Honeypot
From Computing and Software Wiki
| (4 intermediate revisions not shown) | |||
| Line 2: | Line 2: | ||
A Honeypot usually serves as a surveillance and early warning tool. It doesn't fix a single problem, but is a highly flexible security tool that has different applications for security. It has multiple uses including prevention, detection and information gathering. Honeypots all have the same concept that they don't have any production or authorized activity. A Honeypot should not see any legitimate traffic and can be surmised that it will only capture malicious or unauthorized activity. After being deployed in a network, a honeypot should not affect critical network services and applications. Its value as a security resource lies in being probed, attacked or compromised. | A Honeypot usually serves as a surveillance and early warning tool. It doesn't fix a single problem, but is a highly flexible security tool that has different applications for security. It has multiple uses including prevention, detection and information gathering. Honeypots all have the same concept that they don't have any production or authorized activity. A Honeypot should not see any legitimate traffic and can be surmised that it will only capture malicious or unauthorized activity. After being deployed in a network, a honeypot should not affect critical network services and applications. Its value as a security resource lies in being probed, attacked or compromised. | ||
| + | [[Image:figureA.jpg|thumb|right|Honeypot Deployment Example [http://www.honeynet.org/papers/honeynet/]]] | ||
| + | |||
| - | |||
| - | |||
| - | |||
| - | |||
== Types of Honeypots == | == Types of Honeypots == | ||
| + | Honeypots can be classified differently depending on how they are deployed, and the purpose that they are being used for. | ||
| + | === Production Honeypots === | ||
| + | Production Honeypots are generally placed inside a network with other servers that are used for production purposes. They are used by organizations to improve the overall state of security. They can generally only capture a limited amount of information and are used primarily by companies and corporations. They are used to lower the organization's risk and add value to their security measures. Production honeypots give less information about the attacks and the attackers themselves than a research honeypot, but they are easier to use and set up. Production honeypots are normally a type of low-interaction honeypot. | ||
| + | === Research Honeypots === | ||
| + | Research Honeypots are generally used by research organizations or educational institutions. They gather information about the tactics and the motives that are being used by the hacker community that is targeting different types of networks. Research Honeypots do not add a direct value to an organization but are used to research the different types of threats that an organization is facing and how to protect against those threats. They gather information about the attackers that can be used to help protect the organization. They can capture more extensive information, but as a result are more complex to deploy and maintain. Research honeypots are generally a type of high-interaction honeypot that is used by research, military and government institutions. | ||
| + | === Interaction Levels of Honeypots === | ||
| + | Honeypots can be classified as either a '''low-interaction''' level Honeypot or a '''high-interaction''' level Honeypot. | ||
| - | == | + | {| border="5" cellspacing="1" cellpadding="2" align="center" |
| + | |+ [http://www.spitzner.net/honeypots.html 2] | ||
| + | !'''Low-interaction''' | ||
| + | ''emulates operating systems and their services'' | ||
| + | !'''High-interaction''' | ||
| + | ''Not an emulation, uses real operating systems and services'' | ||
| + | |- | ||
| + | | | ||
| + | *Easy to install and deploy, and usually just requires installing and configuring software on a computer | ||
| + | *Minimal risk as it controls what the attackers can and cannot do | ||
| + | *Captures limited amounts of information | ||
| + | | | ||
| + | *Can capture much more information | ||
| + | *Can be complex to deploy and install | ||
| + | *Has increased risk, as the attackers have a real operating system to interact with | ||
| + | |} | ||
| + | === Honeyd === | ||
| + | [http://en.wikipedia.org/wiki/Honeyd Honeyd] is a low-interaction honeypot that was developed by Niels Provos. It is an open source program that allows a user to setup and run multiple virtual hosts on a network. The virtual hosts can be configured to mimic different types of servers. This allows a user to simulate many different computer network configurations. Honeyd works by emulating computers on an unused IP address of a network and allowing scripts to simulate arbitrary services. It usually does not allow a full system compromise but gives hackers a facade to attack. | ||
