Biometric Systems and Security Design Principles
From Computing and Software Wiki
| (12 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
'''Analysis of Biometric Systems using Security Design Principles''' | '''Analysis of Biometric Systems using Security Design Principles''' | ||
| - | Biometric security systems are authentication mechanisms that bind an entity to a subject based on what the entity is, as opposed to what they know, what they have, or where they are. | + | Biometric security systems<sup>[http://www.cafesoft.com/support/security-glossary.html R1]</sup> are authentication mechanisms that bind an entity to a subject based on what the entity is, as opposed to what they know, what they have, or where they are. |
| - | Within the past several years, biometric security systems have gained a lot of ground in terms of advancements in technology and widespread use | + | |
| + | Within the past several years, biometric security systems have gained a lot of ground in terms of advancements in technology and widespread use however, there is still a lot of reluctance to adopt the technology worldwide<sup>[http://en.wikipedia.org/wiki/Biometrics#Issues_and_concerns R2]</sup>. A look at biometric security systems through security design principles should provide a clearer understanding of its strengths and weaknesses in the implementation and design of biometric security systems. | ||
[[Image:3dface.jpg|thumb|3D Face Recognition Software]] | [[Image:3dface.jpg|thumb|3D Face Recognition Software]] | ||
| - | ==Biometrics== | + | =='''Biometrics'''== |
| - | Biometrics is the identification of a person through automated measurements using biological or behavioural features | + | Biometrics is the identification of a person through automated measurements using biological or behavioural features<sup>[[Biometrics in Information Security#Types of Measurements|R3]]</sup> |
| - | ==Security Design Principles== | + | =='''Security Design Principles'''== |
| - | The following eight design principles were created by | + | The following eight design principles were created by Salzter<sup>[http://en.wikipedia.org/wiki/Jerome_H._Saltzer E1]</sup> and Schroeder<sup>[http://en.wikipedia.org/wiki/Michael_Schroeder E2]</sup> for the design and implementation of security mechanisms<sup>R4</sup>. These design principles encompass technical details and human interaction that make designs and mechanisms easy to understand. They are also simple and easy to understand, which is why they will be used as a guide to analyze biometric security systems. The list of design principles are as follows: |
'''Principle of Least Privilege:''' | '''Principle of Least Privilege:''' | ||
| Line 38: | Line 39: | ||
| - | ==Breaking a Biometrics Security System== | + | =='''Breaking a Biometrics Security System'''== |
| - | In addition to looking at biometric security systems from a design and implementation perspective, understanding a biometrics security system from an attacker’s perspective is also important. In general, there are seven different types of attacks. These types of attacks are categorized by their attacks on a specific part of the design. They can be divided into the following: | + | In addition to looking at biometric security systems from a design and implementation perspective, understanding a biometrics security system from an attacker’s perspective is also important. In general, there are seven different types of attacks<sup>R5</sup>. These types of attacks are categorized by their attacks on a specific part of the design. They can be divided into the following: |
'''Type 1:''' Fake biometric sensor | '''Type 1:''' Fake biometric sensor | ||
| Line 58: | Line 59: | ||
| - | ==Analysis== | + | =='''Analysis'''== |
| - | ===Principle of Least Privilege=== | + | |
| + | ===''Principle of Least Privilege''=== | ||
