Electronic Voting Systems
From Computing and Software Wiki
(→Insider Attacks) |
|||
| (97 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
| - | An '''Electronic Voting System''' is an innovative new method of distributing, voting, collecting and tabulating ballots through the use of computer technology. | + | An '''Electronic Voting System''' is an innovative new method of distributing, voting, collecting and tabulating ballots through the use of computer technology. |
| - | input into this technology expand every day to improve security and integrity of the results. | + | <br><br> The software implementations which are input into this technology expand every day to improve security and integrity of the results. |
| - | |||
| - | + | __TOC__ | |
| - | A DRE machine consists of a user screen for information and ballot display, a keypad involving buttons or a touchscreen, and other assisting tools such as head-phones for the handicapped. DRE's have | + | =Electronic Voting Systems= |
| - | been implemented worldwide but most frequently used in countries such as Brazil, India and United States. | + | ==DRE Machines== |
| + | <br> '''DRE (Direct Recording Electronic)''' | ||
| + | |||
| + | <br> A '''DRE''' machine is a recent implementation of a fully self-operated computer voting system. | ||
| + | <br><br>DRE's are user-friendly and time-efficient which makes them an attractive alternative to traditional pen-and-paper voting. A DRE machine consists of a user screen | ||
| + | <br>for information and ballot display, a keypad involving buttons or a touchscreen, and other assisting tools such as head-phones for the handicapped. | ||
| + | |||
| + | [[Image:sequoia_dre.jpg]] | ||
| + | |||
| + | <br> DRE's have been implemented worldwide but most frequently used in countries such as Brazil, India and United States. | ||
| + | |||
| + | <br> To access a DRE machine, a voter must be provided with a Voter Authentication Card (SmartCard or another type of Memory Card) by an Election Official. The Voter card | ||
| + | <br>becomes automatically deactivated by the DRE once a vote is fully cast. | ||
| + | |||
| + | ==Optical Scan== | ||
| + | |||
| + | Optical Scanning machines were introduced shortly after the Punch Card system, incorporating paper ballots with computer technology. There are two common Optical Scanning Machines | ||
| + | <br> used in todays elections, Marksense and the Digital Pen. | ||
| + | <br><br> '''Marksense''' is a system originally developed in Australia. Using a dark marker, a voter shades in their selection on the paper ballot, once completed the paper ballot is run through an optical scanning | ||
| + | <br>machine which uses 'dark mark' logic to select the correct vote. The votes are automatically tabulated using the machine but may also be tabulated manually using the hard copy ballots. | ||
| + | <br><br> A '''Digital Pen''' is a similar version to Marksense except the pen communicates with the paper ballot and knows at all times its location on the ballot. A small camera may also be built within | ||
| + | <br> the pen to keep track of the votes. At the end of the voting session, the pen is taken for vote tabulation and the hard copy ballots are kept for recounts. | ||
| + | |||
| + | [[Image:opticalScan.jpg | 200 px]] [[Image:DigitalPen.jpg]] | ||
| + | |||
| + | ==Internet Voting== | ||
| + | |||
| + | '''Internet voting''' has been widely used in private elections where anonymity, data integrity and tempering assurance are handled with lower standards than private elections. | ||
| + | <br> Voting over the internet can be done remotely (open network) or from a poll site. Implementation of e-voting has been recorded across the UK, US, Canada, France, Estonia & Switzerland. | ||
| + | <br>The ease with which registration, validation, collection and tallying of votes through i-voting proves attractive to the general public. | ||
| + | |||
| + | =Electoral Fraud= | ||
| + | ==Insider Attacks== | ||
| + | |||
