Keystroke Logging
From Computing and Software Wiki
(→External Links) |
|||
| (54 intermediate revisions not shown) | |||
| Line 2: | Line 2: | ||
Most importantly, various login names, passwords, and other keystrokes can be recorded, in which important data such as credit card or banking information can be leaked out. The history of key logging is relative to the ease at which a computer can become infected; a user can simply visit the wrong website and become infected. Therefore, as users become more dependant on the accessibility of online networking, new security measures must be taken to accommodate for the risks involved with the convenience. | Most importantly, various login names, passwords, and other keystrokes can be recorded, in which important data such as credit card or banking information can be leaked out. The history of key logging is relative to the ease at which a computer can become infected; a user can simply visit the wrong website and become infected. Therefore, as users become more dependant on the accessibility of online networking, new security measures must be taken to accommodate for the risks involved with the convenience. | ||
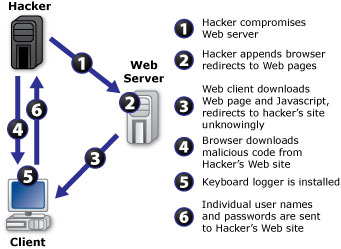
| - | [[Image:keystrokelogging.jpeg|frame|Keystroke Steps|right|Steps in | + | [[Image:keystrokelogging.jpeg|frame|Keystroke Steps|right|Steps in Keystroke Attack]] |
| - | Keystroke loggers can be applied using three different methods: software, hardware, or kernel-driven applications. Information collected from key logging typically include host-names, IP addresses, and GUID (globally unique identifiers). | + | Keystroke loggers can be applied using three different methods: software, hardware, or [http://en.wikipedia.org/wiki/Kernel_(computing) kernel]-driven applications. Information collected from key logging typically include host-names, IP addresses, and [http://en.wikipedia.org/wiki/Globally_Unique_Identifier GUID](globally unique identifiers). |
| Line 12: | Line 12: | ||
| - | Trojans, electronic spying, remote-computer monitoring, viruses, horses, and of course, keystroke logging, are all various threats openly available to everyone who uses computers; from gurus to illiterates. The question now lies on how well a user is protected against threats and attacks from malicious users. Hackers all around the world usually tend to communicate through the internet. Many have come together and formed their own websites that provide information about the world from the hackers’ point of view. One such site is www.antionline.com, another www.attrition.org. Even | + | [http://en.wikipedia.org/wiki/Trojan_horse_(computing) Trojans], electronic spying, remote-computer monitoring, viruses, horses, and of course, keystroke logging, are all various threats openly available to everyone who uses computers; from gurus to illiterates. The question now lies on how well a user is protected against threats and attacks from malicious users. Hackers all around the world usually tend to communicate through the internet. Many have come together and formed their own websites that provide information about the world from the hackers’ point of view. One such site is [http://www.antionline.com/ Anti-online], another [http://www.attrition.org/ Attrition.org]. Even websites such as these, ones created by hackers, for hackers, have been hacked at some point in time. Ever since these sites teamed up with law enforcement officials, they have been an outreach to hacking. They have been breached by some means of security so many times that logs have actually been posted of attempted hacks and threats. |
| Line 20: | Line 20: | ||
===Historic Example: PGP Case=== | ===Historic Example: PGP Case=== | ||
| + | Pretty Good Privacy (PGP) is a [[computer program]] that provides [[cryptographic]] [[privacy]] and [[authentication]]. PGP is often used for signing, encrypting and decrypting e-mails to increase the security of e-mail communications. It was originally created by [[Philip Zimmermann]] in 1991. | ||
| + | |||
| + | PGP and other similar products follow the [[OpenPGP]] standard (RFC 4880) for encrypting and decrypting data. | ||
| + | PGP and other similar products follow the OpenPGP standard (RFC 4880) for encrypting and decrypting data. | ||
