Computer worms
From Computing and Software Wiki
(Added "Future" section.) |
(Fixed spacing between sections, for readability.) |
||
| (13 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
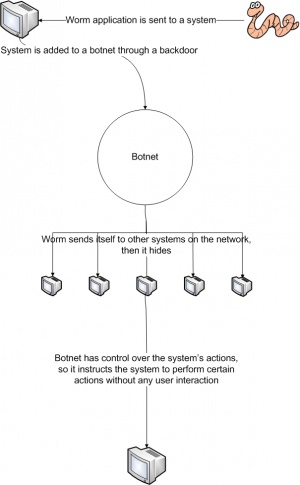
| - | A | + | A computer worm is a self-replicating [http://en.wikipedia.org/wiki/Computer_program computer program]. Once it's executed on a host, the worm adds the computer to a [[http://www.cas.mcmaster.ca/wiki/index.php/Botnets botnet]], sends a copy of itself (through a network connection) to other systems without any user intervention, and hides itself. The worm then repeats this process on the new host. Most security experts regard all worms as [http://en.wikipedia.org/wiki/Malware malware], because they generate network traffic, and perform functions without informing the user. |
| - | + | [[Image:Worms.jpg|thumb|300px|center|An overview of how computer worms work.]] | |
== A Brief History of Everything Worms == | == A Brief History of Everything Worms == | ||
| Line 15: | Line 15: | ||
• Launch a [http://en.wikipedia.org/wiki/Denial_of_service denial of service] attack on the IP address of the [http://en.wikipedia.org/wiki/White_House White House] web server. | • Launch a [http://en.wikipedia.org/wiki/Denial_of_service denial of service] attack on the IP address of the [http://en.wikipedia.org/wiki/White_House White House] web server. | ||
<br> | <br> | ||
| - | It is one of the most famous worms because, at the time, it was believed that Code Red would bring the internet to a halt | + | It is one of the most famous worms because, at the time, it was believed that Code Red would bring the internet to a halt since it was replicating so quickly. [http://computer.howstuffworks.com/virus5.htm [2]] |
| Line 26: | Line 26: | ||
| - | == Protecting Against Worms == | + | == Protecting Yourself Against Worms == |
| - | • Run a more secure operating system, like [http://en.wikipedia.org/wiki/Unix UNIX]. [http://computer.howstuffworks.com/virus6.htm [ | + | • Run a more secure operating system, like [http://en.wikipedia.org/wiki/Unix UNIX]. [http://computer.howstuffworks.com/virus6.htm [3]] <br> |
| - | • Install [http://en.wikipedia.org/wiki/Anti-virus anti-virus] software, and keep its virus database files up-to-date. [http://en.wikipedia.org/wiki/Computer_worm [ | + | • Install [http://en.wikipedia.org/wiki/Anti-virus anti-virus] software, and keep its virus database files up-to-date. [http://en.wikipedia.org/wiki/Computer_worm [4]]<br> |
| - | • Operating system vendors supply regular security patches- these help protect against a majority of worms. [http://en.wikipedia.org/wiki/Computer_worm [ | + | • Operating system vendors supply regular security patches- these help protect against a majority of worms. [http://en.wikipedia.org/wiki/Computer_worm [4]]<br> |
| - | • Do not open attached files or programs from unexpected emails. [http://en.wikipedia.org/wiki/Computer_worm [ | + | • Do not open attached files or programs from unexpected emails. [http://en.wikipedia.org/wiki/Computer_worm [4]]<br> |
== The Future == | == The Future == | ||
| - | While computer worms have usually propagated via e-mail, newer worms are spreading via [http://en.wikipedia.org/wiki/Instant_messaging instant messaging (IM)]. To understand the threat in this, note that Code Red took 14 hours to ping every IP address in the world looking for vulnerable systems, which led to 250,000 servers being affected at its peak. With IM, [http://en.wikipedia.org/wiki/Symantec Symantec] has simulated that 500,000 systems can be infected in 30 seconds. | + | While computer worms have usually propagated via e-mail, newer worms are spreading via [http://en.wikipedia.org/wiki/Instant_messaging instant messaging (IM)]. To understand the threat in this, note that Code Red took 14 hours to ping every IP address in the world looking for vulnerable systems, which led to 250,000 servers being affected at its peak. With IM, [http://en.wikipedia.org/wiki/Symantec Symantec] has simulated that 500,000 systems can be infected in 30 seconds. [http://www.infosecwriters.com/text_resources/pdf/Computer_Worms_Past_Present_and_Future.pdf [1]] |
