The Five-Layer TCP/IP Model: Description/Attacks/Defense
From Computing and Software Wiki
The five-layer TCP/IP model: description/attacks/defense
Application layer
description: The application layer is used by most programs for network communication. Data is passed from the program in an application-specific format, then encapsulated into a transport layer protocol.
Since the IP stack has no layers between the application and transport layers, the application layer must include any protocols that act like the OSI's presentation and session layer protocols. This is usually done through libraries.
Data sent over the network is passed into the application layer where it is encapsulated into the application layer protocol. From there, the data is passed down into the lower layer protocol of the transport layer.
The two most common end-to-end protocols are TCP and UDP. Common servers have specific ports assigned to them (HTTP has port 80; Telnet has port 23; etc.) while clients use ephemeral ports. Some protocols, such as File Transfer Protocol and Telnet may set up a session using a well-known port, but then redirect the actual user session to ephemeral ports.
Routers and switches do not utilize this layer but bandwidth throttling applications do, as with the Resource Reservation Protocol (RSVP).
An example of an attack:
SQL injection:
SQL injection is a technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and thereby unexpectedly executed. It is in fact an instance of a more general class of vulnerabilities that can occur whenever one programming or scripting language is embedded inside another.
Take a simple login page where a legitimate user would enter his username and password combination to enter a secure area to view his personal details or upload his comments in a forum.
When the legitimate user submits his details, an SQL query is generated from these details and submitted to the database for verification. If valid, the user is allowed access. In other words, the web application that controls the login page will communicate with the database through a series of planned commands so as to verify the username and password combination. On verification, the legitimate user is granted appropriate access.
Through SQL Injection, the hacker may input specifically crafted SQL commands with the intent of bypassing the login form barrier and seeing what lies behind it. This is only possible if the inputs are not properly sanitised (i.e., made invulnerable) and sent directly with the SQL query to the database. SQL Injection vulnerabilities provide the means for a hacker to communicate directly to the database.
The technologies vulnerable to this attack are dynamic script languages including ASP, ASP.NET, PHP, JSP, and CGI. All an attacker needs to perform an SQL Injection hacking attack is a web browser, knowledge of SQL queries and creative guess work to important table and field names. The sheer simplicity of SQL Injection has fuelled its popularity.
A way to defense :
A network-based intrusion detection (IDS) tool such as Snort can be set up to detect certain types of SQL injection and XSS attacks as they occur. Snort actually has a default rule set that contains signatures for detecting these intrusions. However, they can be easily bypassed by an attacker, mainly by converting the malicious input string into its hex-encoded value.
Transport layer:
description: The transport layer's responsibilities include end-to-end message transfer capabilities independent of the underlying network, along with error control, fragmentation and flow control. End to end message transmission or connecting applications at the transport layer can be categorized as either:
1. connection-oriented e.g. TCP 2. connectionless e.g UDP
The transport layer can be thought of literally as a transport mechanism e.g. a vehicle whose responsibility is to make sure that its contents (passengers/goods) reach its destination safely and soundly, unless a higher or lower layer is responsible for safe delivery.
The transport layer provides this service of connecting applications together through the use of ports. Since IP provides only a best effort delivery, the transport layer is the first layer of the TCP/IP stack to offer reliability. Note that IP can run over a reliable data link protocol such as the High-Level Data Link Control (HDLC). Protocols above transport, such as RPC, also can provide reliability.
An example of an attack:
Port Scan Attack:
A Port Scan is one of the most popular reconnaissance techniques attackers use to discover services they can break into. All machines connected to a network run many services that use TCP or UDP ports. A port scan helps the attacker find which ports are available. Essentially, a port scan consists of sending a message to each port, one at a time. The kind of response received indicates whether the port is used and can therefore be probed further for weakness.
A way to defense :
Placing a NIDS on the outside of the external firewall will give an early warning advantage, as it should enable the administrator to detect the port scans that typically indicate the start of hacker activity. However, not all scans will be followed by an actual attack, as the hacker may determine that the network currently has no weaknesses that they can exploit. This could lead to large number of alerts that do not require attention. One common yet dangerous effect of this is that the staff may lose faith in the IDS and start ignoring alerts. External firewall can be used to provide alerts for the traffic that it has denied. By placing NIDS inside the DMZ (De-Militarized Zone, a part of the network that is neither "inside" nor "outside" the corporate entity) the advantage that could be taken is that the tailoring of NIDS attack signature database can be done to consider only those attacks that are applicable to the systems in the DMZ; at the same time the firewall will have blocked all other traffic.
