TCP/IP Application Development
From Computing and Software Wiki
(→Signature) |
|||
| (41 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
| - | =Introduction= | + | ==Introduction== |
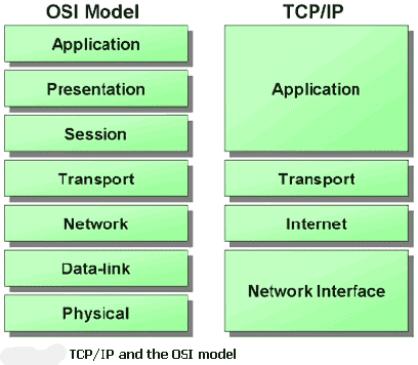
| - | TCP/IP Applications are Applications based on the TCP/IP protocol suite. It is part of the Application Layer of the Layered Network Model also known as OSI. | + | |
| + | [[Image:tcpmodel.jpg]] | ||
| + | |||
| + | TCP/IP Applications are Applications based on the TCP/IP protocol suite. It is part of the Application Layer of the Layered Network Model also known as the OSI Model. TCP is a connection based protocol meaning two applications communicating with each must first establish a connection by what is known as TCP handshaking. Once a connection has been established, applications communicate by sending and receiving streams of data through what is known as sockets. Some popular TCP/IP Applications include telnet, ssh and streaming media. | ||
| - | |||
| - | |||
| - | |||
| - | |||
__TOC__ | __TOC__ | ||
| + | ==Sockets== | ||
| + | TCP/IP Applications use sockets to send and receive data. Sockets contain all the information that is needed for applications to communicate with each other. These generally include: | ||
| + | * Protocol | ||
| + | * IP address | ||
| + | * Port number | ||
| + | |||
| + | A socket can be thought as an 'address' for an application. | ||
| + | |||
| + | Note: Sockets are also used by UDP. | ||
==Client/Server Model== | ==Client/Server Model== | ||
| + | The Client/Server Model is the most used model of TCP/IP applications. The server is usually a host that provides some service to the client and is usually always available to a client. The client and server both use sockets to establish connections with each other as well as send and receive data. The exchange of data depends on the operating system and language of the application. | ||
| + | |||
| + | ===Client=== | ||
| + | 1) Create a socket | ||
| + | 2) Store server information into socket | ||
| + | 3) Establish the connection with server using socket | ||
| + | 4) Send and receive data through the socket | ||
| + | 5) Close socket | ||
| + | |||
| + | ===Server=== | ||
| + | 1) Create a socket | ||
| + | 2) Store server information into socket | ||
| + | 3) Listen for connections on socket | ||
| + | 4) Accept connection | ||
| + | 5) Send and receive data through the socket | ||
| + | 6) Close the socket or Listen for connection on socket | ||
==Examples in Java== | ==Examples in Java== | ||
| Line 227: | Line 251: | ||
</pre></code> | </pre></code> | ||
| - | + | ||
==Security Issues== | ==Security Issues== | ||
| + | TCP does not have any security features and is vulnerable to numerous malicious attacks. These include: | ||
| + | *TCP "SYN" attacks | ||
| + | *IP Spoofing | ||
| + | *Sequence Guessing | ||
| + | *Source Routing | ||
| + | *Connecting Hijacking | ||
| + | *Packet Sniffing | ||
| + | *ICMP attacks | ||
| + | *DNS attacks | ||
| + | |||
| + | and many others. | ||
| + | |||
| + | It is up to the application developer and the system administrator to counter these attacks by securing the host machine as well as creating the application to be robust with security in mind. | ||
==References== | ==References== | ||
[1] Catalyst Development Corporation, [http://www.catalyst.com/products/socketwrench/tutorials/tutorial1.html] | [1] Catalyst Development Corporation, [http://www.catalyst.com/products/socketwrench/tutorials/tutorial1.html] | ||
