IP Spoofing
From Computing and Software Wiki
| Line 1: | Line 1: | ||
| - | '''IP(Internet Protocol) Spoofing''' is term used to describe the creation of IP Packets with a forged (spoofed) source IP address for the purposes of hiding the true identity of the sender or impersonating the identity of another system. IP Spoofing is generally used to gain unauthorized access to a network by impersonating a source with authorized access. IP Spoofing attacks are based on the fact that internet communication occurs between distant computers. The communication is handled by routers which decide the best path based on the destination address while the source address is generally ignored. Once the destination address has been reached, the destination machine reacts based on the source address. | + | '''IP(Internet Protocol) Spoofing''' is term used to describe the creation of IP Packets with a forged |
| + | |||
| + | (spoofed) source IP address for the purposes of hiding the true identity of the sender or impersonating | ||
| + | |||
| + | the identity of another system. IP Spoofing is generally used to gain unauthorized access to a network by | ||
| + | |||
| + | impersonating a source with authorized access. IP Spoofing attacks are based on the fact that internet | ||
| + | |||
| + | communication occurs between distant computers. The communication is handled by routers which decide the | ||
| + | |||
| + | best path based on the destination address while the source address is generally ignored. Once the | ||
| + | |||
| + | destination address has been reached, the destination machine reacts based on the source address. | ||
==How IP Spoofing Works== | ==How IP Spoofing Works== | ||
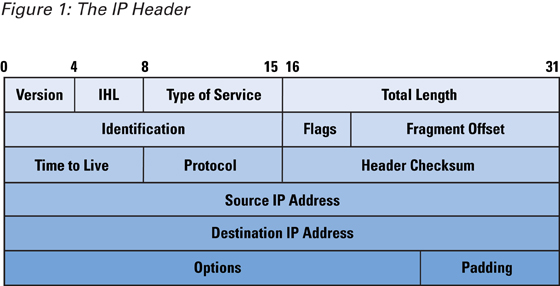
| - | Information is transferred over the internet in the form of Internet Protocol(IP) Datagrams also known as Packets. IP Datagrams consists of the IP header and the data being transferred shown in Figure 1. It is the IP header that contains the IP Header contains the source IP address and IP destination address. | + | Information is transferred over the internet in the form of Internet Protocol(IP) Datagrams also known as |
| + | |||
| + | Packets. IP Datagrams consists of the IP header and the data being transferred shown in Figure 1. It is | ||
| + | |||
| + | the IP header that contains the IP Header contains the source IP address and IP destination address. | ||
[[Image:Ipheader.jpg]] | [[Image:Ipheader.jpg]] | ||
| - | Normally IP Packets are created automatically behind the scenes for the user; however, a user can override this function by inserting a custom IP Header and informing the operating system that a header is not needed. This process creates spoofed IP datagrams that may be used to impersonate another source IP address or hide the true source IP address. These custom packets can created by using raw sockets in UNIX-like systems or packet drivers such as ''WinPcap'' for Windows. | + | Normally IP Packets are created automatically behind the scenes for the user; however, a user can override |
| + | |||
| + | this function by inserting a custom IP Header and informing the operating system that a header is not | ||
| + | |||
| + | needed. This process creates spoofed IP datagrams that may be used to impersonate another source IP | ||
| + | |||
| + | address or hide the true source IP address. These custom packets can created by using raw sockets in UNIX | ||
| + | |||
| + | -like systems or packet drivers such as ''WinPcap'' for Windows. | ||
==Blind/Nonblind Spoofing== | ==Blind/Nonblind Spoofing== | ||
| - | Spoof attacks are generally considered blind attacks because the attacker will not recieve replies | + | Spoof attacks are generally considered blind attacks because the attacker will not recieve replies |
| - | + | directly from the victim. The victim usually only replies back to the source address of the recieved | |
| - | + | ||
| - | ==Denial of Service== | + | packets and does not know the true source address of spoofed packets. If the attacker is on the same |
| - | TCP connections are setup using ''three-way handshake'' that involve the '''SYN''' and '''ACK''' flags in the TCP header. Connection that have been initiated but not completed are called half-open connections. The state of half-open connections are stored and take up part of a finite-sized data structure. If a spoofed '''SYN''' packet is sent to initiate a ''three-way handshake'' to a victim, the victim sends a '''SYN-ACK''' packet and waits for the final '''ACK''' to complete the handshake. If the spoofed address does not belong to the attacker, then the connection is left half-open and waiting indefinitely or for a period of time. Having too many half-open connections will flood the finite-size data structure and prevent and new connections from forming. This causes the victim to deny service to any legitimate connections. | + | |