| + | FBI officials have used the technique to gather evidence, such as the PGP case. In this example, the FBI needed a password in order to decrypt coded files that allegedly contained records of illegal gambling and loan-sharking operations. So FBI officials decided to break into the son of the illicit Philadelphia mob boss’s business, and put a program on his computer (or perhaps an electronic bug in his keyboard) to record all the keystrokes. | ||
| + | |||
| + | |||
| + | The keystroke logger was then used to obtain the [[Pretty Good Privacy|PGP]] [[passphrase]] of [[Nicodemo Scarfo, Jr.]], son of mob boss [[Nicodemo Scarfo]]. Scarfo Jr. pleaded guilty to running an illegal gambling operation in 2002.<ref>"Mobster's son pleads guilty of gambling; computer spying helped seal case" Associated Press, 1 Mar 2002</ref> The FBI has also reportedly developed a trojan-horse-delivered keylogger program known as [[Magic Lantern (software)|Magic Lantern]].<ref>http://www.msnbc.com/news/660096.asp?cp1=1</ref> | ||
| + | |||
| + | This is just one example of a historic case in which key logging was used to promote a positive gain. | ||
| - | |||
| Line 32: | Line 41: | ||
| - | + | “[http://en.wikipedia.org/wiki/Scotiabank Scotia Online®] is a protected environment that meets the highest Internet security standards. When you are signed onto Scotia Online, we take (additional) steps to protect your information” (Scotia Online). | |
Online banking certainly provides great convenience. It can save a lot of time for users by letting them check balances, transfer money between accounts, and pay bills. However, there are risks involved in this convenience. There are a number of different security techniques banks are using today to ensure that their clients have a secure connection to their online banking. However, no matter how secure a connection, with the right time, tools, and patience, anything can be hacked. That being said, the table below is a short list of some of the strategies used today. | Online banking certainly provides great convenience. It can save a lot of time for users by letting them check balances, transfer money between accounts, and pay bills. However, there are risks involved in this convenience. There are a number of different security techniques banks are using today to ensure that their clients have a secure connection to their online banking. However, no matter how secure a connection, with the right time, tools, and patience, anything can be hacked. That being said, the table below is a short list of some of the strategies used today. | ||
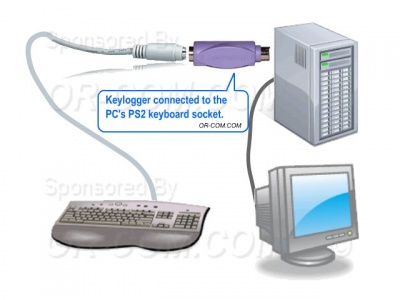
| + | [[Image:Keykatcher_installed_diagram.jpg|thumb|Installed Keylogger|400px|right|Keystroke Logger installed]] | ||
===Protection Table=== | ===Protection Table=== | ||
| Line 71: | Line 81: | ||
==Recommended Strategies== | ==Recommended Strategies== | ||
| - | If you change the way you think, you’ll change the way you act. If you change the way you act, you’ll be able to change the way others act. If you change the way others act, you can help change the world, one person at a time (Wally, 2). | + | If you change the way you think, you’ll change the way you act. If you change the way you act, you’ll be able to change the way others act. If you change the way others act, you can help change the world, one person at a time (Wally, 2). |
| + | |||
There are many ways to protect a user from becoming a victim of a key logged attempt. Firstly, you need to be aware of the kind of threats your up against, be it software, hardware, or kernel-based. Usually people protect themselves against software-based log attempts, as these are the most common. That being said, discussion will be based upon software-based applications. Firstly, it is advised not to use Internet Explorer. Programs such as Firefox, Google Chrome, Netscape, and Opera can be used as alternatives to IE. | There are many ways to protect a user from becoming a victim of a key logged attempt. Firstly, you need to be aware of the kind of threats your up against, be it software, hardware, or kernel-based. Usually people protect themselves against software-based log attempts, as these are the most common. That being said, discussion will be based upon software-based applications. Firstly, it is advised not to use Internet Explorer. Programs such as Firefox, Google Chrome, Netscape, and Opera can be used as alternatives to IE. | ||
| - | |||
