Domain Name System
From Computing and Software Wiki
(→External Links) |
|||
| (22 intermediate revisions not shown) | |||
| Line 4: | Line 4: | ||
== History of DNS == | == History of DNS == | ||
| - | In the late 1960s, the U.S. Department of Defense Advanced Research Projects Agency (ARPA, later known as DARPA) funded and began working toward an internet technology called the ARPANET.<sup>[1]</sup> Each computer on the network was given an address for interconnecting with other computers on the network. | + | In the late 1960s, the U.S. Department of Defense Advanced Research Projects Agency (ARPA, later known as DARPA) funded and began working toward an internet technology called the ARPANET.<sup>[1]</sup> Each computer on the network was given an address for interconnecting with other computers on the network. This information was stored on a central site, called the Network Information Center (NIC), in a single file named HOSTS.TXT.<sup>[3,4]</sup> The HOSTS.TXT file contained information regarding the name-to-address mapping of all computers connected to the ARPANET.<sup>[3]</sup> Each computer on the network needed to retrieve this file in order to communication with other computers on the network.<sup>[3]</sup> With only a small number of computers interconnected in the beginning, HOSTS.TXT worked well. However, there are limitations with this scheme. First, if there was a change in the address of one of the computers on the network, every computer that wanted to communicate with that machine was forced to update its host file. Also, as the network traffic increased, there was a need to overcome problems such as overlapping names. DNS was invented to solve these limitations. |
The Domain Name System was invented by Jon Postel, Paul Mockapetris and Craig Partrige in 1983.<sup>[4]</sup> In addition, they published the original specification, RFC 882, for the DNS.<sup>[4]</sup> Over the years, several more RFCs have been published to update the DNS specification, making the RFC 882 obsolete. | The Domain Name System was invented by Jon Postel, Paul Mockapetris and Craig Partrige in 1983.<sup>[4]</sup> In addition, they published the original specification, RFC 882, for the DNS.<sup>[4]</sup> Over the years, several more RFCs have been published to update the DNS specification, making the RFC 882 obsolete. | ||
| Line 12: | Line 12: | ||
[[Image:Domain Namespace.jpg|thumb|Delegation of authority for names in the Domain Name System.]] | [[Image:Domain Namespace.jpg|thumb|Delegation of authority for names in the Domain Name System.]] | ||
The DNS uses a hierarchical naming scheme. A hierarchical naming scheme operates similar to the management structure of a business organization. At the top level, the namespace is divided and each division is delegated with authority.<sup>[1]</sup> In addition, if there is a change in a division, the top level would not be affected.<sup>[1]</sup> | The DNS uses a hierarchical naming scheme. A hierarchical naming scheme operates similar to the management structure of a business organization. At the top level, the namespace is divided and each division is delegated with authority.<sup>[1]</sup> In addition, if there is a change in a division, the top level would not be affected.<sup>[1]</sup> | ||
| - | The syntax of the assigned names often reflects the hierarchical | + | |
| + | The syntax of the assigned names often reflects the hierarchical structure.<sup>[1]</sup> Using the following namespace as an example: | ||
<center>''local.site''</center> | <center>''local.site''</center> | ||
| - | ''site'' is the name of the site authorized by the central authority; ''local'' is the part that is controlled by the site. The period (“.”) is a delimiter to separate the names. | + | ''site'' is the name of the site authorized by the central authority; ''local'' is the part that is controlled by the site. The period (“.”) is a delimiter to separate the names. This type of hierarchical naming scheme is known as domain name. Domain name is a name consisting of a sequence of labels separated by periods (dots).<sup>[1]</sup> Each suffix of a domain name is also a domain name. In addition, a domain name denotes a set of one or more hosts. In the case of a domain name denoting a single host (known as a ''host name''), the domain name looks no different from a domain name denoting a set of hosts. |
=== Subset Authority === | === Subset Authority === | ||
| Line 24: | Line 25: | ||
=== Top-Level Domains === | === Top-Level Domains === | ||