The design of the biometric security system itself is very linear hence, only the channels themselves need to be protected. This means that overall, processes cannot be accessed past the sensor if the sensor themselves have not been used. From this perspective, the design is secure. However, the system is still vulnerable from all attacks that attack each process directly (type 3, 5, and 6 attacks). | The design of the biometric security system itself is very linear hence, only the channels themselves need to be protected. This means that overall, processes cannot be accessed past the sensor if the sensor themselves have not been used. From this perspective, the design is secure. However, the system is still vulnerable from all attacks that attack each process directly (type 3, 5, and 6 attacks). | ||
| - | ===Principle of Fail-Safe Default=== | + | ===''Principle of Fail-Safe Default''=== |
The principle of fail-safe default is an excellent principle to follow for security mechanisms, but it falls short due to an implicit assumption within the principle itself. The principle assumes that security mechanisms will always work perfectly if all the requirements are passed. However, with biometric security systems, that is not the case. Biometric security systems are not perfect so they don’t always pass legitimate users and at the same time, they also pass the invalid users as well. | The principle of fail-safe default is an excellent principle to follow for security mechanisms, but it falls short due to an implicit assumption within the principle itself. The principle assumes that security mechanisms will always work perfectly if all the requirements are passed. However, with biometric security systems, that is not the case. Biometric security systems are not perfect so they don’t always pass legitimate users and at the same time, they also pass the invalid users as well. | ||
| - | |||
| - | ===Principle of Economy of Mechanism=== | + | {| class="wikitable" border="1" align=center |
| + | |+ '''Chart of Biometric Systems Error Rates'''<sup>[http://en.wikipedia.org/wiki/Biometric#Performance E3]</sup> | ||
| + | |||
| + | |- | ||
| + | |||
| + | ! Biometrics | ||
| + | |||
| + | ! EER | ||
| + | |||
| + | ! FAR | ||
| + | |||
| + | ! FRR | ||
| + | |||
| + | ! Subjects | ||
| + | |||
| + | ! Comment | ||
| + | |||
| + | |- | ||
| + | |||
| + | | Face | ||
| + | |||
| + | | n/a | ||
| + | |||
| + | | 1 % | ||
| + | |||
| + | | 10 % | ||
| + | |||
| + | | 37437 | ||
| + | |||
| + | | Varied lighting, indoor/outdoor | ||
| + | |||
| + | |- | ||
| + | |||
| + | | Fingerprints | ||
| + | |||
| + | | 2 % | ||
| + | |||
| + | | 2 % | ||
| + | |||
| + | | 2 % | ||
| + | |||
| + | | 100 | ||
| + | |||
| + | | Rotation and exaggerated skin distortion | ||
| + | |||
| + | |- | ||
| + | |||
| + | | Hand geometry | ||
| + | |||
| + | | 1 % | ||
| + | |||
| + | | 2 % | ||
| + | |||
| + | | 0.1 % | ||
| + | |||
| + | | 129 | ||
| + | |||
| + | | With rings and improper placement | ||
| + | |||
| + | |- | ||
| + | |||
| + | | Iris | ||
| + | |||
| + | | < 1 % | ||
| + | |||
| + | | 0.94 % | ||
| + | |||
| + | | 0.99 % | ||
| + | |||
| + | | 1224 | ||
| + | |||
| + | | Indoor Environment | ||
| + | |||
| + | |- | ||
| + | |||
| + | | Iris | ||
| + | |||
| + | | 0.01 % | ||
| + | |||
| + | | 0.0001 % | ||
| + | |||
| + | | 0.2 % | ||
| + | |||
| + | | 132 | ||
| + | |||
| + | | Best conditions | ||
| + | |||
| + | |- | ||
| + | |||
| + | | Keystrokes | ||
| + | |||
| + | | 1.8 % | ||
| + | |||
| + | | 7 % | ||
| + | |||
| + | | 0.1 % | ||
| + | |||
| + | | 15 | ||
| + | |||
| + | | During 6 months period | ||
| + | |||
| + | |- | ||
| + | |||
| + | | Voice | ||
| + | |||
| + | | 6 % | ||
| + | |||
| + | | 2 % | ||
| + | |||
| + | | 10 % | ||
| + | |||
| + | | 310 | ||
| + | |||
| + | | Text independent, multilingual | ||
| + | |} | ||
| + | |||
| + | ===''Principle of Economy of Mechanism''=== | ||
In the design of the biometric security systems, each channel must be encrypted and each state must be protected. This means that overall, the design must contain at least four encryption mechanisms must be used for each channel, and at least five security mechanisms for the five states. | In the design of the biometric security systems, each channel must be encrypted and each state must be protected. This means that overall, the design must contain at least four encryption mechanisms must be used for each channel, and at least five security mechanisms for the five states. | ||
