed to pose as you in the future. Alternatively, if a server using public key authentication is hacked the signature sent to the server would mean nothing to the attacker. Without the private key, the attacker cannot impersonate you.<sup>[2]</sup> | ||
| + | |||
| + | ===Brute Force Attacks=== | ||
| + | |||
| + | While brute force attacks are still possible in public key authentication given unlimited computational power of the attacker, the length and complexity of the keys generated in these algorithms make attacks by power limited threats very time consuming to the point that the information is no longer useful by the time the attacker has cracked the encryption. | ||
==Drawbacks== | ==Drawbacks== | ||
| - | + | ||
| - | + | Although brute force attacks are generally ineffective against systems using public key authentication, there are other attacks that are capable of breaking the keys. | |
| + | |||
| + | The same beneficial length of the generated keys that make them hard to crack by brute force attacks also cause the computational costs of using these algorithms to be much greater than the costs required in symmetric key algorithms. As a result, there are hybrid systems that use a public key to allow users to join a confidential session. Once the users have been granted access to the session, future messages are encrypted using symmetric keys to save on computational power. | ||
==Public Key Algorithms== | ==Public Key Algorithms== | ||
| - | * RSA | + | |
| - | * DSA/DSS (Digital Signature Standard) | + | There are many different algorithms that can be used to generate the private and public keys in asymmetric key authentication.<sup>[3, 4]</sup> The RSA and Diffie-Hellman algorithms are the most commonly used algorithms in public key authentication.<sup>[4]</sup> |
| - | * | + | |
| + | * Primes | ||
| + | * Factoring | ||
| + | ** RSA (Rivest-Shamir-Adleman) algorithm | ||
| + | * Discrete Logarithms | ||
| + | ** Diffie-Hellman algorithm | ||
| + | ** DSA/DSS (Digital Signature Standard) algorithm | ||
| + | * Lattices | ||
| + | * [[Digital Signatures]] | ||
==References== | ==References== | ||
| - | + | ||
| - | + | # "[http://en.wikipedia.org/wiki/Public-key_cryptography Public Key Cryptography]" 2009-04-05. | |
| + | # "[http://the.earth.li/~sgtatham/putty/0.55/htmldoc/Chapter8.html#S8.2.8 Using Public Keys for SSH Authentication]". Retrieved 2009-04-05. | ||
| + | # [http://www.infosecwriters.com/text_resources/pdf/Public_Key_Cryptography_AMS.pdf Public Key Cryptography: Applications Algorithms and Mathematical Explanations], Anoop MS (2007). | ||
| + | # "[http://www.ssh.com/support/cryptography/algorithms/asymmetric.html Public Key Cryptosystems: Asymmetric Ciphers]". Retrieved 2009-04-05. | ||
==See Also== | ==See Also== | ||
| + | |||
| + | * [[Digital Signatures]] | ||
==External Links== | ==External Links== | ||
| - | --[[User:larocqt|larocqt]] | + | * [http://computer.howstuffworks.com/encryption3.htm Public Key Encryption] at HowStuffWorks.com |
| + | |||
| + | |||
| + | --[[User:larocqt|larocqt]] 11:18 AM, 11 April 2009 (EDT) | ||
Current revision as of 15:20, 11 April 2009
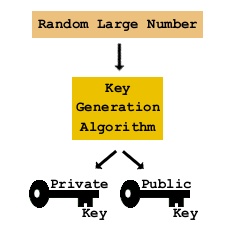
Public key authentication, also known as asymmetric-key encryption is a cryptographic process that involves the generation of a key pair; a public key and a private key for encryption and decryption of messages, as well as the verification of a user's identity on a server. The private key is kept secret on the user's system who generated it, while the public key is distributed to any user or server with which the user wishes to communicate.
Messages are encrypted using the public key, and may only be decrypted by the corresponding private key. In this way, possession of the private key is required for the message to be read and third parties are prevented from intercepting the message. Similarly, the private key can generate unique signatures that could only have come from that specific private key. Using the matching public key a server can verify the signature provided and therefore the user's identity.