| + | '''DRE Machines''' | ||
| + | |||
| + | Insider attacks can be caused by software developers, Poll workers, or other Election officials who are aware of the inner workings of the DRE Machine and how it is implemented. | ||
| + | |||
| + | <br>'''Ex. 1.''' A software developer can change a single line of code to give 10% of all votes to a desired party. | ||
| + | <br>'''Ex. 2.''' A programmer working on the system can change the ordering of candidates in the 'ballot definition' file but keep the original order in the 'result file'; therefore | ||
| + | <br> the reordered list will appear on the DRE screen and voters will unwillingly cast votes for wrong candidates. | ||
| + | |||
| + | ==Outsider Attacks== | ||
| + | |||
| + | '''DRE Machines''' | ||
| + | |||
| + | Outsider attacks are usually caused by people trying to guide the election in favour of their candidate. A common breach in the previous versions of DRE machines was to create a personal home-brewed SmartCard and use it to cast | ||
| + | <br> multiple votes. | ||
| + | |||
| + | <br> '''Ex. 1.''' An outsider could have used software available for purchase to create a home-brewed SmartCard. This is possible since the information on the actual SmartCards was not encrypted in the past. | ||
| + | <br> '''Ex. 2.''' An outsider could have also created a home-brewed Administrator or Ender card to stall an election. An Ender card is typically used by an election official at the end of the voting session in order | ||
| + | <br> to retrieve the memory disk containing votes from the DRE machine. If an election is stalled at locations where many voters focus on one candidate, many votes could be missed. | ||
| + | |||
| + | '''Internet''' | ||
| + | |||
| + | Intercepting an unsecured internet connection can lead to deletion or insertion of votes, though there have been times where a secured network has not been sufficient either. Attacks are also commonly focused | ||
| + | <br> on public elections since there are more areas of weaknesses an intruder can advance upon. Public elections tend to include a larger population and the absolute need for anonymity. | ||
| + | |||
| + | <br> '''Ex. 1.''' A voter casts a vote from his personal computer. An attacker gains access to the IP address of the voter's computer and intercepts the network connection. The attacker can now delete or modify | ||
| + | <br> the vote. The attacker has also retrieved the identity of the voter and can put the voter in a position of social ostracism or embarrassment. | ||
| + | |||
| + | =Reported Problems= | ||
| + | |||
| + | There many underlying issues with Electronic Voting Systems, though only the most severe of them have been historically recorded. | ||
| + | |||
| + | # '''2000 United States Presidential Election''' :: ''DRE machines rejected ballots: An estimated 1.5-2 million votes lost to faulty equipment.'' | ||
| + | # '''2006 United States General Election''' :: ''Votes intended for Democratic candidates displayed as cast for Republican candidates.'' | ||
| + | # '''2004 California Presidential Primary Election''' :: ''Deibold nonfunctional voter card encoders.'' | ||
| + | |||
| + | =Security Implementations and Certification= | ||
| + | |||
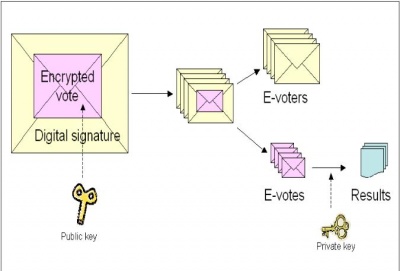
| + | For Internet Voting, new security implementations include firewalls, electronic authentication and other computer security technologies. All of these technologies generally focus on preventing malicious software | ||
| + | <br>from tempering with the votes or securing a network connection from other attacks. If a voter casts a vote from a remote location, in most cases the computer must be in 'safe mode' booted from a provided CD-ROM or | ||
| + | <br>have an attached device in order to run on a secured voting platform. The casted vote must be encrypted and sent to the vote server, the unencrypted copy is then deleted off the voters computer. The identification of | ||