| - | [2] | + | [2] Brian "Beej Jorgensen" Hall, [http://beej.us/guide/bgnet/output/html/multipage/index.html Beej's Guide to Network Programming 2007] |
| + | |||
| + | [3] CHRIS CHAMBERS, JUSTIN DOLSKE, and JAYARAMAN IYER [http://www.linuxsecurity.com/resource_files/documentation/tcpip-security.html TCP/IP Security] | ||
| + | |||
| + | ==See Also== | ||
| + | [1] [[Secure_File_Transfer_Protocols]] | ||
| + | |||
| + | ==External Links== | ||
| + | [1] [http://en.wikipedia.org/wiki/Internet_protocol_suite TCP/IP] | ||
| + | |||
| + | [2] [http://en.wikipedia.org/wiki/Stream_Sockets Stream Sockets] | ||
| + | |||
| + | [3] [http://en.wikipedia.org/wiki/Client/server Client/Server] | ||
| + | |||
| + | ==Signature== | ||
| - | [ | + | --[[User:Hank3|Hank3]] 16:16, 10 April 2008 (EDT) |
Current revision as of 20:16, 10 April 2008
Introduction
TCP/IP Applications are Applications based on the TCP/IP protocol suite. It is part of the Application Layer of the Layered Network Model also known as the OSI Model. TCP is a connection based protocol meaning two applications communicating with each must first establish a connection by what is known as TCP handshaking. Once a connection has been established, applications communicate by sending and receiving streams of data through what is known as sockets. Some popular TCP/IP Applications include telnet, ssh and streaming media.
Contents |
Sockets
TCP/IP Applications use sockets to send and receive data. Sockets contain all the information that is needed for applications to communicate with each other. These generally include:
- Protocol
- IP address
- Port number
A socket can be thought as an 'address' for an application.
Note: Sockets are also used by UDP.
Client/Server Model
The Client/Server Model is the most used model of TCP/IP applications. The server is usually a host that provides some service to the client and is usually always available to a client. The client and server both use sockets to establish connections with each other as well as send and receive data. The exchange of data depends on the operating system and language of the application.
Client
1) Create a socket 2) Store server information into socket 3) Establish the connection with server using socket 4) Send and receive data through the socket 5) Close socket
Server
1) Create a socket 2) Store server information into socket 3) Listen for connections on socket 4) Accept connection 5) Send and receive data through the socket 6) Close the socket or Listen for connection on socket
Examples in Java
/* Simple TCP/IP Client App */
import java.net.*;
import java.io.*;
public class SocketClient {
public static void main(String args[]) throws IOException
{
Socket mySocket = null;
BufferedReader in = null; //INPUT
PrintWriter out = null; //OUTPUT
//INIT AND GET SOCKET
try{
mySocket = new Socket("192.168.1.105", 9999);
}catch(UnknownHostException e){}
//INPUT STREAM
in = new BufferedReader(new InputStreamReader(
mySocket.getInputStream()));
//OUTPUT STREAM
out = new PrintWriter(mySocket.getOutputStream(), true);
//USER INPUT STREAM
BufferedReader stdIn = new BufferedReader(
new InputStreamReader(System.in));
//DO SOMETHING WITH STREAMS
String userInput;
while(true)
{
userInput = stdIn.readLine();
out.println(userInput);
if(userInput.equals("exit"))
{
break;
}
}
//CLOSE STREAMS
in.close();
out.close();
//CLOSE SOCKET
mySocket.close();
}
}
/* Simple TCP/IP Server App */
import java.net.*;
import java.io.*;
public class SocketServer {
public static void main(String args[]) throws IOException
{
ServerSocket myServer = null;
BufferedReader in = null; //INPUT
PrintWriter out = null; //OUTPUT
