Keystroke Logging
From Computing and Software Wiki
m |
|||
| Line 2: | Line 2: | ||
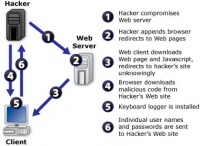
Keystroke loggers can be applied using three different methods: software, hardware, or kernel-driven applications. Information collected from key logging typically include host-names, IP addresses, and GUID (globally unique identifiers). Most importantly, various login names, passwords, and other keystrokes can be recorded in which important data, such as credit card information, can be leaked out. The history of key logging is relative to the ease at which a computer can become infected-a user simply needs to visit the wrong website to become infected. Therefore, as users become more dependant on the accessibility of online networking, new security measures must be taken to accommodate the risks involved with the convenience. | Keystroke loggers can be applied using three different methods: software, hardware, or kernel-driven applications. Information collected from key logging typically include host-names, IP addresses, and GUID (globally unique identifiers). Most importantly, various login names, passwords, and other keystrokes can be recorded in which important data, such as credit card information, can be leaked out. The history of key logging is relative to the ease at which a computer can become infected-a user simply needs to visit the wrong website to become infected. Therefore, as users become more dependant on the accessibility of online networking, new security measures must be taken to accommodate the risks involved with the convenience. | ||
| + | [[Image:keystrokelogging.jpeg|thumb|The Palace of Westminster|200px|right|From the Thames]] | ||
==History== | ==History== | ||
===Subheading=== | ===Subheading=== | ||
====Another level down==== | ====Another level down==== | ||
| - | |||
==References== | ==References== | ||
Revision as of 20:45, 12 April 2009
Keystroke logging commonly refers to the practice of logging (or storing) keystrokes, mouse events, and clipboard contents.
Keystroke loggers can be applied using three different methods: software, hardware, or kernel-driven applications. Information collected from key logging typically include host-names, IP addresses, and GUID (globally unique identifiers). Most importantly, various login names, passwords, and other keystrokes can be recorded in which important data, such as credit card information, can be leaked out. The history of key logging is relative to the ease at which a computer can become infected-a user simply needs to visit the wrong website to become infected. Therefore, as users become more dependant on the accessibility of online networking, new security measures must be taken to accommodate the risks involved with the convenience.
Contents |