| + | <br>the voter becomes completely separated from the vote once the votes are sent for counting. Other methods of improving i-voting are Secure Socket Layers and more implementations of Public Key Cryptography. | ||
| + | |||
| + | [[Image:evoting.jpg | 400 px]] | ||
| + | |||
| + | New implementations of security for DRE machines are introduced at every election, though attacks still slip through from unexpected angles. One of the most common ways to check for the integrity of votes | ||
| + | <br>is to use '''Parallel Testing'''. Parallel Testing incorporates the comparison of tabulated ballots from several different sources. The most commonly used sources are the memory register inside the DRE machine, a local | ||
| + | <br>network from which votes were sent as they were cast, and the '''Voter Verified Paper Audit Trail (VVPAT)''' hard copy of the ballots. VVPAT is a security measure introduced in the year 2000 by Dr. Rebecca Mercuri to | ||
| + | provide a printed copy of the vote to detect fraud and equipment malfunction. The votes from all three sources are tabulated and the results are compared; if any fraudulent behaviour occurred, it would be more likely | ||
| + | to be detected. | ||
| + | |||
| + | In 2005, the US Election commission had introduced the 2005 Voluntary Voting System Guidelines which demand greater security requirements for voting systems. The guidelines will be implemented in Dec 2007 and replace | ||
| + | the 2002 Voting System Standards. | ||
| + | |||
| + | =Links= | ||
| + | |||
| + | # [[Piggybacking]] | ||
| + | # [[Phishing]] | ||
| + | # [[Biometrics_in_Information_Security]] | ||
| + | # [[Smart_Card_technology_to_prevent_fraud]] | ||
| + | # [[Information_security_awareness]] | ||
| + | |||
| + | =References= | ||
| + | |||
| + | # "INTERNET VOTING." Ready Or Not Here It Comes!. CS 594 Computer and Network Security. 8 Dec 2007 <http://www.cs.utk.edu/~ffowler/cns-html/project.html>. | ||
| + | # W. Jones , Douglas . "Counting Mark-Sense Ballots." Relating Technology, the Law and Common Sense. 2003. THE UNIVERSITY OF IOWA Department of Computer Science. 8 Dec 2007 <http://www.cs.uiowa.edu/~jones/voting/optical/>. | ||
| + | # Rhodes , Richard . "Third Party & Independents: Archives." HAVA Series Part Five: More Problems With Electronic Voting Security. 24 Sept 2006. . 8 Dec 2007 <http://www.watchblog.com/thirdparty/archives/004234.html>. | ||
| + | # provided by penvote.com, "Digital Pen Voting Information Page." 08 05 2007. . Dec 8 2007 <http://www.votingindustry.com/Tech_Corner/Digital%20Pen/digital_pen_Voting.htm>. | ||
| + | # "Picture of a man hacking into system." 8 Dec 2007 <http://www.sunscs.com/SunsCSimages/disast5.jpg>. | ||
| + | # Zilberstein, Shirley. "Picture of a man hacking into systemBallot, machine problems to blame for uncounted votes in 2000 election." Inside Politics. 17 July 2001. CNN Washington Bureau. 8 Dec 2007 <http://archives.cnn.com/2001/ALLPOLITICS/07/16/voting.problems/index.html>. | ||
| + | # Bellis, Mary . "The History of Voting Machines." Inventors. 2007. 8 Dec 2007 <http://inventors.about.com/library/weekly/aa111300b.htm>. | ||
| + | # TADAYOSHI KOHNO, ADAM S TUBBLEFIELD, AVIEL D. RUBIN, DAN S. WALLACH. "Analysis of an Electronic Voting System." EEE Symposium on Security and Privacy 2004 February 27, 2004 1-32. 08 Dec 2007 <avirubin.com/vote.pdf>. | ||
| + | # Internet Voting Picture. Abbas Alfaraj. 9 Dec 2007 <aalfaraj.com/Dcouments/Voting_over_Internet.pdf> | ||
| + | # Alfaraj, Abbas. "Electronic Remote Voting Over Internet." Information Security UCL, Network Security. 9 Dec 2007 <aalfaraj.com/Dcouments/Voting_over_Internet.pdf>. | ||
| + | |||
| + | __NOTOC__ | ||
Current revision as of 23:45, 9 December 2007
An Electronic Voting System is an innovative new method of distributing, voting, collecting and tabulating ballots through the use of computer technology.
The software implementations which are input into this technology expand every day to improve security and integrity of the results.