Contents |
Background
The idea behind the use public keys is to create a secure system of authentication which prevents third parties from hacking into one of the participants' systems and gaining access to any sensitive information that is transferred. The use of complex schemes to separately generate the private and public keys go a long way in preventing this from happening. Even though the public key is freely distributed, the key pair is generated in such a way that the private key cannot be derived should the public key fall into the wrong hands. Since the private key does all of the important work regarding sensitive material (decrypting messages, generating signatures to confirm identity) the public key is useless to those seeking to use it for malicious purposes.
This is not the case with password-based authentication, also known as symmetric key authentication in which only the one password is used for all encryption. Should an attacker obtain this password, there is no telling the damage they can do.
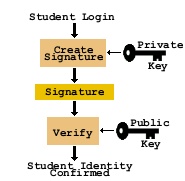
Identity Verification Process
- Generate a key pair on your computer
- Copy your public key to the server
- When authentication is required, a signature is generated using the private key
- Server uses the public key to verify the signature and grant access
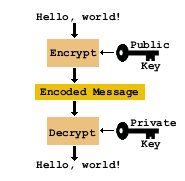
Message Encryption/Decryption Process
- Generate a key pair on your computer
- Send your public key to the desired user you wish to communicate with
- Recipient may generate their own key pair
- Sender uses the recipient's public key to encrypt the message and sends it
- Recipient uses their private key to decrypt the message
Physical World Equivalents
The process of message delivery in networking resembles the postal system of the physical world. Encryption of the messages themselves is like locking the parcel with a padlock. Using a symmetric key would involve a single padlock with each user possessing an identical copy of the key used to open that padlock.
Alternatively, the use of a public (asymmetric) key system is equivalent to each user purchasing their own key/padlock set and sending the padlock to the user with whom they wish to communicate. This second user would then use this received padlock to lock up any messages they wish to send. The first user then unlocks the padlock with the matching key that they remained in possession of the entire time.[1]
History
Although the first asymmetric key algorithm was published in 1976 by Whitfield Diffie and Martin Hellman, a similar such cryptography had already been invented independently by James H. Ellis, Clifford Cocks, and Malcolm Williamson in the early 1970s due to the fact that Ellis, Cocks, and Williamson work was done for Britain's Government Communications Headquarters and was kept confidential until 1997.[1]
These were soon followed by the invention of the RSA algorithm by Ron Rivest, Adi Shamir, and Leonard Adleman in 1977 as well many more schemes over the previous three decades.[1]
Benefits
Hacked Server
One advantage the public key authentication possesses over those that are password-based is when the server has been hacked or spoofed. In systems that use symmetric keys for authentication, the attacker can learn your password and proceed to pose as you in the future. Alternatively, if a server using public key authentication is hacked the signature sent to the server would mean nothing to the attacker. Without the private key, the attacker cannot impersonate you.[2]
Brute Force Attacks
While brute force attacks are still possible in public key authentication given unlimited computational power of the attacker, the length and complexity of the keys generated in these algorithms make attacks by power limited threats very time consuming to the point that the information is no longer useful by the time the attacker has cracked the encryption.
Drawbacks
Although brute force attacks are generally ineffective against systems using public key authentication, there are other attacks that are capable of breaking the keys.
The same beneficial length of the generated keys that make them hard to crack by brute force attacks also cause the computational costs of using these algorithms to be much greater than the costs required in symmetric key algorithms. As a result, there are hybrid systems that use a public key to allow users to join a confidential session. Once the users have been granted access to the session, future messages are encrypted using symmetric keys to save on computational power.
Public Key Algorithms
There are many different algorithms that can be used to generate the private and public keys in asymmetric key authentication.[3, 4] The RSA and Diffie-Hellman algorithms are the most commonly used algorithms in public key authentication.[4]
- Primes
- Factoring
- RSA (Rivest-Shamir-Adleman) algorithm
- Discrete Logarithms
- Diffie-Hellman algorithm
- DSA/DSS (Digital Signature Standard) algorithm
- Lattices
- Digital Signatures
References
- "Public Key Cryptography" 2009-04-05.
- "Using Public Keys for SSH Authentication". Retrieved 2009-04-05.
- Public Key Cryptography: Applications Algorithms and Mathematical Explanations, Anoop MS (2007).
- "Public Key Cryptosystems: Asymmetric Ciphers". Retrieved 2009-04-05.
See Also
External Links
- Public Key Encryption at HowStuffWorks.com
--larocqt 11:18 AM, 11 April 2009 (EDT)