<br> | <br> | ||
Worms aren’t even limited to computers anymore- the first worm for mobile phones appeared in 2004, known as [http://en.wikipedia.org/wiki/Caribe_%28computer_worm%29 Cabir]. While Cabir was not harmless, it was able to spread by replicating and transferring itself to other vulnerable phones in the area via [http://en.wikipedia.org/wiki/Bluetooth Bluetooth]. [http://www.infosecwriters.com/text_resources/pdf/Computer_Worms_Past_Present_and_Future.pdf [1]] | Worms aren’t even limited to computers anymore- the first worm for mobile phones appeared in 2004, known as [http://en.wikipedia.org/wiki/Caribe_%28computer_worm%29 Cabir]. While Cabir was not harmless, it was able to spread by replicating and transferring itself to other vulnerable phones in the area via [http://en.wikipedia.org/wiki/Bluetooth Bluetooth]. [http://www.infosecwriters.com/text_resources/pdf/Computer_Worms_Past_Present_and_Future.pdf [1]] | ||
| + | |||
| + | |||
| + | |||
| + | == References == | ||
| + | '''1.''' Fosnock, Craig: [http://www.infosecwriters.com/text_resources/pdf/Computer_Worms_Past_Present_and_Future.pdf Computer Worms: Past, Present, and Future], Infosecwriters.com, July 27, 2005. Retrieved on April 7, 2008. | ||
| + | <br>'''2.''' Brain, Marshall: [http://computer.howstuffworks.com/virus5.htm How Computer Viruses Work: Worms], Howstuffworks. Retrieved on April 7, 2008. | ||
| + | <br>'''3.''' Brain, Marshall: [http://computer.howstuffworks.com/virus6.htm How Computer Viruses Work: How to Protect Your Computer from Viruses], Howstuffworks. Retrieved on April 7, 2008. | ||
| + | <br>'''4.''' [http://en.wikipedia.org/wiki/Computer_worm Computer worm], Wikipedia April 7, 2008. Retrieved on April 8, 2008. | ||
| + | |||
| + | |||
| + | |||
| + | == See Also == | ||
| + | *[[http://www.cas.mcmaster.ca/wiki/index.php/Internet_Worm_Defenses Internet Worm Defenses]] | ||
| + | *[[http://www.cas.mcmaster.ca/wiki/index.php/Botnets Botnets]] | ||
| + | *[[http://www.cas.mcmaster.ca/wiki/index.php/Bluetooth_Security Bluetooth Security]] | ||
| + | *[[http://www.cas.mcmaster.ca/wiki/index.php/Systems_for_Detecting_Network_Intrusion Systems for Detecting Network Intrusion]] | ||
| + | |||
| + | |||
| + | |||
| + | == External Links == | ||
| + | *[http://www.vernalex.com/guides/malware/ Guides: Malware Guide] - a brief introduction to malware, signs of infection, and a guide to removing the malware. | ||
| + | *[http://www.wormblog.com/ worm blog] - news about new worms, as well as defenses against them. | ||
| + | *[http://www.securityfocus.com/columnists/347 Jose Nazario discusses worms] - an insightful interview with the creator of wormblog. | ||
| + | *[http://en.wikipedia.org/wiki/Notable_computer_viruses_and_worms Notable Computer Viruses and Worms] - a timeline of the most notable computer viruses and worms. | ||
| + | |||
| + | |||
| + | |||
| + | == Signature == | ||
| + | --[[User:Ahmadmu|Ahmadmu]] 21:30, 13 April 2008 (EDT) | ||
Current revision as of 01:30, 14 April 2008
A computer worm is a self-replicating computer program. Once it's executed on a host, the worm adds the computer to a [botnet], sends a copy of itself (through a network connection) to other systems without any user intervention, and hides itself. The worm then repeats this process on the new host. Most security experts regard all worms as malware, because they generate network traffic, and perform functions without informing the user.
