Blowfish
From Computing and Software Wiki
In cryptography, Blowfish is symmetric block cipher, designed in 1993 by Bruce Schneier. It is a fast and compact, that is, it provides a good encryption rate in software. There still exists no effective cryptanalysis of the algorithm and is therefore considered an extremely strong algorithm.
Blowfish was designed as an algorithm that could be used in everyday life by everybody, intended as a replacement of the Data Encryption Standard (DES). At that time most of the encryption algorithms in use were proprietary or kept secret by the governments, Blowfish broke away from that standard and Schneier placed it in the public domain to be used by anyone free of cost.
Blowfish Algorithm
Blowfish encrypts data in 64-bits blocks and has a variable key length between 32 and 448 bits. Also as Blowfish is a symmetric encryption algorithm, it uses the same secret key to encrypt and decrypt messages. A graphical representation of the blowfish algorithm can be seen in Figure 1.
In this figure we can see, a 64-bit plaintext message is first divided into 32 bits. The "left" 32 bits are XORed with the first element of a P-array to create a value P', run through a transformation function called F, then XORed with the "right" 32 bits of the message to produce a new value F'. F' then replaces the "left" half of the message and P' replaces the "right" half, and the process is repeated 15 more times with successive members of the P-array. The resulting P' and F' are then XORed with the last two entries in the P-array (entries 17 and 18), and recombined to produce the 64-bit ciphertext.
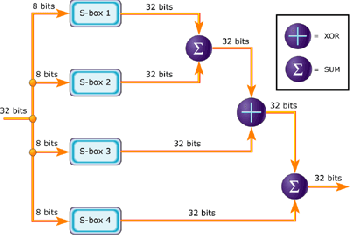
Figure 2 shows a graphical representation of F, The function divides a 32-bit input into four bytes and uses those as indices into an S-array. The lookup results are then added and XORed together to produce the output. As previously mentioned blowfish is a symmetric algorithm and therefore employs the same technique to decrypt a message. The only difference being the output is in plain-text. The P-array and S-array values used by Blowfish are precomputed based on the user's key. In effect, the user's key is transformed into the P-array and S-array; the key itself may be discarded after the transformation. The P-array and S-array need not be recomputed (as long as the key doesn't change), but must remain secret.
![Figure 1 Blowfish Algorithm. [1 ]](/images/5/51/Blowfish_alg.gif)