Sandbox
From Computing and Software Wiki
| (6 intermediate revisions not shown) | |||
| Line 19: | Line 19: | ||
When a sandbox is used inside a web browser, it traps all unsolicited activity ([http://en.wikipedia.org/wiki/Malware malware], [http://en.wikipedia.org/wiki/Spyware spyware], etc) within the sandbox itself. So in the event that there is an actual malware attack, the sandbox could easily be discarded with no damage to the system. | When a sandbox is used inside a web browser, it traps all unsolicited activity ([http://en.wikipedia.org/wiki/Malware malware], [http://en.wikipedia.org/wiki/Spyware spyware], etc) within the sandbox itself. So in the event that there is an actual malware attack, the sandbox could easily be discarded with no damage to the system. | ||
| - | When a sandbox is used inside a web browser it traps all the unsolicited , | + | When a sandbox is used inside a web browser it traps all the unsolicited malware, spyware and like within the sandbox itself. In case there is an actual malware attack, the sandbox could be discarded easily and no damage occurs to the system. |
=== Gaming === | === Gaming === | ||
| Line 37: | Line 37: | ||
== Implementation == | == Implementation == | ||
| - | + | Implementation details of a commercial sandbox could be obtained [https://www.paypal.com/en_US/pdf/PP_Sandbox_UserGuide.pdf here] | |
== Downside == | == Downside == | ||
| Line 65: | Line 65: | ||
http://en.wikipedia.org/wiki/Malware - Wikipedia page for a malware<br> | http://en.wikipedia.org/wiki/Malware - Wikipedia page for a malware<br> | ||
http://en.wikipedia.org/wiki/Spyware - Wikipedia page for a spyware <br> | http://en.wikipedia.org/wiki/Spyware - Wikipedia page for a spyware <br> | ||
| - | http://secondlife.com/ - 3D social networking site | + | http://secondlife.com/ - 3D social networking site that uses sandboxes<br> |
| - | http://www.sun.com/ Sun Microsystems <br> | + | http://www.sun.com/ - Sun Microsystems <br> |
| - | https://www.paypal.com/en_US/pdf/PP_Sandbox_UserGuide.pdf Impelementation details of a commercial sandbox<br> | + | https://www.paypal.com/en_US/pdf/PP_Sandbox_UserGuide.pdf - Impelementation details of a commercial sandbox<br> |
---- | ---- | ||
| - | + | --[[User:Chatteik|Chatteik]] 23:22, 13 April 2008 (EDT) | |
| - | --[[User:Chatteik|Chatteik]] | + | |
Current revision as of 03:22, 14 April 2008
A sandbox (in computer security) is a security mechanism used on servers and personal computers to execute third-party programs that are unverified or have a non-trusted source. A sandbox allows a guest program to run under tightly-controlled conditions, which typically prevent the guest program to write to the host computer’s permanent disk storage and provide a highly restricted network access (if any). Some sandboxes also disallow the guest program to read from the host’s input devices as a means to prevent malicious programs from reading sensitive data like passwords, network keys and credit card information.
Contents |
Mechanism
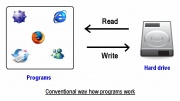
Typically, when a program is run, the hard disk is read to load program parameters and then data is written back to the hard disk from time to time during program execution and termination. [Figure A] below demonstrates this scenario.
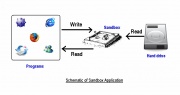
What if the program was of malicious nature? It could do all sorts of unscrupulous activities like reading sensitive data, corrupting system files or consuming network bandwidth. A sandbox is used to prevent such unauthorized read/write access. It provides the guest program a limited amount of scratch space on the hard disk where the program executes but is not allowed to write or read directly from any other sector of the hard disk. The figure below shows a sandbox acting as a transient storage area where data flows in both directions (read and write) between the sandbox and the guest program but no read or write takes place between the guest program and the permanent disk storage. Sandboxes intercept changes to both files and registry making it literally impossible for the guest program to reach outside the sandbox. [Figure B] below shows the schematic of a sandbox protecting the permanent disk storage.
Usage
Web Browsers
When a sandbox is used inside a web browser, it traps all unsolicited activity (malware, spyware, etc) within the sandbox itself. So in the event that there is an actual malware attack, the sandbox could easily be discarded with no damage to the system.
When a sandbox is used inside a web browser it traps all the unsolicited malware, spyware and like within the sandbox itself. In case there is an actual malware attack, the sandbox could be discarded easily and no damage occurs to the system.
Gaming
Sandboxes are a great way to protect game statistics from (low) scores by inexperienced players. Many online gaming servers implement sandboxes to prevent flooding of their servers with statistics from gamers on trial membership. PC users could also benefit, by allowing inexperienced gamers to play their favorite game from the sandbox, which does not change the statistics for the game.
Second Life
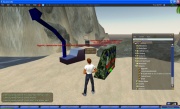
Second Life is a virtual social network which allows users to create 3D objects in their allowed virtual space. Users can test their object in public sandboxes, which ensures their object does not damage or threaten objects from other users. [Figure C] below shows the public sandbox from Sun Microsystems where user Groupf Camel is testing object Digger06.
Operating System Virtualization
The guest operating system is sandboxed in the sense that it does not run natively on the host and can only access host resources through the emulator.
Implementation
Implementation details of a commercial sandbox could be obtained here
Downside
Sandboxes can consume a lot of memory. It is not recommended to use sandboxes if your computer has less than 1 Gigabyte of physical memory.
Sandbox Software
Sandboxie is a free sandbox application for Windows operating system.
References
Microsoft Security GLossary Retrieved on April 5, 2008
Sandbox from Wikipedia Retrieved on April 5, 2008
Digital Money World Retrieved on April 6, 2008
Sandboxie Retrieved on March 30, 2008
Lotus SandboxRetrieved on March 16, 2008
See Also
Sandboxes (Software Development)
External Links
http://en.wikipedia.org/wiki/Malware - Wikipedia page for a malware
http://en.wikipedia.org/wiki/Spyware - Wikipedia page for a spyware
http://secondlife.com/ - 3D social networking site that uses sandboxes
http://www.sun.com/ - Sun Microsystems
https://www.paypal.com/en_US/pdf/PP_Sandbox_UserGuide.pdf - Impelementation details of a commercial sandbox
--Chatteik 23:22, 13 April 2008 (EDT)