Contents |
A Brief History of Everything Worms
The first computer worm was created by John Shoch, at Xeros PARC. The program was named “tapeworm” after a program in a science fiction novel, “The Shockwave Rider”. John’s research required him to install the same program on 100 different machines, on the same network. So instead of manually installing the program on each machine, John created the first worm: it would seek out idle hosts on his network and install the program on them automatically. Eventually, the worm became corrupt, which led it to crash the host. There was a control worm, which would sense that it had lost a computer, and so it would send out another copy to another system, which would also crash. This would keep happening until most of the computers on the network were not working. Luckily, John had preloaded a failsafe against unpredictable circumstances, which he used to stop the worm. [1]
One famous worm on the internet was the Code Red Worm, which was put on the internet on July 13, 2001, and targeted Microsoft’s IIS Web Server. Code Red had instructions to do three things:
• Replicate itself for the first 20 days of each month
• Replace web pages on the infected server with a page containing the message “Hacked By Chinese”
• Launch a denial of service attack on the IP address of the White House web server.
It is one of the most famous worms because, at the time, it was believed that Code Red would bring the internet to a halt since it was replicating so quickly. [2]
Worm Vs. Virus
A computer virus spreads itself by inserting copies of itself into other executable code. An analogy that is often used for computer viruses is that it’s similar to a biological virus, in that it spreads by inserting itself into cells. These infected cells are known as the hosts.
A worm, on the other hand, is self-contained, and does not need to insert itself into another program to propagate itself. [1]
Protecting Yourself Against Worms
• Run a more secure operating system, like UNIX. [3]
• Install anti-virus software, and keep its virus database files up-to-date. [4]
• Operating system vendors supply regular security patches- these help protect against a majority of worms. [4]
• Do not open attached files or programs from unexpected emails. [4]
The Future
While computer worms have usually propagated via e-mail, newer worms are spreading via instant messaging (IM). To understand the threat in this, note that Code Red took 14 hours to ping every IP address in the world looking for vulnerable systems, which led to 250,000 servers being affected at its peak. With IM, Symantec has simulated that 500,000 systems can be infected in 30 seconds. [1]
Worms aren’t even limited to computers anymore- the first worm for mobile phones appeared in 2004, known as Cabir. While Cabir was not harmless, it was able to spread by replicating and transferring itself to other vulnerable phones in the area via Bluetooth. [1]
References
1. Fosnock, Craig: Computer Worms: Past, Present, and Future, Infosecwriters.com, July 27, 2005. Retrieved on April 7, 2008.
2. Brain, Marshall: How Computer Viruses Work: Worms, Howstuffworks. Retrieved on April 7, 2008.
3. Brain, Marshall: How Computer Viruses Work: How to Protect Your Computer from Viruses, Howstuffworks. Retrieved on April 7, 2008.
4. Computer worm, Wikipedia April 7, 2008. Retrieved on April 8, 2008.
See Also
External Links
- Guides: Malware Guide - a brief introduction to malware, signs of infection, and a guide to removing the malware.
- worm blog - news about new worms, as well as defenses against them.
- Jose Nazario discusses worms - an insightful interview with the creator of wormblog.
- Notable Computer Viruses and Worms - a timeline of the most notable computer viruses and worms.
Signature
--Ahmadmu 21:30, 13 April 2008 (EDT)