| - | [[Image:Internet Domain Name.jpg|thumb|A small part of the Internet domain name hierarchy.<sup>[1]</sup>]]The Internet's DNS currently uses a set of official top-level domain names (TLDs). These set of TLDs are maintained by the Internet Corporation for Assigned Names and Numbers ( | + | [[Image:Internet Domain Name.jpg|thumb|A small part of the Internet domain name hierarchy.<sup>[1]</sup>]]The Internet's DNS currently uses a set of official top-level domain names (TLDs). These set of TLDs are maintained by the Internet Corporation for Assigned Names and Numbers (ICANN). Currently, ICANN distinguishes the following groups of TLDs:<sup>[5]</sup> |
* Infrastructure top-level domain | * Infrastructure top-level domain | ||
| Line 88: | Line 89: | ||
[[image:Conceptual_Arrangement_of_Server.jpg|thumb|The conceptual arrangement of domain name servers in a tree that corresponds to the naming hierarchy.<sup>[1]</sup>]] | [[image:Conceptual_Arrangement_of_Server.jpg|thumb|The conceptual arrangement of domain name servers in a tree that corresponds to the naming hierarchy.<sup>[1]</sup>]] | ||
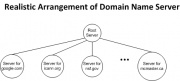
[[image:Realistic_Arrangement_of_Server.jpg|thumb|The realistic arrangement of domain name servers in a tree that corresponds to the naming hierarchy.<sup>[1]</sup>]] | [[image:Realistic_Arrangement_of_Server.jpg|thumb|The realistic arrangement of domain name servers in a tree that corresponds to the naming hierarchy.<sup>[1]</sup>]] | ||
| + | The DNS uses the ''client-server model''. On the server side, the mechanism that DNS uses to map domain names to addresses is a set of independent, cooperative systems called ''name servers''.<sup>[1]</sup> A name server is a server program that maps domain names to IP addresses. On the client side, there is a client software, called ''name resolver'', which uses one or more name servers when mapping a name to IP address.<sup>[1]</sup> It is used to initiate the queries for the mapping. In a conceptual arrangement of domain name servers, each server knows the addresses of all lower-level servers for all subdomains within the domain it handles.<sup>[1]</sup> However, in reality, servers are combined together since a single server can be used to store all of the information.<sup>[1]</sup> | ||
| + | |||
=== Domain Name Resolution === | === Domain Name Resolution === | ||
| + | In theory, the domain name resolution operates in a top-down approach. It starts from the root name server and traces its way down to the servers at the leaves of the hierarchical tree. There are two ways of using DNS:<sup>[1]</sup> | ||
| + | # The client sends a query to each of the name server one at a time | ||
| + | # The client sends a query to one of the name server and makes the name server carry out the whole mapping. | ||
| + | In either of the case, the client is required to send a query containing the domain name that is needed to be mapped to the name server. | ||
| + | |||
| + | When the name server receives the query sent by the client, the server checks to see if the domain name is under its subdomain. If the domain name is under its subdomain, the server will map the name to the address and append the answer onto the client’s query and send back the answer to the client. However, if the domain name is not under its subdomain, the server checks the type of interaction the client specified. There are two types of DNS query that can the client can send:<sup>[1]</sup> | ||
| + | # ''Non-recursive Resolution'' (''Iterative Resolution'') | ||
| + | # ''Recursive Resolution'' (''Complete Resolution'') | ||
| + | If the client specified for non-recursive resolution, the server will generate a reply and suggest the next name server that the client should look to resolve the name, or give an error. On the other hand, if the client specified for recursive resolution, the server will contact another name server that can map the name and send the answer back to the client, or give an error. | ||
| + | |||
| + | In order for the client to start a query, the client needs to know which name server to start the search from. Additionally, the client needs to know at least one of the addresses of the name server. Moreover, DNS requires that each server know at least one of the address of its root server or parent. | ||
| + | Domain name servers communicate with each other using both TCP and UDP.<sup>[6]</sup> In addition, the name servers listen on TCP and UDP ports 53.<sup>[6]</sup> As a result, the client knows how to communicate with the name server once it knows the IP address of the server. | ||
| + | |||
=== Caching === | === Caching === | ||
| - | + | Due to large amount of queries send by the resolvers to the root server, there is an extremely high cost associated with looking up names. In addition, name lookup can present a heavy load on the Internet. As a result, there is a need to reduce the load on the DNS servers and reduce the number of lookups for names. | |
| - | + | ||