| - | In addition to this, installing an anti-spyware program as well as a firewall also aids in increased protection. However, when an individual wants to access their online banking on a public computer, he/she may not be able to scan the computer for any keystroke logging devices; therefore you must make sure your navigation is based on some form of encryption: See Protection Table above. | + | The IE browser is no longer recommended due to the level of danger and risk involved in its threats. Major organizations are no longer suggesting that users merely download the latest patches, check their security settings for IE. Secondly, invest in an anti-virus program and keep its definitions up-to-date. In addition to this, installing an anti-spyware program as well as a firewall also aids in increased protection. However, when an individual wants to access their online banking on a public computer, he/she may not be able to scan the computer for any keystroke logging devices; therefore you must make sure your navigation is based on some form of encryption: See Protection Table above. If users keep their anti-virus and anti-spyware software up-to-date, use firewalls, and avoid running programs received via e-mail or instant messaging, they increase their chances of protection against many threats, including Keystroke Logging. |
| + | ==References== | ||
| + | * Wang Wally, “Steal This Computer Book: What They Won’t tell You About the Internet.”, San Francisco No Starch Press, 2001. netLibrary [http://netlibrary.com/Search/SearchResults.aspx?__EVENTTARGET=&__EVENTARGUMENT=&VIEW_STATE_FIELD_NAME=1&__VIEWSTATE=&tt1=FullText&t1=steal+this+computer+book&ql=ENG Link] | ||
| + | * Audti and Jim Lanford, ''How to keep the money in you bank account safe'' 2002, Issue #92 | ||
| - | + | * Abraham Sinkov, ''Elementary Cryptanalysis: A Mathematical Approach'', Mathematical Association of America, 1966. | |
| - | ==See | + | *Levy, Henry M., ''Capability-based computer systems'' Digital Press Maynard, Mass isbn=0-932376-22-3 [http://www.cs.washington.edu/homes/levy/capabook/index.html Link] |
| + | |||
| + | *Jochen Liedtke|Liedtke Jochen, ''[http://i30www.ira.uka.de/research/publications/papers/index.php?lid=en&docid=642 On µ-Kernel Construction]'', ''Proc. 15th ACM Symposium on Operating System Principles (SOSP)'', December 1995 | ||
| + | |||
| + | * Linden Theodore A., ''Operating System Structures to Support Security and Reliable Software'' ACM Computing Surveys (CSUR) pp. 409–445 volume 8 issue 4 1976 isbn 0360-0300 [http://portal.acm.org/citation.cfm?id=356682&coll=&dl=ACM&CFID=15151515&CFTOKEN=6184618|doi=10.1145/356678.356682 Link] | ||
| + | |||
| + | == See also == | ||
| + | * [[Cryptography in Information Security]] | ||
| + | * [[Security and Storage Mediums]] | ||
| + | * [[Security for Small Home Networks]] | ||
| + | * [[Data Encryption for Storage Devices]] | ||
| + | * [[IP Spoofing]] | ||
==External Links== | ==External Links== | ||
| + | * [[http://en.wikipedia.org/wiki/Cryptography Cryptography]] | ||
| + | * [[http://en.wikipedia.org/wiki/Trojan_horse_(computing) Trojan horses]] | ||
| + | * [http://www.netadmintools.com/art215.html Keylogging] Hardware and software keylogging methods. | ||
| + | * [http://freeware.wikia.com/wiki/Lists_of_freeware_antikeyloggers Lists of Freeware Anti-Keyloggers] | ||
| + | * {{dmoz|Computers/Security/Products_and_Tools/Monitoring/Keyloggers/|Keyloggers}} | ||
| + | * [http://www.keylogger.org Keylogger.Org - Independent testing, rating and review of monitoring software] | ||
| + | * [http://www.securityfocus.com/infocus/1829 Introduction to Spyware Keyloggers] | ||
| + | * [http://www.viruslist.com/en/analysis?pubid=204791931 Keyloggers: How they work and how to detect them] | ||
| + | * [http://cups.cs.cmu.edu/soups/2006/posters/herley-poster_abstract.pdf How To Login From an Internet Cafe Without Worrying About Keyloggers] | ||
| + | |||
| + | --[[User:Shukrim|Shukrim]] 20:58, 12 April 2009 (EDT) | ||
Current revision as of 00:58, 13 April 2009
Keystroke logging commonly refers to the practice of logging (or storing) keystrokes, mouse events, and clipboard contents.
Most importantly, various login names, passwords, and other keystrokes can be recorded, in which important data such as credit card or banking information can be leaked out. The history of key logging is relative to the ease at which a computer can become infected; a user can simply visit the wrong website and become infected. Therefore, as users become more dependant on the accessibility of online networking, new security measures must be taken to accommodate for the risks involved with the convenience.
