Onion Routing
From Computing and Software Wiki
Onion Routing provides a way for two computers to communicate on a network anonymously. Onion routing focuses on hiding the source and destination addresses of a packet, rather than the contents of the packet In order for this to work, a message is encrypted and placed inside an 'onion'. The intermediate nodes along the path, called onion routers, decrypt (peel off a layer) of the onion to reveal the next router along the path to receive the onion. Onion routing runs on top of TCP [1].
Contents |
Onions
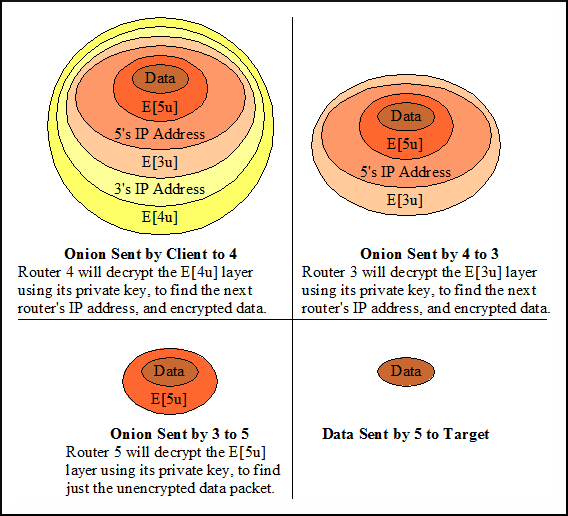
Onions are created by the sender of a message, who first determines the network path it wishes to send a message. Onions rely on Public Key Technology, where each router on the path has its own public key. The sender encrypts the message multiple times with the public keys of each of the intermediate routers. Starting with the public key of the last router on the path, and continually encrypting the message with the previous router's public key. The final message to be sent is encrypted with the public key of the first router in the path.
The concept of the onion data structure is based on the idea of 'peeling off' layers of the onion at each intermediate node to reveal information for that specific node.
The first router on the path decrypts the onion with its private key, which reveals the address of the second router on the path, and then sends the message to that address.
The newly 'peeled off' onion can now be decrypted by the the second router with its private key. This process is continued until the final onion router receives the encrypted message,
decrypts it with its private key to reveal the intended message encrypted by the sender. This message is finally sent to the recipient.
One limitation of using onions is that the sender must know the path to the recipient before a message can be sent.
Anonymous Communication
Once decrypted, each layer of the onion contains only the address of the next router. This way each router along the path knows only the previous hop and next hop addresses. Further, no router along the path, except the final router, knows the destination address of the packet.
If all of the routers of an Onion Network have built in protection against Eavesdropping and Traffic Analysis, and additional encryption of the contents of a message, then the network provides total anonymous and private communication between two parties.
Security
The onion datatype itself does not encrypt the actual content of the message, since it only focuses on anonymous destination and source addresses. Since the onion is encrypted up until the last (or exit) node, the content of the onion is relatively safe. However, once an onion leaves the exit node it is unencrypted, and if it is intercepted after leaving the exit node, it has no protection. The solution to this problem is to encrypt the data area of the message to be the deepest layer of the onion, such as using recipient's public key to encrypt the information, or any other type of encryption technique.
Traffic Analysis / Eavesdropping
Onion routing, by itself, has a certain level of protection against eavesdropping because as an onion is decrypted at each router, the onion coming in is physically different than the onion going out of that same router. There also can be measures added to protect against traffic analysis and eavesdropping, two examples are explained below.
Timing Analysis
In order to make it difficult for an observer to trace an onion's path, each onion router can perform timing alterations for outgoing onions. This strategy has each intermediate router wait a pseudo-random amount of time before sending out an onion. This way it makes it difficult for an observer tell which onion coming into a router corresponds to which onion going out.
Padding
Another measure for protecting against traffic analysis is to pad each onion with random data to make each onion have the same size. This makes distinguishing between different onions difficult since they all share the same size.
Denial of Service Attacks
Denial of Service (DoS) Attacks occur when a machine's resources are unavailable to its intended users by a perpetrator overloading the resources of the machine. Normal routers are vulnerable to DoS attacks by being flooded with incoming packets, resulting in them being overwhelmed with processing each packet and unable to route normal incoming packets properly. Onion routers are vulnerable to Denial of Service attacks even more so than normal routers because of the additional time it takes to decrypt the onion with its private key [1] This makes a DoS attack even easier to perform on an onion router requiring less resources on the perpetrator's part.
Tor
Tor is an open source implementation of onion routing written in the C programming language. Tor works at the TCP level.
A user runs an onion proxy, which connects to Tor. The onion proxy also presents a SOCKS interface to the client [1].
Tor provides anonymous use of services like instant messaging and Web browsing.
Tor is comprised of hundreds of onion routers run by volunteers, any of which are available to users of the Tor network.
See Also
Public Key Encryption Algorithms
Proxy Server
Denial Of Service Attacks
External Links
References
1. Onion Routing for Anonymous Communications. http://ntrg.cs.tcd.ie/undergrad/4ba2.05/group10/index.html.
2. Onion Routing. http://www.onion-router.net/Summary.html.
3. Onion Routing - Wikipedia. http://en.wikipedia.org/wiki/Onion_routing.