| + | The Internet name servers use ''caching'' to improve the search costs.<sup>[1]</sup> Each server maintains a cache of recently looked up names as well as a record of where the names are from. When the client sends a request to the server to map a name, the server will first check to see if the domain name is under its subdomain. If not, the server checks its cache to see if the domain name has recently been resolved. The server will send its cached information (the address and which name server it’s from) back to the client and the information is marked as ''nonauthoritative'' binding.<sup>[1]</sup> As a result, the client receives the information quickly. However, the information could be outdated and be incorrect. To keep the cache correct, servers keep track of the time of the entries and discard entries that exceed a certain time limit. If the server is asked for the information that it removed, the server will have to go through the domain name resolution process again. The servers do not apply a fixed time to remove the outdated information; instead, they allow the authority to enter in a Time To Live (TTL) value to specify how long it guarantees the binding to be valid.<sup>[1]</sup> | ||
| + | |||
| + | Caching can also be done on the host itself. If the user looks up the same name repeatedly, the subsequent look ups can be retrieved from its cache without using the network. | ||
| + | |||
== Security Concerns == | == Security Concerns == | ||
| + | DNS was implemented with little security in mind; as a result, DNS has a number of security issues. Firstly, authentication using the domain name of the source host alone is much weaker than using the IP address alone.<sup>[6]</sup> Thus, host names are easily spoofed. In addition, some domain names can easily spoof other domain names that look similar. For instance, “www.paypal.com” and “www.paypa1.com” are two different domain names; however, users might be tricked and unable to tell the difference between the two because the alphabet ‘l’ looks very similar to the number ‘1’ in certain fonts. In some fonts, the two domain names might even look identical. Another security issue is that attackers might try to corrupt or replace certain information in the DNS.<sup>[6]</sup> This could cause packets to be misdirected. Even worst, the attacker could make IP addresses of that name server to redirect everything to a malicious address with a long TTL. | ||
| + | |||
| + | DNS is an effective tool for probing organization’s network. With that in mind, it is important for the organization to secure and hide its DNS information regarding its internal network from Internet.<sup>[6]</sup> | ||
| + | |||
== Domain Registration == | == Domain Registration == | ||
| + | The right to use a domain name is authorized by ''domain name registrars''.<sup>[7]</sup> In addition, domain name registrars are accredited by ICANN.<sup>[7]</sup> Each top-level domain (TLD) is maintained by InterNIC, which is also operated by ICANN. InterNIC receives domain name registration information provided by the domain name registrars and publishes the information.<sup>[7]</sup> There is an annual fee for the service of authorizing domain name to a user. The authorized users are known as “registrants” or as “domain holders”. | ||
| + | |||
== References == | == References == | ||
# Comer, D. E. (2006). The domain name system (DNS). ''Internetworking with TCP/IP'' (Fifth ed., pp. 419-441). Upper Saddle River, NJ: Pearson Prentice Hall. | # Comer, D. E. (2006). The domain name system (DNS). ''Internetworking with TCP/IP'' (Fifth ed., pp. 419-441). Upper Saddle River, NJ: Pearson Prentice Hall. | ||
| Line 99: | Line 125: | ||
# "[http://www.lagunainternet.com/techsupport/history_of_dns.htm History of the Domain Name System]". Retrieved on 2009-04-07. | # "[http://www.lagunainternet.com/techsupport/history_of_dns.htm History of the Domain Name System]". Retrieved on 2009-04-07. | ||
# "[http://www.mapsofworld.com/referrals/internet/internet-history/history-of-domain-name-system.html History of Domain Name System]". Retrieved on 2009-04-07. | # "[http://www.mapsofworld.com/referrals/internet/internet-history/history-of-domain-name-system.html History of Domain Name System]". Retrieved on 2009-04-07. | ||
| - | # "[http://www.icann.org/en/registries/about.htm ICANN | About gTLDs]". Retrieved on 2009-04-09 | + | # "[http://www.icann.org/en/registries/about.htm ICANN | About gTLDs]". Retrieved on 2009-04-09. |
| + | # William, F. M. (2009). Domain Name System (DNS). In ''Lecture 09: Common Network Services''. | ||
| + | # "[http://www.icann.org/en/faq/ ICANN | FAQs]". Retrieved on 2009-04-09. | ||
| + | |||
== See Also == | == See Also == | ||
