Identity 2.0
From Computing and Software Wiki
(→Identity 2.0) |
(→Identity 2.0) |
||
| Line 7: | Line 7: | ||
[[Image:user_centric.jpg|thumb|450px|center|Figure 3: Identity 2.0 user-centric]] | [[Image:user_centric.jpg|thumb|450px|center|Figure 3: Identity 2.0 user-centric]] | ||
| + | |||
| + | ==Identity 1.0 Philosophy== | ||
| + | |||
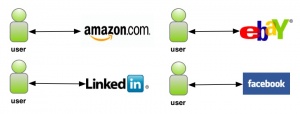
| + | The philosophy of Identity 1.0 is "site-centric". This refers to the fact the people's digital identities are locked-in with specific sites. Sites are seen as the center of digital identities, they store people's identities for their own purposes. Therefore, people's identities are not shared across various sites, which means people are required to repeatedly enter the same information on each site's particular user registration forms. | ||
| + | [[Image:site centric.jpg|thumb|300px|center|Figure 1: Identity 1.0 "Identity Silos"]] | ||
| + | [[Image:Site_centric2.jpg|thumb|300px|center|Figure 2: Identity 1.0 site-centric philosophy]] | ||
==Identity 1.0 Structure== | ==Identity 1.0 Structure== | ||
| - | |||
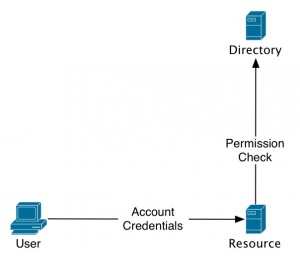
| - | In addition to a less enjoyable user-experience, Identity 1.0 is also flawed in it's ability to scale efficiently. | + | In addition to a less enjoyable user-experience, Identity 1.0 is also flawed in it's ability to scale efficiently. This is due to the fact that each time a user visits a resource (site), the resource must check a directory to identify the user and verify they have permission. |
| - | [[Image:Identity10.jpg|thumb|300px|none|Figure 3: Identity | + | [[Image:Identity10.jpg|thumb|300px|none|Figure 3: Identity 1.0 Structure]] |
| - | ==Identity 2.0 Structure== | + | ==Identity 2.0 Philosphy== |
| - | Identity 2.0 follows a transparent structure which closely mimics our real-world identification processes. | + | |
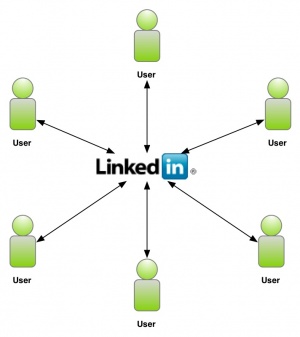
| + | Identity 2.0 represents a major shift from the philosophy of Identity 1.0. Identity 2.0 moves away from the site-centric model, and puts the user at the center. This is a more open and simple philosophy. This allows the user to take their identity from any site to any site; thus allowing for a more efficient and enjoyable experience. | ||
| + | |||
| + | [[Image:user_centric.jpg|thumb|450px|center|Figure 3: Identity 2.0 user-centric]] | ||
| + | |||
| + | ==Identity 2.0 Structure == | ||
| + | |||
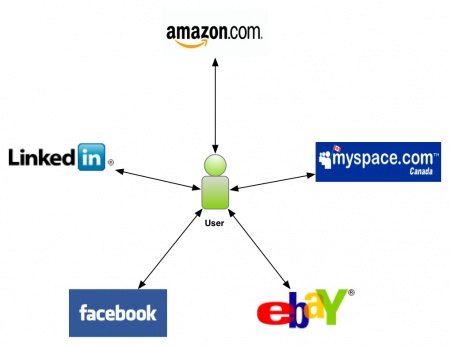
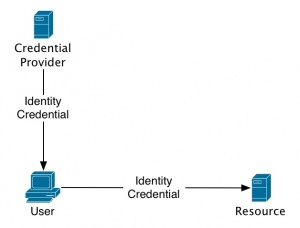
| + | Identity 2.0 follows a transparent structure which closely mimics our real-world identification processes. A major advantage here is the flexibility and scalability. | ||
[[Image:Identity20.jpg|thumb|300px|none|Figure 3: Identity 2.0 user-centric]] | [[Image:Identity20.jpg|thumb|300px|none|Figure 3: Identity 2.0 user-centric]] | ||
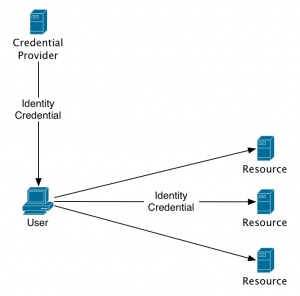
| - | + | The following are two examples of the scaling possible with Identity 2.0. | |
[[Image:Identity20a.jpg|thumb|300px|none|Figure 3: Identity 2.0 user-centric]] | [[Image:Identity20a.jpg|thumb|300px|none|Figure 3: Identity 2.0 user-centric]] | ||
