Digital Signatures
From Computing and Software Wiki
Digital Signatures are a type of asymmetric cryptography [1] or used to simulate the security properties of a handwritten signature on paper. Digital signature schemes normally give two algorithms, one for signing which involves the user's secret or private key, and one for verifying signatures which involves the user's public key. The output of the signature process is called the "digital signature."

Digital signatures are created and verified by cryptography, the branch of applied mathematics that concerns itself with transforming messages into seemingly unintelligible forms and back again.[6].
There is confusion between the terms electronic signature [2] and digital signature. Most, especially those with an information theory or cryptography background, use "digital signature" to refer to a digital signature protocol using cryptographic techniques, as is sometimes applied to an 'electronic document'. Many, however, use the terms interchangeably, leading to considerable confusion as cryptographic signature techniques are very different, whatever the term used, than other electronic signatures and have extremely different security properties. Since it is the security properties which are of interest in signatures of all kinds, this is a very significant distinction. Digital signature is properly a subset of electronic signature.
Contents |
History
The history of cryptography begins thousands of years ago. Until recent decades, it has been the story of what might be called classic cryptography — that is, of methods of encryption that use pen and paper, or perhaps simple mechanical aids. In the early 20th century, the invention of complex mechanical and electromechanical machines, such as the Enigma rotor machine, provided more sophisticated and efficient means of encryption; and the subsequent introduction of electronics and computing has allowed elaborate schemes of still greater complexity, most of which are entirely unsuited to pen and paper.
The first invention of asymmetric key algorithms was by James H. Ellis, Clifford Cocks, and Malcolm Williamson at GCHQ in the UK in the early 1970s; these inventions were what later became known as Diffie-Hellman key exchange, and a special case of RSA. The GCHQ cryptographers referred to the technique as "non-secret encryption". These inventions were not publicly disclosed at the time, and the fact that they had been developed was kept secret until 1997.
The first widely marketed software package to offer digital signature was Lotus Notes 1.0, released in 1989, which used the RSA algorithm [3].
Cryptography
Cryptography is the practice and study of hiding information. In modern times, cryptography is considered to be a branch of both mathematics and computer science, and is affiliated closely with information theory, computer security, and engineering. Cryptography is used in applications present in technologically advanced societies; examples include the security of ATM cards, computer passwords, and electronic commerce, which all depend on cryptography.
Asymmetric key
Asymmetric cryptography [4], is a form of cryptography in which a user has a pair of cryptographic keys—a public key and a private key. The private key is kept secret, while the public key may be widely distributed. The keys are related mathematically, but the private key cannot be practically derived from the public key. A message encrypted with the public key can be decrypted only with the corresponding private key.
Symmetric key
Symmetric cryptography [5] refers to encryption methods in which both the sender and receiver share the same key (or, less commonly, in which their keys are different, but related in an easily computable way). This was the only kind of encryption publicly known until June 1976. Symmetric authentication keys are used with symmetric key algorithms to provide assurance of the integrity and source of messages, communication sessions, or stored data.
Digital Signature
A digital signature scheme typically consists of three algorithms
- A key generation algorithm G that randomly produces a "key pair" (PK, SK) for the signer. PK is the verifying key, which is to be public, and SK is the signing key, to be kept private.
- A signing algorithm S, that on input of a message m and a signing key SK, produces a signature σ.
- A signature verifying algorithm V, that on input of a message m, a verifying key PK and a signature σ, either accepts or rejects.
Two main properties are required. First, signatures computed honestly should always verify. That is, V should accept (m, PK, S (m, SK)) where SK is the secret key related to PK, for any message m. Secondly, it should be hard for any adversary, knowing only PK, to create valid signature(s).
How Does it work?
To make it easier, check the following example
The components that a digital signature comprise of are [7].
- Your public key: This is the part that any one can get a copy of and is part of the verification system.
- Your name and e-mail address: This is necessary for contact information purposes and to enable the viewer to identify the details.
- Expiration date of the public key: This part of the signature is used to set a shelf life and to ensure that in the event of prolonged abuse of a signature eventually the signature is reset.
- Name of the company: This section identifies the company that the signature belongs too.
- Serial number of the Digital ID: This part is a unique number that is bundled to the signature for tracking ad extra identification reasons.
- Digital signature of the CA (certification Authority): This is a signature that is issued by the authority that issues the certificates.
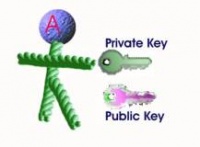
User A is depicted above and has two keys a public key, this key is available to the public for download, and a private key, this key is not available to the public. All keys are used to lock the information in an encrypted mode. The same keys are required to decrypt the data.
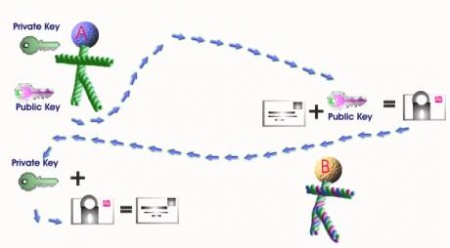
Another user can encrypt the data using users A’s Public Key. User A will use the Private Key to decrypt the message. Without user A’s Private Key the data can not be decrypted. Figure B below depicts the encryption method and decryption method and witch keys are used.