Contents |
Electronic Voting Systems
DRE Machines
DRE (Direct Recording Electronic)
A DRE machine is a recent implementation of a fully self-operated computer voting system.
DRE's are user-friendly and time-efficient which makes them an attractive alternative to traditional pen-and-paper voting. A DRE machine consists of a user screen
for information and ballot display, a keypad involving buttons or a touchscreen, and other assisting tools such as head-phones for the handicapped.
DRE's have been implemented worldwide but most frequently used in countries such as Brazil, India and United States.
To access a DRE machine, a voter must be provided with a Voter Authentication Card (SmartCard or another type of Memory Card) by an Election Official. The Voter card
becomes automatically deactivated by the DRE once a vote is fully cast.
Optical Scan
Optical Scanning machines were introduced shortly after the Punch Card system, incorporating paper ballots with computer technology. There are two common Optical Scanning Machines
used in todays elections, Marksense and the Digital Pen.
Marksense is a system originally developed in Australia. Using a dark marker, a voter shades in their selection on the paper ballot, once completed the paper ballot is run through an optical scanning
machine which uses 'dark mark' logic to select the correct vote. The votes are automatically tabulated using the machine but may also be tabulated manually using the hard copy ballots.
A Digital Pen is a similar version to Marksense except the pen communicates with the paper ballot and knows at all times its location on the ballot. A small camera may also be built within
the pen to keep track of the votes. At the end of the voting session, the pen is taken for vote tabulation and the hard copy ballots are kept for recounts.
Internet Voting
Internet voting has been widely used in private elections where anonymity, data integrity and tempering assurance are handled with lower standards than private elections.
Voting over the internet can be done remotely (open network) or from a poll site. Implementation of e-voting has been recorded across the UK, US, Canada, France, Estonia & Switzerland.
The ease with which registration, validation, collection and tallying of votes through i-voting proves attractive to the general public.
Electoral Fraud
Insider Attacks
DRE Machines
Insider attacks can be caused by software developers, Poll workers, or other Election officials who are aware of the inner workings of the DRE Machine and how it is implemented.
Ex. 1. A software developer can change a single line of code to give 10% of all votes to a desired party.
Ex. 2. A programmer working on the system can change the ordering of candidates in the 'ballot definition' file but keep the original order in the 'result file'; therefore
the reordered list will appear on the DRE screen and voters will unwillingly cast votes for wrong candidates.
Outsider Attacks
DRE Machines
Outsider attacks are usually caused by people trying to guide the election in favour of their candidate. A common breach in the previous versions of DRE machines was to create a personal home-brewed SmartCard and use it to cast
multiple votes.
Ex. 1. An outsider could have used software available for purchase to create a home-brewed SmartCard. This is possible since the information on the actual SmartCards was not encrypted in the past.
Ex. 2. An outsider could have also created a home-brewed Administrator or Ender card to stall an election. An Ender card is typically used by an election official at the end of the voting session in order
to retrieve the memory disk containing votes from the DRE machine. If an election is stalled at locations where many voters focus on one candidate, many votes could be missed.
Internet
Intercepting an unsecured internet connection can lead to deletion or insertion of votes, though there have been times where a secured network has not been sufficient either. Attacks are also commonly focused
on public elections since there are more areas of weaknesses an intruder can advance upon. Public elections tend to include a larger population and the absolute need for anonymity.
Ex. 1. A voter casts a vote from his personal computer. An attacker gains access to the IP address of the voter's computer and intercepts the network connection. The attacker can now delete or modify
the vote. The attacker has also retrieved the identity of the voter and can put the voter in a position of social ostracism or embarrassment.
Reported Problems
There many underlying issues with Electronic Voting Systems, though only the most severe of them have been historically recorded.
- 2000 United States Presidential Election :: DRE machines rejected ballots: An estimated 1.5-2 million votes lost to faulty equipment.
- 2006 United States General Election :: Votes intended for Democratic candidates displayed as cast for Republican candidates.
- 2004 California Presidential Primary Election :: Deibold nonfunctional voter card encoders.
