Honeypot
From Computing and Software Wiki
| Line 8: | Line 8: | ||
<br style="clear:both;"/> | <br style="clear:both;"/> | ||
== Types of Honeypots == | == Types of Honeypots == | ||
| + | Honeypots can be classified differently depending on how they are deployed, and the purpose that they are being used for. | ||
| + | === Production Honeypots === | ||
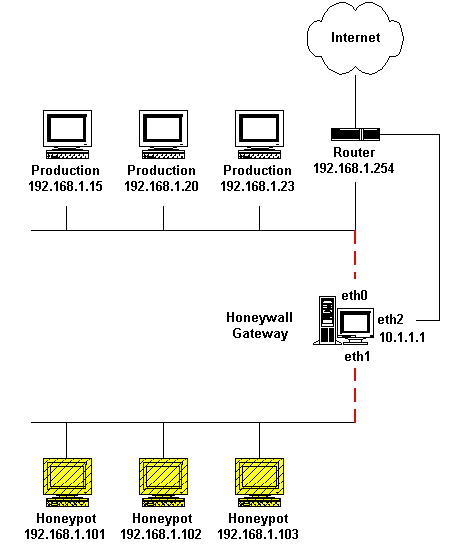
| + | Production Honeypots are generally placed inside a network with other servers that are used for production purposes. They are used by organizations to improve the overall state of security. They can generally only capture a limited amount of information and are used primarily by companies and corporations. They are used to lower the organization's risk and add value to their security measures. Production honeypots give less information about the attacks and the attackers themselves than a research honeypot, but they are easier to use and set up. Production honeypots are normally a type of low-interaction honeypot. | ||
| + | |||
| + | === Research Honeypots === | ||
| + | Research Honeypots are generally used by research organizations or educational institutions. They gather information about the tactics and the motives that are being used by the hacker community that is targeting different types of networks. Research Honeypots do not add a direct value to an organization but are used to research the different types of threats that an organization is facing and how to protect against those threats. They gather information about the attackers that can be used to help protect the organization. They can capture more extensive information, but as a result are more complex to deploy and maintain. Research honeypots are generally a type of high-interaction honeypot that is used by research, military and government institutions. | ||
Revision as of 22:15, 8 December 2007
In computing terminology, a Honeypot is a closely monitored network decoy that serves several purposes. It can provide early warning about a new attack or exploitation trends, can distract adversaries from other more valuable resources on a network, or allow a detailed examination of adversaries during and after a honeypot has been exploited.
A Honeypot usually serves as a surveillance and early warning tool. It doesn't fix a single problem, but is a highly flexible security tool that has different applications for security. It has multiple uses including prevention, detection and information gathering. Honeypots all have the same concept that they don't have any production or authorized activity. A Honeypot should not see any legitimate traffic and can be surmised that it will only capture malicious or unauthorized activity. After being deployed in a network, a honeypot should not affect critical network services and applications. Its value as a security resource lies in being probed, attacked or compromised.
A Honeypot can also carry certain risks to a network and should be handled with care. If it is not properly looked after or walled off, an attacker can use it to break into another system.
Contents |
Types of Honeypots
Honeypots can be classified differently depending on how they are deployed, and the purpose that they are being used for.
Production Honeypots
Production Honeypots are generally placed inside a network with other servers that are used for production purposes. They are used by organizations to improve the overall state of security. They can generally only capture a limited amount of information and are used primarily by companies and corporations. They are used to lower the organization's risk and add value to their security measures. Production honeypots give less information about the attacks and the attackers themselves than a research honeypot, but they are easier to use and set up. Production honeypots are normally a type of low-interaction honeypot.
Research Honeypots
Research Honeypots are generally used by research organizations or educational institutions. They gather information about the tactics and the motives that are being used by the hacker community that is targeting different types of networks. Research Honeypots do not add a direct value to an organization but are used to research the different types of threats that an organization is facing and how to protect against those threats. They gather information about the attackers that can be used to help protect the organization. They can capture more extensive information, but as a result are more complex to deploy and maintain. Research honeypots are generally a type of high-interaction honeypot that is used by research, military and government institutions.
References
See also
Piggybacking
Security and Storage Mediums
Random Number Generators and Information Security
Biometric systems regarding security design principle
Phishing
Biometrics in Information Security
Smart Card technology to prevent fraud
Electronic Voting Systems
Anti-spam Systems and Techniques
The Mitnick attack
Payment Card Industry Data Security Standard
Operating Systems Security
Autocomplete
Social engineering
Identity Theft
Information security awareness
External Links
--Colbyl2 18:42, 1 December 2007 (EST)