Conventional Encryption Algorithms
From Computing and Software Wiki
(Difference between revisions)
| Line 18: | Line 18: | ||
[2] [http://en.wikipedia.org/wiki/Identity_2.0/ Identity 2.0] Wikipedia.org | [2] [http://en.wikipedia.org/wiki/Identity_2.0/ Identity 2.0] Wikipedia.org | ||
| + | |||
| + | == External Links == | ||
[http://www.ling.ohio-state.edu/~cbrew/2008/winter/484/monoalphabetic.pdf Monoalphabetic Ciphers] | [http://www.ling.ohio-state.edu/~cbrew/2008/winter/484/monoalphabetic.pdf Monoalphabetic Ciphers] | ||
| - | [[User:Angiusei|Elian]] | + | [[User:Angiusei|Elian]] April 8/2008 |
Revision as of 14:45, 8 April 2008
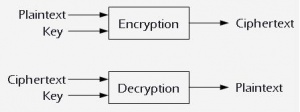
Conventional Encryption is ...
Contents |
Classification of Ciphers
Monoalphabetic Ciphers
Polyalphabetic Ciphers
Transposition Ciphers
Synchronous Stream Ciphers
Asynchronous Stream Ciphers
Popular Algorithms
References
[1] Identity 2.0 Keynote Sxip Identity Video
[2] Identity 2.0 Wikipedia.org
External Links
Elian April 8/2008