| + | '''subnet''' of the host being impersonated, then the attacker can "sniff" the reply and intercept the | ||
| + | |||
| + | packet. Scenarios where the attacker inspects the responses from the victim are called "nonblind spoofing" | ||
| + | |||
| + | and in other cases it is called "blind spoofing" where the responses are not intercepted. | ||
| + | |||
| + | ==Sequence Number Prediction== | ||
| + | Once a connection between two hosts is established by using TCP, the exchange of packets between the two | ||
| + | |||
| + | parties also carry sequence numbers and acknowledgments. The sequence numbers are used to determine lost | ||
| + | |||
| + | packets or the order of packet and provide the reliability of TCP. Sequence numbers are generated pseudo- | ||
| + | |||
| + | randomly by an algorithm known by both parties. This prevents spoofing attacks from succeeding unless the | ||
| + | |||
| + | correct next sequence numbers are attached to the spoofed packets. If the responses can be viewed, the | ||
| + | |||
| + | attacker may be able to determine the algorithm and send packets with the correct sequence numbers. Once | ||
| + | |||
| + | this is accomplished the attack may intercept the session. | ||
| + | |||
| + | ==Denial of Service Using IP Spoofing== | ||
| + | TCP connections are setup using ''three-way handshake'' that involve the '''SYN''' and '''ACK''' flags in | ||
| + | |||
| + | the TCP header. Connection that have been initiated but not completed are called half-open connections. | ||
| + | |||
| + | The state of half-open connections are stored and take up part of a finite-sized data structure. If a | ||
| + | |||
| + | spoofed '''SYN''' packet is sent to initiate a ''three-way handshake'' to a victim, the victim sends a | ||
| + | |||
| + | '''SYN-ACK''' packet and waits for the final '''ACK''' to complete the handshake. If the spoofed address | ||
| + | |||
| + | does not belong to the attacker, then the connection is left half-open and waiting indefinitely or for a | ||
| + | |||
| + | period of time. Having too many half-open connections will flood the finite-size data structure and | ||
| + | |||
| + | prevent and new connections from forming. This causes the victim to deny service to any legitimate | ||
| + | |||
| + | connections. | ||
| + | |||
| + | ==Session Hijacking== | ||
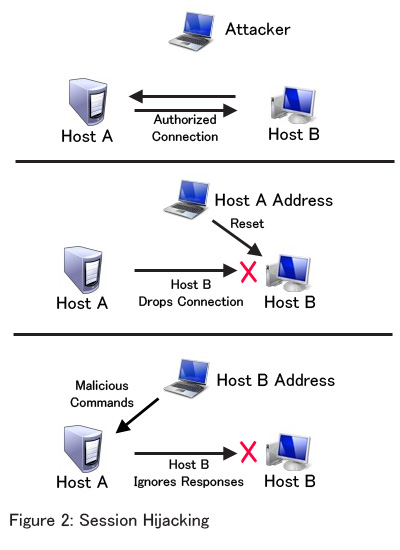
| + | Using a combination of Sequence Number Prediction and Denial of Service attacks, an attacker can hijack a | ||
| + | |||
| + | session from a trusted host. Once the sequence number has been predicted, the attacker can send a reset | ||
| + | |||
| + | message to one of the two trusted hosts to end the connection from one host by impersonating the other. | ||
| + | |||
| + | The attacker can then impersonate the trusted host that dropped the connection by impersonating the source | ||
| + | |||
| + | address. At this point the attacker can preform commands with the priviledges of the dropped host. Figure 2 shows a visual representation of session hijacking. | ||
| + | |||
| + | [[Image:sessionhijacking.jpg]] | ||
==References== | ==References== | ||
| Line 22: | Line 97: | ||
*[http://www.securityfocus.com/infocus/1674 IP Spoofing: An Introduction] | *[http://www.securityfocus.com/infocus/1674 IP Spoofing: An Introduction] | ||
*[http://www.giac.org/certified_professionals/practicals/gsec/0201.php Introduction to IP Spoofing] | *[http://www.giac.org/certified_professionals/practicals/gsec/0201.php Introduction to IP Spoofing] | ||
| - | *[http://www.cisco.com/web/about/ac123/ac147/archived_issues/ipj_10-4/104_ip-spoofing.html IP Spoofing, The Internet Protocol Journal, Volume 10, No. 4] | + | *[http://www.cisco.com/web/about/ac123/ac147/archived_issues/ipj_10-4/104_ip-spoofing.html IP Spoofing, |
| + | |||
| + | The Internet Protocol Journal, Volume 10, No. 4] | ||
| + | --[[User:Luongp|Luongp]] 22:59, 12 April 2009 (EDT) | ||
Revision as of 02:59, 13 April 2009
IP(Internet Protocol) Spoofing is term used to describe the creation of IP Packets with a forged
(spoofed) source IP address for the purposes of hiding the true identity of the sender or impersonating
the identity of another system. IP Spoofing is generally used to gain unauthorized access to a network by
impersonating a source with authorized access. IP Spoofing attacks are based on the fact that internet
communication occurs between distant computers. The communication is handled by routers which decide the
best path based on the destination address while the source address is generally ignored. Once the
destination address has been reached, the destination machine reacts based on the source address.
