Secure File Transfer Protocols
From Computing and Software Wiki
Secure File Transfer Protocol is a one of the safe ways to exchange files on the internet. Simply, Secure File Transfer Protocol is a secure version of normal File Transfer Protocol (FTP). Secure File Transfer Protocol uses the same FTP commands to send or receive files securely, if it is setup properly.
Contents |
History
File Transfer Protocol (FTP, RFC 114) has become one of the most commonly used internet protocol for any of internet users since the TCP/IP protocol suite was developed in the late 1970s and early 1980s. The first FTP standard published in the early 1970s [1].
It specified only few simple commands of file transfer protocol. FTP is platform independent which means it works any kind of operating systems such as Microsoft Windows, Mac OS, and Linux.
However, File Transfer Protocol is not secure which means there are always possibilities to be stolen your username and password via computer network. Therefore, many developers and network administrators have been making an effort to make it secure.
SFTP (SSH File Transfer Protocol)
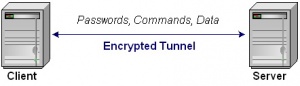
SSH File Transfer Protocols (SFTP, RFC 4253) is a secure version of File Transfer Protocol. Typically, SFTP uses SSH2 protocol and TCP port 22 to establish the secure connection but It could be used with other protocol as well.
It is much more secure but requires special server setting and also it requires SSH File Transfer Protocol Client which is not compatible with File Transfer Protocol.
SFTP Client / Server
Generally, many operating systems already supports numerous kinds of SFTP clients such filezilla in Microsoft Windows and sftp command in Linux or Unix platforms.
For servers, OpenSSH is the most widely used but there are also many commercial products.
Usage in Linux
sftp username@mills.cas.mcmaster.ca
If it is the first time to connect to the server, you will be asked, and see the warning message from the server.
Connecting to mills.cas.mcmaster.ca... The authenticity of host 'mills.cas.mcmaster.ca (130.113.68.11)' can't be established. RSA key fingerprint is e4:16:3a:3f:69:b6:37:69:69:ca:bb:a6:33:fa:47:ac. Are you sure you want to continue connecting (yes/no)?
If you enter 'yes' then you will see a warning message like below.
Warning: Permanently added 'mills.cas.mcmaster.ca, 130.113.68.11' (RSA) to the list of known hosts.
After connecting the server, you are able to tranfer files to the server or downloads files from the server through commands 'get' and 'put'.
FTPS (File Transfer Protocol over SSL)
There is another Secure File Transfer Protocol called File Transfer Protocol over TLS/SSL (FTPS, RFC 959, RFC 1123, RFC 4217 and RFC 2228). FTPS commonly refers FTP/SSL [2]. Basically, FTPS runs over tcp port 21 or 990 [3].
Main disadvantage of SFTP is that it is required that all users who wish to use SFTP should have shell accounts. Unlike SFTP, FTPS is just simply FTP over TLS/SSL that means you will have all the advantages of general FTP service also it is faster than SFTP. Recently, many ftp clients have been supported SFTP and FTPS as well so there is no problem to use FTPS instead of SFTP.
FTPS Client / Server
Most FTP Clients supports FTP, SFTP and FTPS. You just need to install new version of FTP Clients. If you intend to setup it on your FTP Server, just follw the 3 steps below.
- Generate SSL certificate
- Copy the certificate to installation directory of your ftp server
- Setup your ftp server to use SSL
References
[1] Charles M. Kozierok, The TCP/IP Guide, No Starch Press, Inc 2005
[2] FTPS From Wikipedia, http://en.wikipedia.org/wiki/FTPS
[3] Secure FTP, FTP/SSL, SFTP, FTPS, FTP. What's the difference?, http://www.rebex.net/secure-ftp.net/
[4] SSH file transfer protocol, http://en.wikipedia.org/wiki/
[5] FTPS (FTP over SSL), http://www.linomasoftware.com/products/transferanywhere/Encryption/FTPS-FTP-over-SSL
External links
- RFC 959: File Transfer Protocol, http://www.w3.org/Protocols/rfc959/
- List of raw FTP commands, http://www.nsftools.com/tips/RawFTP.htm
- FTPS (FTP over SSL) vs. SFTP (SSH File Transfer Protocol): What To Choosehttp://searchwarp.com/swa261185.htm
See also
- Wireless Security for (Small) Networks
- Digital Signatures
- Bluetooth Security
- Secure Electronic Transmission
- Network-Based Software Architectures
- Systems for Detecting Network Intrusion
- Applications of SSH
- Digital Identity
- SOA enhancements through XML Networking
- Public Key Encryption Algorithms
- Streaming Media Technology
- TCP/IP Application Development
- Insider Threats
- Sandbox
- Internet Worm Defenses
Signature
--Leehw 20:10, 7 April 2008 (EDT)