Onion Routing
From Computing and Software Wiki
| Line 1: | Line 1: | ||
'''Onion Routing''' provides a way for two computers to communicate on a network anonymously. In order for this to work, a message is encrypted and placed inside an 'onion'. | '''Onion Routing''' provides a way for two computers to communicate on a network anonymously. In order for this to work, a message is encrypted and placed inside an 'onion'. | ||
| - | The intermediate nodes along the path, called onion routers, decrypt (peel off a layer) of the onion to reveal the next router along the path to receive the onion. | + | The intermediate nodes along the path, called onion routers, decrypt (peel off a layer) of the onion to reveal the next router along the path to receive the onion. Onion routing runs |
| + | on top of TCP [http://ntrg.cs.tcd.ie/undergrad/4ba2.05/group10/index.html]. | ||
| + | |||
== Onions == | == Onions == | ||
| - | Onions are created by the sender of a message, who first determines the network path it wishes to send a message. | + | Onions are created by the sender of a message, who first determines the network path it wishes to send a message. Onions rely on Public Key Technology, where each router on the path has its own public key. |
The sender encrypts the message multiple times with the public keys of each of the intermediate routers. Starting with the public key of the last router on the path, and | The sender encrypts the message multiple times with the public keys of each of the intermediate routers. Starting with the public key of the last router on the path, and | ||
continually encrypting the message with the previous router's public key. The final message to be sent is encrypted with the public key of the first router in the path. | continually encrypting the message with the previous router's public key. The final message to be sent is encrypted with the public key of the first router in the path. | ||
| Line 10: | Line 12: | ||
The first router on the path decrypts the onion with its private key, which reveals the address of the second router on the path, and then sends the message to that address. | The first router on the path decrypts the onion with its private key, which reveals the address of the second router on the path, and then sends the message to that address. | ||
The newly 'peeled off' onion can now be decrypted by router two with its private key. This process is continued until the final onion router receives the encrypted message, | The newly 'peeled off' onion can now be decrypted by router two with its private key. This process is continued until the final onion router receives the encrypted message, | ||
| - | decrypts it with its private key to reveal the intended message encrypted by the sender. This message is finally sent to the recipient. | + | decrypts it with its private key to reveal the intended message encrypted by the sender. This message is finally sent to the recipient. |
[[Image:onion.png]] | [[Image:onion.png]] | ||
| Line 16: | Line 18: | ||
protects the identities of the sender and receiver | protects the identities of the sender and receiver | ||
| - | |||
===Traffic Analysis=== | ===Traffic Analysis=== | ||
===Eavesdropping=== | ===Eavesdropping=== | ||
Revision as of 02:00, 29 March 2009
Onion Routing provides a way for two computers to communicate on a network anonymously. In order for this to work, a message is encrypted and placed inside an 'onion'. The intermediate nodes along the path, called onion routers, decrypt (peel off a layer) of the onion to reveal the next router along the path to receive the onion. Onion routing runs on top of TCP [1].
Contents |
Onions
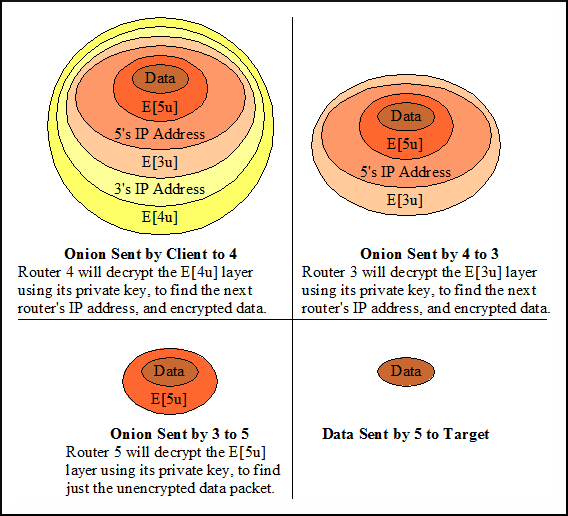
Onions are created by the sender of a message, who first determines the network path it wishes to send a message. Onions rely on Public Key Technology, where each router on the path has its own public key. The sender encrypts the message multiple times with the public keys of each of the intermediate routers. Starting with the public key of the last router on the path, and continually encrypting the message with the previous router's public key. The final message to be sent is encrypted with the public key of the first router in the path.
The concept of the onion data structure is based on the idea of 'peeling off' layers of the onion at each intermediate node to reveal information for that specific node.
The first router on the path decrypts the onion with its private key, which reveals the address of the second router on the path, and then sends the message to that address.
The newly 'peeled off' onion can now be decrypted by router two with its private key. This process is continued until the final onion router receives the encrypted message,
decrypts it with its private key to reveal the intended message encrypted by the sender. This message is finally sent to the recipient.
Anonymous Communication
protects the identities of the sender and receiver
Traffic Analysis
Eavesdropping
Denial of Service Attacks
Tor
See Also
External Links
References
1. Onion Routing for Anonymous Communications. http://ntrg.cs.tcd.ie/undergrad/4ba2.05/group10/index.html.