Contents |
How IP Spoofing Works
Information is transferred over the internet in the form of Internet Protocol(IP) Datagrams also known as
Packets. IP Datagrams consists of the IP header and the data being transferred shown in Figure 1. It is
the IP header that contains the IP Header contains the source IP address and IP destination address.
Normally IP Packets are created automatically behind the scenes for the user; however, a user can override
this function by inserting a custom IP Header and informing the operating system that a header is not
needed. This process creates spoofed IP datagrams that may be used to impersonate another source IP
address or hide the true source IP address. These custom packets can created by using raw sockets in UNIX
-like systems or packet drivers such as WinPcap for Windows.
Blind/Nonblind Spoofing
Spoof attacks are generally considered blind attacks because the attacker will not recieve replies
directly from the victim. The victim usually only replies back to the source address of the recieved
packets and does not know the true source address of spoofed packets. If the attacker is on the same
subnet of the host being impersonated, then the attacker can "sniff" the reply and intercept the
packet. Scenarios where the attacker inspects the responses from the victim are called "nonblind spoofing"
and in other cases it is called "blind spoofing" where the responses are not intercepted.
Sequence Number Prediction
Once a connection between two hosts is established by using TCP, the exchange of packets between the two
parties also carry sequence numbers and acknowledgments. The sequence numbers are used to determine lost
packets or the order of packet and provide the reliability of TCP. Sequence numbers are generated pseudo-
randomly by an algorithm known by both parties. This prevents spoofing attacks from succeeding unless the
correct next sequence numbers are attached to the spoofed packets. If the responses can be viewed, the
attacker may be able to determine the algorithm and send packets with the correct sequence numbers. Once
this is accomplished the attack may intercept the session.
Denial of Service Using IP Spoofing
TCP connections are setup using three-way handshake that involve the SYN and ACK flags in
the TCP header. Connection that have been initiated but not completed are called half-open connections.
The state of half-open connections are stored and take up part of a finite-sized data structure. If a
spoofed SYN packet is sent to initiate a three-way handshake to a victim, the victim sends a
SYN-ACK packet and waits for the final ACK to complete the handshake. If the spoofed address
does not belong to the attacker, then the connection is left half-open and waiting indefinitely or for a
period of time. Having too many half-open connections will flood the finite-size data structure and
prevent and new connections from forming. This causes the victim to deny service to any legitimate
connections.
Session Hijacking
Using a combination of Sequence Number Prediction and Denial of Service attacks, an attacker can hijack a
session from a trusted host. Once the sequence number has been predicted, the attacker can send a reset
message to one of the two trusted hosts to end the connection from one host by impersonating the other.
The attacker can then impersonate the trusted host that dropped the connection by impersonating the source
address. At this point the attacker can preform commands with the priviledges of the dropped host. Figure 2 shows a visual representation of session hijacking.
References
- Wikipedia: Spoofing attack
- Wikipedia: IP address spoofing
- IP Spoofing: An Introduction
- Introduction to IP Spoofing
- [http://www.cisco.com/web/about/ac123/ac147/archived_issues/ipj_10-4/104_ip-spoofing.html IP Spoofing,
The Internet Protocol Journal, Volume 10, No. 4] --Luongp 22:59, 12 April 2009 (EDT)