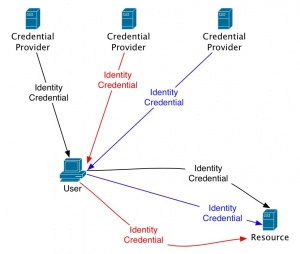
[[Image:Identity20b.jpg|thumb|300px|none|Figure 3: Identity 2.0 user-centric]] | [[Image:Identity20b.jpg|thumb|300px|none|Figure 3: Identity 2.0 user-centric]] | ||
| + | |||
| + | ==Identity 2.0 Security == | ||
| + | |||
| + | Identity 2.0 is much more secure than its predecessor 1.0. Instead of having their identities controlled by numerous sites, users' identities are stored by a trusted source. Other sites are only permitted to verify the required about details about identity. Such as "Is the person over 21?", "Is the person a U.S. resident". This puts the control of their identies into the hands of the user. | ||
==Future== | ==Future== | ||
Revision as of 19:31, 5 April 2008
Identity 2.0
Identity 2.0 is the forthcoming revolution in digital identity verification on the Internet.
Contents |
The major shift from Identity 1.0 is the move from site-centric identity silos (figures 1 and 2) to an open concept user-centric structure, where the user can move their identity from any site to any site (figure 3).
Identity 1.0 Philosophy
The philosophy of Identity 1.0 is "site-centric". This refers to the fact the people's digital identities are locked-in with specific sites. Sites are seen as the center of digital identities, they store people's identities for their own purposes. Therefore, people's identities are not shared across various sites, which means people are required to repeatedly enter the same information on each site's particular user registration forms.
Identity 1.0 Structure
In addition to a less enjoyable user-experience, Identity 1.0 is also flawed in it's ability to scale efficiently. This is due to the fact that each time a user visits a resource (site), the resource must check a directory to identify the user and verify they have permission.
Identity 2.0 Philosphy
Identity 2.0 represents a major shift from the philosophy of Identity 1.0. Identity 2.0 moves away from the site-centric model, and puts the user at the center. This is a more open and simple philosophy. This allows the user to take their identity from any site to any site; thus allowing for a more efficient and enjoyable experience.
Identity 2.0 Structure
Identity 2.0 follows a transparent structure which closely mimics our real-world identification processes. A major advantage here is the flexibility and scalability.
The following are two examples of the scaling possible with Identity 2.0.
Identity 2.0 Security
Identity 2.0 is much more secure than its predecessor 1.0. Instead of having their identities controlled by numerous sites, users' identities are stored by a trusted source. Other sites are only permitted to verify the required about details about identity. Such as "Is the person over 21?", "Is the person a U.S. resident". This puts the control of their identies into the hands of the user.
Future
There are several companies and technologies looking to implement and direct the future of Identity 2.0.
References
Identity 2.0 Wikipedia.org