| + | === Honeynets === | ||
| + | A Honeynet is a network of multiple honeypots and are usually made up of real systems. They are a type of high-interaction honeypot that is used for monitoring a larger and/or more diverse network where one honeypot might not be sufficient. The network is reached via the Honeywall Gateway. This network bridge closely monitors and controls the data flow that comes to and from the honeypots in the network. Types of data that it can capture include system event data in logs, keylog data and network traffic. | ||
| - | == | + | == Value of Honeypots == |
| + | === Advantages === | ||
| + | [http://www.spitzner.net/honeypots.html]Honeypots are a very simple concept which gives them some powerful strengths: | ||
| + | *''Small data sets with high value:'' Honeypots can collect small amounts of information. They might log about 1MB of data a day. They also can generate only 10 alerts a day, as opposed to 10,000. Since honeypots only capture the bad activity, all of this information would be unauthorized or malicious. So it is much easier to analyze the data and find value from it. | ||
| + | *''Minimal resources:'' Honeypots only require minimal resources since they only capture bad activity. | ||
| + | *''New tools and tactics:'' Honeypots are made to capture anything that is thrown at them, even if it hasn't been seen before. | ||
| + | *''Encryption:'' Honeypots will work fine in encrypted environments unlike many other security technologies. The honeypot will detect and capture whatever is thrown at it. | ||
| + | *''Information:'' Honeypots can collect in-depth information that few other technologies can match. | ||
| + | *''Simplicity:'' The conceptual part of honeypots is very simple, so it is less likely to have mistakes or misconfigurations. | ||
| + | === Disadvantages === | ||
| + | Honeypots also have weaknesses, like any other technology, so they should be used in addition to other technologies. | ||
| + | *''Limited view:'' Honeypots will only capture and track the activity that directly interacts with them. They can't capture attacks on other systems unless they interact with the honeypot as well. | ||
| + | *''Risk:'' All security technologies have some risk associated with them. Honeypots run the risk of being taken over by the hacker and being used to harm other systems. The level of risk is associated with the type of the honeypot. High-interaction honeypots generally run a much higher level of risk than low-interaction honeypots. | ||
| + | == Legal Issues == | ||
| + | As the purpose of Honeypots is to track and monitor the actions of a hacker, certain questions may arise as to whether or not Honeypots are legal. This is not a simple question, and the answer may not be fully known at this point in time. As security professionals are just beginning to understand what Honeypots are and how they are used, the legal community is as well. There are 3 main issues that are commonly discussed with the legality of honeypots: entrapment, privacy and liability. Honeypots are not considered to be a form of entrapment, whereas the other 2 issues are more complex. As the actions of Honeypots have not really been tried in the court system as of yet, it is unknown as to its outcome. However, there are some precautionary measures that would be important to take. Putting up banners indicating that a hackers actions are being monitored would ensure that they have consented to it. It is also important to be a conscientious honeypot administrator. If a honeypot was to become compromised, it must be dealt with immediately as to prevent the administrator from becoming liable if the hacker uses it to harm other information systems. It is recommended to seek legal advice before deploying a honeypot. [http://www.securityfocus.com/infocus/1703] | ||
| - | == | + | == References == |
| + | # Know your Enemy: Honeynets <[http://www.honeynet.org/papers/honeynet/ http://www.honeynet.org/papers/honeynet/]> | ||
| + | # Honeypots: Definitions and value of Honeypots <[http://www.spitzner.net/honeypots.html http://www.spitzner.net/honeypots.html]> | ||
| + | # Honeypots: Are they illegal? <[http://www.securityfocus.com/infocus/1703 http://www.securityfocus.com/infocus/1703]> | ||
| + | == See also == | ||
| + | [[Piggybacking]]<BR> | ||
| + | [[Security and Storage Mediums]]<BR> | ||
| + | [[Random Number Generators and Information Security]]<BR> | ||
| + | [[Biometric systems regarding security design principle]]<BR> | ||
| + | [[Phishing]]<BR> | ||
| + | [[Biometrics in Information Security]]<BR> | ||
