Computer Network Traffic Shaping
From Computing and Software Wiki
| Line 1: | Line 1: | ||
| - | Traffic shaping (also referred to as packet shaping) is the technique of delaying and restricting certain packets traveling through a network to increase the performance of packets that have been given priority. | + | Traffic shaping (also referred to as packet shaping) is the technique of delaying and restricting certain packets traveling through a network to increase the performance of packets that have been given priority. Classes are defined to separate the packets into groupings so that they can each be shaped separately allowing some classes to pass through a network more freely than others. Traffic shapers are usually placed at the boundaries of a network to either shape the traffic going entering or leaving a network. |
| Line 5: | Line 5: | ||
| - | == Implementations == | + | == Implementations == |
| - | + | ||
===Leaky bucket=== | ===Leaky bucket=== | ||
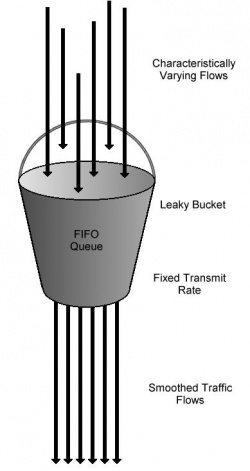
| - | + | A leaky bucket is a fifo buffer used to store incoming/outgoing traffic. It then leaks out packets at a set rate slowing down incoming or outgoing traffic to a desired rate. For different classes separate fifos are used to store the incoming packets. Each bucket is set to leak out packets at different rates allowing some classes to have a higher throughput than other classes. | |
| - | A leaky bucket is a buffer used to store incoming/outgoing traffic. It then leaks out packets at a set rate slowing down incoming or outgoing traffic to a desired rate. | + | |
[[Image:LeakyBucket.jpg|thumbnail|right|250px|Leaky Bucket]] | [[Image:LeakyBucket.jpg|thumbnail|right|250px|Leaky Bucket]] | ||
===Token Bucket=== | ===Token Bucket=== | ||
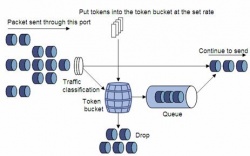
| - | A Token bucket | + | A Token bucket uses tokens which are added to the bucket at a set rate r. At most n tokens can be stored in the bucket. Packets are allowed to pass through the bucket only if there are enough tokens in the bucket to allow it. Tokens are removed from the bucket as traffic is allowed to pass through. Similar to Leaky Bucket Token Bucket only lets traffic through at a set rate r overall, the difference is that Token bucket allows burst speeds of up to n can occur if tokens are allowed to accumulate in the bucket. |
[[Image:Tokenbucket.jpg|thumbnail|right|250px|Token Bucket]] | [[Image:Tokenbucket.jpg|thumbnail|right|250px|Token Bucket]] | ||
== Costs and Benefits == | == Costs and Benefits == | ||
| + | One of the disadvantages with traffic shaping is that it usually doesnt take into account availability of network ersources | ||
| + | Overflow | ||
| + | TheCost | ||
| + | == Uses == | ||
| + | Traffic shaping is used to help manage organizations with centralized servers that are under heavy traffic. | ||
| + | For example ATM's are known to use the Leaky Bucket algorthm[1]. | ||
| - | + | '''ISP's''' | |
| - | + | Internet Service providers will use traffic shaping increase performance of traffic that depends on good delivery times. For example packets for VoIP and gaming will in class of packets that provide a better throughput. Thus more of the limited bandwidth is made available for these packets by slowing down traffic that does not depend on latency. An example of this would be Torrents. Often users have torrents running in the background so having there traffic slowed down causes little inconvenience. | |
| - | Internet Service providers will use traffic shaping increase performance of traffic that depends on good delivery times. | + | |
| - | + | ||
== References == | == References == | ||
| + | |||
| + | 1. Traffic Shaping in an ATM Environment | ||
| + | |||
http://www.h3c.com/portal/Products___Solutions/Technology/QoS/QoS/200701/195599_57_0.htm | http://www.h3c.com/portal/Products___Solutions/Technology/QoS/QoS/200701/195599_57_0.htm | ||
http://www.answers.com/topic/leaky-bucket?cat=technology | http://www.answers.com/topic/leaky-bucket?cat=technology | ||
| + | |||
== See Also == | == See Also == | ||
Revision as of 22:08, 11 April 2008
Traffic shaping (also referred to as packet shaping) is the technique of delaying and restricting certain packets traveling through a network to increase the performance of packets that have been given priority. Classes are defined to separate the packets into groupings so that they can each be shaped separately allowing some classes to pass through a network more freely than others. Traffic shapers are usually placed at the boundaries of a network to either shape the traffic going entering or leaving a network.
Contents |
Implementations
Leaky bucket
A leaky bucket is a fifo buffer used to store incoming/outgoing traffic. It then leaks out packets at a set rate slowing down incoming or outgoing traffic to a desired rate. For different classes separate fifos are used to store the incoming packets. Each bucket is set to leak out packets at different rates allowing some classes to have a higher throughput than other classes.
Token Bucket
A Token bucket uses tokens which are added to the bucket at a set rate r. At most n tokens can be stored in the bucket. Packets are allowed to pass through the bucket only if there are enough tokens in the bucket to allow it. Tokens are removed from the bucket as traffic is allowed to pass through. Similar to Leaky Bucket Token Bucket only lets traffic through at a set rate r overall, the difference is that Token bucket allows burst speeds of up to n can occur if tokens are allowed to accumulate in the bucket.
Costs and Benefits
One of the disadvantages with traffic shaping is that it usually doesnt take into account availability of network ersources Overflow TheCost
Uses
Traffic shaping is used to help manage organizations with centralized servers that are under heavy traffic. For example ATM's are known to use the Leaky Bucket algorthm[1].
ISP's Internet Service providers will use traffic shaping increase performance of traffic that depends on good delivery times. For example packets for VoIP and gaming will in class of packets that provide a better throughput. Thus more of the limited bandwidth is made available for these packets by slowing down traffic that does not depend on latency. An example of this would be Torrents. Often users have torrents running in the background so having there traffic slowed down causes little inconvenience.
References
1. Traffic Shaping in an ATM Environment
http://www.h3c.com/portal/Products___Solutions/Technology/QoS/QoS/200701/195599_57_0.htm http://www.answers.com/topic/leaky-bucket?cat=technology
See Also
External Links
--Younga3 11:46, 9 April 2008 (EDT)Andrew Young