Conventional Encryption Algorithms
From Computing and Software Wiki
(Difference between revisions)
| Line 1: | Line 1: | ||
'''Conventional Encryption''' is ... | '''Conventional Encryption''' is ... | ||
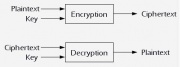
| - | [[Image:FlowDiagram.jpg|thumb | + | [[Image:FlowDiagram.jpg|thumb|right|Figure 1: Flow Diagram]] |
__TOC__ | __TOC__ | ||
Revision as of 15:14, 8 April 2008
Conventional Encryption is ...
Contents |
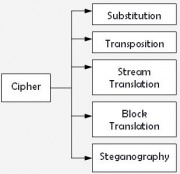
Classification of Ciphers
Monoalphabetic
This is a substitution technique that uses a single alphabet to replace symbols of plaintext for symbols of ciphertext as dictated by the key. These techniques are relatively easy to break due to the fact that symbol frequency remains invariant.
Polyalphabetic
Transposition
Synchronous Stream
Asynchronous Stream
Steganographic
Popular Algorithms
References
[1] Identity 2.0 Keynote Sxip Identity Video
[2] Identity 2.0 Wikipedia.org
External Links
Elian April 8/2008