* [http://en.wikipedia.org/wiki/Dynamic_DNS Dynamic DNS] | * [http://en.wikipedia.org/wiki/Dynamic_DNS Dynamic DNS] | ||
| + | * [http://en.wikipedia.org/wiki/DNSSEC DNS Security Extensions (DNSSEC)] | ||
| + | * [http://en.wikipedia.org/wiki/DNS_management_software DNS Management Software] | ||
| + | * [http://en.wikipedia.org/wiki/Comparison_of_DNS_server_software Comparison Of DNS Server Software] | ||
| + | * [http://www.cas.mcmaster.ca/wiki/index.php/DHCP DHCP] | ||
| + | |||
== External Links == | == External Links == | ||
| - | * | + | * [http://technet.microsoft.com/en-us/library/cc772774.aspx How DNS Works: Domain Name System(DNS)] |
| - | --Jacky Ng ([[User:Ngck|Ngck]]) | + | * [http://icann.org Internet Corporation for Assigned Names and Numbers (ICANN)] |
| + | * [http://queue.acm.org/detail.cfm?id=1242499 DNS Complexity] | ||
| + | * [http://www.zytrax.com/books/dns/ DNS For Rocket Scientists: An Open Source Guide of DNS] | ||
| + | * [http://www.bind9.net/ DNS & BIND] | ||
| + | --Jacky Ng ([[User:Ngck|Ngck]]) 20:18, 12 April 2009 (EDT) | ||
Current revision as of 00:18, 13 April 2009
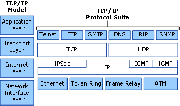
DNS is a hierarchical naming system used to map human-readable machine names into Internet Protocol addresses (IP addresses) for the Internet.[1] Although IP addresses provide a compact representation for identifying machines, users prefer to assign machines with pronounceable, meaningful, and easy-to-remember names.[1] DNS can be thought of as the Internet’s Phone Book. Instead of looking up a phone number using the person’s name or business’s name, the IP address can be looked up by using the domain name. For example, DNS translates the domain name www.mcmaster.ca into 130.113.64.65. DNS is also able to translate from IP addresses to domain names, which is known as Reverse Mapping or Inverse Mapping.[1]DNS is part of the Application Layer of the TCP/IP Internet Protocol Suite. It has two conceptually independent aspects. First, it specifies the name syntax and rules for delegating authority over names.[1] Secondly, it specifies the implementation of a system that efficiently maps names to addresses.[1]
Contents |
History of DNS
In the late 1960s, the U.S. Department of Defense Advanced Research Projects Agency (ARPA, later known as DARPA) funded and began working toward an internet technology called the ARPANET.[1] Each computer on the network was given an address for interconnecting with other computers on the network. This information was stored on a central site, called the Network Information Center (NIC), in a single file named HOSTS.TXT.[3,4] The HOSTS.TXT file contained information regarding the name-to-address mapping of all computers connected to the ARPANET.[3] Each computer on the network needed to retrieve this file in order to communication with other computers on the network.[3] With only a small number of computers interconnected in the beginning, HOSTS.TXT worked well. However, there are limitations with this scheme. First, if there was a change in the address of one of the computers on the network, every computer that wanted to communicate with that machine was forced to update its host file. Also, as the network traffic increased, there was a need to overcome problems such as overlapping names. DNS was invented to solve these limitations.
The Domain Name System was invented by Jon Postel, Paul Mockapetris and Craig Partrige in 1983.[4] In addition, they published the original specification, RFC 882, for the DNS.[4] Over the years, several more RFCs have been published to update the DNS specification, making the RFC 882 obsolete.
Name Syntax And Rules Of DNS
Delegation Of Authority For Names
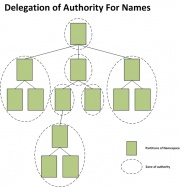
The DNS uses a hierarchical naming scheme. A hierarchical naming scheme operates similar to the management structure of a business organization. At the top level, the namespace is divided and each division is delegated with authority.[1] In addition, if there is a change in a division, the top level would not be affected.[1]
The syntax of the assigned names often reflects the hierarchical structure.[1] Using the following namespace as an example:
site is the name of the site authorized by the central authority; local is the part that is controlled by the site. The period (“.”) is a delimiter to separate the names. This type of hierarchical naming scheme is known as domain name. Domain name is a name consisting of a sequence of labels separated by periods (dots).[1] Each suffix of a domain name is also a domain name. In addition, a domain name denotes a set of one or more hosts. In the case of a domain name denoting a single host (known as a host name), the domain name looks no different from a domain name denoting a set of hosts.
