Applications of SSH
From Computing and Software Wiki
(Difference between revisions)
| Line 6: | Line 6: | ||
==File Transfer Using SCP== | ==File Transfer Using SCP== | ||
# Download and install WinSCP from [http://winscp.net/eng/index.php here]. | # Download and install WinSCP from [http://winscp.net/eng/index.php here]. | ||
| + | # Start the program and click "New" | ||
| + | # Enter the host, user name and password as well as the type of protocol (SCP in this case). | ||
| + | # To save this information to the computer, click Save. Note that this will save the password in an easily recoverable format. A prompt appears asking you if you are sure. | ||
| + | # Otherwise, for a single Login, just click Login. | ||
| + | # The default interface is the "Norton Commander interface shown here. Note that the interface can be changed to an Explorer-like interface by clicking Options > Preferences > Interface and choosing the Explorer-like radio button. | ||
| + | |||
==SSH Tunneling== | ==SSH Tunneling== | ||
Revision as of 11:52, 13 April 2008
SSH (Secure Shell) is an encrypted network protocol. It has many useful applications that solve all kinds of communication and security problems.
Contents |
Secure Shell
The most obvious use for SSH is to allow remote machines to access a shell on the host computer. The host machine must be running an SSH Daemon (sshd) which usually runs on port 22. The remote machine must use an SSH client to connect to the host. On Unix based systems, the command "ssh hostname" will connect to the host specified by hostname with the same username as the user running the command. Alternatively, the user can type "ssh username@hostname" to log in as a different user. In either case, the user will usually be asked to enter the password for the specified user on the host.
File Transfer Using SCP
- Download and install WinSCP from here.
- Start the program and click "New"
- Enter the host, user name and password as well as the type of protocol (SCP in this case).
- To save this information to the computer, click Save. Note that this will save the password in an easily recoverable format. A prompt appears asking you if you are sure.
- Otherwise, for a single Login, just click Login.
- The default interface is the "Norton Commander interface shown here. Note that the interface can be changed to an Explorer-like interface by clicking Options > Preferences > Interface and choosing the Explorer-like radio button.
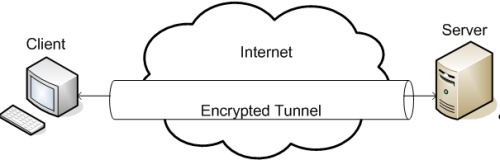
SSH Tunneling
- One of the many benefits of SSH is that you can create an encrypted tunnel from a port on the client machine to
- One of the many benefits of SSH is that you can create an encrypted tunnel from a port on the client machine to
- One of the many benefits of SSH is that you can create an encrypted tunnel from a port on the client machine to
- One of the many benefits of SSH is that you can create an encrypted tunnel from a port on the client machine to
- One of the many benefits of SSH is that you can create an encrypted tunnel from a port on the client machine to
- One of the many benefits of SSH is that you can create an encrypted tunnel from a port on the client machine to
- One of the many benefits of SSH is that you can create an encrypted tunnel from a port on the client machine to
Remote Backup/Restore
X11 Forwarding
See Also
- Some other stuff
References
- Some references