Digital signature can be used to make document e-mails and other data private. Big brother is out there and choosing a high encryption mechanism ensures that any one attempting to decrypt the data would find it unviable to attempt decryption.
User A’s machine digests the data into a simple string of code after user A’s software has encrypted the message digest with his private key. The result is the digital signature. User A’s software then appends the digital signature to document. All of the data that was hashed has been signed. User A then passes the digitally signed document to user B.
First user B’s software decrypts the signature, using User A’s public key then changing it back into a message digest. After the decryption if it has decrypted the data to digest level then verifies that user A in fact did sign the data. To stop fraud certificate authorities have been introduced. Certificate authorities can sign User A’s public key, ensuring that no one else uses Bobs information or impersonated his key.
If a user is uncertain of the digital signature it is possible to verify the digital signature with the certificate authority. Signatures can also be revoked if they are abused or if it is suspected that they are abused. When a digital signature is compromised the user that suspects that the certificate is compromised should report the incident to the certificate authority.
The process of checking the validity of digital signature.
- User A sends a signed document to User B.
- To verify the signature on the document, user B’s application first uses the certificate authority's public key to check the signature on user A’s certificate.
- Successful de-encryption of the certificate proves that the certificate authority created it.
- After the certificate is de-encrypted, user B’s software can check if user A is in good standing with the certificate authority and that all of the certificate information concerning user A’s identity has not been altered.
- User B’s software then takes user A’s public key from the certificate and uses it to check user A’s signature. If user A’s public key de-encrypts the signature successfully, then user B is assured that the signature was created using user A’s private key, for the certificate authority has certified the matching public key.
- If the signature is found to be valid, then we know that an intruder didn't try to change the signed content.
Benefits
Below are some common reasons for applying a digital signature to communications
- Digital signatures can be used to authenticate the source of messages. When ownership of a digital signature secret key is bound to a specific user, a valid signature shows that the message was sent by that user. The importance of high confidence in sender authenticity is especially obvious in a financial context.
- It ensures data Integrity giving the user piece of mind that the message or transaction has not been accidentally or maliciously altered. This is done cryptographically.
- Digital signature ensures confidentiality and ensure that messages can only be read by authorized intended recipients.
- Digital certificates also verify date and time so that senders or recipients can not dispute if the message was actually sent or received.
Algorithms
There are some algorithms that can be used in digital signature, there are some examples below:
- Full Domain Hash, RSA-PSS etc., based on RSA (see more about RSA on Public Key Encryption Algorithms)
- DSA
- ECDSA
- Rabin signature algorithm
- Pointcheval-Stern signature algorithm
- Schnorr signature
Digital Signature Algorithm (DSA) is appropriate for applications requiring a digital rather than written signature. The DSA digital signature is a pair of large numbers represented in a computer as strings of binary digits. The digital signature is computed using a set of rules (i.e., the DSA) and a set of parameters such that the identity of the signatory and integrity of the data can be verified. The DSA provides the capability to generate and verify signatures.
How/Where it can be used?
Smart Cards
Most advanced smart cards [8] are equipped with specialized cryptographic hardware that let you use algorithms such as RSA and DSA on board. Today's cryptographic smart cards are also able to generate key pairs on board, to avoid the risk of having more than one copy of the key (since by design there usually isn't a way to extract private keys from a smart card).
Such smart cards are mainly used for digital signature and secure identification.
A realy secure alternative is to store the private key on a smart card. Many smart cards are deliberately designed to be tamper resistant (however, quite a few designs have been broken, notably by Ross Anderson and his students). In a typical implementation, the hash calculated from the document is sent to the smart card, whose CPU encrypts the hash using the stored private key of the user and returns it. Typically, a user must activate his smart card by entering a personal identification number or PIN code (thus providing a two-factor authentication). Note that it can be sensibly arranged (but is not always done) that the private key never leaves the smart card. If the smart card is stolen, the thief will still need the PIN code to generate a digital signature. This reduces the security of the scheme to that of the PIN system, but is nevertheless more secure than are many PCs. A mitigating factor, however, is that private keys, if generated and stored on smart cards, are usually regarded as not easy to copy, and thus often assumed to exist in exactly one copy. Thus, the loss of the smart card may be detected by the owner and the corresponding certificate may (and in fact, should) be immediately revoked. Private keys that are protected by software only may be easier to copy, and such compromises are far more difficult to detect.
Using smart card readers with a separate keyboard
Entering a PIN code to activate the smart card, commonly requires a numeric keypad. Some card readers have their own numeric keypad. This is safer than using a card reader integrated into a PC, and then entering the PIN using that computer's keyboard. The computer might be running a keystroke logger (by its owner/operators intention or otherwise -- due to a virus, for instance) so that the PIN code becomes compromised. Specialized card readers are less vulnerable, though not invulnerable, against tampering with their software or hardware. And, of course, eavesdropping attacks against all such equipment are possible.
