Computer Network Traffic Shaping
From Computing and Software Wiki
(→Uses) |
|||
| (7 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
Traffic shaping (also referred to as packet shaping) is the technique of delaying and restricting certain packets traveling through a network to increase the performance of packets that have been given priority. Classes are defined to separate the packets into groupings so that they can each be shaped separately allowing some classes to pass through a network more freely than others. Traffic shapers are usually placed at the boundaries of a network to either shape the traffic going entering or leaving a network. Traffic shaping does not actually speed up a networks total thoughput. It is a tool used to help manage a network's resources. | Traffic shaping (also referred to as packet shaping) is the technique of delaying and restricting certain packets traveling through a network to increase the performance of packets that have been given priority. Classes are defined to separate the packets into groupings so that they can each be shaped separately allowing some classes to pass through a network more freely than others. Traffic shapers are usually placed at the boundaries of a network to either shape the traffic going entering or leaving a network. Traffic shaping does not actually speed up a networks total thoughput. It is a tool used to help manage a network's resources. | ||
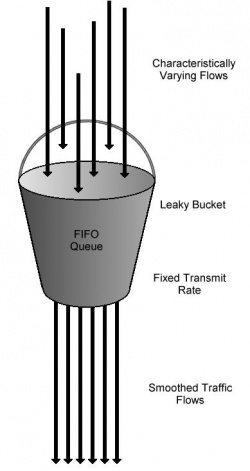
| - | + | [[Image:LeakyBucket.jpg|thumbnail|right|250px|A Leaky Bucket implementation of Traffic Shaping[1]]] | |
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
== Implementations == | == Implementations == | ||
===Leaky bucket=== | ===Leaky bucket=== | ||
| - | + | A leaky bucket is a fifo buffer used to store incoming/outgoing traffic. It then leaks out packets at a set rate slowing down incoming or outgoing traffic to a desired rate. For different classes separate fifos are used to store the incoming packets. Each bucket is set to leak out packets at different rates allowing some classes to have a higher throughput than other classes. When excessive traffic causes the buffer to overflow additional incoming traffic can either be lost, or even let through. A Random Early Discard algorithm may may also be used to deal with overflow. | |
| - | A leaky bucket is a fifo buffer used to store incoming/outgoing traffic. It then leaks out packets at a set rate slowing down incoming or outgoing traffic to a desired rate. For different classes separate fifos are used to store the incoming packets. Each bucket is set to leak out packets at different rates allowing some classes to have a higher throughput than other classes. When excessive traffic causes the buffer to overflow additional incoming traffic | + | |
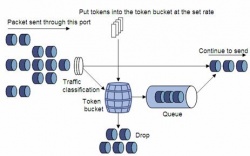
===Token Bucket=== | ===Token Bucket=== | ||
| - | A Token bucket is Similar to a Leaky bucket except that it uses tokens which are added to the bucket at a set rate r. At most n tokens can be stored in the bucket. Packets are allowed to pass through the bucket only if there are enough tokens in the bucket to allow it. Tokens are removed from the bucket as traffic is allowed to pass through. Like a Leaky Bucket Token Bucket only lets traffic through at a set rate r overall, the difference is that Token bucket allows burst speeds of up to n can occur if tokens are allowed to accumulate in the bucket. | + | [[Image:Tokenbucket.jpg|thumbnail|right|250px|A Token Bucket implementaion[2]]] |
| - | + | A Token bucket is Similar to a Leaky bucket except that it uses tokens which are added to the bucket at a set rate r. At most n tokens can be stored in the bucket. Packets are allowed to pass through the bucket only if there are enough tokens in the bucket to allow it. Tokens are removed from the bucket as traffic is allowed to pass through. Like a Leaky Bucket Token Bucket only lets traffic through at a set rate r overall, the difference is that Token bucket allows burst speeds of up to n can occur if tokens are allowed to accumulate in the bucket. | |
== Costs and Benefits == | == Costs and Benefits == | ||
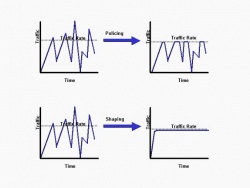
| + | [[Image:ShapingvsPolicing.jpg|thumbnail|right|250px|A comparison of Shaping versus Policing[3]]] | ||
