Simple Mail Transfer Protocol (SMTP)
From Computing and Software Wiki
(→Security) |
|||
| (66 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
| - | + | SMTP is straight forward, simple, and efficient protocol to transfer mail between machines over the internet. It was first defined in RFC 821. To send mail a sender (client) establish a TCP connection to the receiver (server). SMTP uses a readable simple ASCII text in which one or more recipients are defined.<sup>[3]</sup> | |
==SMTP Model== | ==SMTP Model== | ||
| - | |||
| - | |||
| - | + | SMTP Required reliable ordered data stream channel to transfer mail uses the following model of communication: | |
| - | + | ||
| - | SMTP | + | * Mail request start with a command. |
| - | + | * The SMTP sender establish a two way transmission channel to connect with the receiver. | |
| + | * The receiver can be intermediate or final destination for the mail. | ||
| + | * The receiver then send back a reply as a response to the commands. | ||
| + | * The response can be an Okay response if the receiver can accept the mail. | ||
| + | * The sender responds by sending a RCPT command to identify the mail recipient. | ||
| + | * The receiver may rejects the recipients, but cannot reject the whole transaction. | ||
| + | * The sender terminate the connection, after sending one or more emails. | ||
| + | |||
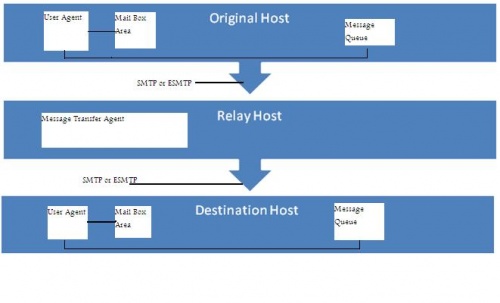
| + | This model is used to send email messages over the internet from one machine to another, the message then can be retrieved from the local client with an email agent using POP protocol, configure both protocols required to have the complete picture. Negotiation between Sender and receiver may occur over the several recipients, if the receiver is successfully processed and accepted SMTP will send email data, the receiver send an Okay reply when data received.<sup>[1]</sup> | ||
| + | |||
| + | [[Image:Component of email system.jpg|left|500px|thumb|Components of an electronic mail system (SMTP) model]] | ||
| - | |||
| - | |||
<br clear=all/> | <br clear=all/> | ||
| - | |||
| - | == | + | ==Time Stamps and Message ID== |
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| + | {|align="right" | ||
| + | |- | ||
| + | | [[Image:mailreport.jpg|thumb|mail report including SMTP Diagnostic code ]] | ||
| + | |- | ||
| + | | | ||
|} | |} | ||
| + | When email is received by your computer, SMTP added time to the mail header this feature also include store tracking data of all hosts that relayed the message. Usually SMTP Message Transfer Agent is used to show the time stamp at the start of message, as well as the sender and each time that an item relayed, this time stamp shows the ID for the host send the message, the ID of the message receiver , and the time that the message was received, the important of this information become from the fact that most of the time stamp and host identity enhance the chance for the receiver to distinguish between email sent from a trusted destination or crackers, also it provide an important information if a problem in mail delivery happened.<sup>[2]</sup> | ||
| + | Time stamps not always a reliable information source as computer clocks are sometimes inaccurately set , or the information sequence is not make since, adding the time stamp is optional by the recipient user agent. | ||
| + | |||
| + | ==Mail Error== | ||
| + | SMTP concentrate on how underlying email delivery system transfer mail messages between hosts, but does not give much details about how mail is stored or accepted, if error occur ( for example unidentified email address) this error reported to FROM filed to the sender. the receiver must report every error by sending error message to the sender. | ||
<br clear=all/> | <br clear=all/> | ||
| - | |||
| + | ==Mail Bouncing== | ||
| + | It is not always true that every email will be delivered to its destination , this happened if the sender provide incorrect recipient ID, in this case the email send back to the sender with a message indicate the reason of why the mail not delivered, the returned email called Bounced email.<sup>[2]</sup> | ||
| + | |||
| + | <br clear=all/> | ||
| + | |||
| + | ==Security== | ||
| + | Many critical [[Email_Security|security]] issues related to emails and emails agents, one of the most used agents is Sendmail, it is complicated and big program that have many functions including mail translation and mail alias names. Sendmail mainly use SMTP which run NVT Telnet , as known Telnet has so many security issues by using open text format to send data, NVT Telnet use port 25, if any body try to break into a computer this is a great security hole to do so, other limitation on original SMTP is it has no way to authenticate senders. some easy solutions are used by using more secure and efficient mail agents written with some kind of mail encryption and spam filter, or even have an assistant virus scanner to scan emails before can be open.<sup>[2,3]</sup> | ||