The quantity of states and channels involved means that there are a high number of security mechanisms involved which means that security of the overall design is quite complex. This violates the principle of economy of mechanism, but the security of each channel and state may not be as complex as the design, depending on the implementation. | The quantity of states and channels involved means that there are a high number of security mechanisms involved which means that security of the overall design is quite complex. This violates the principle of economy of mechanism, but the security of each channel and state may not be as complex as the design, depending on the implementation. | ||
| - | ===Principle of Complete Mediation=== | + | ===''Principle of Complete Mediation''=== |
| - | Depending on the implementation, as long as each channel is encrypted with several layers of protection, it does not violate the principle. However, the problem comes from the human side and the issue arises when people try to replace current authentication mechanism such as password systems with biometric security systems. | + | Depending on the implementation, as long as each channel is encrypted with several layers of protection, it does not violate the principle. However, the problem comes from the human side and the issue arises when people try to replace current authentication mechanism such as password systems with biometric security systems. <sup>[http://en.wikipedia.org/wiki/Biometric#Marketing_of_biometric_products R6]</sup> |
For example, new laptops with the Windows operating system have been released with biometric security systems. On the Windows login page, there are two logins available, the password system or the biometric system, and the user only has to use one of them to login, a clear violation of the principle of complete mediation. | For example, new laptops with the Windows operating system have been released with biometric security systems. On the Windows login page, there are two logins available, the password system or the biometric system, and the user only has to use one of them to login, a clear violation of the principle of complete mediation. | ||
| - | ===Principle of Open Design=== | + | ===''Principle of Open Design''=== |
The design of the biometric security is acceptable but the weakness is easily identified. The weakness of the design lies in the storage of the templates, which to this day, remains a difficult issue. Two options are available, a centralized data bank or decentralized servers to store all the templates. | The design of the biometric security is acceptable but the weakness is easily identified. The weakness of the design lies in the storage of the templates, which to this day, remains a difficult issue. Two options are available, a centralized data bank or decentralized servers to store all the templates. | ||
The design violates the principle not because the design is shrouded in secrecy but because the design itself is weak. This issue can be solved in the future by having a stronger design. | The design violates the principle not because the design is shrouded in secrecy but because the design itself is weak. This issue can be solved in the future by having a stronger design. | ||
| - | ===Principle of Separation of Privilege=== | + | ===''Principle of Separation of Privilege''=== |
It is common knowledge that a system is not secure if only one security mechanism is used, so an obvious solution is to have multiple security mechanisms. The issue arises when multiple biometric security systems are used. For example, fingerprints and retinas are used together. However, the problem is similar to those of the principle of fail-safe defaults. It assume that security mechanism work when they are supposed to work, but by increasing the types of biometrics required, the number of FARs (false acceptance rates) and FRRs (false rejection rates) increase as well. | It is common knowledge that a system is not secure if only one security mechanism is used, so an obvious solution is to have multiple security mechanisms. The issue arises when multiple biometric security systems are used. For example, fingerprints and retinas are used together. However, the problem is similar to those of the principle of fail-safe defaults. It assume that security mechanism work when they are supposed to work, but by increasing the types of biometrics required, the number of FARs (false acceptance rates) and FRRs (false rejection rates) increase as well. | ||