Subset Authority
In the hierarchical naming scheme, authority can be subdivided at each level. The idea is to subdivide the namespace until the subdivision is small enough to be manageable.[1] When subdividing namespace, another partition of the name is introduced. The following example shows the syntax of a group subdivision being added to names already partitioned:[1]
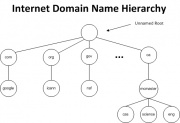
In DNS, the individual sections of names that represent sites and groups are called labels.[1] As a result, the domain name:
contains three labels: cas, mcmaster, and ca. Any suffix of a label in the domain name is called a domain. The lowest level domain in the above example is cas.mcmaster.ca (the domain name for the Computer and Software Department at McMaster University); the second level domain is mcmaster.ca (the domain name for McMaster University); and the top-level domain is ca (the domain name for Canada).
Top-Level Domains
The Internet's DNS currently uses a set of official top-level domain names (TLDs). These set of TLDs are maintained by the Internet Corporation for Assigned Names and Numbers (ICANN). Currently, ICANN distinguishes the following groups of TLDs:[5]- Infrastructure top-level domain
- Country-code top-level domains
- Generic top-level domains
The following table is a list of top-level domain names and their meanings:[1,5]
| Domain Name | Meaning |
|---|---|
| aero | Air transport industry |
| arpa | Intrastructure domain |
| asia | Companies, organisations and individuals in the Asia-Pacific region |
| biz | Businesses |
| cat | Catalan language/culture |
| com | Commerical organization |
| coop | Cooperative associations |
| edu | Educational institution (4-year) |
| gov | United States government |
| info | Information |
| int | International treaty organizations |
| jobs | Employment-related sites |
| mil | United States military |
| museum | Museums |
| name | Individuals |
| net | Major network support centers |
| org | Organizations other than those above |
| pro | Credentialed professionals |
| tel | Services involving connections between telephone network and the Internet |
| travel | Travel agents, airlines, hoteliers, tourism bureaus, etc |
| country code | Each country (geographic scheme) |
Name Syntax And Type
The DNS stores information about hosts and collection of hosts such as mail exchangers. In addition, it allows multiple naming hierarchies to be combined into one system.[1] A given name might be mapped to more than one item in the DNS.[1] To resolve this, each item stored in the DNS is assigned a type (user, mailbox, machine, etc).[1] This way, the client can specify the type of object that they are seeking for and would receive the address of that object.
Implementation of DNS
Mapping Domain Names To Addresses
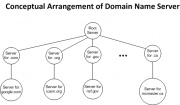
The DNS uses the client-server model. On the server side, the mechanism that DNS uses to map domain names to addresses is a set of independent, cooperative systems called name servers.[1] A name server is a server program that maps domain names to IP addresses. On the client side, there is a client software, called name resolver, which uses one or more name servers when mapping a name to IP address.[1] It is used to initiate the queries for the mapping. In a conceptual arrangement of domain name servers, each server knows the addresses of all lower-level servers for all subdomains within the domain it handles.[1] However, in reality, servers are combined together since a single server can be used to store all of the information.[1]
Domain Name Resolution
In theory, the domain name resolution operates in a top-down approach. It starts from the root name server and traces its way down to the servers at the leaves of the hierarchical tree. There are two ways of using DNS:[1]
- The client sends a query to each of the name server one at a time
- The client sends a query to one of the name server and makes the name server carry out the whole mapping.
In either of the case, the client is required to send a query containing the domain name that is needed to be mapped to the name server.
When the name server receives the query sent by the client, the server checks to see if the domain name is under its subdomain. If the domain name is under its subdomain, the server will map the name to the address and append the answer onto the client’s query and send back the answer to the client. However, if the domain name is not under its subdomain, the server checks the type of interaction the client specified. There are two types of DNS query that can the client can send:[1]
- Non-recursive Resolution (Iterative Resolution)
- Recursive Resolution (Complete Resolution)
If the client specified for non-recursive resolution, the server will generate a reply and suggest the next name server that the client should look to resolve the name, or give an error. On the other hand, if the client specified for recursive resolution, the server will contact another name server that can map the name and send the answer back to the client, or give an error.