| + | Call back verification also can be used as validate email address this mostly used as ant spam measure, other solution as modify SMTP intensively not practical as so many installation is depends on how SMTP already build. | ||
| + | |||
| + | ==Commands Example== | ||
| + | Every SMTP transmission consist of a sequence of commands and responses between the server and the client, these commands format is easy to understand because each command appears on a separate line. Here is some of commands and their meanings. <sup>[3]</sup> | ||
| + | |||
| + | SMTP Commands Example | ||
| + | |||
| + | HELO : Identify the sender | ||
| + | MAIL FROM : Start mail transaction and identify mail originator | ||
| + | RCOT TO : Identify an individual recipient | ||
| + | DATA : Sender is ready to transmit a series of line of text | ||
| + | VERFY : Ask for name identification from the receiver | ||
| + | TURN : Ask partiner to switch roles and become a sender | ||
| + | SOML : Send email if receiver is logged in, deliver direct to the terminal | ||
| + | SEND : Deliver the mail directly to the recipient if logged in | ||
| + | QUIT : Close connection | ||
| + | |||
| + | |||
| + | <br clear=all/> | ||
| + | |||
| + | == Reply Codes Example== | ||
| + | SMTP reply code look like FTP reply code in structure, it consist of three digits the first digit show the status of the command.<sup>[3]</sup> | ||
| + | |||
| + | 1yz : Positive primary reply | ||
| + | 2yz : Positive completion reply | ||
| + | 3yz : Positive intermediate reply | ||
| + | 4yz : Try again reply | ||
| + | 5yz : Permanent negative reply | ||
| + | x0z : Syntax error or unknown command | ||
| + | x1z : Information request | ||
| + | x2z : Connection reference reply | ||
| + | x5z : Status of the receiver mail system | ||
| + | |||
| + | x4z, and x5z : Unspecified as yet. | ||
| + | |||
| + | <br clear=all/> | ||
| + | |||
| + | ==See Also== | ||
* [[Anti-spam Systems and Techniques]] | * [[Anti-spam Systems and Techniques]] | ||
| - | * [[ | + | * [[Insider_Threats]] |
| - | * [[ | + | * [[Information_security_awareness]] |
==References== | ==References== | ||
| - | *[http://james.apache.org/server/rfclist/smtp/rfc0821.txt] - RFC 821 | + | *[http://james.apache.org/server/rfclist/smtp/rfc0821.txt] - RFC 821 Simple Mail Transfer Protocol, Jonathan B. Postel |
| - | + | *[http://www.lincoln.edu/math/rmyrick/ComputerNetworks/InetReference/94.htm] - SMTP protocol overview | |
| - | *[ TCP/IP architecture , protocols, and implementation with IPv6 and IP security. second edition , McGraw-Hill , Dr. Sidnie Feit. 1996 | + | |
| + | *[3] TCP/IP architecture , protocols, and implementation with IPv6 and IP security. second edition, McGraw-Hill , Dr. Sidnie Feit. 1996. | ||
| Line 42: | Line 97: | ||
==External Links== | ==External Links== | ||
*[http://en.wikipedia.org/wiki/Simple_Mail_Transfer_Protocol SMTP in Wikipedia] | *[http://en.wikipedia.org/wiki/Simple_Mail_Transfer_Protocol SMTP in Wikipedia] | ||
| - | + | *[http://en.wikipedia.org/wiki/Extended_SMTP Extended SMTP Wikipedia ] | |
| - | *[http://en.wikipedia.org/wiki/Extended_SMTP | + | *[http://www.the-welters.com/professional/smtp.html SMTP Commands] - SMTP complete command list |
| - | *[http:// | + | *[http://en.wikipedia.org/wiki/Mail_Transfer_Agent Mail Transfer Agents.] |
| - | *[http:// | + | *[http://en.wikipedia.org/wiki/SMTP_proxy SMTP Proxy ] |
| - | *[http:// | + | *[http://en.wikipedia.org/wiki/Anti-Spam_SMTP_Proxy Anti spam SMTP proxy] |
| - | *[http:// | + | *[http://www.sendmail.org/ Sendmail.org] |
| - | *[http://www. | + | |
| - | + | --[[User:Shahroma|Shahroma]] 20:51, 2 April 2009 (EDT) Mohammad Shahrouri | |
Current revision as of 16:09, 21 December 2009
SMTP is straight forward, simple, and efficient protocol to transfer mail between machines over the internet. It was first defined in RFC 821. To send mail a sender (client) establish a TCP connection to the receiver (server). SMTP uses a readable simple ASCII text in which one or more recipients are defined.[3]
Contents |
SMTP Model
SMTP Required reliable ordered data stream channel to transfer mail uses the following model of communication:
- Mail request start with a command.