Cite examples. | Cite examples. | ||
| - | ===Principle of Least Common Mechanism=== | + | ===''Principle of Least Common Mechanism''=== |
| - | + | [[Image:biometric_attacks2.jpg|thumb|Biometric security system design that includes enrollment]] | |
Again, the design is simple due to its rather linear structure. However, in order for the security system to work, there must be a step in which users are enrolled, so that features can be stored. To cut costs, that enrolment system is typically a part of the authentication mechanism. This means that the biometric security system is more opened to attacks because another channel (between feature extractor and the template bank) must be encrypted, making the design more complicated, and the attacker has another option to attack the template bank. | Again, the design is simple due to its rather linear structure. However, in order for the security system to work, there must be a step in which users are enrolled, so that features can be stored. To cut costs, that enrolment system is typically a part of the authentication mechanism. This means that the biometric security system is more opened to attacks because another channel (between feature extractor and the template bank) must be encrypted, making the design more complicated, and the attacker has another option to attack the template bank. | ||
| - | |||
| - | The big reason why biometric security systems are so popular is that from an end-user perspective, they are the simplest security mechanisms to use. The user does not require any sort of knowledge of passwords to use, since it depends on either physiological or behavioural traits. However, if it fails, due to the FARs and FRRs, such a problem can be extremely annoying since it is not easy to remedy unless there is an alternative login method, which of course, defeats the purpose of having a biometric authentication method. | + | ===''Principle of Psychological Acceptability''=== |
| + | |||
| + | The big reason why biometric security systems are so popular is that from an end-user perspective, they are the simplest security mechanisms to use. The user does not require any sort of knowledge of passwords to use, since it depends on either physiological or behavioural traits. However, if it fails, due to the FARs and FRRs, such a problem can be extremely annoying since it is not easy to remedy unless there is an alternative login method, which of course, defeats the purpose of having a biometric authentication method.<sup>[http://en.wikipedia.org/wiki/Biometric#Performance_measurement R7]</sup> | ||
| + | |||
| + | |||
| + | =='''Conclusion'''== | ||
| + | |||
| + | A lot of the faults of a biometric security system are due to current biometric technology. It is simply not advanced enough because the errors in identifying valid and invalid users are still too big, even though it may be as small as 0.01%<sup>[http://en.wikipedia.org/wiki/Biometric#Performance R8]</sup>. | ||
| + | |||
| + | Another issue involves the weak design. As a concept, it is simple, but to implement the design, it requires a lot of encryption and security mechanisms due to the many transactions of the system. Also, the design highlights a weakness in storage of the templates. Just like storage of passwords, storage of the templates carries even more risks, because stolen templates could potentially mean a stolen identity. | ||
| + | |||
| + | Also, the current thought regarding biometric security systems is that they are the way of the future, meaning they are to replace current security mechanisms, but as shown above, that is terrible because there are still too many weaknesses, including the fact that not everyone can use such a system either. However, it is so popular because it is so simple to use and requires almost no effort. Also, even if we can reduce the number of errors to zero, we should never rely solely on one type of security system. Hence, biometric security systems should only be used as a supplement to current security systems, not a replacement. | ||