| + | [[Smart Card technology to prevent fraud]]<BR> | ||
| + | [[Electronic Voting Systems]]<BR> | ||
| + | [[Anti-spam Systems and Techniques]]<BR> | ||
| + | [[The Mitnick attack]]<BR> | ||
| + | [[Payment Card Industry Data Security Standard]]<BR> | ||
| + | [[Operating Systems Security]]<BR> | ||
| + | [[Autocomplete]]<BR> | ||
| + | [[Social engineering]]<BR> | ||
| + | [[Identity Theft]]<BR> | ||
| + | [[Information security awareness]]<BR> | ||
| + | == External Links == | ||
| + | *[http://www.tracking-hackers.com/ Honeytech] | ||
| + | *[http://www.honeypots.net/ Intrusion Detection, Honeypots and Incident Handling Resources] | ||
| + | *[http://honeypots.sourceforge.net/ Honeypots: Monitoring and Forensics] | ||
| + | *[http://www.honeynet.org/ The Honeynet Project] | ||
| + | *[http://www.honeyd.org/ Developments of the Honeyd Virtual Honeypot] | ||
| + | *[http://honeynet.ca/ Canadian Honeynet Project | Canadian Honeypot Security Research] | ||
| + | *[http://www.linux.com/articles/39244 Know your enemy: Everything you need to know about Honeypots] | ||
| + | *[http://en.wikipedia.org/wiki/Honeypot_%28computing%29 Wikipedia: Honeypot(computing)] | ||
| - | --[[User:Colbyl2|Colbyl2]] | + | --[[User:Colbyl2|Colbyl2]] 02:03, 9 December 2007 (EST) |
Current revision as of 07:41, 9 December 2007
In computing terminology, a Honeypot is a closely monitored network decoy that serves several purposes. It can provide early warning about a new attack or exploitation trends, can distract adversaries from other more valuable resources on a network, or allow a detailed examination of adversaries during and after a honeypot has been exploited.
A Honeypot usually serves as a surveillance and early warning tool. It doesn't fix a single problem, but is a highly flexible security tool that has different applications for security. It has multiple uses including prevention, detection and information gathering. Honeypots all have the same concept that they don't have any production or authorized activity. A Honeypot should not see any legitimate traffic and can be surmised that it will only capture malicious or unauthorized activity. After being deployed in a network, a honeypot should not affect critical network services and applications. Its value as a security resource lies in being probed, attacked or compromised.
Contents |
Types of Honeypots
Honeypots can be classified differently depending on how they are deployed, and the purpose that they are being used for.
Production Honeypots
Production Honeypots are generally placed inside a network with other servers that are used for production purposes. They are used by organizations to improve the overall state of security. They can generally only capture a limited amount of information and are used primarily by companies and corporations. They are used to lower the organization's risk and add value to their security measures. Production honeypots give less information about the attacks and the attackers themselves than a research honeypot, but they are easier to use and set up. Production honeypots are normally a type of low-interaction honeypot.
Research Honeypots
Research Honeypots are generally used by research organizations or educational institutions. They gather information about the tactics and the motives that are being used by the hacker community that is targeting different types of networks. Research Honeypots do not add a direct value to an organization but are used to research the different types of threats that an organization is facing and how to protect against those threats. They gather information about the attackers that can be used to help protect the organization. They can capture more extensive information, but as a result are more complex to deploy and maintain. Research honeypots are generally a type of high-interaction honeypot that is used by research, military and government institutions.
Interaction Levels of Honeypots
Honeypots can be classified as either a low-interaction level Honeypot or a high-interaction level Honeypot.
| Low-interaction
emulates operating systems and their services | High-interaction
Not an emulation, uses real operating systems and services |
|---|---|
|
|
Honeyd
Honeyd is a low-interaction honeypot that was developed by Niels Provos. It is an open source program that allows a user to setup and run multiple virtual hosts on a network. The virtual hosts can be configured to mimic different types of servers. This allows a user to simulate many different computer network configurations. Honeyd works by emulating computers on an unused IP address of a network and allowing scripts to simulate arbitrary services. It usually does not allow a full system compromise but gives hackers a facade to attack.