In order for the client to start a query, the client needs to know which name server to start the search from. Additionally, the client needs to know at least one of the addresses of the name server. Moreover, DNS requires that each server know at least one of the address of its root server or parent. Domain name servers communicate with each other using both TCP and UDP.[6] In addition, the name servers listen on TCP and UDP ports 53.[6] As a result, the client knows how to communicate with the name server once it knows the IP address of the server.
Caching
Due to large amount of queries send by the resolvers to the root server, there is an extremely high cost associated with looking up names. In addition, name lookup can present a heavy load on the Internet. As a result, there is a need to reduce the load on the DNS servers and reduce the number of lookups for names.
The Internet name servers use caching to improve the search costs.[1] Each server maintains a cache of recently looked up names as well as a record of where the names are from. When the client sends a request to the server to map a name, the server will first check to see if the domain name is under its subdomain. If not, the server checks its cache to see if the domain name has recently been resolved. The server will send its cached information (the address and which name server it’s from) back to the client and the information is marked as nonauthoritative binding.[1] As a result, the client receives the information quickly. However, the information could be outdated and be incorrect. To keep the cache correct, servers keep track of the time of the entries and discard entries that exceed a certain time limit. If the server is asked for the information that it removed, the server will have to go through the domain name resolution process again. The servers do not apply a fixed time to remove the outdated information; instead, they allow the authority to enter in a Time To Live (TTL) value to specify how long it guarantees the binding to be valid.[1]
Caching can also be done on the host itself. If the user looks up the same name repeatedly, the subsequent look ups can be retrieved from its cache without using the network.
Security Concerns
DNS was implemented with little security in mind; as a result, DNS has a number of security issues. Firstly, authentication using the domain name of the source host alone is much weaker than using the IP address alone.[6] Thus, host names are easily spoofed. In addition, some domain names can easily spoof other domain names that look similar. For instance, “www.paypal.com” and “www.paypa1.com” are two different domain names; however, users might be tricked and unable to tell the difference between the two because the alphabet ‘l’ looks very similar to the number ‘1’ in certain fonts. In some fonts, the two domain names might even look identical. Another security issue is that attackers might try to corrupt or replace certain information in the DNS.[6] This could cause packets to be misdirected. Even worst, the attacker could make IP addresses of that name server to redirect everything to a malicious address with a long TTL.
DNS is an effective tool for probing organization’s network. With that in mind, it is important for the organization to secure and hide its DNS information regarding its internal network from Internet.[6]
Domain Registration
The right to use a domain name is authorized by domain name registrars.[7] In addition, domain name registrars are accredited by ICANN.[7] Each top-level domain (TLD) is maintained by InterNIC, which is also operated by ICANN. InterNIC receives domain name registration information provided by the domain name registrars and publishes the information.[7] There is an annual fee for the service of authorizing domain name to a user. The authorized users are known as “registrants” or as “domain holders”.
References
- Comer, D. E. (2006). The domain name system (DNS). Internetworking with TCP/IP (Fifth ed., pp. 419-441). Upper Saddle River, NJ: Pearson Prentice Hall.
- "What is DNS?: Domain Name System(DNS)". Retrieved on 2009-04-07
- "History of the Domain Name System". Retrieved on 2009-04-07.
- "History of Domain Name System". Retrieved on 2009-04-07.
- "ICANN | About gTLDs". Retrieved on 2009-04-09.
- William, F. M. (2009). Domain Name System (DNS). In Lecture 09: Common Network Services.
- "ICANN | FAQs". Retrieved on 2009-04-09.
See Also
- Dynamic DNS
- DNS Security Extensions (DNSSEC)
- DNS Management Software
- Comparison Of DNS Server Software
- DHCP
External Links
- How DNS Works: Domain Name System(DNS)
- Internet Corporation for Assigned Names and Numbers (ICANN)
- DNS Complexity
- DNS For Rocket Scientists: An Open Source Guide of DNS
- DNS & BIND
--Jacky Ng (Ngck) 20:18, 12 April 2009 (EDT)