Fingerprint Authentication
From Computing and Software Wiki
Fingerprint authentication is a type of biometrics which digitally and compares and verifies two fingerprints. Fingerprint biometrics is known to be effective because of its distinctiveness, permanence, and performance[1]. Nowadays, it is commonly used in granting computer access, identifying bank account holders and is currently being incorporated into smart card.
Contents |
Background
The use of fingerprint authentication can be dated back to more than 30,000 years ago[2]. It was often used as a form of signature, such as in contracts and on piece of artworks. In the late 1800s, Alphonse Bertillion introduced such verification techniques to the field of forensic[2]. This technique verifies fingerprint patterns and ridges of a suspect[2]. Such system is based on two believes:
- No two individuals have the same set of fingerprints
- A fingerprint never changes naturally
Although fingerprint authentication is considered as an effective method, the quality of the verification is highly dependent upon sample quality.
Generally, a fingerprint is captured at least once using a fingerprint sensor, also known as fingerprint reader, and is then recorded into a database. To authenticate a user’s access, an image of the user’s fingerprint is obtained and compared to the record in the database. Depending on the algorithms employed, when the user’s fingerprint fulfills the matching requirements he/she is given access to the system.
As fingerprint authentication has become less expensive, it has been adopted by different types of systems. It is not unusual to find fingerprint reader on new laptops. There are also inexpensive fingerprint readers available for existing desktops and laptops, such as the Microsoft Fingerprint Reader. These devices replace the traditional username and password authentication. Recently fingerprint authentication is also combined with smart card to enhance security and increase efficiency. The smart card-fingerprint authentication is done either through a two-way or three-way manner[3]. Two-way authentication verifies using both the smart card and fingerprint[3]. Three-way adds an extra level of security by requiring also a correct password [3].
Minutiae
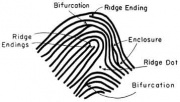
Fingerprint is composed of a series of ridges and valleys. This pattern series and the minutiae points define the fingerprint’s uniqueness. Minutiae points occur at the ridge endings or ridge bifurcations. One of the fingerprint verification methods is minutiae-based and compares minutiae points of two fingerprints[4]. The effectiveness of this approach is heavily dependent on the quality of the fingerprint sample.
Henry's Classification Scheme
Francis Galton and Edward Henry were among the first scientists to perform study on fingerprint classification. They identified five classes of fingerprint and the probability of its occurrence[5]:
- Arch 3.7%
- Tented Arch 2.9%
- Left Loop 33.8%
- Right Loop 31.7%
- Whorl 27.9%
Due to the small variances among these five classes and large variations within each class, it is often difficult to automate pattern recognition for these classes[5]. The process of verification can also be affected by noise in the fingerprint sample[5].
Image/Sample Enhancement
Since the performance of the verification relies heavily on the quality of the fingerprint sample, numerous researches were conducted to improve the quality of fingerprint image. Salil Prabhakar and Anil Jain had proposed a fast fingerprint enhancement algorithm which focuses on improving the clarity of ridges and valleys[5]. Other popular options involve applying filters to the sampled image such as directional Fourier domain filtering and Gabor filtering[6, 7].
Fingerprint Sensors
A fingerprint sensor captures digital samples of the user’s fingerprint in an image format and is generally called a fingerprint reader. Normally the fingerprint reader consists of a camera used to capture the image and a glass or surface for the user to place his/her finger. Three types of technologies for capturing fingerprint are currently being used: optical, capacitive and ultrasound.
Optical Technology
Optical Technology uses visible light to illuminate and capture a fingerprint sample[8]. This sample is then converted in to a digital image.
Optical Sensors
- Optical Reflexive: Uses reflection of light to capture a picture of the finger lines[9]
- Optical Scattering: Similar to Optical Reflexive but uses only the scattered light[9]
- Optical Contactless: Captures fingerprint without direct contact to a plate[9]
Capacitive Technology
Capacitive technology can be passive or active. Passive capacitive technology uses an array of plates made of silicon[8]. When a finger is in contact with the sensor, a small electrical current is applied and the capacitance at each pixel is measured[8]. Fingerprint ridges discharge a greater capacitance than valleys[8]. Active capacitive technology is similar to the passive one except voltage is applied to the skin before measurements take place[8].
Capacitive Sensors
- Static Capacitive Sensor Type 1: measures between pixel and groove[9]
- Static Capacitive Sensor Type 2: measures between pixel and ground[9]
- Dynamic Capacitive: uses AC voltage[9]
- Luminescent Capacitive: uses front-side of the finger as counter electrode[9]
Ultrasound Technology
Ultrasound provides the best performance but is the most expensive out of the three types of fingerprint capturing technology. It uses high frequency sound waves to capture the internal fingerprint structure[10]. This method helps in preventing imitations and is not affected by dirt, grease or other noises which would normally degrade the performance in Capacitive and Optical technologies[10].