One of the disadvantages with traffic shaping is that it usually doesn't take into account availability of network resources. Since the throughput of network traffic is fixed it won't make use of additional bandwidth if its available. | One of the disadvantages with traffic shaping is that it usually doesn't take into account availability of network resources. Since the throughput of network traffic is fixed it won't make use of additional bandwidth if its available. | ||
| - | + | Traffic shaping can also make network traffic more consistent when it tends to come in bursts. That is when traffic exceeds a set rate it is stored in a buffer. This is unlike Traffic Policing in which excessive traffic is lost. | |
| + | |||
Applying traffic shaping to improve network performance can be a cheaper solution than upgrading a network's hardware. | Applying traffic shaping to improve network performance can be a cheaper solution than upgrading a network's hardware. | ||
| - | |||
| - | |||
== Uses == | == Uses == | ||
| - | Traffic shaping is used to help | + | Traffic shaping is used to help organizations with centralized servers that are under heavy traffic manage their resources. |
| - | + | ||
| - | ''' | + | '''ATM's''' - Automatic Bank tellers are a good example where Traffic shaping is used. Here a Leaky Bucket algorithm to help manage traffic[4]. |
| - | Internet Service providers will use traffic shaping | + | |
| + | '''ISP's''' - Internet Service providers will use traffic shaping to classify packets that depend on good latency in one class and then provide lower latency to these packets. For example packets for VoIP and gaming will be in a class that provides better throughput. Thus more of the bandwidth is made available for these packets by slowing down traffic that does not depend on good latency. An example of traffic an ISP would want to throttle is that caused by Torrents. Torrents take up a considerable amount of an ISP's bandwidth. Often users have torrents running in the background so having this traffic slowed down causes little inconvenience. | ||
== References == | == References == | ||
| - | 1. | + | 1.Computer Desktop Encyclopedia: leaky bucket, Answers.com. http://www.answers.com/topic/leaky-bucket?cat=technology |
| - | + | ||
| - | + | ||
| - | + | ||
| + | 2. QoS Introduction, H3C Technologies Co., Limited. http://www.h3c.com/portal/Products___Solutions/Technology/QoS/QoS/200701/195599_57_0.htm | ||
| + | |||
| + | 3. Comparing Traffic Policing and Traffic Shaping for Bandwidth Limiting, Cisco Systems, Inc. Aug 10, 2005. http://www.cisco.com/warp/public/105/policevsshape.html | ||
| + | |||
| + | 4. Traffic Shaping in an ATM Environment, Prabhakar T V1, Burkhard Stiller, Thomas Walter, nstitut für Technische Informatik und Kommunikationsnetze TIK ETH Zürich, Gloriastrasse 35, CH – 8092 Zürich, Schweiz | ||
== See Also == | == See Also == | ||
[[BitTorrent]] | [[BitTorrent]] | ||
| + | [[Network-Based Software Architectures]] | ||
| + | |||
| + | [[Bandwidth Throttling]] | ||
==External Links== | ==External Links== | ||
http://e-collection.ethbib.ethz.ch/show?type=incoll&nr=379&part=text | http://e-collection.ethbib.ethz.ch/show?type=incoll&nr=379&part=text | ||
| + | |||
| + | http://en.wikipedia.org/wiki/Traffic_shaping | ||
| + | |||
| + | http://www.linuxdevcenter.com/pub/a/linux/2000/08/24/LinuxAdmin.html | ||
--[[User:Younga3|Younga3]] 11:46, 9 April 2008 (EDT)Andrew Young | --[[User:Younga3|Younga3]] 11:46, 9 April 2008 (EDT)Andrew Young | ||
Current revision as of 23:29, 11 April 2008
Traffic shaping (also referred to as packet shaping) is the technique of delaying and restricting certain packets traveling through a network to increase the performance of packets that have been given priority. Classes are defined to separate the packets into groupings so that they can each be shaped separately allowing some classes to pass through a network more freely than others. Traffic shapers are usually placed at the boundaries of a network to either shape the traffic going entering or leaving a network. Traffic shaping does not actually speed up a networks total thoughput. It is a tool used to help manage a network's resources.