Honeynets
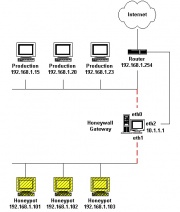
A Honeynet is a network of multiple honeypots and are usually made up of real systems. They are a type of high-interaction honeypot that is used for monitoring a larger and/or more diverse network where one honeypot might not be sufficient. The network is reached via the Honeywall Gateway. This network bridge closely monitors and controls the data flow that comes to and from the honeypots in the network. Types of data that it can capture include system event data in logs, keylog data and network traffic.
Value of Honeypots
Advantages
[2]Honeypots are a very simple concept which gives them some powerful strengths:
- Small data sets with high value: Honeypots can collect small amounts of information. They might log about 1MB of data a day. They also can generate only 10 alerts a day, as opposed to 10,000. Since honeypots only capture the bad activity, all of this information would be unauthorized or malicious. So it is much easier to analyze the data and find value from it.
- Minimal resources: Honeypots only require minimal resources since they only capture bad activity.
- New tools and tactics: Honeypots are made to capture anything that is thrown at them, even if it hasn't been seen before.
- Encryption: Honeypots will work fine in encrypted environments unlike many other security technologies. The honeypot will detect and capture whatever is thrown at it.
- Information: Honeypots can collect in-depth information that few other technologies can match.
- Simplicity: The conceptual part of honeypots is very simple, so it is less likely to have mistakes or misconfigurations.
Disadvantages
Honeypots also have weaknesses, like any other technology, so they should be used in addition to other technologies.
- Limited view: Honeypots will only capture and track the activity that directly interacts with them. They can't capture attacks on other systems unless they interact with the honeypot as well.
- Risk: All security technologies have some risk associated with them. Honeypots run the risk of being taken over by the hacker and being used to harm other systems. The level of risk is associated with the type of the honeypot. High-interaction honeypots generally run a much higher level of risk than low-interaction honeypots.
Legal Issues
As the purpose of Honeypots is to track and monitor the actions of a hacker, certain questions may arise as to whether or not Honeypots are legal. This is not a simple question, and the answer may not be fully known at this point in time. As security professionals are just beginning to understand what Honeypots are and how they are used, the legal community is as well. There are 3 main issues that are commonly discussed with the legality of honeypots: entrapment, privacy and liability. Honeypots are not considered to be a form of entrapment, whereas the other 2 issues are more complex. As the actions of Honeypots have not really been tried in the court system as of yet, it is unknown as to its outcome. However, there are some precautionary measures that would be important to take. Putting up banners indicating that a hackers actions are being monitored would ensure that they have consented to it. It is also important to be a conscientious honeypot administrator. If a honeypot was to become compromised, it must be dealt with immediately as to prevent the administrator from becoming liable if the hacker uses it to harm other information systems. It is recommended to seek legal advice before deploying a honeypot. [3]
References
- Know your Enemy: Honeynets <http://www.honeynet.org/papers/honeynet/>
- Honeypots: Definitions and value of Honeypots <http://www.spitzner.net/honeypots.html>
- Honeypots: Are they illegal? <http://www.securityfocus.com/infocus/1703>
See also
Piggybacking
Security and Storage Mediums
Random Number Generators and Information Security
Biometric systems regarding security design principle
Phishing
Biometrics in Information Security
Smart Card technology to prevent fraud
Electronic Voting Systems
Anti-spam Systems and Techniques
The Mitnick attack
Payment Card Industry Data Security Standard
Operating Systems Security
Autocomplete
Social engineering
Identity Theft
Information security awareness
External Links
- Honeytech
- Intrusion Detection, Honeypots and Incident Handling Resources
- Honeypots: Monitoring and Forensics
- The Honeynet Project
- Developments of the Honeyd Virtual Honeypot
- Canadian Honeynet Project | Canadian Honeypot Security Research
- Know your enemy: Everything you need to know about Honeypots
- Wikipedia: Honeypot(computing)
--Colbyl2 02:03, 9 December 2007 (EST)