| + | |||
| + | |||
| + | =='''See Also'''== | ||
| + | |||
| + | [http://www.cas.mcmaster.ca/wiki/index.php/Biometrics_in_Information_Security Biometrics in Information Security] | ||
| + | |||
| + | [http://www.cas.mcmaster.ca/wiki/index.php/Identity_Theft Identity Theft] | ||
| + | |||
| + | [http://www.cas.mcmaster.ca/wiki/index.php/Operating_Systems_Security Operating Systems Security] | ||
| + | |||
| + | [http://www.cas.mcmaster.ca/wiki/index.php/The_Mitnick_attack The Mitnick Attack] | ||
| + | |||
| + | |||
| + | =='''External Links'''== | ||
| + | |||
| + | [E1] http://en.wikipedia.org/wiki/Jerome_H._Saltzer | ||
| + | |||
| + | [E2] http://en.wikipedia.org/wiki/Michael_Schroeder | ||
| + | |||
| + | [E3] http://en.wikipedia.org/wiki/Biometric#Performance | ||
| + | |||
| + | |||
| + | =='''References'''== | ||
| + | |||
| + | [R1] http://www.cafesoft.com/support/security-glossary.html | ||
| + | |||
| + | [R2] http://en.wikipedia.org/wiki/Biometrics#Issues_and_concerns | ||
| + | |||
| + | [R3] [[Biometrics in Information Security#Types of Measurements]] | ||
| + | |||
| + | [R4] Bishop, Matt. Introduction to Computer Security. Boston: Addison-Wesley, 2006. | ||
| + | |||
| + | [R5] Jain, Anil K. Biometric Security System. Michigan, 2006. | ||
| + | |||
| + | [R6] http://en.wikipedia.org/wiki/Biometric#Marketing_of_biometric_products | ||
| + | |||
| + | [R7] http://en.wikipedia.org/wiki/Biometric#Performance_measurement | ||
| + | [R8] http://en.wikipedia.org/wiki/Biometric#Performance | ||
| - | |||
| - | + | [Ra] John Woodward Jr, Katharine Webb, Elaine Newton, Melissa Bradley, David Rubenson. Army Biometric Applications: Identifying and Addressing Sociocultural Concerns. Santa Monica, CA: RAND, 2001. | |
| - | + | [Rb] D. J. Hurley, B. Arbab-Zavar, M.S. Nixon. The Ear as a Biometric. University of Southampton: Eurosip, 2007. | |
| - | |||
| - | + | --[[User:Mad Doktor|Mad Doktor]] 14:16, 10 December 2007 (EST) | |
Current revision as of 19:16, 10 December 2007
Analysis of Biometric Systems using Security Design Principles
Biometric security systemsR1 are authentication mechanisms that bind an entity to a subject based on what the entity is, as opposed to what they know, what they have, or where they are.
Within the past several years, biometric security systems have gained a lot of ground in terms of advancements in technology and widespread use however, there is still a lot of reluctance to adopt the technology worldwideR2. A look at biometric security systems through security design principles should provide a clearer understanding of its strengths and weaknesses in the implementation and design of biometric security systems.
Contents |
Biometrics
Biometrics is the identification of a person through automated measurements using biological or behavioural featuresR3
Security Design Principles
The following eight design principles were created by SalzterE1 and SchroederE2 for the design and implementation of security mechanismsR4. These design principles encompass technical details and human interaction that make designs and mechanisms easy to understand. They are also simple and easy to understand, which is why they will be used as a guide to analyze biometric security systems. The list of design principles are as follows:
Principle of Least Privilege: A subject should be given only those privileges that it needs in order to complete its task.
Principle of Fails-Safe Defaults: A subject should be denied access to an object unless the subject was given access.
Principle of Economy of Mechanism: Security mechanisms should be as simple as possible.
Principle of Complete Mediation: All accesses to objects are checked to ensure that they are allowed.
Principle of Open Design: Security of a mechanism should not depend on the secrecy of its design or implementation.
Principle of Separation of Privilege: A system should not grant permission based on a single condition.
Principle of Least Common Mechanism: Mechanisms used to access resources should not be shared.
Principle of Psychological Acceptability: Security mechanisms should not make the resource more difficult to access than if the security mechanisms were not present.