Contents |
Implementations
Leaky bucket
A leaky bucket is a fifo buffer used to store incoming/outgoing traffic. It then leaks out packets at a set rate slowing down incoming or outgoing traffic to a desired rate. For different classes separate fifos are used to store the incoming packets. Each bucket is set to leak out packets at different rates allowing some classes to have a higher throughput than other classes. When excessive traffic causes the buffer to overflow additional incoming traffic can either be lost, or even let through. A Random Early Discard algorithm may may also be used to deal with overflow.
Token Bucket
A Token bucket is Similar to a Leaky bucket except that it uses tokens which are added to the bucket at a set rate r. At most n tokens can be stored in the bucket. Packets are allowed to pass through the bucket only if there are enough tokens in the bucket to allow it. Tokens are removed from the bucket as traffic is allowed to pass through. Like a Leaky Bucket Token Bucket only lets traffic through at a set rate r overall, the difference is that Token bucket allows burst speeds of up to n can occur if tokens are allowed to accumulate in the bucket.
Costs and Benefits
One of the disadvantages with traffic shaping is that it usually doesn't take into account availability of network resources. Since the throughput of network traffic is fixed it won't make use of additional bandwidth if its available.
Traffic shaping can also make network traffic more consistent when it tends to come in bursts. That is when traffic exceeds a set rate it is stored in a buffer. This is unlike Traffic Policing in which excessive traffic is lost.
Applying traffic shaping to improve network performance can be a cheaper solution than upgrading a network's hardware.
Uses
Traffic shaping is used to help organizations with centralized servers that are under heavy traffic manage their resources.
ATM's - Automatic Bank tellers are a good example where Traffic shaping is used. Here a Leaky Bucket algorithm to help manage traffic[4].
ISP's - Internet Service providers will use traffic shaping to classify packets that depend on good latency in one class and then provide lower latency to these packets. For example packets for VoIP and gaming will be in a class that provides better throughput. Thus more of the bandwidth is made available for these packets by slowing down traffic that does not depend on good latency. An example of traffic an ISP would want to throttle is that caused by Torrents. Torrents take up a considerable amount of an ISP's bandwidth. Often users have torrents running in the background so having this traffic slowed down causes little inconvenience.
References
1.Computer Desktop Encyclopedia: leaky bucket, Answers.com. http://www.answers.com/topic/leaky-bucket?cat=technology
2. QoS Introduction, H3C Technologies Co., Limited. http://www.h3c.com/portal/Products___Solutions/Technology/QoS/QoS/200701/195599_57_0.htm
3. Comparing Traffic Policing and Traffic Shaping for Bandwidth Limiting, Cisco Systems, Inc. Aug 10, 2005. http://www.cisco.com/warp/public/105/policevsshape.html
4. Traffic Shaping in an ATM Environment, Prabhakar T V1, Burkhard Stiller, Thomas Walter, nstitut für Technische Informatik und Kommunikationsnetze TIK ETH Zürich, Gloriastrasse 35, CH – 8092 Zürich, Schweiz
See Also
Network-Based Software Architectures
External Links
http://e-collection.ethbib.ethz.ch/show?type=incoll&nr=379&part=text
http://en.wikipedia.org/wiki/Traffic_shaping
http://www.linuxdevcenter.com/pub/a/linux/2000/08/24/LinuxAdmin.html
--Younga3 11:46, 9 April 2008 (EDT)Andrew Young