Security Implementations and Certification
For Internet Voting, new security implementations include firewalls, electronic authentication and other computer security technologies. All of these technologies generally focus on preventing malicious software
from tempering with the votes or securing a network connection from other attacks. If a voter casts a vote from a remote location, in most cases the computer must be in 'safe mode' booted from a provided CD-ROM or
have an attached device in order to run on a secured voting platform. The casted vote must be encrypted and sent to the vote server, the unencrypted copy is then deleted off the voters computer. The identification of
the voter becomes completely separated from the vote once the votes are sent for counting. Other methods of improving i-voting are Secure Socket Layers and more implementations of Public Key Cryptography.
New implementations of security for DRE machines are introduced at every election, though attacks still slip through from unexpected angles. One of the most common ways to check for the integrity of votes
is to use Parallel Testing. Parallel Testing incorporates the comparison of tabulated ballots from several different sources. The most commonly used sources are the memory register inside the DRE machine, a local
network from which votes were sent as they were cast, and the Voter Verified Paper Audit Trail (VVPAT) hard copy of the ballots. VVPAT is a security measure introduced in the year 2000 by Dr. Rebecca Mercuri to
provide a printed copy of the vote to detect fraud and equipment malfunction. The votes from all three sources are tabulated and the results are compared; if any fraudulent behaviour occurred, it would be more likely
to be detected.
In 2005, the US Election commission had introduced the 2005 Voluntary Voting System Guidelines which demand greater security requirements for voting systems. The guidelines will be implemented in Dec 2007 and replace the 2002 Voting System Standards.
Links
- Piggybacking
- Phishing
- Biometrics_in_Information_Security
- Smart_Card_technology_to_prevent_fraud
- Information_security_awareness
References
- "INTERNET VOTING." Ready Or Not Here It Comes!. CS 594 Computer and Network Security. 8 Dec 2007 <http://www.cs.utk.edu/~ffowler/cns-html/project.html>.
- W. Jones , Douglas . "Counting Mark-Sense Ballots." Relating Technology, the Law and Common Sense. 2003. THE UNIVERSITY OF IOWA Department of Computer Science. 8 Dec 2007 <http://www.cs.uiowa.edu/~jones/voting/optical/>.
- Rhodes , Richard . "Third Party & Independents: Archives." HAVA Series Part Five: More Problems With Electronic Voting Security. 24 Sept 2006. . 8 Dec 2007 <http://www.watchblog.com/thirdparty/archives/004234.html>.
- provided by penvote.com, "Digital Pen Voting Information Page." 08 05 2007. . Dec 8 2007 <http://www.votingindustry.com/Tech_Corner/Digital%20Pen/digital_pen_Voting.htm>.
- "Picture of a man hacking into system." 8 Dec 2007 <http://www.sunscs.com/SunsCSimages/disast5.jpg>.
- Zilberstein, Shirley. "Picture of a man hacking into systemBallot, machine problems to blame for uncounted votes in 2000 election." Inside Politics. 17 July 2001. CNN Washington Bureau. 8 Dec 2007 <http://archives.cnn.com/2001/ALLPOLITICS/07/16/voting.problems/index.html>.
- Bellis, Mary . "The History of Voting Machines." Inventors. 2007. 8 Dec 2007 <http://inventors.about.com/library/weekly/aa111300b.htm>.
- TADAYOSHI KOHNO, ADAM S TUBBLEFIELD, AVIEL D. RUBIN, DAN S. WALLACH. "Analysis of an Electronic Voting System." EEE Symposium on Security and Privacy 2004 February 27, 2004 1-32. 08 Dec 2007 <avirubin.com/vote.pdf>.
- Internet Voting Picture. Abbas Alfaraj. 9 Dec 2007 <aalfaraj.com/Dcouments/Voting_over_Internet.pdf>
- Alfaraj, Abbas. "Electronic Remote Voting Over Internet." Information Security UCL, Network Security. 9 Dec 2007 <aalfaraj.com/Dcouments/Voting_over_Internet.pdf>.