Socket mySocket = null;
//INIT AND GET SOCKET
try{
myServer = new ServerSocket(9999);
}catch(UnknownHostException e){}
//LISTEN IN AND ACCEPT CONNECTIONS ON SOCKET
mySocket = myServer.accept();
//INPUT STREAM
in = new BufferedReader(new InputStreamReader(
mySocket.getInputStream()));
//OUTPUT STREAM
out = new PrintWriter(mySocket.getOutputStream(), true);
//DO SOMETHING WITH STREAMS
String inputFromClient = "";
while((inputFromClient = in.readLine()) != null)
{
System.out.println(inputFromClient);
if (inputFromClient.equals("exit"))
{
break;
}
}
//CLOSE STREAMS
in.close();
out.close();
//CLOSE SOCKET AND SERVER
myServer.close();
mySocket.close();
}
}
Examples in C
/* A simple client in C */
#include <string.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netinet/in.h>
#include <arpa/inet.h>
#include <stdio.h>
#define SERVERPORT 8888
#define SERVERADDRESS "192.168.1.105"
int main()
{
int servSock, bytes_sent, sin_size;
char msg[10];
struct sockaddr_in serverAddress; // server's address and port information
struct hostent *host; //host information
if ((servSock = socket(PF_INET, SOCK_STREAM, 0)) < 0)
printf("socket() FAILED");
serverAddress.sin_family = AF_INET;
serverAddress.sin_port = htons(SERVERPORT);
serverAddress.sin_addr.s_addr = inet_addr(SERVERADDRESS);
memset(serverAddress.sin_zero, '\0', sizeof serverAddress.sin_zero);
connect(servSock, (struct sockaddr *)&serverAddress, sizeof serverAddress);
while(1)
{
scanf("%s", msg);
send(servSock, msg, sizeof (msg), 0);
if(strcmp(msg, "exit") == 0)
break;
}
close(servSock);
return 1;
}
/* A simple server in C */
#include <string.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netinet/in.h>
#include <arpa/inet.h>
#include <stdio.h>
#define MYPORT 8888
#define BACKLOG 1
int main()
{
int servSock, new_fd, sin_size, bytes_sent, bytes_recv;
char buffer[10];
struct sockaddr_in myServer; //server information
struct sockaddr_in their_addr; // connector's address information
if ((servSock = socket(PF_INET, SOCK_STREAM, 0)) < 0)
printf("socket() FAILED");
myServer.sin_family = AF_INET;
myServer.sin_port = htons(MYPORT);
myServer.sin_addr.s_addr = INADDR_ANY;
memset(myServer.sin_zero, '\0', sizeof myServer.sin_zero);
printf("Server [%d] accepting and listening on %d\n", myServer.sin_addr.s_addr, myServer.sin_port);
bind(servSock, (struct sockaddr *)&myServer, sizeof myServer);
listen(servSock, BACKLOG); //LISTEN IN PORT 8888
sin_size = sizeof their_addr;
printf("size = %d\n", sizeof (buffer));
new_fd = accept(servSock, (struct sockaddr *)&their_addr, &sin_size);
while(1)
{
bytes_recv = recv(new_fd, buffer, sizeof (buffer), 0);
//buffer[10] = '\0';
printf("%s\n", buffer);
if(strcmp(buffer, "exit") == 0)
break;
}
close(new_fd);
close(servSock);
return 1;
}
Security Issues
TCP does not have any security features and is vulnerable to numerous malicious attacks. These include:
- TCP "SYN" attacks
- IP Spoofing
- Sequence Guessing
- Source Routing
- Connecting Hijacking
- Packet Sniffing
- ICMP attacks
- DNS attacks
and many others.
It is up to the application developer and the system administrator to counter these attacks by securing the host machine as well as creating the application to be robust with security in mind.
References
[1] Catalyst Development Corporation, [1]
[2] Brian "Beej Jorgensen" Hall, Beej's Guide to Network Programming 2007
[3] CHRIS CHAMBERS, JUSTIN DOLSKE, and JAYARAMAN IYER TCP/IP Security
See Also
[1] Secure_File_Transfer_Protocols
External Links
[1] TCP/IP
[2] Stream Sockets
[3] Client/Server
Signature
--Hank3 16:16, 10 April 2008 (EDT)