Digital Certificate
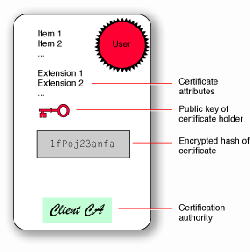
A digital certificate is an electronic "credit card" that establishes your credentials when doing business or other transactions on the Web. It is issued by a certification authority (CA). It contains your name, a serial number, expiration dates, a copy of the certificate holder's public key (used for encrypting messages and digital signatures), and the digital signature of the certificate-issuing authority so that a recipient can verify that the certificate is real.[11] Some digital certificates conform to a standard X.509. Digital certificates can be kept in registries so that authenticating users can look up other users' public keys.
The CA verifies that a public key belongs to a specific company or individual (the "subject"), and the validation process it goes through to determine if the subject is who it claims to be depends on the level of certification and the CA itself.
Creating the Certificate After the validation process is completed, the CA creates an X.509 certificate that contains CA and subject information, including the subject's public key (details below). The CA signs the certificate by creating a digest (a hash) of all the fields in the certificate and encrypting the hash value with its private key. The encrypted digest is called a "digital signature," and when placed into the X.509 certificate, the certificate is said to be "signed."
The CA keeps its private key very secure, because if ever discovered, false certificates could be created. See HSM.
Verifying the Certificate The process of verifying the "signed certificate" is done by the recipient's software, which is typically the Web browser. The browser maintains an internal list of popular CAs and their public keys and uses the appropriate public key to decrypt the signature back into the digest. It then recomputes its own digest from the plain text in the certificate and compares the two. If both digests match, the integrity of the certificate is verified (it was not tampered with), and the public key in the certificate is assumed to be the valid public key of the subject.
At this point, the subject's identity and the certificate's integrity (no tampering) have been verified. The certificate is typically combined with a signed message or signed executable file, and the public key is used to verify the signatures. The subject's public key may also be used to provide a secure key exchange in order to have an encrypted two-way communications session.
Security
Reasons for using digital security.
- It insures by means of verification and validation that the user is whom he/she claims to be. This is done by combine the users credential to the digital certificate and in turn this method uses one point of authentication.
- Digital certificates insure data Integrity giving the user piece of mind that the message or transaction has not been accidentally or maliciously altered. This is done cryptographically.
- Digital certificates ensure confidentiality and ensure that messages can only be read by authorized intended recipients.
- Digital certificates also verify date and time so that senders or recipients can not dispute if the message was actually sent or received.
How to increase safeness
- Using Smart card: A good way to increase safeness that was mention before(see smart card section) is to use smart card to store the private key. (see Smart Card technology to prevent fraud )
- Using digital signatures only with trusted applications
One of the main differences between a digital signature and a written signature is that the user does not "see" what he signs. The user application presents a hash code to be encrypted by the digital signing algorithm using the private key. An attacker who gains control of the user's PC can possibly replace the user application with a foreign subsitute, in effect replacing the user's own communications with that of the attacker's. Thus, the malicious application can trick the unwitting user into signing any document by displaying the user's original on-screen, but presenting the attacker's own documents (probably less favorable) to the signing application.
To protect against this scenario, a authentication system can be setup between the user-application (word-processor, email client, etc.) and the signing-application. The general idea is to provide some means for both the user app and signing app to verify each other's integrity. (For example, the signing application may require all requests to come from digitally-signed binaries.)
See Also
References
- Asymetric key algorithm. Retrieved on March 29th 2008, from <http://en.wikipedia.org/wiki/Asymmetric_key_algorithm>
- Electronic Signature. Retrieved on March 29th 2008, from <http://en.wikipedia.org/wiki/Electronic_signature>
- RSA Algorithm. Retrieved on April 1th 2008, from <http://www.di-mgt.com.au/rsa_alg.html>
- Assymetric Cryptography. Retrieved on April 1th 2008, from <http://www.cs.cornell.edu/Courses/cs513/2007fa/TL04.asymmetric.html>
- Symetric Cryptography. Retrieved on April 1th 2008, from <http://www.cs.bham.ac.uk/~mdr/teaching/modules04/security/lectures/symmetric-key.html
- Digital Signature Guidelines Tutorial. Retrieved on April 1th 2008, from <http://www.abanet.org/scitech/ec/isc/dsg-tutorial.html>
- Digital Signatures <http://www.windowsecurity.com/articles/Digital_Signatures.html>
- Smart Cards. Retrieved on April 2th 2008, from <http://en.wikipedia.org/wiki/Smart_card>
- http://www.infosecwriters.com/text_resources/pdf/Public_Key_Cryptography_AMS.pdf
- http://www.state.sc.us/scdah/erg/ermEDS.pdf
- Digital Certificate. Retrieved on April 2th 2008, from <http://searchsecurity.techtarget.com/sDefinition/0,,sid14_gci211947,00.html>
External links
--Ribeirag 17:38, 5 April 2008 (EDT)