Breaking a Biometrics Security System
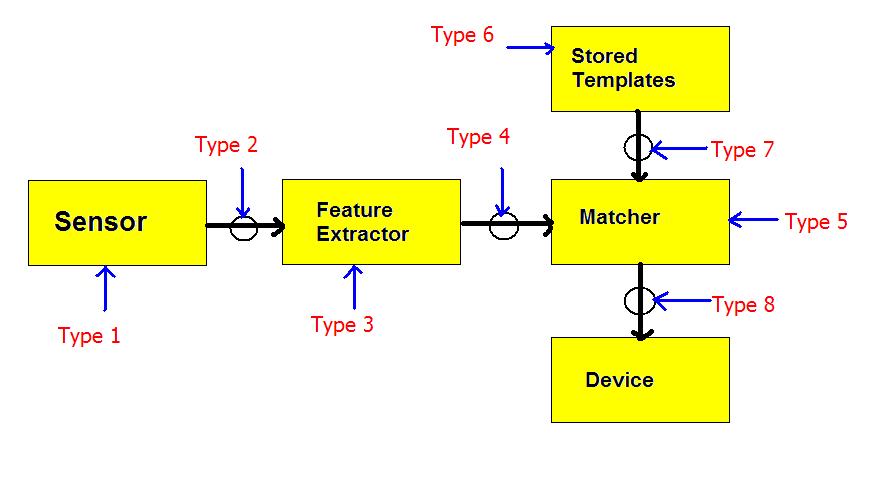
In addition to looking at biometric security systems from a design and implementation perspective, understanding a biometrics security system from an attacker’s perspective is also important. In general, there are seven different types of attacksR5. These types of attacks are categorized by their attacks on a specific part of the design. They can be divided into the following:
Type 1: Fake biometric sensor
Type 2: Replay attacks
Type 3: Trojan horse program at feature extractor
Type 4: Real features replaced by synthetic features.
Type 5: Trojan horse program at matcher.
Type 6: Attacks modifying database of templates.
Type 7: Results overridden.
Analysis
Principle of Least Privilege
The design of the biometric security system itself is very linear hence, only the channels themselves need to be protected. This means that overall, processes cannot be accessed past the sensor if the sensor themselves have not been used. From this perspective, the design is secure. However, the system is still vulnerable from all attacks that attack each process directly (type 3, 5, and 6 attacks).
Principle of Fail-Safe Default
The principle of fail-safe default is an excellent principle to follow for security mechanisms, but it falls short due to an implicit assumption within the principle itself. The principle assumes that security mechanisms will always work perfectly if all the requirements are passed. However, with biometric security systems, that is not the case. Biometric security systems are not perfect so they don’t always pass legitimate users and at the same time, they also pass the invalid users as well.
| Biometrics | EER | FAR | FRR | Subjects | Comment |
|---|---|---|---|---|---|
| Face | n/a | 1 % | 10 % | 37437 | Varied lighting, indoor/outdoor |
| Fingerprints | 2 % | 2 % | 2 % | 100 | Rotation and exaggerated skin distortion |
| Hand geometry | 1 % | 2 % | 0.1 % | 129 | With rings and improper placement |
| Iris | < 1 % | 0.94 % | 0.99 % | 1224 | Indoor Environment |
| Iris | 0.01 % | 0.0001 % | 0.2 % | 132 | Best conditions |
| Keystrokes | 1.8 % | 7 % | 0.1 % | 15 | During 6 months period |
| Voice | 6 % | 2 % | 10 % | 310 | Text independent, multilingual |
Principle of Economy of Mechanism
In the design of the biometric security systems, each channel must be encrypted and each state must be protected. This means that overall, the design must contain at least four encryption mechanisms must be used for each channel, and at least five security mechanisms for the five states.
The quantity of states and channels involved means that there are a high number of security mechanisms involved which means that security of the overall design is quite complex. This violates the principle of economy of mechanism, but the security of each channel and state may not be as complex as the design, depending on the implementation.
Principle of Complete Mediation
Depending on the implementation, as long as each channel is encrypted with several layers of protection, it does not violate the principle. However, the problem comes from the human side and the issue arises when people try to replace current authentication mechanism such as password systems with biometric security systems. R6
For example, new laptops with the Windows operating system have been released with biometric security systems. On the Windows login page, there are two logins available, the password system or the biometric system, and the user only has to use one of them to login, a clear violation of the principle of complete mediation.
Principle of Open Design
The design of the biometric security is acceptable but the weakness is easily identified. The weakness of the design lies in the storage of the templates, which to this day, remains a difficult issue. Two options are available, a centralized data bank or decentralized servers to store all the templates.