Network layer
description: Network layer solves the problem of getting packets across a single network. Examples of such protocols are X.25, and the ARPANET's Host/IMP Protocol.
With the advent of the concept of internetworking, additional functionality was added to this layer, namely getting data from the source network to the destination network. This generally involves routing the packet across a network of networks, known as an internetwork or (lower-case) internet.[7]
In the Internet protocol suite, IP performs the basic task of getting packets of data from source to destination. IP can carry data for a number of different upper layer protocols; these protocols are each identified by a unique protocol number: ICMP and IGMP are protocols 1 and 2, respectively.
Some of the protocols carried by IP, such as ICMP (used to transmit diagnostic information about IP transmission) and IGMP (used to manage IP Multicast data) are layered on top of IP but perform internetwork layer functions, illustrating an incompatibility between the Internet and the IP stack and OSI model. All routing protocols, such as OSPF, and RIP are also part of the network layer. What makes them part of the network layer is that their payload is totally concerned with management of the network layer. The particular encapsulation of that payload is irrelevant for layering purposes.
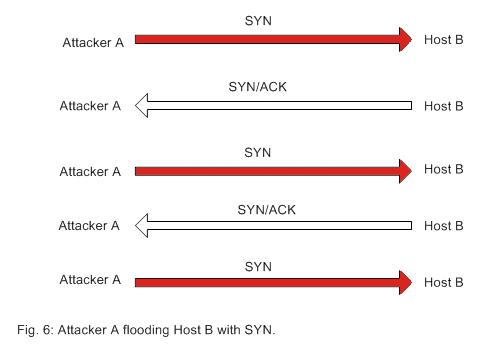
An example of an attack: SYN Flooding: The basis of the attack is to not complete the 3-way handshake necessary to establish communication. Specifically the attacker (client machine A in fig. 6) refusing to send the ACK signal to the host server (B) after receiving the SYN/ACK from Host B. Such a connection is called a half open connection.
Instead of sending an ACK, attacker A sends another SYN signal to the victim server. The server again acknowledges it with a SYN/ACK and B again refuses to send the final ACK signal. By repeating this several times the attacker tries to overflow the data structure of the host server. The data structure is built in the memory of the host server with the purpose of keeping records of connections to be completed (or half open connections). Since the data structure is of a finite size, it is possible to overflow it by establishing a large number of open connections.
Once overflow occurs the host server will not be able to accept new connections thus resulting in a denial of service. There is however a time-out associated with each of the connections (approximately 3 minutes) after which the host server will automatically drop the half open connection and can start accepting new connections. If the attacker can request connections at a rate higher than the victim servers ability to expire the pending connections then it is possible to crash the server.
Thus the objective of SYN flooding is to disable one side of the TCP connection which will result in one or more of the following
* The server is unable to accept new connections. * The server crashes or becomes inoperative. * Authorization between servers is impaired.
defense:
Data link layer
description: The link layer, which is the method used to move packets from the network layer on two different hosts, is not really part of the Internet protocol suite, because IP can run over a variety of different link layers. The processes of transmitting packets on a given link layer and receiving packets from a given link layer can be controlled both in the software device driver for the network card, as well as on firmware or specialist chipsets. These will perform data link functions such as adding a packet header to prepare it for transmission, then actually transmit the frame over a physical medium.
For Internet access over a dial-up modem, IP packets are usually transmitted using PPP. For broadband Internet access such as ADSL or cable modems, PPPoE is often used. On a local wired network, Ethernet is usually used, and on local wireless networks, IEEE 802.11 is usually used. For wide-area networks, either PPP over T-carrier or E-carrier lines, Frame relay, ATM, or packet over SONET/SDH (POS) are often used.
attack: it is the easiest, & can only be done on local network
1. APR poisoning
2.Switch's routing table looks like this:
mcaddress ip ..blah...blah.. ..192.168.... ....blah blah.. ....192.168.1..
the pirate will fill the routing table with mc IDs saying you are all of them. (is is called spoofing)
defense:
1. read only routing table: preferred method
2.
Physical layer
description: The Physical layer is responsible for encoding and transmission of data over network communications media. It operates with data in the form of bits that are sent from the Physical layer of the sending (source) device and received at the Physical layer of the destination device.
Ethernet, Token Ring, SCSI, hubs, repeaters, cables and connectors are standard network devices that function at the Physical layer. The Physical layer is also considered the domain of many hardware-related network design issues, such as LAN and WAN topology and wireless technology.
attack: some one can physically take away your network card or unplug your internet cable.
defense: Don't let people touch your computer :) it gets more complicated with wireless technologies