Rootkits
From Computing and Software Wiki
| Line 11: | Line 11: | ||
Hybrid rootkits attempt to combine both the stealthy aspects of kernel level and the stability of user level rootkits. This style of rootkit in one of the most common in existence currently. | Hybrid rootkits attempt to combine both the stealthy aspects of kernel level and the stability of user level rootkits. This style of rootkit in one of the most common in existence currently. | ||
=== Firmware Level === | === Firmware Level === | ||
| - | Firmware level rootkits are very difficult to detect and remove. Firmware rootkits hide themselves in the firmware of the hardware components of the system. Firmware rootkits are able to reinstall themselves on booting. Certain hard disk rootkits have been found that are capable of reinstalling themselves after a complete system formatting and installation. | + | Firmware level rootkits are very difficult to detect and remove. Firmware rootkits hide themselves in the firmware of the hardware components of the system. Firmware rootkits are able to reinstall themselves on booting. Certain hard disk rootkits have been found that are capable of reinstalling themselves after a complete system formatting and installation. http://www.theregister.co.uk/2009/03/24/persistent_bios_rootkits/ |
=== Virtual Level === | === Virtual Level === | ||
== Examples == | == Examples == | ||
Revision as of 18:00, 10 April 2009
Rootkits are software which provide remote access to resources without the owner's knowledge. Rootkits are available for many different operating systems including Windows, Linux, Mac OS and others. Rootkits can have both malicious and legitimate uses. Law enforcement and child protection programs use various forms of rootkits to monitor the use of a system. Rootkits have become most known for their application with malicious intent. Hackers can use rootkits to take control of a users computer and use it for any intents they wish.
Contents |
Types of Rootkits
User-Mode
User-Mode rootkits are given administrative privileges on the computer they run on. They are able to modify any files and resources and will start whenever the computer boots. User-Mode rootkits are the easiest to be detected by rootkit detection software.
Kernel-Mode
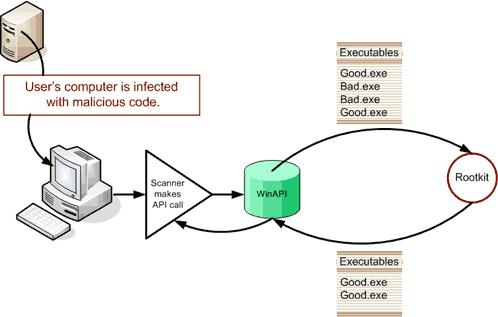
Rootkits running in kernel mode run at the same level as the operating system. The rootkit is integrated into the operating system and is concealed behind operating system application programming interfaces. Kernel level rootkits disguise themselves by interrupting system calls and returning expected information concealing their presence. Kernel level rootkits often experience stability issues as they are operating at the OS level they generally bring down the entire system if they fail.
User/Kernel Hybrid
Hybrid rootkits attempt to combine both the stealthy aspects of kernel level and the stability of user level rootkits. This style of rootkit in one of the most common in existence currently.
Firmware Level
Firmware level rootkits are very difficult to detect and remove. Firmware rootkits hide themselves in the firmware of the hardware components of the system. Firmware rootkits are able to reinstall themselves on booting. Certain hard disk rootkits have been found that are capable of reinstalling themselves after a complete system formatting and installation. http://www.theregister.co.uk/2009/03/24/persistent_bios_rootkits/
Virtual Level
Examples
Detection
Removal
References
See Also
External Links
--Elesc 14:02, 9 April 2009 (EDT)