- The SMTP sender establish a two way transmission channel to connect with the receiver.
- The receiver can be intermediate or final destination for the mail.
- The receiver then send back a reply as a response to the commands.
- The response can be an Okay response if the receiver can accept the mail.
- The sender responds by sending a RCPT command to identify the mail recipient.
- The receiver may rejects the recipients, but cannot reject the whole transaction.
- The sender terminate the connection, after sending one or more emails.
This model is used to send email messages over the internet from one machine to another, the message then can be retrieved from the local client with an email agent using POP protocol, configure both protocols required to have the complete picture. Negotiation between Sender and receiver may occur over the several recipients, if the receiver is successfully processed and accepted SMTP will send email data, the receiver send an Okay reply when data received.[1]
Time Stamps and Message ID
When email is received by your computer, SMTP added time to the mail header this feature also include store tracking data of all hosts that relayed the message. Usually SMTP Message Transfer Agent is used to show the time stamp at the start of message, as well as the sender and each time that an item relayed, this time stamp shows the ID for the host send the message, the ID of the message receiver , and the time that the message was received, the important of this information become from the fact that most of the time stamp and host identity enhance the chance for the receiver to distinguish between email sent from a trusted destination or crackers, also it provide an important information if a problem in mail delivery happened.[2] Time stamps not always a reliable information source as computer clocks are sometimes inaccurately set , or the information sequence is not make since, adding the time stamp is optional by the recipient user agent.
Mail Error
SMTP concentrate on how underlying email delivery system transfer mail messages between hosts, but does not give much details about how mail is stored or accepted, if error occur ( for example unidentified email address) this error reported to FROM filed to the sender. the receiver must report every error by sending error message to the sender.
Mail Bouncing
It is not always true that every email will be delivered to its destination , this happened if the sender provide incorrect recipient ID, in this case the email send back to the sender with a message indicate the reason of why the mail not delivered, the returned email called Bounced email.[2]
Security
Many critical security issues related to emails and emails agents, one of the most used agents is Sendmail, it is complicated and big program that have many functions including mail translation and mail alias names. Sendmail mainly use SMTP which run NVT Telnet , as known Telnet has so many security issues by using open text format to send data, NVT Telnet use port 25, if any body try to break into a computer this is a great security hole to do so, other limitation on original SMTP is it has no way to authenticate senders. some easy solutions are used by using more secure and efficient mail agents written with some kind of mail encryption and spam filter, or even have an assistant virus scanner to scan emails before can be open.[2,3] Call back verification also can be used as validate email address this mostly used as ant spam measure, other solution as modify SMTP intensively not practical as so many installation is depends on how SMTP already build.
Commands Example
Every SMTP transmission consist of a sequence of commands and responses between the server and the client, these commands format is easy to understand because each command appears on a separate line. Here is some of commands and their meanings. [3]
SMTP Commands Example
HELO : Identify the sender MAIL FROM : Start mail transaction and identify mail originator RCOT TO : Identify an individual recipient DATA : Sender is ready to transmit a series of line of text VERFY : Ask for name identification from the receiver TURN : Ask partiner to switch roles and become a sender SOML : Send email if receiver is logged in, deliver direct to the terminal SEND : Deliver the mail directly to the recipient if logged in QUIT : Close connection
Reply Codes Example
SMTP reply code look like FTP reply code in structure, it consist of three digits the first digit show the status of the command.[3]
1yz : Positive primary reply 2yz : Positive completion reply 3yz : Positive intermediate reply 4yz : Try again reply 5yz : Permanent negative reply x0z : Syntax error or unknown command x1z : Information request x2z : Connection reference reply x5z : Status of the receiver mail system
x4z, and x5z : Unspecified as yet.
See Also
References
- [3] TCP/IP architecture , protocols, and implementation with IPv6 and IP security. second edition, McGraw-Hill , Dr. Sidnie Feit. 1996.
External Links
- SMTP in Wikipedia
- Extended SMTP Wikipedia
- SMTP Commands - SMTP complete command list
- Mail Transfer Agents.
- SMTP Proxy
- Anti spam SMTP proxy
- Sendmail.org
--Shahroma 20:51, 2 April 2009 (EDT) Mohammad Shahrouri