Ultrasound Sensors
- Acoustic: records fingerprint using high frequency ultrasound [9]
Other Types of Fingerprint Capturing Technologies
- Pressure Sensitive: measures the pressure at each pixel of the fingerprint sensor
- Thermal Line: distinguishes between finger lines and grooves by comparing temperature differences over a certain time period
- Capacitive and Optical Line: similar to Thermal line but compares captured light and voltage differences instead of temperature differences
Advantages and Disadvantages to Fingerprint Authentication
Fingerprint authentication provides countless advantages but like any other systems it contains some defects. The degree of importance of these defects depend on the security requirements of the system.
Advantages
1. Permanent characteristics
- Fingerprints do not change over time and remain as a permanent signature of an individual. This avoids efforts required in updating an individual’s fingerprint that already exists in the database.
2. Distinctiveness and Theft Prevention
- Unlike traditional authentications such as cards and passwords, fingerprint is unique to each individual and cannot be stolen or lost. Even though it is possible to copy fingerprint, distinction between an actual print and a copy could still be made depending on the technology used.
3. Prevent authentication sharing
- Users cannot pass their fingerprints as easily as in the case of passwords and cards. From the perspective of security management, this enforces tighter security policy and prevents any sharing in authentication.
4. Memory lapses
- Users do not have to worry about forgetting and losing access keys since fingerprints cannot be lost and are something that users always have.
Disadvantages
1. Needs of improvement related to accuracy and speed
- Fingerprint authentication is far from ideal. Areas such as accuracy and speed still require improvements.
2. Fail to enrol handicapped individuals
- Physically impaired people, such as those without fingers or hands, or people with injuries on their fingers are often rejected by the system because of the insufficient quality of the sample.
3. Easily affected by additive noise such as dirt and cuts
- The performance of the authentication is heavily dependent on the quality of the fingerprint sample. Cuts, scars and dirt serve as additive noise to the system, especially in the case of Optical and Capacitive technologies.
4. Limited lifetime of the fingerprint readers
- Readers such as those using optical technology has a short life span (approximately one year) and requires extensive maintenance (requires regular cleaning).
5. Violation to user’s privacy
- Fingerprint can be considered as personal information and sensitive data. Some individuals may consider storing his/her fingerprint as an act of violation to his/her privacy.
References
[1] F. Ahmed and I.S. Moskowitz, Composite Signature Based Watermarking for Fingerprint Authentication, International Multimedia Conference, 2005, p. 137-142, available at http://portal.acm.org/citation.cfm?doid=1073170.1073195
[2] D. Bala, Biometrics and Information Security, Information Security Curriculum Development, 2008, p.64-66, available at http://portal.acm.org/citation.cfm?doid=1456625.1456644
[3] ACS, AET63 BioTRUSTKey, 2008, available at http://www.acs.com.hk/aet63.php
[4] S. Prabhakar and A.Jain, Fingerprint Identification, available at http://biometrics.cse.msu.edu/fingerprint.html
[5] R. Cappelli, D. Maio, D. Maltoni, L. Nanni, A Two-Stage Fingerprint Classification System, International Multimedia Conference, 2003, p.95-99, available at http://portal.acm.org/citation.cfm?doid=982507.982525
[6] S.K. Oh, J.J. Lee, C.H. Park, B.S. Kim and K.H. Park, New Fingerprint Image Enhancement Using Directional Filter Bank, Journal of WSCG, Vol.11, No.1, Feb. 2003, available at http://wscg.zcu.cz/WSCG2003/Papers_2003/J37.pdf
[7] S. Greenberg, M. Aladjem, D. Kogan and I. Dimitrov, Fingerprint Image Enhancement Using Filtering Techniques, June 2002, available at http://fvs.sourceforge.net/C27_icpr2000.pdf
[8] D. Harris, Fingerprint Authentication, Electronic Design, June 2007, available at http://electronicdesign.com/Articles/Index.cfm?AD=1&ArticleID=15658
[9] Dr. M. Bromba, Fingerprint FAQ, Feb 2009, available at http://www.bromba.com/faq/fpfaqe.htm
[10] W. Bicz, Fingerprint Structure Imaging Based on an Ultrasound Camera, OPTEL Ultrasonic Technology, available at http://www.optel.com.pl/article/english/article.htm
[11] TFTS, Microsoft USB Fingerprint Reader, July 2008, available at http://nexus404.com/Blog/2008/07/02/microsoft-usb-fingerprint-reader-log-in-with-the-touch-of-a-finger/
[12] D. Chang, Fingerprint Recognition Through Circular Sampling, available at http://www.cis.rit.edu/research/thesis/bs/1999/chang/thesis.html
See Also
- Biometrics in Information Security
- Biometric Systems and Security Design Principles
- Two-factor Authentication
- Smart Card technology to prevent fraud
External Links
--Wongck4 21:46, 12 April 2009 (EDT)