Keystroke loggers can be applied using three different methods: software, hardware, or kernel-driven applications. Information collected from key logging typically include host-names, IP addresses, and GUID(globally unique identifiers).
Contents |
History
Trojans, electronic spying, remote-computer monitoring, viruses, horses, and of course, keystroke logging, are all various threats openly available to everyone who uses computers; from gurus to illiterates. The question now lies on how well a user is protected against threats and attacks from malicious users. Hackers all around the world usually tend to communicate through the internet. Many have come together and formed their own websites that provide information about the world from the hackers’ point of view. One such site is Anti-online, another Attrition.org. Even websites such as these, ones created by hackers, for hackers, have been hacked at some point in time. Ever since these sites teamed up with law enforcement officials, they have been an outreach to hacking. They have been breached by some means of security so many times that logs have actually been posted of attempted hacks and threats.
Keystroke logging (or keylogging), has been a steal-string concept used ever since computers were first invented, and is continually growing as technology advances. It can be used in both a negative and position aspect. For example, its idea can be useful in law enforcement as it provides a way to unlock passwords and encryption keys.
Historic Example: PGP Case
Pretty Good Privacy (PGP) is a computer program that provides cryptographic privacy and authentication. PGP is often used for signing, encrypting and decrypting e-mails to increase the security of e-mail communications. It was originally created by Philip Zimmermann in 1991.
PGP and other similar products follow the OpenPGP standard (RFC 4880) for encrypting and decrypting data. PGP and other similar products follow the OpenPGP standard (RFC 4880) for encrypting and decrypting data. FBI officials have used the technique to gather evidence, such as the PGP case. In this example, the FBI needed a password in order to decrypt coded files that allegedly contained records of illegal gambling and loan-sharking operations. So FBI officials decided to break into the son of the illicit Philadelphia mob boss’s business, and put a program on his computer (or perhaps an electronic bug in his keyboard) to record all the keystrokes.
The keystroke logger was then used to obtain the PGP passphrase of Nicodemo Scarfo, Jr., son of mob boss Nicodemo Scarfo. Scarfo Jr. pleaded guilty to running an illegal gambling operation in 2002.<ref>"Mobster's son pleads guilty of gambling; computer spying helped seal case" Associated Press, 1 Mar 2002</ref> The FBI has also reportedly developed a trojan-horse-delivered keylogger program known as Magic Lantern.<ref>http://www.msnbc.com/news/660096.asp?cp1=1</ref>
This is just one example of a historic case in which key logging was used to promote a positive gain.
Therefore, many different types of risks and security threats are faced online today. Cryptography can serve as an aid for protection against such threats, including Keystroke Logging.
Protection: A Formal Analysis
Case Study
“Scotia Online® is a protected environment that meets the highest Internet security standards. When you are signed onto Scotia Online, we take (additional) steps to protect your information” (Scotia Online).
Online banking certainly provides great convenience. It can save a lot of time for users by letting them check balances, transfer money between accounts, and pay bills. However, there are risks involved in this convenience. There are a number of different security techniques banks are using today to ensure that their clients have a secure connection to their online banking. However, no matter how secure a connection, with the right time, tools, and patience, anything can be hacked. That being said, the table below is a short list of some of the strategies used today.
Protection Table
| 1.) 128-bit SSL Security |
| 2.) Software Pin Pads |
| 3.) Two-factor Authentication |
| 4.) Timeouts |
| 5.) Reference Numbers |
| 6.) Masked Account Numbers |
SSL Security
The main focus of protection will be on SSL security. The first and most important strategy used by many banks around the world entitles a 128-bit Secure Sockets Layer. SSL security is now the strongest browser-supported encryption available and is the standard within the banking, finance and online e-commerce industries. It ensures that confidential information is encrypted in such a way so that it cannot be viewed, manipulated, altered or embellished in any way during transmission. It prevents others from reading or tampering with account activity. It is an encryption standard developed by Netscape Corporation, that is based on a scheme known as a public key encryption.