The design violates the principle not because the design is shrouded in secrecy but because the design itself is weak. This issue can be solved in the future by having a stronger design.
Principle of Separation of Privilege
It is common knowledge that a system is not secure if only one security mechanism is used, so an obvious solution is to have multiple security mechanisms. The issue arises when multiple biometric security systems are used. For example, fingerprints and retinas are used together. However, the problem is similar to those of the principle of fail-safe defaults. It assume that security mechanism work when they are supposed to work, but by increasing the types of biometrics required, the number of FARs (false acceptance rates) and FRRs (false rejection rates) increase as well. Cite examples.
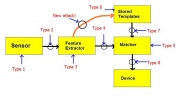
Principle of Least Common Mechanism
Again, the design is simple due to its rather linear structure. However, in order for the security system to work, there must be a step in which users are enrolled, so that features can be stored. To cut costs, that enrolment system is typically a part of the authentication mechanism. This means that the biometric security system is more opened to attacks because another channel (between feature extractor and the template bank) must be encrypted, making the design more complicated, and the attacker has another option to attack the template bank.
Principle of Psychological Acceptability
The big reason why biometric security systems are so popular is that from an end-user perspective, they are the simplest security mechanisms to use. The user does not require any sort of knowledge of passwords to use, since it depends on either physiological or behavioural traits. However, if it fails, due to the FARs and FRRs, such a problem can be extremely annoying since it is not easy to remedy unless there is an alternative login method, which of course, defeats the purpose of having a biometric authentication method.R7
Conclusion
A lot of the faults of a biometric security system are due to current biometric technology. It is simply not advanced enough because the errors in identifying valid and invalid users are still too big, even though it may be as small as 0.01%R8.
Another issue involves the weak design. As a concept, it is simple, but to implement the design, it requires a lot of encryption and security mechanisms due to the many transactions of the system. Also, the design highlights a weakness in storage of the templates. Just like storage of passwords, storage of the templates carries even more risks, because stolen templates could potentially mean a stolen identity.
Also, the current thought regarding biometric security systems is that they are the way of the future, meaning they are to replace current security mechanisms, but as shown above, that is terrible because there are still too many weaknesses, including the fact that not everyone can use such a system either. However, it is so popular because it is so simple to use and requires almost no effort. Also, even if we can reduce the number of errors to zero, we should never rely solely on one type of security system. Hence, biometric security systems should only be used as a supplement to current security systems, not a replacement.
See Also
Biometrics in Information Security
External Links
[E1] http://en.wikipedia.org/wiki/Jerome_H._Saltzer
[E2] http://en.wikipedia.org/wiki/Michael_Schroeder
[E3] http://en.wikipedia.org/wiki/Biometric#Performance
References
[R1] http://www.cafesoft.com/support/security-glossary.html
[R2] http://en.wikipedia.org/wiki/Biometrics#Issues_and_concerns
[R3] Biometrics in Information Security#Types of Measurements
[R4] Bishop, Matt. Introduction to Computer Security. Boston: Addison-Wesley, 2006.
[R5] Jain, Anil K. Biometric Security System. Michigan, 2006.
[R6] http://en.wikipedia.org/wiki/Biometric#Marketing_of_biometric_products
[R7] http://en.wikipedia.org/wiki/Biometric#Performance_measurement
[R8] http://en.wikipedia.org/wiki/Biometric#Performance
[Ra] John Woodward Jr, Katharine Webb, Elaine Newton, Melissa Bradley, David Rubenson. Army Biometric Applications: Identifying and Addressing Sociocultural Concerns. Santa Monica, CA: RAND, 2001.
[Rb] D. J. Hurley, B. Arbab-Zavar, M.S. Nixon. The Ear as a Biometric. University of Southampton: Eurosip, 2007.
--Mad Doktor 14:16, 10 December 2007 (EST)