Man in the Middle Attack
From Computing and Software Wiki
| Line 5: | Line 5: | ||
==Example Attacks== | ==Example Attacks== | ||
| - | + | Historically, several different man in the middle attacks have been described. Perhaps the earliest reference is <ref>[A Weakness in the 4.2BSD Unix TCP/IP Software, Robert T. Morris, AT&T Bell Laboratories, February 1985]</ref> | |
Revision as of 07:46, 6 April 2009
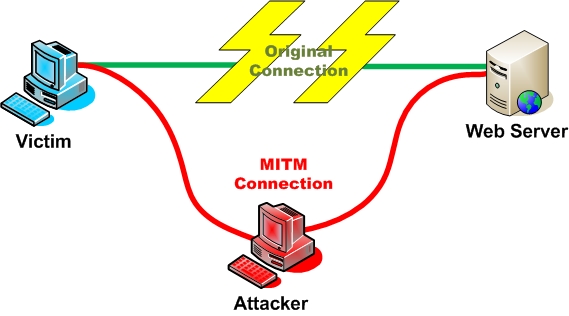
Man in the Middle Attacks (sometimes MITM) are attacks where the attacker intercepts communication between two parties, forwarding the communication as if the attacker were not present. The name is derived from the popular game Man in the Middle. It is also referred to as a fire-brigade or bucket brigade attack based on the method for putting out a fire. Lastly it is referred to as a Janus attack in reference to the roman two-headed god of gates.
Contents |
Example Attacks
Historically, several different man in the middle attacks have been described. Perhaps the earliest reference is <ref>[A Weakness in the 4.2BSD Unix TCP/IP Software, Robert T. Morris, AT&T Bell Laboratories, February 1985]</ref>
See Also
Information Security Topics:
- Mitnick Attack
- IP Spoofing
- Piggybacking
- Phishing
- Operating Systems Security
- Information security awareness
- Network stack (dode) - attack patterns on each layer & how to defend it
External Links
References
Template loop detected: Template:Reflist
--Heifetj 03:17, 6 April 2009 (EDT)