Denial Of Service Attacks
From Computing and Software Wiki
A denial of service attack (DoS attack) is generally the attempt to degrade the resources of another computer, or crash it, so the that the intended users of that computer can not longer use it. The methods used to do such an attack usually involve an attempt to exploit a weakness in one of the protocols that are used on the internet to cause harm to the target machine or make it lose and use resources at an unusual level. Since denial of service attacks are so common today protection has become a very important concern for machines on the internet.
Contents |
Attack Methods
Goals of the attacks:
- "flood" a network which will prevent legitimate network traffic
- disrupt connections between two machines, which will prevent access to a service
- disrupt the service given to a particular system or person [2]
ICMP flood
There are two basic ways that ICMP is used to deny service. The first is by flooding the target with ping messages until they are overwhelmed by trying to send responses and are slowed down. This can be done in either a very simple way that's only requirement is that you have more bandwidth than the target you are attacking or in a more complex way such as Smurfing or the Smurf Attack which exploits poorly configured network devices allow packets to be sent to all other hosts on a network using the broadcast address. The other way is called a often called a nuke and the most popular example is called the Ping of Death which sends an ICMP ECHO request packet that is much larger than the maximum IP packet size to target. Because of the size of the packet the target cannot reassemble them. This often causes the system to crash as a result. [1]
TCP SYN Flood Attack
Transmission Control Protocol connection request packets can be used to attack a target machine by causing the target to create half-open connections and reserve all of the ports on the machine. This is done by attempting to create a regular connection with the target, but never returning anything back to them after they have sent the SYN-ACK packet. Since the process of opening a TCP connect is a three-way handshake this will stall the process while waiting for confirmation from the attacker. Unlike an ICMP flood this attack does not depend on having more bandwidth than the target because there is a relatively small number of ports that have to be reserved.[1,2]
Application level floods
DoS attacks are not limited to only a server scale. Individual applications on a users machine are also prone to attack depending on the software. IRC is a very common example of where the various types of attacks used on servers can be seen on a smaller scale. These can include exploits such as buffer overflow which can cause software to get confused and fill disk space or consume all available memory or CPU time. As well as the more common types of attack such as flooding.[3]
Distributed attack
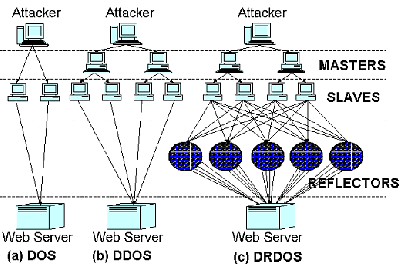
A distributed denial of service attack (DDoS) is a much more powerful form of the traditional DoS attack. In this form of the attack multiple compromised computers (also known as slaves) are used to proform the attacks noted above. Capturing the computers to do such an attack is done through viruses and malware. Both may be designed so that all of the machines are triggered at a specific date and time. Alternatively the master system could have has more specific and varied control over them. There are many DDoS tools that can be used to both run through lists of exploits to aquire new slaves as well as to control the slaves. A collected group of compermised computers are often called Bots & Botnets. Stacheldraht is a classic example of a control program that may be used to control multiple master systems at once which in turn control all of the slaved machines. [8]
The primary difference and advantage of DDoS is that DoS only makes use of one computer while DDoS uses many computer to complete a task. Because so many more computers are involved these attacks can be much harder to stop and also harder to detect because more focus can be put on staying hidden instead of getting the maxium power out of a single machine. They attacks are also much more powerful and often involve hundreds or even thousands of computers.[7]
Unintentional attack
As certain websites on the Internet grew more popular a relatively interesting phenomena started to develop in which websites were unintentionally being attacked by huge spikes in popularity. It is almost always the case that when big and often very popular sites link to small, unknown websites these sites cannot handle all of the extra traffic and end up under a denial of service like effect. Digg, Slashdot and Fark are prime examples of websites that's only goal is to increase the popularity of other websites and they have gained a reputation for their own related "effects" when any website is posted on them.
Unintentional attacks are not limited to popularity. Routes such as D-Link and Netgear also have a history of flooding Network Time Protocol servers without the intention of the owner of the router.[6]
Prevention and Protection
Firewalls
Common firewalls are not well suited to handle DoS attacks except by taking extreme measures. It does not take a very sophisticated defense to simply drop certain types of packets that are received. The Linux command iptables can be used to manually set the firewall rules that would partially protect a system from a DoS attack. An issue with extreme measures like blocking ICMP messages so that you are not vulnerable to ICMP flooding is that you losing a lot of functionality that comes with the protocol. This could be taken to an extreme of crippling a system by not allowing TCP or UDP packets to reach it. Even by taking steps to limit traffic other areas may still be left vulnerable most notably routers leading to the system.[4]
A few modern firewalls such as Cisco PIX have taken steps to help differentiate between good TCP traffic and malicious traffic.
Switches and Routers
Most switches and routers have some options in limiting the amount of information that is allowed through device and access control list features. For switches this may include automatic traffic limiting, delayed binding when dealing with TCP, deep packet inspection and the ability to identify bogus IP addresses. The obvious disadvantage to having many features like this turned on is that the router or switch takes a large performance hit since each packet has to be closely inspected before it is allowed past.
See also
- Tools for conducting denial-of-service attacks
- Internet Control Message Protocol
- ping
- Smurfing
- Bots & Botnets
References
- Types of DDoS Attacks. Retrieved April 11, 2009, from http://anml.iu.edu/ddos/types.html
- CERT/CC Denial of Service. Retrieved April 11, 2009, from http://www.cert.org/tech_tips/denial_of_service.html
- Mullen, Ruth. Flood Protection and Ignoring People. Retrieved April 11, 2009, from http://www.irchelp.org/irchelp/mirc/flood.html
- "Simple Nomad", Strategies for Defeating Distributed Attacks. Retrieved April 11, 2009, from http://www.windowsecurity.com/whitepapers/Strategies_for_Defeating_Distributed_Attacks.html
- Parks, J. (2008, August 25). DDoS Attack Prevention - The Best Medicine. Retrieved April 12, 2009, from http://ezinearticles.com/?DDoS-Attack-Prevention---The-Best-Medicine&id=1439320
- Plonka, Dave. (August 21, 2003). Flawed Routers Flood University of Wisconsin Internet Time Server. Retrieved April 12, 2009, from http://pages.cs.wisc.edu/~plonka/netgear-sntp/
- Manzano, Yanet. Tracing the Development of Denial of Service Attacks: A Corporate Analogy. Retrieved April 12, 2009, from http://www.acm.org/crossroads/xrds10-1/tracingDOS.html
- Dittrich, David. The "stacheldraht" distributed denial of service attack tool. Retrieved April 12, 2009, from http://staff.washington.edu/dittrich/misc/stacheldraht.analysis
External links
--Frostd 17:32, 3 April 2009 (EDT)