Smurfing
From Computing and Software Wiki
| Line 1: | Line 1: | ||
'''Smurfing''' or a '''Smurf Attack''' is a form of Denial-of-Service attack where an attacker floods a target with ICMP echo (ping) traffic. | '''Smurfing''' or a '''Smurf Attack''' is a form of Denial-of-Service attack where an attacker floods a target with ICMP echo (ping) traffic. | ||
| - | |||
| - | |||
| - | |||
{| __TOC__ | {| __TOC__ | ||
|} | |} | ||
| - | <br> | + | {|align="right" |
| + | |- | ||
| + | | [[Image:brainy.jpg|thumb|165px|''Brainy Smurf''<br>Smurfs, as a society, were against any sort of attack.]] | ||
| + | |} | ||
| + | |||
| + | |||
| + | |||
| + | |||
==What is Smurfing?== | ==What is Smurfing?== | ||
'''Smurfing''' is a banking industry term used to describe the act of splitting up a large financial transaction into several smaller ones to avoid scrutiny from regulators. "Smurfing" is originally derived from a cartoon, The Smurfs, which consisted of a large society of many small individuals. The coining of the term is attributed to Miami-based lawyer, Gregory Baldwin in the 1980s. | '''Smurfing''' is a banking industry term used to describe the act of splitting up a large financial transaction into several smaller ones to avoid scrutiny from regulators. "Smurfing" is originally derived from a cartoon, The Smurfs, which consisted of a large society of many small individuals. The coining of the term is attributed to Miami-based lawyer, Gregory Baldwin in the 1980s. | ||
Revision as of 21:19, 13 April 2008
Smurfing or a Smurf Attack is a form of Denial-of-Service attack where an attacker floods a target with ICMP echo (ping) traffic.
Contents |
What is Smurfing?
Smurfing is a banking industry term used to describe the act of splitting up a large financial transaction into several smaller ones to avoid scrutiny from regulators. "Smurfing" is originally derived from a cartoon, The Smurfs, which consisted of a large society of many small individuals. The coining of the term is attributed to Miami-based lawyer, Gregory Baldwin in the 1980s.
Smurging or a Smurf Attack in the context of network security describes the act of many small ICMP pings being used to create very large network traffic congestion. The "smurf" attack's cousin is called Fraggle, which uses UDP echo packets in the same fashion as the ICMP echo packets. It was a simple re-write of "smurf".
How does a Smurf Attack take place?
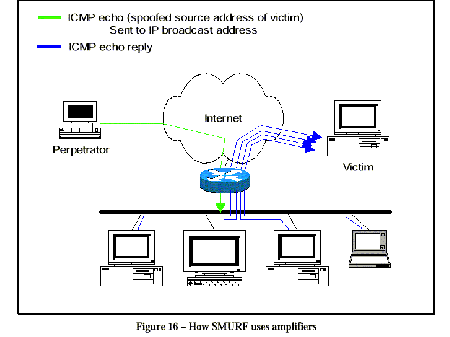
In order for a Smurf Attack to take place there are three parties which need to be considered. First is the attack who orcastrates the attack. Second is the amplifier, who is usually another victim of the attack, and lastly, the target.
The Attacker
The attack itself is fairly simple. However the attacker will need a few things before the attack can be carried out. First the attacker will need a fast connection to the internet, and will need to find a large network, or a number of networks, that is attached to the Internet by a router that will forward ICMP requests. This network is the amplifier. The attacker will then send a ping request with a spoofed source address (the address of the target) to the broadcast address of the amplifier. The attacker has completed his portion of the attack.
The Amplifier
An amplifier is a large network that is connected to the internet with a router. The router must be able to perform an IP broadcast. When the router receives traffic to the broadcast address, it will forward the message to all the hosts on the network. If the router receives and broadcasts an ICMP ping request, most of the hosts will reply to the source address of the message. This means that if there are 500 hosts which reply to the IP broadcast, then for every 1 ping request to that amplifier, 500 ping relies are sent. When an attacker spoofs the source address of the ping requests, rather than the pings replies going back to the attacker, they will go to the spoofed address (i.e. the victim). If the attacker has a fast connection, then it can send several ping requests very quickly. The amplifier is assumed to have a much faster connection (i.e. T3) to accommodate the ping replies.
The Target
The target is generally a specific server or small network. Upon receiving the ICMP replies, the target is no longer able to make its services available to its intended users since it is busy processing these ICMP messages. This creates a Denial-of-Service and render the target unaccessible to other users.
Prevention
References
http://www.webopedia.com/TERM/S/smurf.html http://www.pentics.net/denial-of-service/white-papers/smurf.cgi http://www.academ.com/nanog/oct1997/smurfing/sld001.htm http://faculty.ed.umuc.edu/~meinkej/inss690/cummins/cummins.htm http://en.wikipedia.org/wiki/Smurf_attack http://www.networkworld.com/archive/1999b/0222gearhead.html http://www-arc.com/sara/cve/Possible_DoS_problem.html