Basically, 128 bit SSL encryption is a technology that encrypts, or scrambles digital information into a string of unrecognizable characters called cipher text. The information sent from one computer across the internet is encrypted, then decrypted, deciphered, or unscrambled on the receiving computer. This prevents the information from being viewed by a non-trusted third party whilst in transit between computers. The transaction takes place over what is also known as a Secure Internet Connection. This 128 bit SSL encryption method protects the users’ transaction from the moment they enter their credit card information to the moment they receive payment confirmation. With the vast majority of online business websites now using 128 bit SSL encryption, all sensitive data, such as bank details and credit card numbers are between computers using what is currently one of the most secure protocols available. Usually, users can tell that 128-bit SSL security protection is working correctly from the SSL Certificate. This alters the website page’s link (or URL), by adding the "s" in "https. The user can then see the padlock icon in the lower right hand corner of their browser to ensure that the online transaction is secure.
PIN Pads
The second method many banks are using to ensure keystrokes are not saved is the software pin pad method. Online banks sometimes have software keyboards on their log-in pages. This ensures that a simple key logger cannot record what you are typing because everything happens on screen through the use of the mouse. This type of software constantly changes the labels on its virtual keys, so key loggers cannot tell what number or letter you are clicking on by recording pointer's location on screen each time a user clicks. Of course, there are ways around software pin pads as well. By using malware with software that can capture an image of the user’s screen, a hacker can record every time the user clicks a number on the on-screen PIN pad, and can take screen shots for review. Therefore, the only trusted form of protection, even though it may not be 100 percent risk-free, is the 128-bit SSL security.
Recommended Strategies
If you change the way you think, you’ll change the way you act. If you change the way you act, you’ll be able to change the way others act. If you change the way others act, you can help change the world, one person at a time (Wally, 2).
There are many ways to protect a user from becoming a victim of a key logged attempt. Firstly, you need to be aware of the kind of threats your up against, be it software, hardware, or kernel-based. Usually people protect themselves against software-based log attempts, as these are the most common. That being said, discussion will be based upon software-based applications. Firstly, it is advised not to use Internet Explorer. Programs such as Firefox, Google Chrome, Netscape, and Opera can be used as alternatives to IE.
The IE browser is no longer recommended due to the level of danger and risk involved in its threats. Major organizations are no longer suggesting that users merely download the latest patches, check their security settings for IE. Secondly, invest in an anti-virus program and keep its definitions up-to-date. In addition to this, installing an anti-spyware program as well as a firewall also aids in increased protection. However, when an individual wants to access their online banking on a public computer, he/she may not be able to scan the computer for any keystroke logging devices; therefore you must make sure your navigation is based on some form of encryption: See Protection Table above. If users keep their anti-virus and anti-spyware software up-to-date, use firewalls, and avoid running programs received via e-mail or instant messaging, they increase their chances of protection against many threats, including Keystroke Logging.
References
- Wang Wally, “Steal This Computer Book: What They Won’t tell You About the Internet.”, San Francisco No Starch Press, 2001. netLibrary Link
- Audti and Jim Lanford, How to keep the money in you bank account safe 2002, Issue #92
- Abraham Sinkov, Elementary Cryptanalysis: A Mathematical Approach, Mathematical Association of America, 1966.
- Levy, Henry M., Capability-based computer systems Digital Press Maynard, Mass isbn=0-932376-22-3 Link
- Jochen Liedtke|Liedtke Jochen, On µ-Kernel Construction, Proc. 15th ACM Symposium on Operating System Principles (SOSP), December 1995
- Linden Theodore A., Operating System Structures to Support Security and Reliable Software ACM Computing Surveys (CSUR) pp. 409–445 volume 8 issue 4 1976 isbn 0360-0300 Link
See also
- Cryptography in Information Security
- Security and Storage Mediums
- Security for Small Home Networks
- Data Encryption for Storage Devices
- IP Spoofing
External Links
- [Cryptography]
- [Trojan horses]
- Keylogging Hardware and software keylogging methods.
- Lists of Freeware Anti-Keyloggers
- Template:Dmoz
- Keylogger.Org - Independent testing, rating and review of monitoring software
- Introduction to Spyware Keyloggers
- Keyloggers: How they work and how to detect them
- How To Login From an Internet Cafe Without Worrying About Keyloggers
--Shukrim 20:58, 12 April 2009 (EDT)